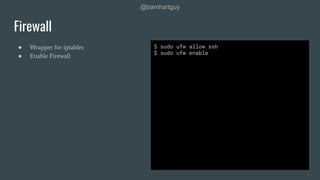
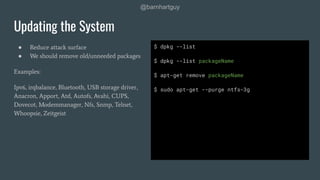
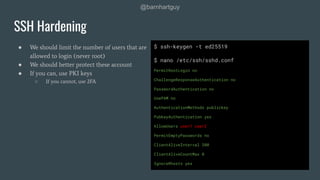
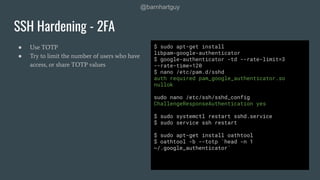
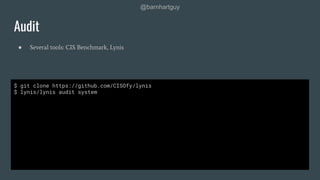
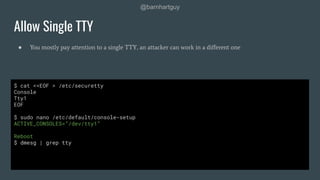
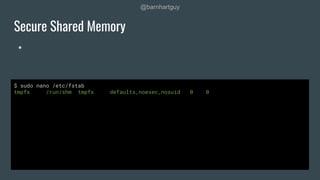
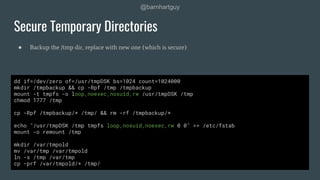
The document discusses hardening Linux servers against security threats. It begins by introducing the speaker and explaining the importance of hardening systems assuming an attacker has gained access. It then provides recommendations for various hardening techniques including: updating systems, removing unnecessary packages and users, securing SSH access, configuring firewalls and remote logging, auditing systems, and restricting access to things like temporary directories and compilers. The document is a guide that walks through steps to harden a Linux server across several areas.







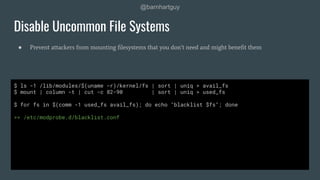
![@barnhartguy
● Prevent attackers from compiling code to get
higher order abilities
Disable Compilers
>>
COMPILERS=(
"/usr/bin/byacc"
"/usr/bin/yacc"
"/usr/bin/bcc"
"/usr/bin/kgcc"
"/usr/bin/cc"
"/usr/bin/gcc"
"/usr/bin/c++"
"/usr/bin/g++"
)
for compiler in ${COMPILERS[@]}; do
if [ -f ${compiler} ]; then
echo "removing ${compiler}
chmod 000 ${compiler}
else
echo "missing ${compiler}
fi
done](https://image.slidesharecdn.com/yalladevops-linuxhardeningmadeeasy-191016193033/85/Linux-Hardening-Made-Easy-25-320.jpg)
