- TCP was originally designed with a goal of allowing communication networks to withstand nuclear war through a loose network of interconnected nodes with ad-hoc routing and weak service guarantees.
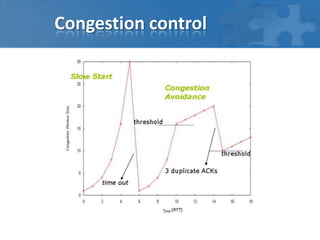
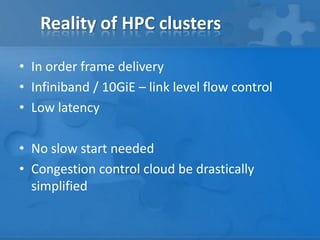
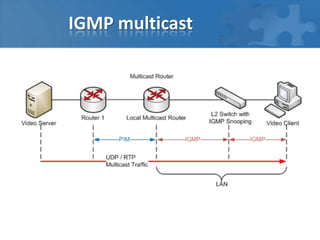
- While TCP works well for high reliability and in-order delivery over high-latency wide-area networks, it is not optimized for high-performance computing clusters with low-latency infiniband or 10 gigabit ethernet networks.
- Alternatives like TCMP and SCTP were designed for low-latency clustered environments and provide features like message-orientation, multi-streaming, and multi-homing that simplify congestion control compared to TCP.