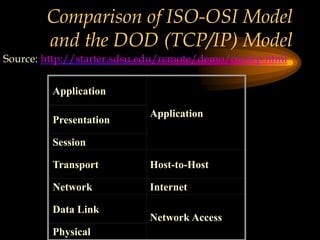
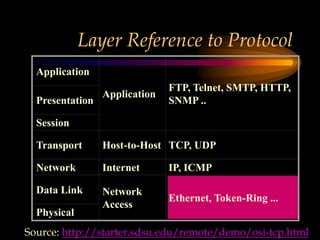
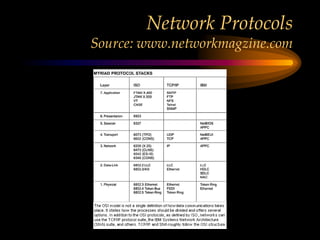
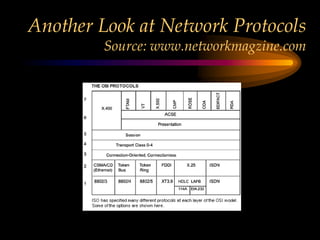
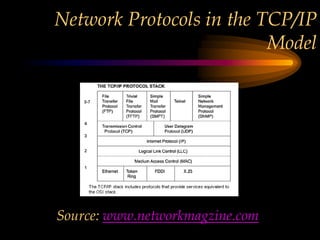
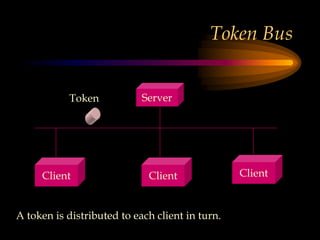
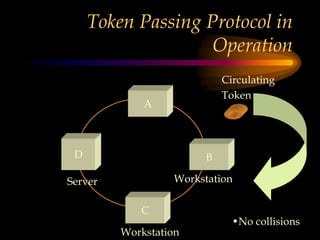
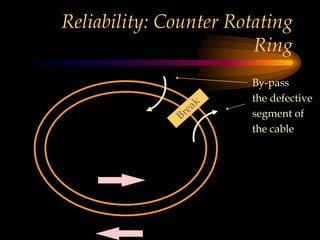
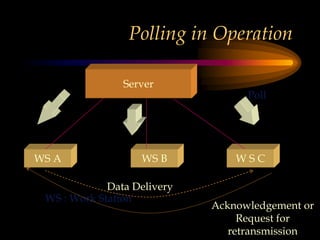
The chapter discusses media level protocols including CSMA/CD, token passing, and polling. It describes the IEEE standards that apply to LANs based on different protocols. The key protocols discussed are Ethernet (CSMA/CD) under IEEE 802.3, token ring under IEEE 802.5, and token bus under IEEE 802.4. The chapter also provides an overview of the IEEE organization and its role in setting networking standards, particularly for the physical and data link layers.