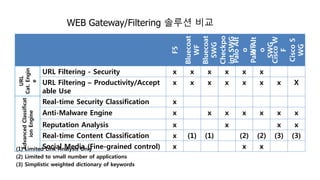
The document discusses Secure Web Gateway (SWG) technology which provides effective control of inbound and outbound network traffic. Key features of SWG include blocking access to dangerous websites or malware, classifying and securely filtering social media and web searches, and detecting malware in web pages. The document then focuses on the F5 SWG product and its primary capabilities such as URL/app filtering, malware detection, user identification, and security management/reporting. A comparison chart shows how F5's SWG compares favorably to other vendors in areas like advanced classification, real-time security, and content filtering.