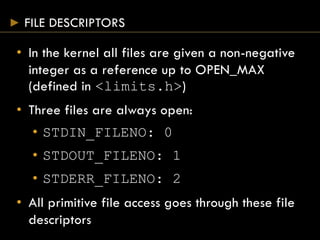
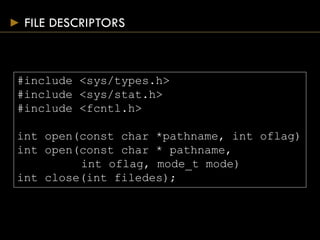
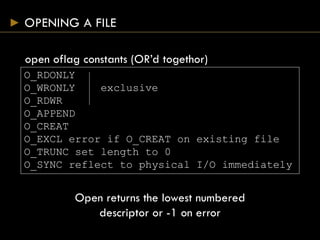
This document provides an overview of file I/O and systems programming in UNIX. It discusses file descriptors, opening and accessing files, file permissions, file systems, linking and renaming files, and password files. The key points covered are:
- Files are accessed using file descriptors rather than FILE objects.
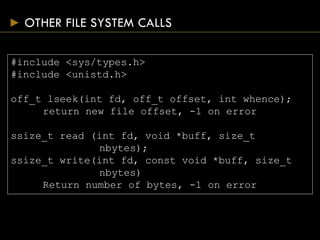
- Common file access functions include open(), close(), read(), write(), and lseek().
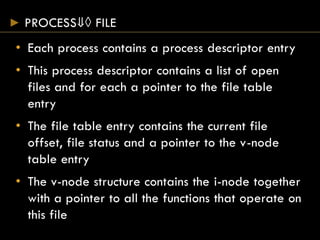
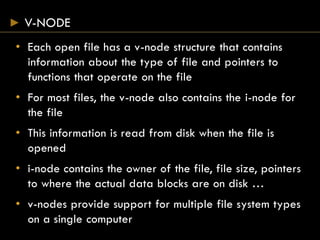
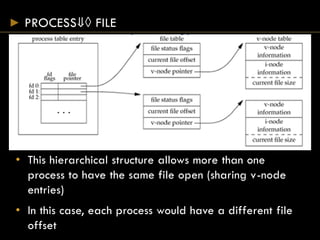
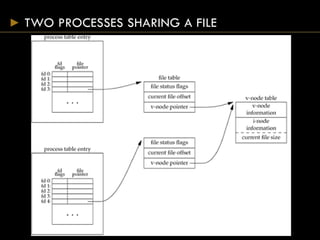
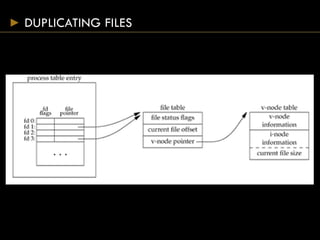
- Each open file has a v-node containing metadata and pointers to functions for that file type.
- File permissions are checked against a process's effective user and group IDs.
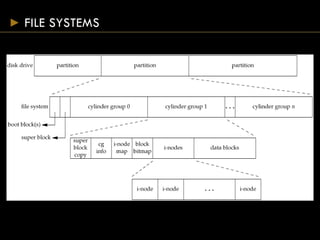
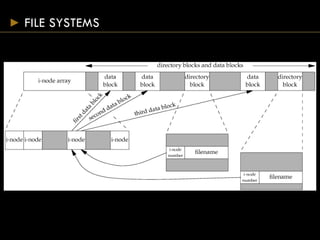
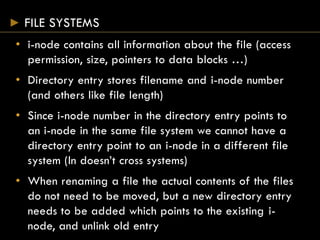
- Directories map filenames to inodes, which contain file metadata and data block pointers.
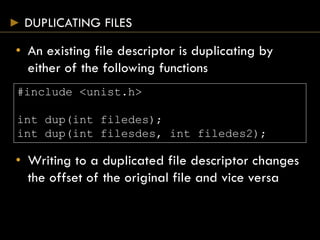
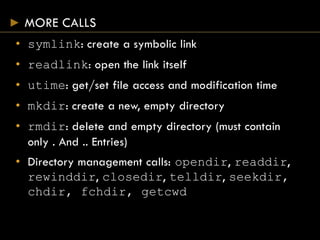
- Functions for file manipulation include link(), unlink