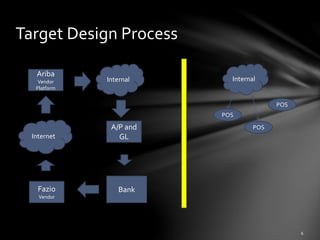
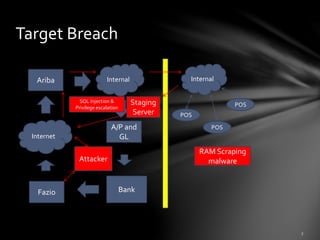
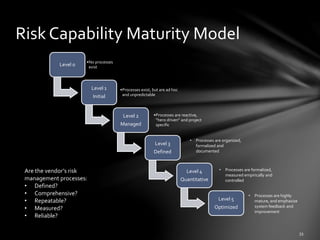
The document discusses third-party risk management (TPRM) and its importance in preventing data breaches, citing the Target data breach as a significant example. It outlines regulatory requirements, critical risk management processes, and the necessity for diligent vendor assessments and ongoing monitoring. The insights emphasize that most organizations do not adequately manage third-party risks, despite relying heavily on external vendors.