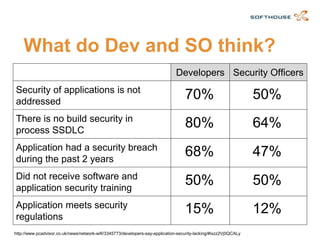
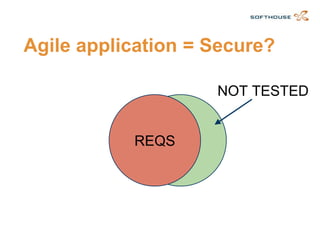
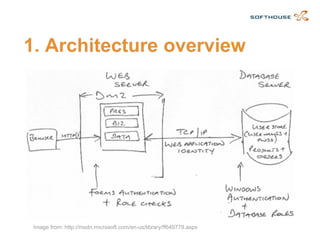
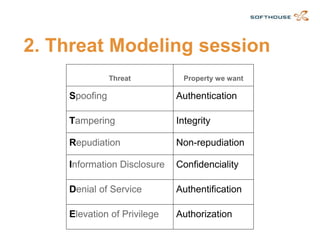
The document discusses how to integrate security requirements within agile development teams, highlighting the lack of security throughout the software development lifecycle. It presents key strategies for improving application security, including threat modeling, continuous integration, and incorporating security activities into sprints. The author emphasizes the importance of collaboration and responsibility among team members to create secure applications.