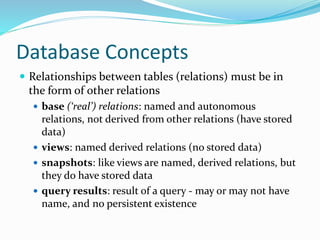
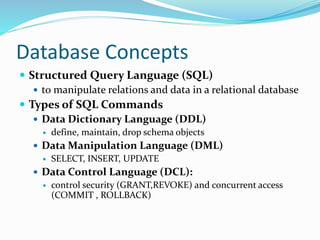
This document discusses database concepts and security models. It covers relational database concepts like tables, relations, attributes, tuples, primary keys and foreign keys. It then discusses security requirements for databases like physical integrity, logical integrity, element integrity, auditability, access control and availability. It describes the SQL security model of users, actions, objects, privileges and views. It also covers weaknesses of the discretionary access control model and alternatives like mandatory access controls.