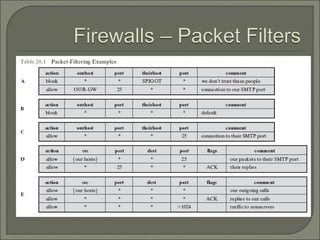
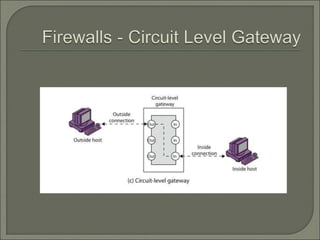
This document discusses network security and firewalls. It describes how firewalls provide perimeter defense and control access between interconnected networks. Several types of firewalls are mentioned, including packet filtering firewalls, stateful firewalls, application-level gateways, and proxies. The document also briefly discusses access control models, multilevel security models like Bell-LaPadula, and security evaluation standards such as Common Criteria.