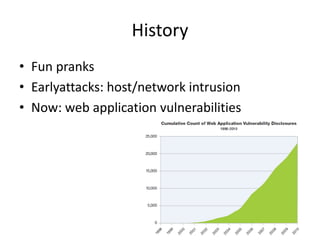
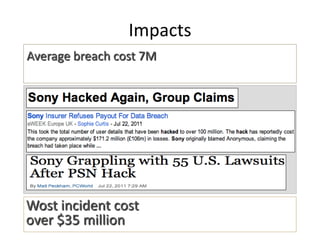
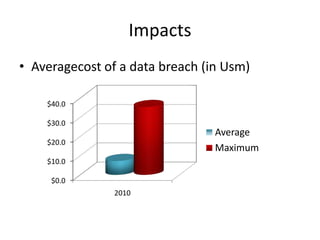
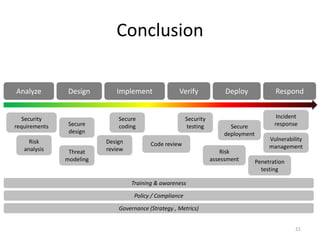
This document summarizes a presentation on web security given at the Confoo Conference in 2012. The presentation was given by Antonio Fontes from L7 and David Mirza from Subgraph. They discussed the history of web attacks moving from host/network intrusion to modern vulnerabilities like XSS and SQL injection. They explained that all business logic and data is now on the web, making it the main target for attacks. The motivations for these attacks include money, ideology, fame, and supporting other criminal activities. They outlined the impacts such as financial costs, reputation damage, and legal/compliance issues. Finally, they provided recommendations on technical controls like web application testing and process controls like secure development practices and training to help address these ongoing