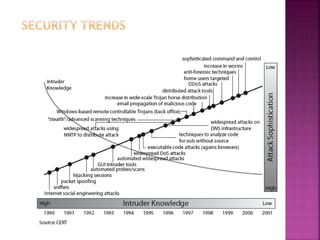
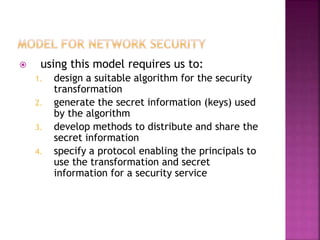
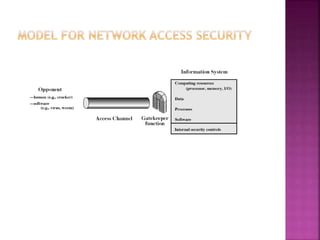
This document discusses key concepts in internet security. It defines computer, network, and internet security. It outlines the ITU-T X.800 standard for defining security requirements and describes security attacks, services, and mechanisms. Finally, it discusses models for implementing network security including cryptographic techniques and access controls.