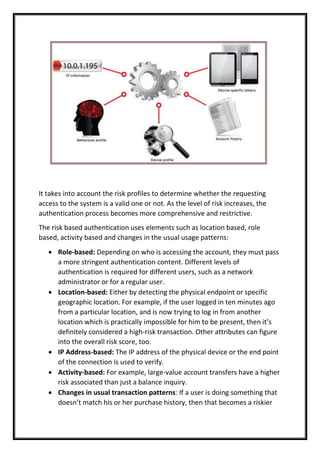
The document discusses risk-based authentication as a solution to enhance security against data theft in cloud environments. It outlines how this method uses multiple verification steps and contextual factors to assess the risk of access attempts, thereby preventing unauthorized access. The importance of conducting a proper risk assessment before implementation is also emphasized to ensure robust protection against breaches.