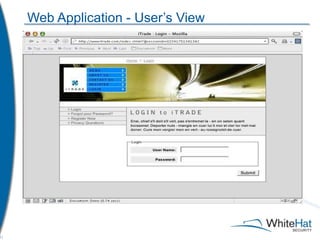
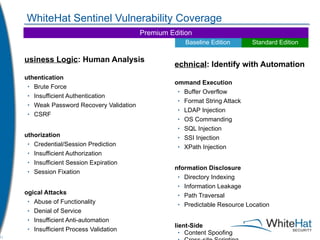
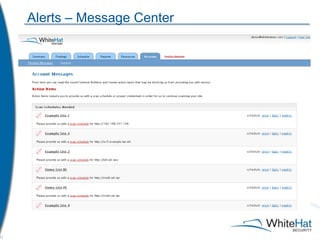
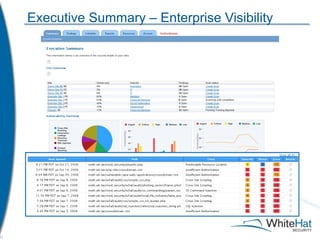
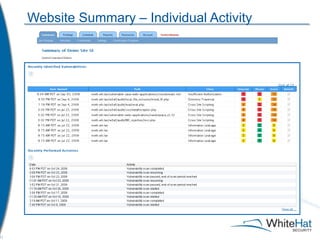
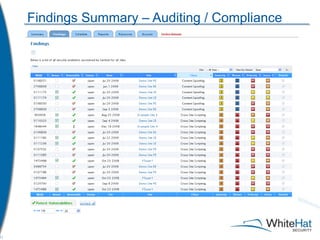
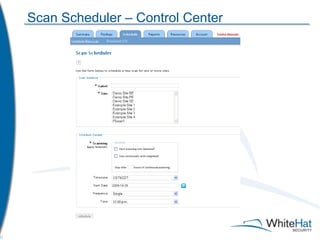
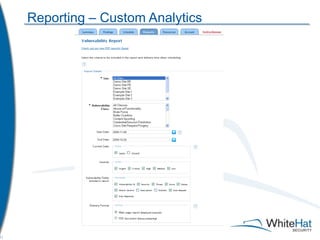
The document discusses Whitehat Security's comprehensive website risk management services, including various vulnerability assessment editions designed for different types of web applications. It outlines the evolution of their services since 2001, emphasizing cost-efficient, scalable SaaS solutions with verified vulnerability reporting. Additionally, the document details key functionalities, automated identification of security issues, and the importance of secure coding practices.
![WhiteHat Security Website Risk Management Mark G. Meyer Director of Sales – Northeast 212-422-9400 [email_address]](https://image.slidesharecdn.com/whpresentation102809-12570946116822-phpapp02/75/WhiteHat-Security-Presentation-1-2048.jpg)