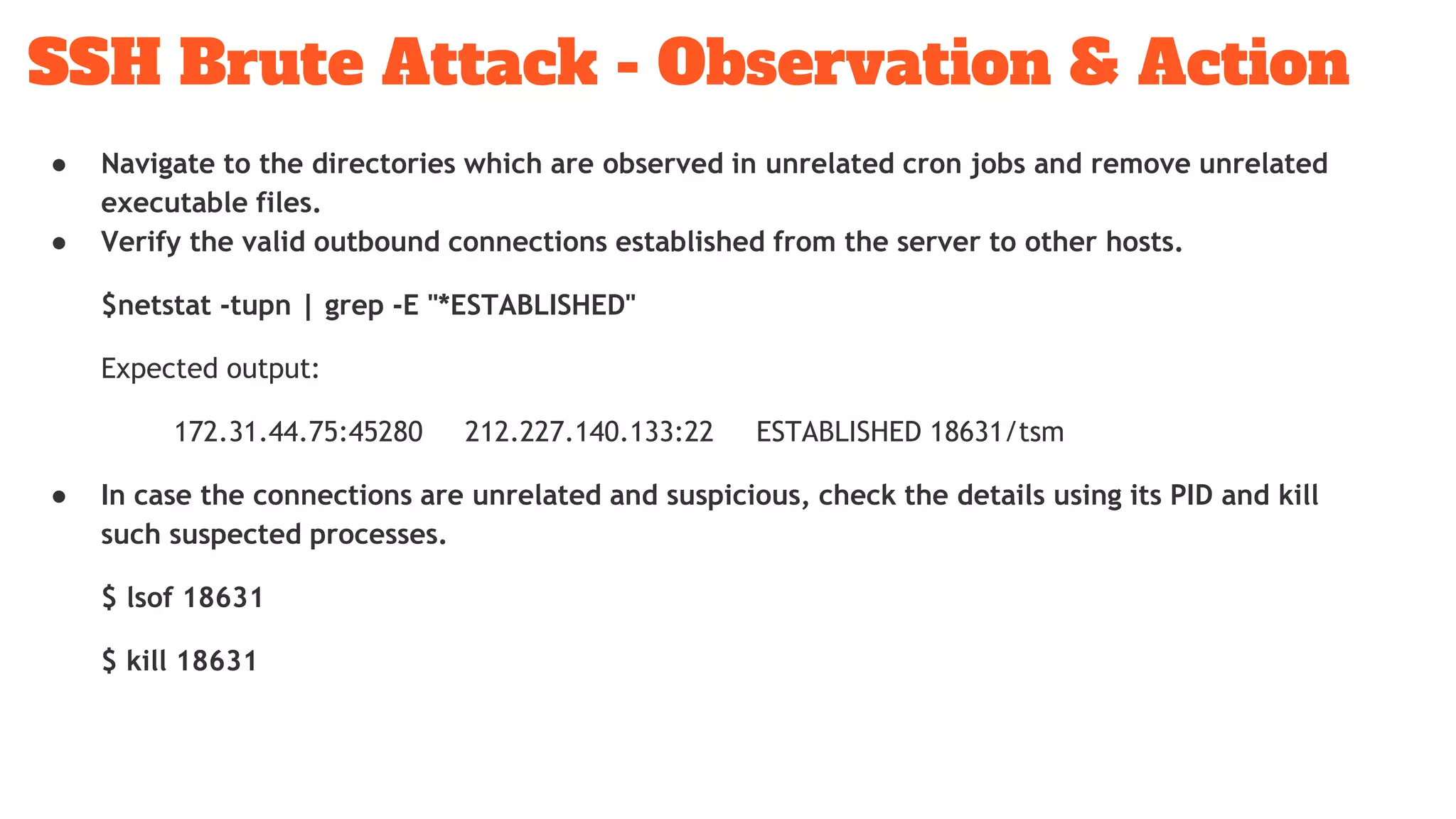
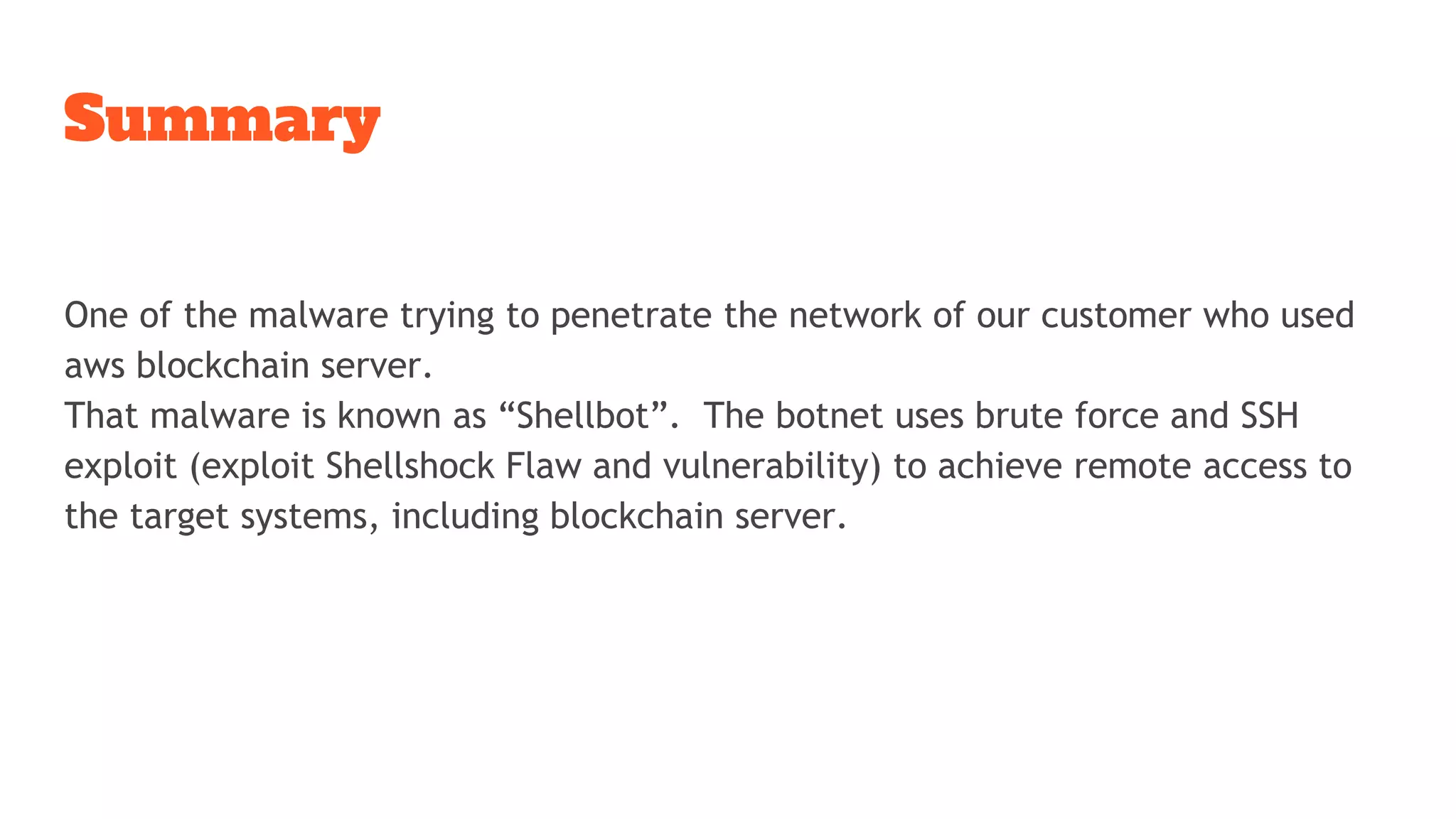
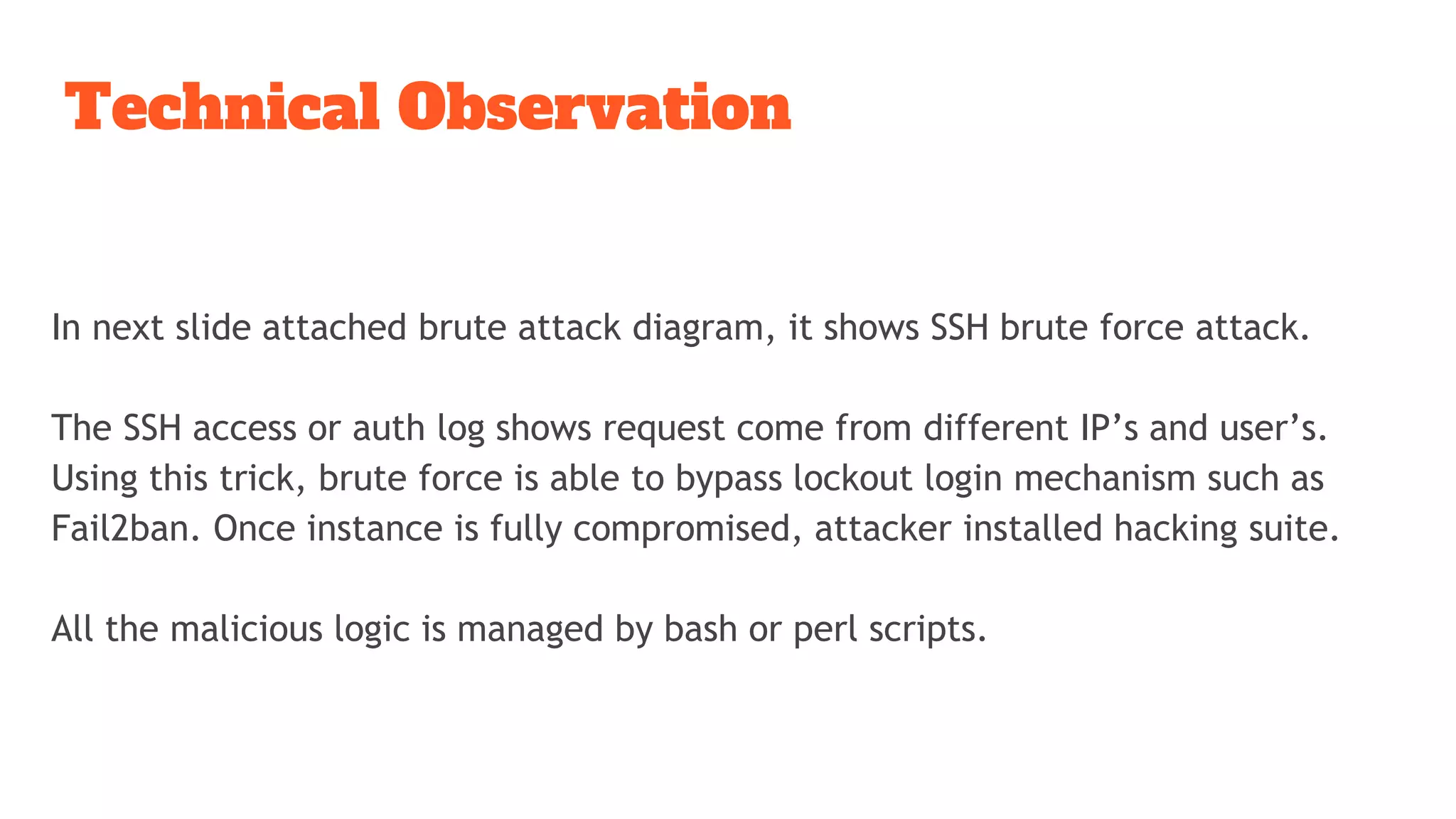
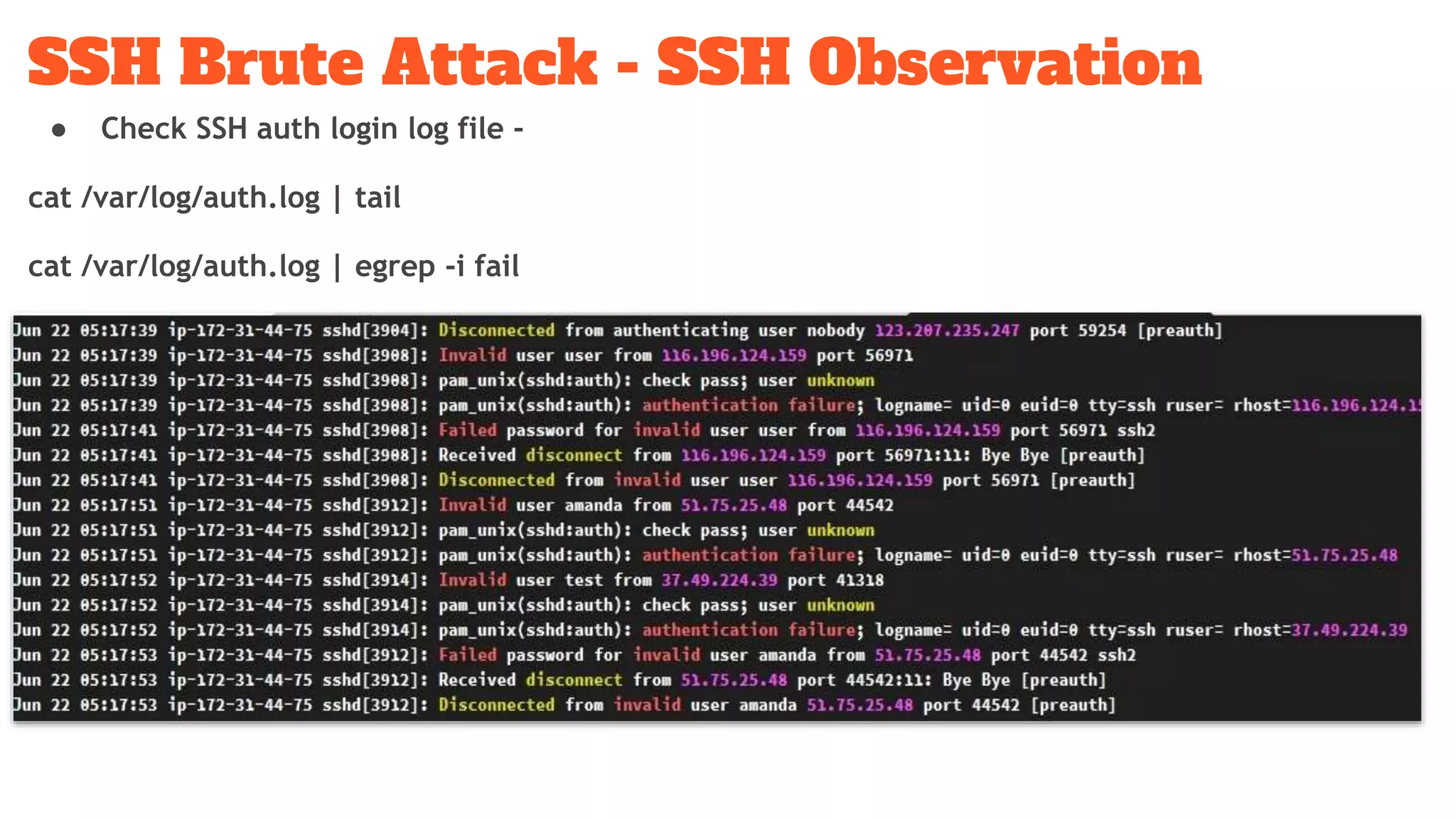
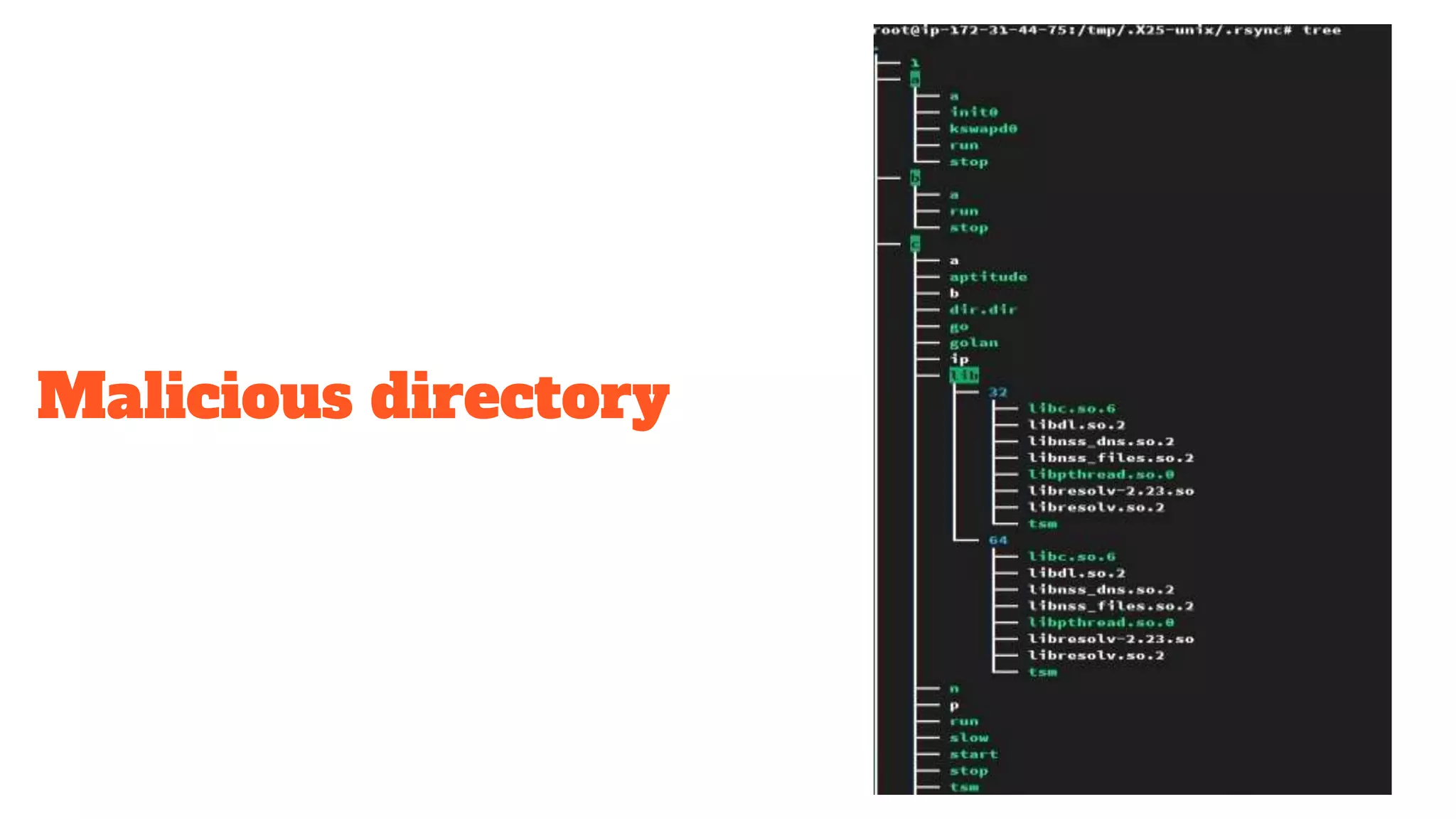
The document discusses a ssh brute force attack on an AWS blockchain instance, highlighting continuous CPU utilization increases and a malware known as 'shellbot' that exploits SSH vulnerabilities for unauthorized access. It details methods for observing and mitigating the attack, including reviewing SSH logs, checking user authentication attempts, and removing unnecessary cron jobs. Recommendations include navigating suspicious directories, validating outbound connections, and terminating insecure processes.



![● Find out un-necessary cron jobs of all system users & remove it.
$ sed 's/^([^:]*):.*$/crontab -u 1 -l 2>&1/' /etc/passwd | grep -v "no crontab for" | sh
Expected output -
1 1 */2 * * /var/lib/postgresql/.configrc/a/upd>/dev/null 2>&1
@reboot /var/lib/postgresql/.configrc/a/upd>/dev/null 2>&1
5 8 * * 0 /var/lib/postgresql/.configrc/b/sync>/dev/null 2>&1
@reboot /var/lib/postgresql/.configrc/b/sync>/dev/null 2>&1
0 0 */3 * * /tmp/.X25-unix/.rsync/c/aptitude>/dev/null 2>&1
SSH Brute Attack - Observation & Action](https://image.slidesharecdn.com/sshbruteforceattackonawsblockchain-200707072202/75/SSH-Brute-Force-Attack-8-2048.jpg)