Hack the box open admin writeup
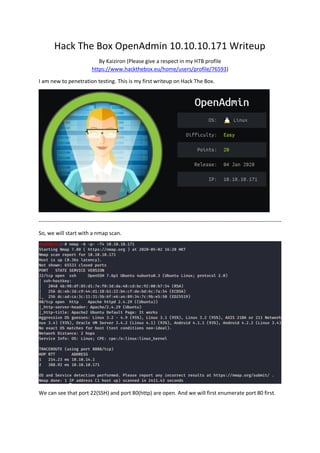
- 1. Hack The Box OpenAdmin 10.10.10.171 Writeup By Kaiziron (Please give a respect in my HTB profile https://www.hackthebox.eu/home/users/profile/76593) I am new to penetration testing. This is my first writeup on Hack The Box. -------------------------------------------------------------------------------------------------------------------------------------- So, we will start with a nmap scan. We can see that port 22(SSH) and port 80(http) are open. And we will first enumerate port 80 first.
- 2. We can see it is an apache2 default page, so some other pages may in some other locations. Let’s use dirbuster to see if we can find any other pages. After a while, dirbuster found a page /ona Let’s browser to that page and see if there’s any information disclosure.
- 3. We can see it show that the version is v18.1.1 and the “DOWNLOAD” hyperlink show that it is probably running something called opennetadmin. We found an exploit for this version of opennetadmin in github by googling. https://github.com/amriunix/ona-rce It is a python script which can check if the target is vulnerable, and of course can also exploit this vulnerability. That script show that our target is vulnerable to this exploit. Then we will use it to exploit the vulnerability and try gain a shell. We gain a shell as www-data. However we are in /opt/ona/www and unable to change directory with cd, but we can use ls and also cat so it doesn’t matter at all. After some enumeration we found there is a file in /opt/ona/www/local/config called database_settings.inc.php . We use cat to open it up.
- 4. And it seems is the credentials of some database. Don’t forget that port 22(SSH) is open. Let’s try to login with SSH with the password n1nj4W4rri0R! and see if there’s any password reuse. We use “cat /etc/passwd” to open up the passwd file to check some username in this machine. We can found 2 users, called jimmy and Joanna. We can also find the user by using “ls -la /home/” to check for home folder of user. Then we will try to use SSH to login to those users using sshpass to enter in one line for convenient. sshpass -p n1nj4W4rri0R! ssh jimmy@10.10.10.171 sshpass -p n1nj4W4rri0R! ssh joanna@10.10.10.171 We can successfully login as jimmy but not Joanna.
- 5. After some enumeration, we found few interesting things, first there is a folder in /var/www/ called internal which is owned by user jimmy which looks like a webpage. We found few pages inside the internal folder, one of them is very interesting. This php file will execute a command “cat /home/joanna/.ssh/id_rsa” which should be the key of joanna ssh. Second, we found a file /etc/apache2/sites-available/internal.conf which seems is the configuration file of the internal site.
- 6. It shows that it listen on port 52846. So now we will try to browse to main.php in the internal site on port 52846 to get the ssh key of Joanna /home/joanna/.ssh/id_rsa . We try to use browser to browse 10.10.10.171:52846 , however it is unable to connect. The site named internal so maybe it can only be access in the target machine itself. So, there is 2 method which I will show in this writeup which can get the ssh key. Method 1, we set a SSH tunnel to 10.10.10.171:52846. sshpass -p n1nj4W4rri0R! ssh -L 52846:127.0.0.1:52846 jimmy@10.10.10.171 Then we use browser to browse localhost port 52846, 127.0.0.1:52846. We found a login page which should be the index.php in /var/www/internal/ . We tried the credentials jimmy:n1nj4W4rri0R! ,however we failed to login.
- 7. Then we go to SSH and open index.php with vim. vim /var/www/internal/index.php It store the password in sha512 hash, I tried to crack it but failed and it is probably not some easy password which will present in some weak wordlist. So we can make some modification in the if statement to make our login succeed. Remember to undo the modification after we get the SSH key to avoid any spoiler to others.
- 8. Method 2, we use curl command in SSH which run as the target machine itself, to get the SSH key -------------------------------------------------------------------------------------------------------------------------------------- Then we copy the RSA private key to our local machine and save as id_rsa. I tried to use SSH to login to Joanna using id_rsa key. However it will ask for passphrase, so we need to crack the RSA key first. We will use john to crack it, so we need to change the RSA key to hash first, we will use ssh2john.py ssh2john.py id_rsa > id_rsa.hash Then we will use john to crack it with rockyou.txt as wordlist. john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
- 9. We can see that the passphrase is bloodninjas. So we will use SSH to login as Joanna. ssh -i id_rsa joanna@10.10.10.171 bloodninjas We successfully login as Joanna in SSH and we can get the user.txt. Now, we will try escalate to root privilege. After some enumeration, we run the command “sudo -l”, and found that user Joanna can run the following command using sudo without entering password. /bin/nano /opt/priv Which will open /opt/priv with nano in superuser privilege. Then I go to google and search for nano privilege escalation and I found a guide about privilege escalation using nano. https://gtfobins.github.io/gtfobins/nano/
- 10. So we will open /opt/priv using nano with sudo first. sudo /bin/nano /opt/priv We can run nano as root and open /opt/priv which is blank,then press ^R^X which is ctrl-r then ctrl-x We can execute command as root, we can directly view root.txt by running cat /root/root.txt But in order to gain root shell, we need to run the following command to break out from restricted environments by spawning an interactive system shell. reset; bash 1>&0 2>&0
- 11. After that we need to run “clear”, to clear out the nano UI to have a normal bash shell. And finally we got a shell in root privilege. 光復香港 時代革命