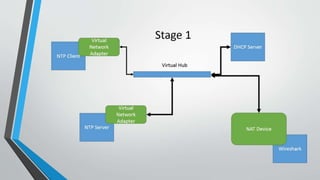
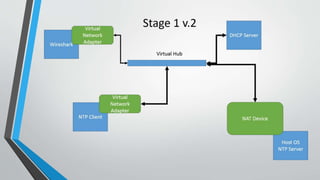
This document summarizes a research project exploring security flaws in the Network Timing Protocol (NTP). The project goals were to set up a virtual computer network with an NTP client and server, and demonstrate a man-in-the-middle attack by fooling the NTP client. The researchers set up virtual machines running Linux, configured one as an NTP server synchronized to an external time source, and monitored network traffic. They planned to use Ettercap to intercept NTP traffic through ARP poisoning, but ran out of time before completing the attack.