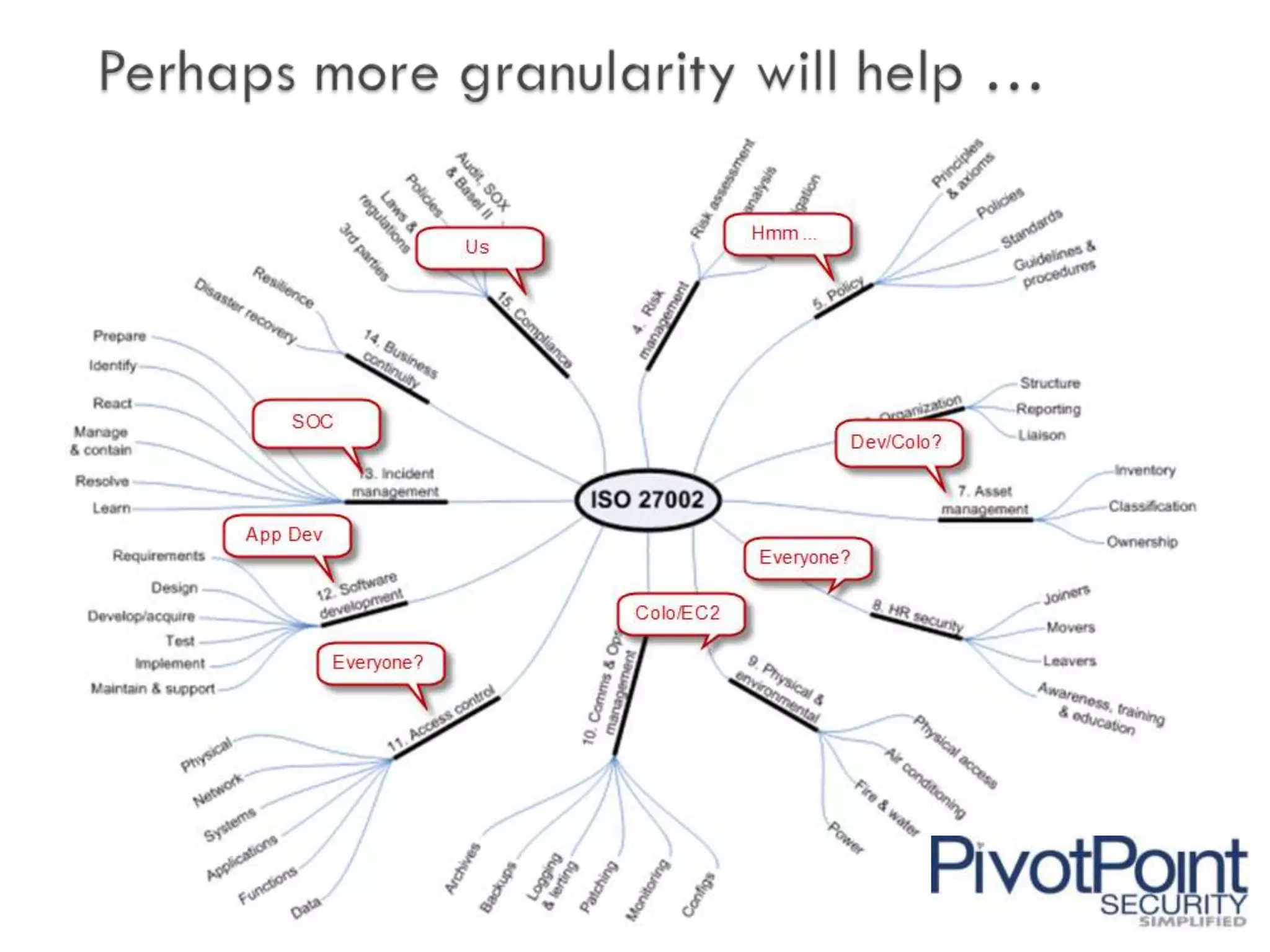
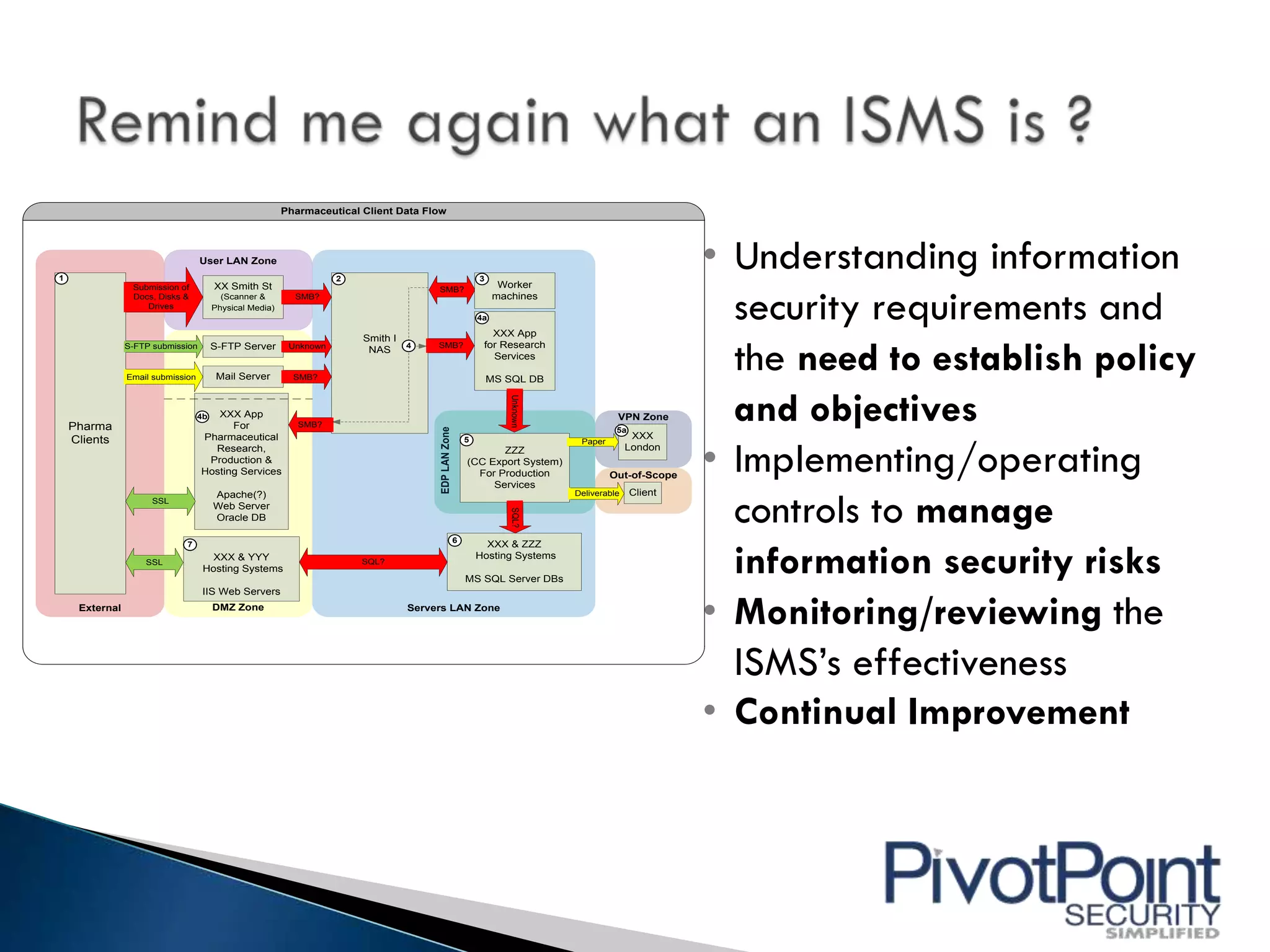
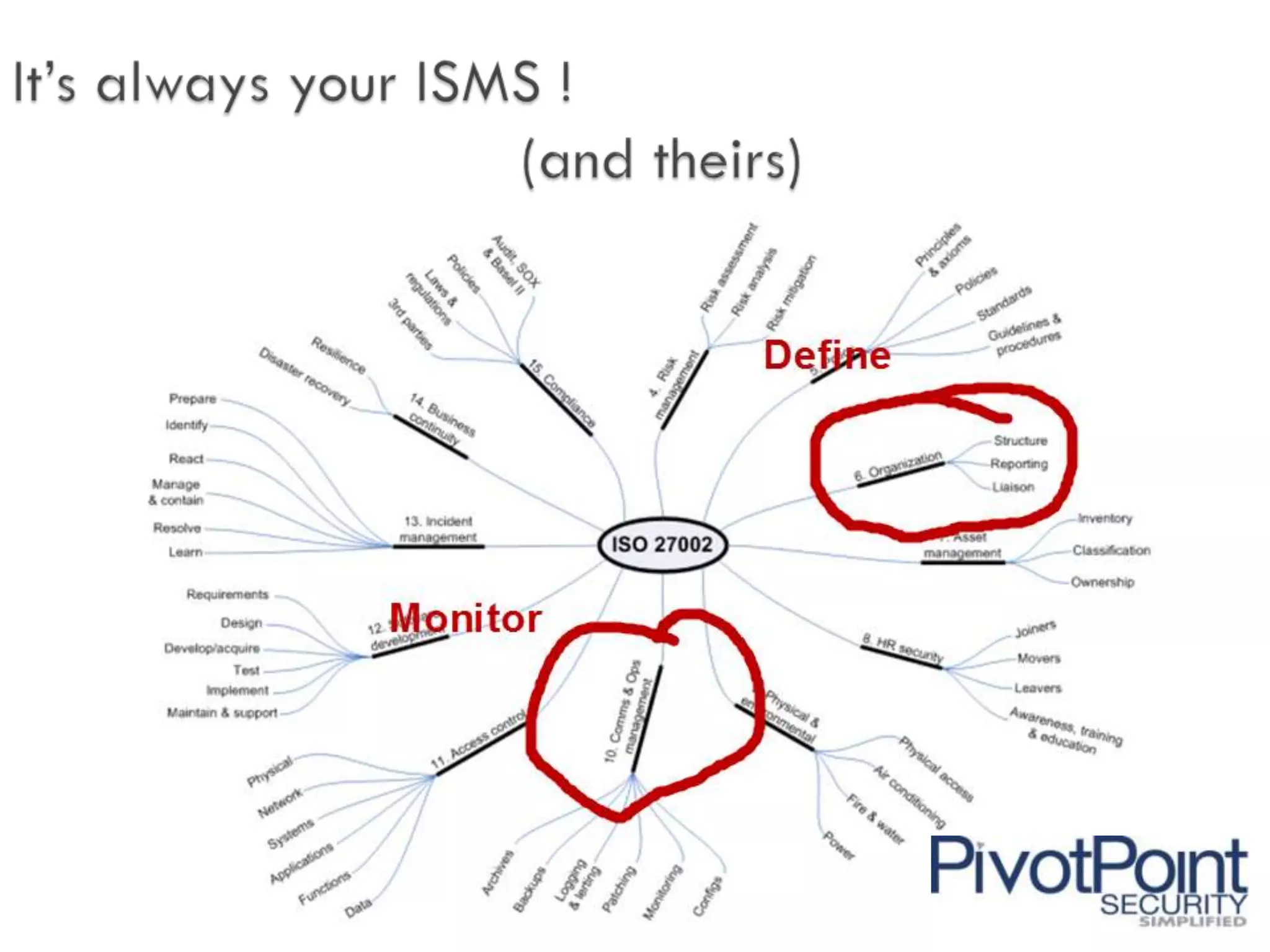
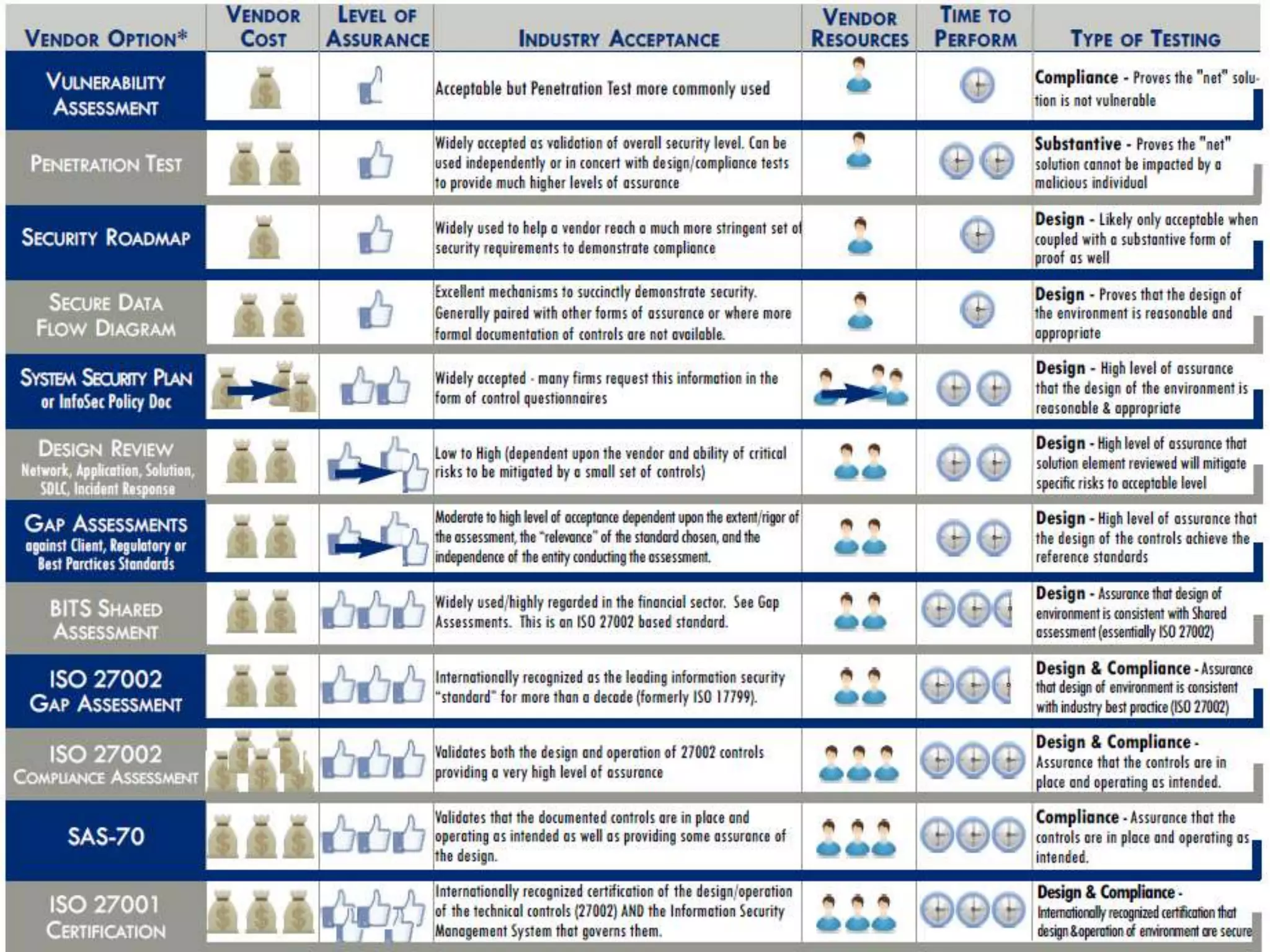
This document discusses outsourcing and the notable risks and rewards it provides. While outsourcing can reduce costs and increase flexibility, it also carries risks such as data breaches, failure to comply with regulations, and intellectual property disclosure. When outsourcing, organizations must be able to prove to regulators that key vendors are secure and compliant. Outsourcing responsibility and liability is not possible. Organizations must integrate information security into their vendor management programs to properly assess and manage risks from third parties.