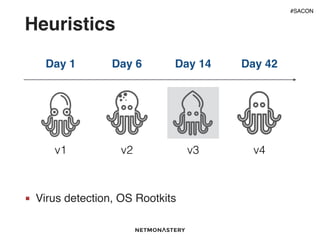
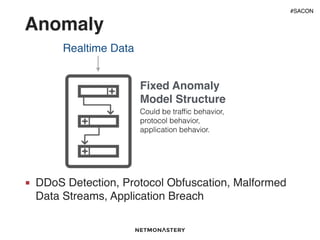
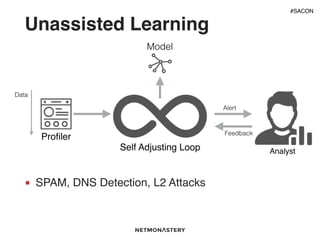
This document discusses using analytics and machine learning for threat detection. It covers different types of detection systems like signature-based, anomaly-based and learning systems. It explains why analytics are needed given challenges like the speed of attacks. Various machine learning techniques are described, including heuristics, anomaly detection, time series analysis and classifiers. Examples of when machine learning works well include DNS-based detection and traffic anomalies. Common failures are also discussed, such as the stale dataset problem and variance challenges.