Report
Share
Download to read offline
Recommended
SSH how to 2011

Internal knowledge share on SSH setup and usage. Includes some helpful config file options to save time and how to create and use SSH keys for better security and productivity.
How to increase security with SSH

This presentation describes how to connect to the remote servers and authenticate with security keys instead of login/password
Recommended
SSH how to 2011

Internal knowledge share on SSH setup and usage. Includes some helpful config file options to save time and how to create and use SSH keys for better security and productivity.
How to increase security with SSH

This presentation describes how to connect to the remote servers and authenticate with security keys instead of login/password
Windowshadoop

install hadoop in windows using maven and windows sdk and visual c++ compiler.
To install hadoop on windows see below link step by step guidance.
From version 2.3 hadoop suppot windows also but by default it supports linux and other version. to install in windows need to compile the hadoop source in native windows sdk and then that hadoop distribution generated can be used to run hadoop in windows.
hadoop installation on windows
How to set up ssh keys on ubuntu

SSH or secure shell is an encrypted protocol used to communicate and administer with the servers. It follows simple steps to generate on ubuntu. Generating ssh keys in ubuntu, the windows operating system is moreover similar.
Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment

Leland Lammert's presentation on Nagios in a Multi-Platform Enviornment.
The presentation was given during the Nagios World Conference North America held Sept 20-Oct 2nd, 2013 in Saint Paul, MN. For more information on the conference (including photos and videos), visit: http://go.nagios.com/nwcna
tutorial-ssh.pdf

This is the best tutorial for ssh protocol and its configuration for secure communucation.
Many times when we login to a system we use a usernamepass.pdf

Many times when we login to a system, we use a username/password combination.
For example, to login to the DTCC portal, you enter a username/password combination into a web
form like what is displayed below
Another option for authentication, and one that is used by cloud computing infrastructure
environments such as AWS is to use a cryptographic key and pass the key to the server during
login.
In this lab, youll generate a cryptographic key to enable passwordless login to your Ubuntu VM.
Step 1:
Generate the keypair. On either your Windows10 VM or your Ubuntu VM, run the command: ssh-
keygen You should see output similar to the following:
Two files were created as a result of running this command:
The file id_rsa is readable ONLY by the owner because it is the RSA Private key. This file should
be guarded and treated as a password.
The other file, id_rsa.pub is the RSA public key associated with the private key file.
Step 2:
To enable login to your Ubuntu VM using the certificate (and without entering a password) copy
the id_rsa.pub file into your home directory in a file named .ssh/authorized_keys.
Step 3:
Login to your Ubuntu VM from your Windows 10 VM using the ssh command in a command
window. You will need to supply the -i option and include the name and location of your RSA
private key that you generated in step 1
Instructions
Many times when we login to a system, we use a username/password combination.
For example, to login to the DTCC portal, you enter a username/password combination into a
web form like what is displayed below
Another option for authentication, and one that is used by cloud computing infrastructure
environments such as AWS is to use a cryptographic key and pass the key to the server during
login.
In this lab, youll generate a cryptographic key to enable passwordless login to your Ubuntu VM.
Step 1:
Generate the keypair. On either your Windows10 VM or your Ubuntu VM, run the command: ssh-
keygen You should see output similar to the following:
Two files were created as a result of running this command:
The file id_rsa is readable ONLY by the owner because it is the RSA Private key. This file should
be guarded and treated as a password.
The other file, id_rsa.pub is the RSA public key associated with the private key file.
Step 2:
To enable login to your Ubuntu VM using the certificate (and without entering a password) copy
the id_rsa.pub file into your home directory in a file named .ssh/authorized_keys.
Step 3:
Login to your Ubuntu VM from your Windows 10 VM using the ssh command in a command
window. You will need to supply the -i option and include the name and location of your RSA
private key that you generated in step 1.
Discuss what is SSH and the advantages and disadvantages of using it.pdf

Discuss what is SSH and the advantages and disadvantages of using it on your Linux
distribution.
Also discuss how to control ssh access and how you configure this service.
Solution
SSH is also known as Secure Socket Shell. It is a network protocol that provides administrators
with a secure way to access a remote computer.
For advantages of it, SSH is widely used by network administrators for managing systems and
applications remotely. It allows them to log in to another computer over a network, execute
commands and move files from one computer to another.
The biggest disadvantage would be people logging in as the computer\'s administrator over SSH
and this can be done by brute force for the password.
To limit ssh access to a linux machine based on originating IP address, edit /etc/hosts.allow:.
Rasperry pi Part 12

The Raspberry Pi is a series of credit card–sized single-board computers developed in the UK by the Raspberry Pi Foundation with the intention of promoting the teaching of basic computer science in schools.
The original Raspberry Pi and Raspberry Pi 2 are manufactured in several board configurations through licensed manufacturing agreements with Newark element14 (Premier Farnell), RS Components and Egoman. These companies sell the Raspberry Pi online. Egoman produces a version for distribution solely in China and Taiwan, which can be distinguished from other Pis by their red colouring and lack of FCC/CE marks. The hardware is the same across all manufacturers.
The original Raspberry Pi is based on the Broadcom BCM2835 system on a chip (SoC), which includes an ARM1176JZF-S 700 MHz processor, VideoCore IV GPU, and was originally shipped with 256 megabytes of RAM, later upgraded (models B and B+) to 512 MB. The system has Secure Digital (SD) (models A and B) or MicroSD (models A+ and B+) sockets for boot media and persistent storage.
Up and Running SSH Service - Part 2

Webinar topic: Up and Running SSH Service
Presenter: Achmad Mardiansyah, M. Taufik Nurhuda
In this webinar series, Up and Running SSH Service
Please share your feedback or webinar ideas here: http://bit.ly/glcfeedback
Check our schedule for future events: https://www.glcnetworks.com/en/schedule/
Follow our social media for updates: Facebook, Instagram, YouTube Channel, and telegram also discord
Recording available on Youtube
https://youtu.be/8Y0NsleBFRg
Using Secure Shell on Linux: What Everyone Should Know

Secure Shell, or SSH, is a network protocol that allows data to be exchanged over a secure channel. SSH is much more than just data being passed over the wire. SSH can be used to tunnel traffic and specific ports or applications across multiple servers. SSH is a must for anyone using Linux. If you haven't used SSH, then you have not used Linux!
This session is designed for all technical staff or decision makers curious about great Linux tools and making access to Windows services, remote desktops and remote servers easier and less complicated. During this session, we will demonstrate techniques to tunnel RDP sessions, SOAP sessions and HTTP sessions between remote systems.
Copie de Robotic Workshop Infographics by Slidesgo.pptx

Copie de Robotic Workshop Infographics by Slidesgo
More Related Content
Similar to SSH.pdf
Windowshadoop

install hadoop in windows using maven and windows sdk and visual c++ compiler.
To install hadoop on windows see below link step by step guidance.
From version 2.3 hadoop suppot windows also but by default it supports linux and other version. to install in windows need to compile the hadoop source in native windows sdk and then that hadoop distribution generated can be used to run hadoop in windows.
hadoop installation on windows
How to set up ssh keys on ubuntu

SSH or secure shell is an encrypted protocol used to communicate and administer with the servers. It follows simple steps to generate on ubuntu. Generating ssh keys in ubuntu, the windows operating system is moreover similar.
Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment

Leland Lammert's presentation on Nagios in a Multi-Platform Enviornment.
The presentation was given during the Nagios World Conference North America held Sept 20-Oct 2nd, 2013 in Saint Paul, MN. For more information on the conference (including photos and videos), visit: http://go.nagios.com/nwcna
tutorial-ssh.pdf

This is the best tutorial for ssh protocol and its configuration for secure communucation.
Many times when we login to a system we use a usernamepass.pdf

Many times when we login to a system, we use a username/password combination.
For example, to login to the DTCC portal, you enter a username/password combination into a web
form like what is displayed below
Another option for authentication, and one that is used by cloud computing infrastructure
environments such as AWS is to use a cryptographic key and pass the key to the server during
login.
In this lab, youll generate a cryptographic key to enable passwordless login to your Ubuntu VM.
Step 1:
Generate the keypair. On either your Windows10 VM or your Ubuntu VM, run the command: ssh-
keygen You should see output similar to the following:
Two files were created as a result of running this command:
The file id_rsa is readable ONLY by the owner because it is the RSA Private key. This file should
be guarded and treated as a password.
The other file, id_rsa.pub is the RSA public key associated with the private key file.
Step 2:
To enable login to your Ubuntu VM using the certificate (and without entering a password) copy
the id_rsa.pub file into your home directory in a file named .ssh/authorized_keys.
Step 3:
Login to your Ubuntu VM from your Windows 10 VM using the ssh command in a command
window. You will need to supply the -i option and include the name and location of your RSA
private key that you generated in step 1
Instructions
Many times when we login to a system, we use a username/password combination.
For example, to login to the DTCC portal, you enter a username/password combination into a
web form like what is displayed below
Another option for authentication, and one that is used by cloud computing infrastructure
environments such as AWS is to use a cryptographic key and pass the key to the server during
login.
In this lab, youll generate a cryptographic key to enable passwordless login to your Ubuntu VM.
Step 1:
Generate the keypair. On either your Windows10 VM or your Ubuntu VM, run the command: ssh-
keygen You should see output similar to the following:
Two files were created as a result of running this command:
The file id_rsa is readable ONLY by the owner because it is the RSA Private key. This file should
be guarded and treated as a password.
The other file, id_rsa.pub is the RSA public key associated with the private key file.
Step 2:
To enable login to your Ubuntu VM using the certificate (and without entering a password) copy
the id_rsa.pub file into your home directory in a file named .ssh/authorized_keys.
Step 3:
Login to your Ubuntu VM from your Windows 10 VM using the ssh command in a command
window. You will need to supply the -i option and include the name and location of your RSA
private key that you generated in step 1.
Discuss what is SSH and the advantages and disadvantages of using it.pdf

Discuss what is SSH and the advantages and disadvantages of using it on your Linux
distribution.
Also discuss how to control ssh access and how you configure this service.
Solution
SSH is also known as Secure Socket Shell. It is a network protocol that provides administrators
with a secure way to access a remote computer.
For advantages of it, SSH is widely used by network administrators for managing systems and
applications remotely. It allows them to log in to another computer over a network, execute
commands and move files from one computer to another.
The biggest disadvantage would be people logging in as the computer\'s administrator over SSH
and this can be done by brute force for the password.
To limit ssh access to a linux machine based on originating IP address, edit /etc/hosts.allow:.
Rasperry pi Part 12

The Raspberry Pi is a series of credit card–sized single-board computers developed in the UK by the Raspberry Pi Foundation with the intention of promoting the teaching of basic computer science in schools.
The original Raspberry Pi and Raspberry Pi 2 are manufactured in several board configurations through licensed manufacturing agreements with Newark element14 (Premier Farnell), RS Components and Egoman. These companies sell the Raspberry Pi online. Egoman produces a version for distribution solely in China and Taiwan, which can be distinguished from other Pis by their red colouring and lack of FCC/CE marks. The hardware is the same across all manufacturers.
The original Raspberry Pi is based on the Broadcom BCM2835 system on a chip (SoC), which includes an ARM1176JZF-S 700 MHz processor, VideoCore IV GPU, and was originally shipped with 256 megabytes of RAM, later upgraded (models B and B+) to 512 MB. The system has Secure Digital (SD) (models A and B) or MicroSD (models A+ and B+) sockets for boot media and persistent storage.
Up and Running SSH Service - Part 2

Webinar topic: Up and Running SSH Service
Presenter: Achmad Mardiansyah, M. Taufik Nurhuda
In this webinar series, Up and Running SSH Service
Please share your feedback or webinar ideas here: http://bit.ly/glcfeedback
Check our schedule for future events: https://www.glcnetworks.com/en/schedule/
Follow our social media for updates: Facebook, Instagram, YouTube Channel, and telegram also discord
Recording available on Youtube
https://youtu.be/8Y0NsleBFRg
Using Secure Shell on Linux: What Everyone Should Know

Secure Shell, or SSH, is a network protocol that allows data to be exchanged over a secure channel. SSH is much more than just data being passed over the wire. SSH can be used to tunnel traffic and specific ports or applications across multiple servers. SSH is a must for anyone using Linux. If you haven't used SSH, then you have not used Linux!
This session is designed for all technical staff or decision makers curious about great Linux tools and making access to Windows services, remote desktops and remote servers easier and less complicated. During this session, we will demonstrate techniques to tunnel RDP sessions, SOAP sessions and HTTP sessions between remote systems.
Similar to SSH.pdf (20)
Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment

Nagios Conference 2013 - Leland Lammert - Nagios in a Multi-Platform Enviornment
Many times when we login to a system we use a usernamepass.pdf

Many times when we login to a system we use a usernamepass.pdf
Discuss what is SSH and the advantages and disadvantages of using it.pdf

Discuss what is SSH and the advantages and disadvantages of using it.pdf
Using Secure Shell on Linux: What Everyone Should Know

Using Secure Shell on Linux: What Everyone Should Know
More from AnisSalhi3
Copie de Robotic Workshop Infographics by Slidesgo.pptx

Copie de Robotic Workshop Infographics by Slidesgo
Research Proposal Business Presentation in Dark Green Orange Geometric Style.pdf

Research Proposal Business Presentation in Dark Green Orange Geometric Style
Copie de Introduction to Coding Workshop by Slidesgo.pptx

Copie de Introduction to Coding Workshop by Slidesgo
JFTL-2018-Comment-mettre-en-place-des-plateformes-de-test-gr__ce-__-Docker.pptx

JFTL-2018-Comment-mettre-en-place-des-plateformes-de-test-gr__ce-__-Docker.pptx
More from AnisSalhi3 (9)
Copie de Robotic Workshop Infographics by Slidesgo.pptx

Copie de Robotic Workshop Infographics by Slidesgo.pptx
Research Proposal Business Presentation in Dark Green Orange Geometric Style.pdf

Research Proposal Business Presentation in Dark Green Orange Geometric Style.pdf
Copie de Introduction to Coding Workshop by Slidesgo.pptx

Copie de Introduction to Coding Workshop by Slidesgo.pptx
JFTL-2018-Comment-mettre-en-place-des-plateformes-de-test-gr__ce-__-Docker.pptx

JFTL-2018-Comment-mettre-en-place-des-plateformes-de-test-gr__ce-__-Docker.pptx
Recently uploaded
The geography of Taylor Swift - some ideas

Geographical themes connected with Taylor Swift's ERAS tour - coming to the UK in June 2024
Palestine last event orientationfvgnh .pptx

An EFL lesson about the current events in Palestine. It is intended to be for intermediate students who wish to increase their listening skills through a short lesson in power point.
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptxMohd Adib Abd Muin, Senior Lecturer at Universiti Utara Malaysia
This slide is prepared for master's students (MIFB & MIBS) UUM. May it be useful to all.BÀI TẬP BỔ TRỢ TIẾNG ANH GLOBAL SUCCESS LỚP 3 - CẢ NĂM (CÓ FILE NGHE VÀ ĐÁP Á...

BÀI TẬP BỔ TRỢ TIẾNG ANH GLOBAL SUCCESS LỚP 3 - CẢ NĂM (CÓ FILE NGHE VÀ ĐÁP Á...Nguyen Thanh Tu Collection
https://app.box.com/s/hqnndn05v4q5a4k4jd597rkdbda0fniiThe French Revolution Class 9 Study Material pdf free download

The French Revolution, which began in 1789, was a period of radical social and political upheaval in France. It marked the decline of absolute monarchies, the rise of secular and democratic republics, and the eventual rise of Napoleon Bonaparte. This revolutionary period is crucial in understanding the transition from feudalism to modernity in Europe.
For more information, visit-www.vavaclasses.com
Digital Tools and AI for Teaching Learning and Research

This Presentation in details discusses on Digital Tools and AI for Teaching Learning and Research
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH ANSWERS.
Instructions for Submissions thorugh G- Classroom.pptx

This presentation provides a briefing on how to upload submissions and documents in Google Classroom. It was prepared as part of an orientation for new Sainik School in-service teacher trainees. As a training officer, my goal is to ensure that you are comfortable and proficient with this essential tool for managing assignments and fostering student engagement.
special B.ed 2nd year old paper_20240531.pdf

Instagram:-
https://instagram.com/special_education_needs_01?igshid=YmMyMTA2M2Y=
WhatsApp:-
https://chat.whatsapp.com/JVakNIYlSV94x7bwunO3Dc
YouTube:-
https://youtube.com/@special_education_needs
Teligram :- https://t.me/special_education_needs
Slide Shere :-
https://www.slideshare.net/shabnambano20?utm_campaign=profiletracking&utm_medium=sssite&utm_source=ssslideview
The Roman Empire A Historical Colossus.pdf

The Roman Empire, a vast and enduring power, stands as one of history's most remarkable civilizations, leaving an indelible imprint on the world. It emerged from the Roman Republic, transitioning into an imperial powerhouse under the leadership of Augustus Caesar in 27 BCE. This transformation marked the beginning of an era defined by unprecedented territorial expansion, architectural marvels, and profound cultural influence.
The empire's roots lie in the city of Rome, founded, according to legend, by Romulus in 753 BCE. Over centuries, Rome evolved from a small settlement to a formidable republic, characterized by a complex political system with elected officials and checks on power. However, internal strife, class conflicts, and military ambitions paved the way for the end of the Republic. Julius Caesar’s dictatorship and subsequent assassination in 44 BCE created a power vacuum, leading to a civil war. Octavian, later Augustus, emerged victorious, heralding the Roman Empire’s birth.
Under Augustus, the empire experienced the Pax Romana, a 200-year period of relative peace and stability. Augustus reformed the military, established efficient administrative systems, and initiated grand construction projects. The empire's borders expanded, encompassing territories from Britain to Egypt and from Spain to the Euphrates. Roman legions, renowned for their discipline and engineering prowess, secured and maintained these vast territories, building roads, fortifications, and cities that facilitated control and integration.
The Roman Empire’s society was hierarchical, with a rigid class system. At the top were the patricians, wealthy elites who held significant political power. Below them were the plebeians, free citizens with limited political influence, and the vast numbers of slaves who formed the backbone of the economy. The family unit was central, governed by the paterfamilias, the male head who held absolute authority.
Culturally, the Romans were eclectic, absorbing and adapting elements from the civilizations they encountered, particularly the Greeks. Roman art, literature, and philosophy reflected this synthesis, creating a rich cultural tapestry. Latin, the Roman language, became the lingua franca of the Western world, influencing numerous modern languages.
Roman architecture and engineering achievements were monumental. They perfected the arch, vault, and dome, constructing enduring structures like the Colosseum, Pantheon, and aqueducts. These engineering marvels not only showcased Roman ingenuity but also served practical purposes, from public entertainment to water supply.
Unit 2- Research Aptitude (UGC NET Paper I).pdf

This slide describes the research aptitude of unit 2 in the UGC NET paper I.
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk from the OECD’s Centre for Educational Research and Innovation presents at the Ask an Expert Webinar: How can education support child empowerment?
Acetabularia Information For Class 9 .docx

Acetabularia acetabulum is a single-celled green alga that in its vegetative state is morphologically differentiated into a basal rhizoid and an axially elongated stalk, which bears whorls of branching hairs. The single diploid nucleus resides in the rhizoid.
Synthetic Fiber Construction in lab .pptx

Synthetic fiber production is a fascinating and complex field that blends chemistry, engineering, and environmental science. By understanding these aspects, students can gain a comprehensive view of synthetic fiber production, its impact on society and the environment, and the potential for future innovations. Synthetic fibers play a crucial role in modern society, impacting various aspects of daily life, industry, and the environment. ynthetic fibers are integral to modern life, offering a range of benefits from cost-effectiveness and versatility to innovative applications and performance characteristics. While they pose environmental challenges, ongoing research and development aim to create more sustainable and eco-friendly alternatives. Understanding the importance of synthetic fibers helps in appreciating their role in the economy, industry, and daily life, while also emphasizing the need for sustainable practices and innovation.
Recently uploaded (20)
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptx
BÀI TẬP BỔ TRỢ TIẾNG ANH GLOBAL SUCCESS LỚP 3 - CẢ NĂM (CÓ FILE NGHE VÀ ĐÁP Á...

BÀI TẬP BỔ TRỢ TIẾNG ANH GLOBAL SUCCESS LỚP 3 - CẢ NĂM (CÓ FILE NGHE VÀ ĐÁP Á...
The French Revolution Class 9 Study Material pdf free download

The French Revolution Class 9 Study Material pdf free download
Digital Tools and AI for Teaching Learning and Research

Digital Tools and AI for Teaching Learning and Research
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...
Instructions for Submissions thorugh G- Classroom.pptx

Instructions for Submissions thorugh G- Classroom.pptx
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk - How can education support child empowerment.pptx
Adversarial Attention Modeling for Multi-dimensional Emotion Regression.pdf

Adversarial Attention Modeling for Multi-dimensional Emotion Regression.pdf
SSH.pdf
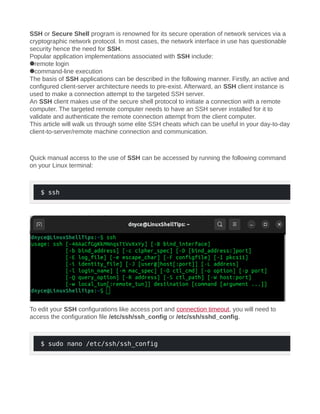
- 1. SSH or Secure Shell program is renowned for its secure operation of network services via a cryptographic network protocol. In most cases, the network interface in use has questionable security hence the need for SSH. Popular application implementations associated with SSH include: remote login command-line execution The basis of SSH applications can be described in the following manner. Firstly, an active and configured client-server architecture needs to pre-exist. Afterward, an SSH client instance is used to make a connection attempt to the targeted SSH server. An SSH client makes use of the secure shell protocol to initiate a connection with a remote computer. The targeted remote computer needs to have an SSH server installed for it to validate and authenticate the remote connection attempt from the client computer. This article will walk us through some elite SSH cheats which can be useful in your day-to-day client-to-server/remote machine connection and communication. Quick manual access to the use of SSH can be accessed by running the following command on your Linux terminal: $ ssh To edit your SSH configurations like access port and connection timeout, you will need to access the configuration file /etc/ssh/ssh_config or /etc/ssh/sshd_config. $ sudo nano /etc/ssh/ssh_config
- 2. OR $ sudo vim /etc/ssh/sshd_config To access a remote/server machine from a client machine via SSH, you will need to adhere to the following command implementation: $ ssh username@remote_ip_address
- 3. You will then be prompted for a password associated with the remote machine’s user before gaining access. Useful SSH Cheat Sheet for Linux Other than gaining direct access to a remote machine and editing the SSH configuration file to your preference, the following SSH cheats have been proven to be very useful in your client-to-remote machine communication. Generate SSH-Keygen It is a recommendation to make use of the ed25519 algorithm while generating SSH keys. Consider the implementation below using a random email address: $ ssh-keygen -t ed25519 -C "linuxshelltips@gmail.com"
- 4. For compatibility reasons, you might decide to generate the key via RSA as demonstrated below: $ ssh-keygen -t rsa -b 4096 -C "user@linuxshelltips.com" The -C flag associates each public key with a comment making it easy to link an email address to its rightful public key. During SSH key generation, always remember to associate each private key with a passphrase for security purposes.
- 5. Connect Server Using SSH Keys To connect to a remote machine via a specific private key, refer to the following command implementation: For ed25519 algorithm generated private keys: $ ssh -i $HOME/.ssh/id_ed25519 ubuntu@192.168.100.29
- 6. For RSA-generated private keys: $ ssh -i $HOME/.ssh/id_rsa ubuntu@192.168.100.29 Connect Server Using Authorized Keys If you aim to use your SSH keys (public keys) with a server system or service like Github, you will need to append a copy of the keys with the file ~/.ssh/authorized_keys on the remote/server system as demonstrated below.
- 7. $ cat ~/.ssh/id_rsa.pub | ssh ubuntu@192.168.100.29 "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys" Alternatively, the following command also works: $ ssh-copy-id ubuntu@192.168.100.29 From here, we can connect to the remote machine without being prompted for a password: $ ssh ubuntu@192.168.100.29
- 8. SCP Commands for Upload/Download Files When wanting to perform file uploads on remote machines: $ scp simple.txt ubuntu@192.168.100.29:/home/ubuntu/Downloads When wanting to perform recursive local folder/directory upload to a remote machine: $ scp -rp mypackage ubuntu@192.168.100.29:/home/ubuntu/Downloads
- 9. Downloading/retrieving a file from a remote machine: $ scp ubuntu@192.168.100.29:/home/ubuntu/Downloads/simple.txt /home/dnyce/Downloads Downloading/retrieving a folder/directory recursively from a remote machine: $ scp -rp ubuntu@192.168.100.29:/home/ubuntu/Downloads/mypackage /home/dnyce/Downloads
- 10. Using Non-Standard SSH Ports If the SSH server is running on a non-standard port like 3333, your connection should be implemented in the following manner: $ ssh -p 3333 ubuntu@192.168.100.29 Running Commands on Remote Machines If we want to execute a command on the remote machine like a system update or ping command after a successful SSH connection, we will implement the following command: $ ssh -t ubuntu@192.168.100.29 'sudo apt update' Because we are executing a sudo-privileged command, you will be asked for a user password.