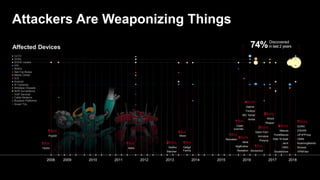
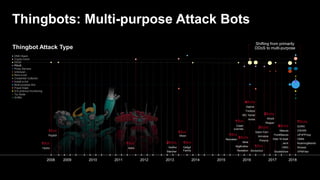
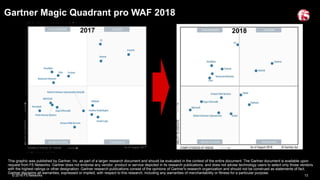
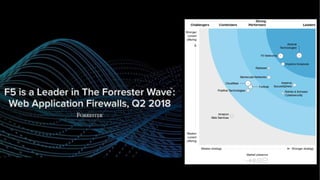
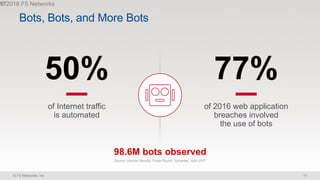
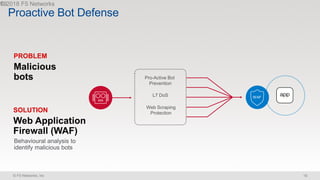
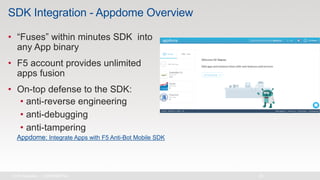
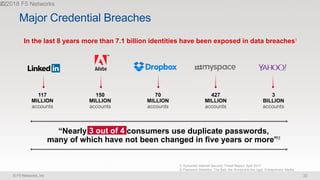
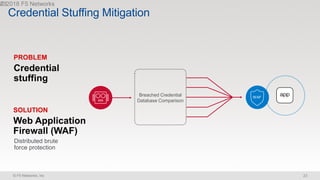
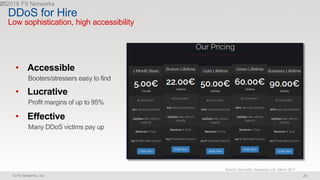
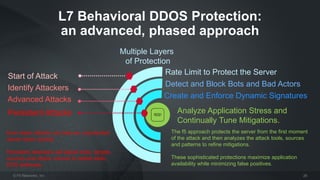
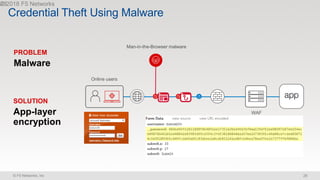
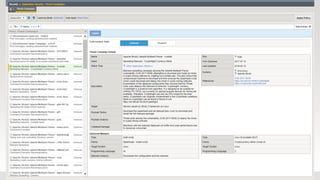
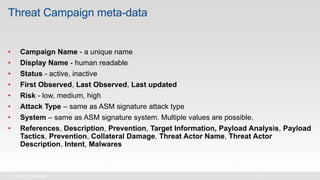
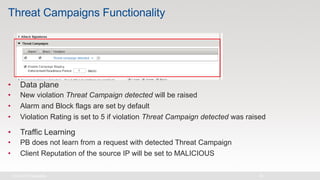
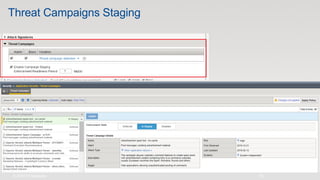
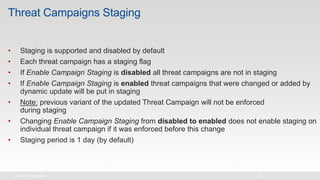
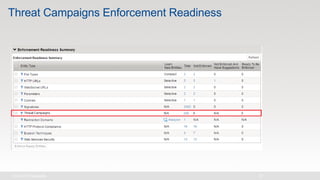
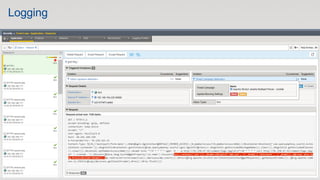
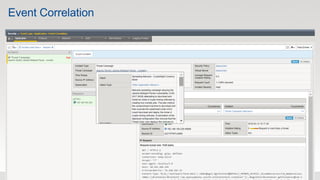
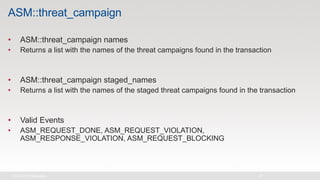
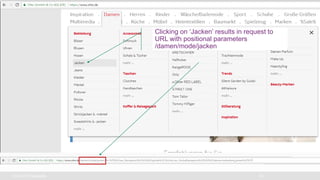
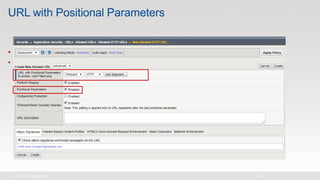
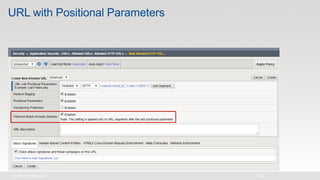
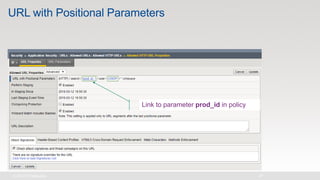
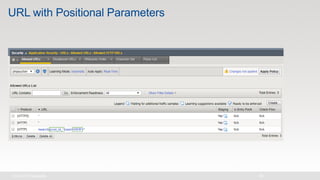
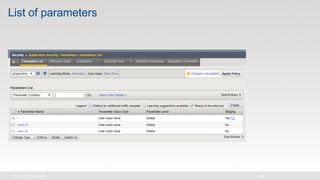
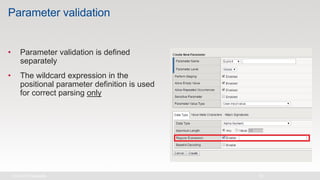
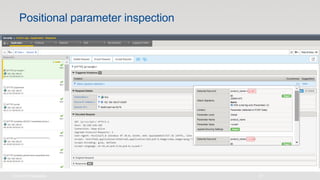
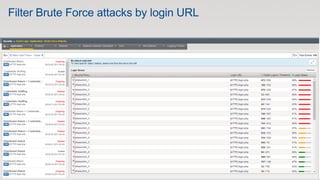
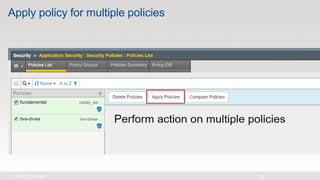
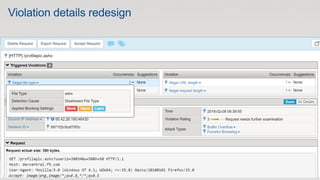
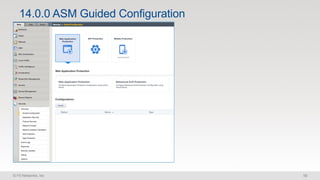
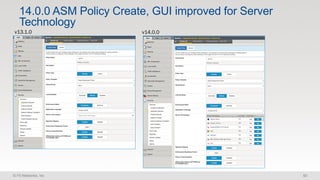
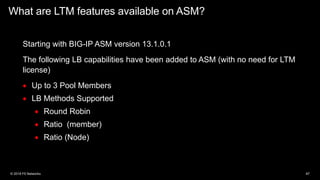
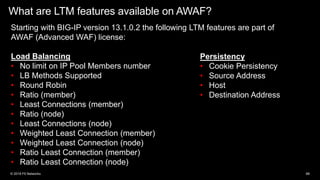
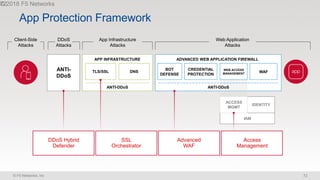
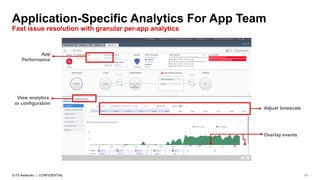
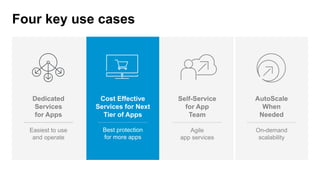
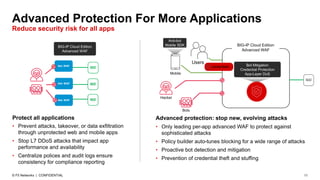
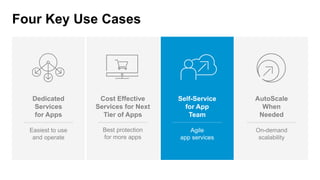
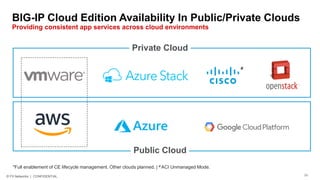
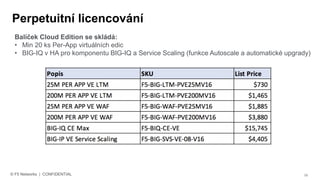
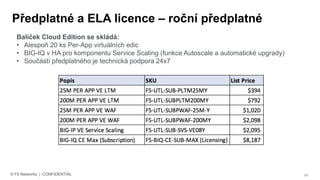
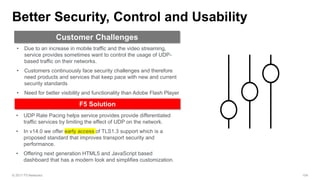
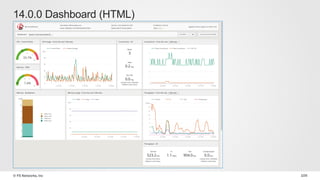
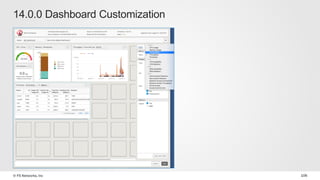
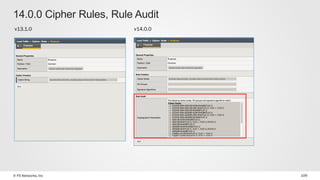
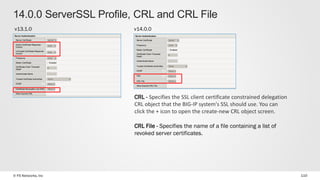
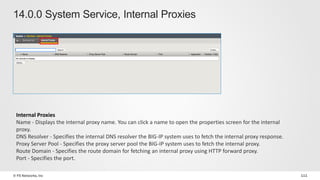
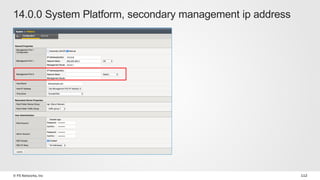
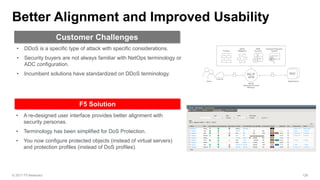
The document discusses various internet security threats and the evolving landscape of cyber attacks, particularly focusing on the OWASP Top 10 vulnerabilities from 2013 and 2017. It highlights the prevalence of bots in web traffic and different attack types such as DDoS, malware, and credential stuffing, emphasizing the importance of proactive measures like bot defense and application security management. Additionally, it outlines F5 Networks' offerings in application protection and security solutions against these threats.