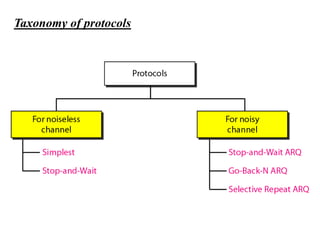
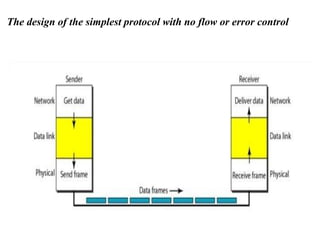
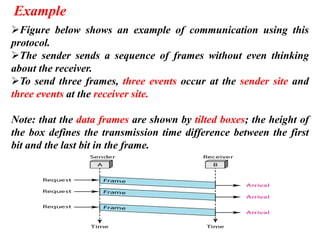
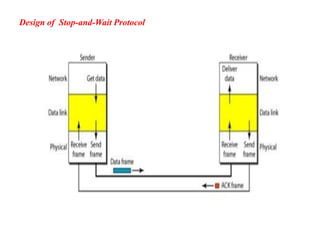
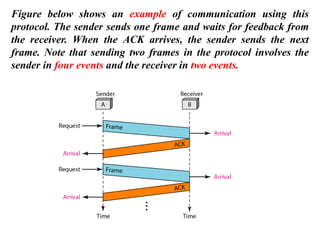
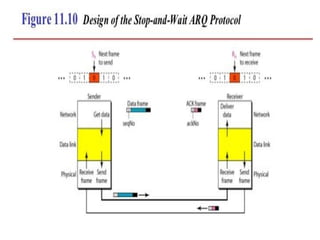
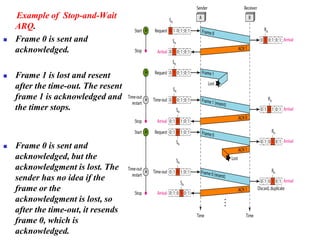
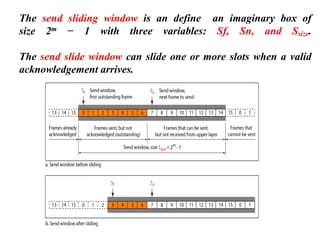
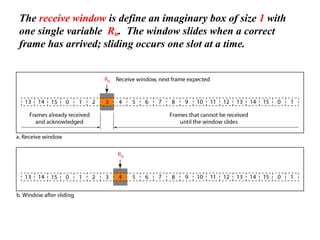
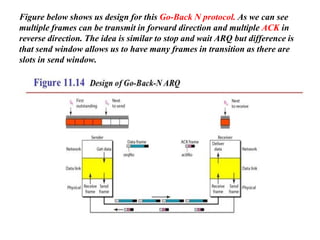
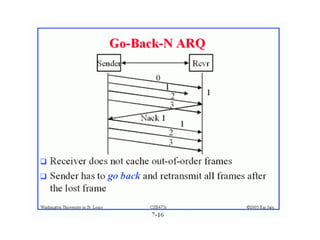
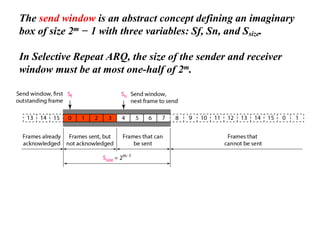
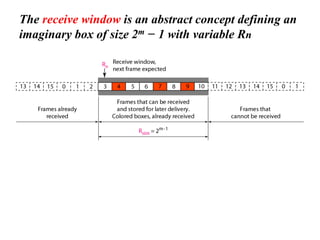
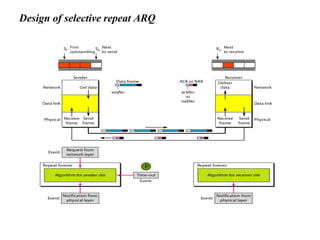
The document discusses various data transmission protocols used in computer networking, categorizing them into those for noiseless and noisy channels. Key protocols include the simplest protocol, stop-and-wait protocol, stop-and-wait ARQ, go-back-n ARQ, and selective repeat ARQ, each with unique advantages and disadvantages regarding efficiency and error handling. The document also describes the concept of piggybacking to improve bidirectional communication efficiency.