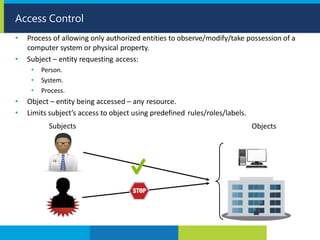
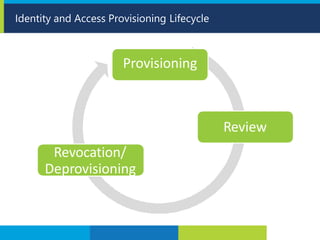
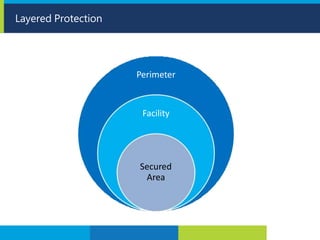
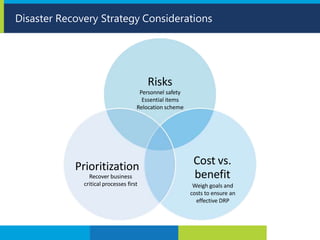
The document provides information about Leo Lourdes and his foundation in cyber security. Leo Lourdes has extensive training and certifications in IT management, information security, project management and other related fields. The objective of his foundation is to prevent harm to computer networks, applications, devices and data through security awareness training, vulnerability assessments, penetration testing and other methods.