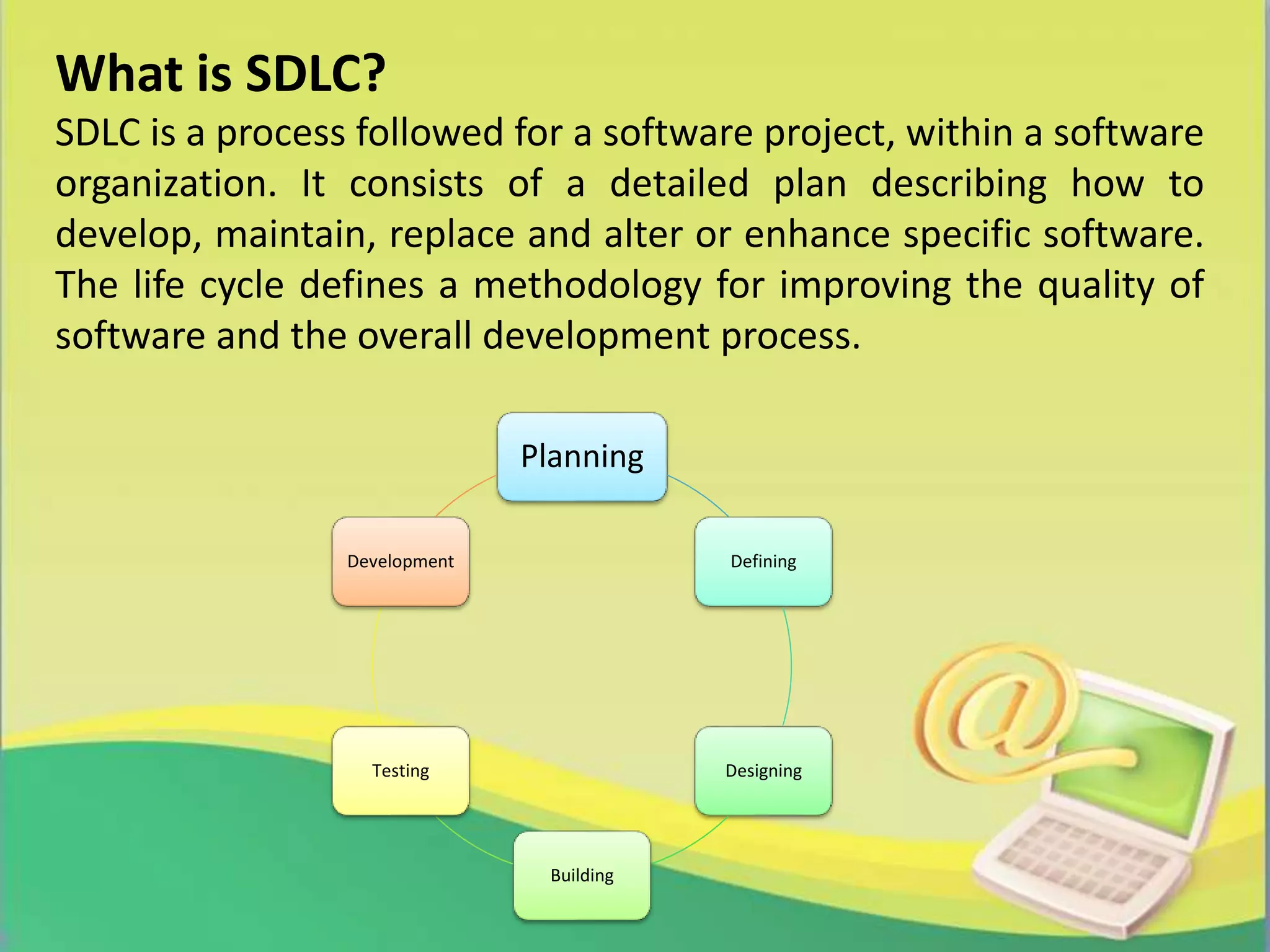
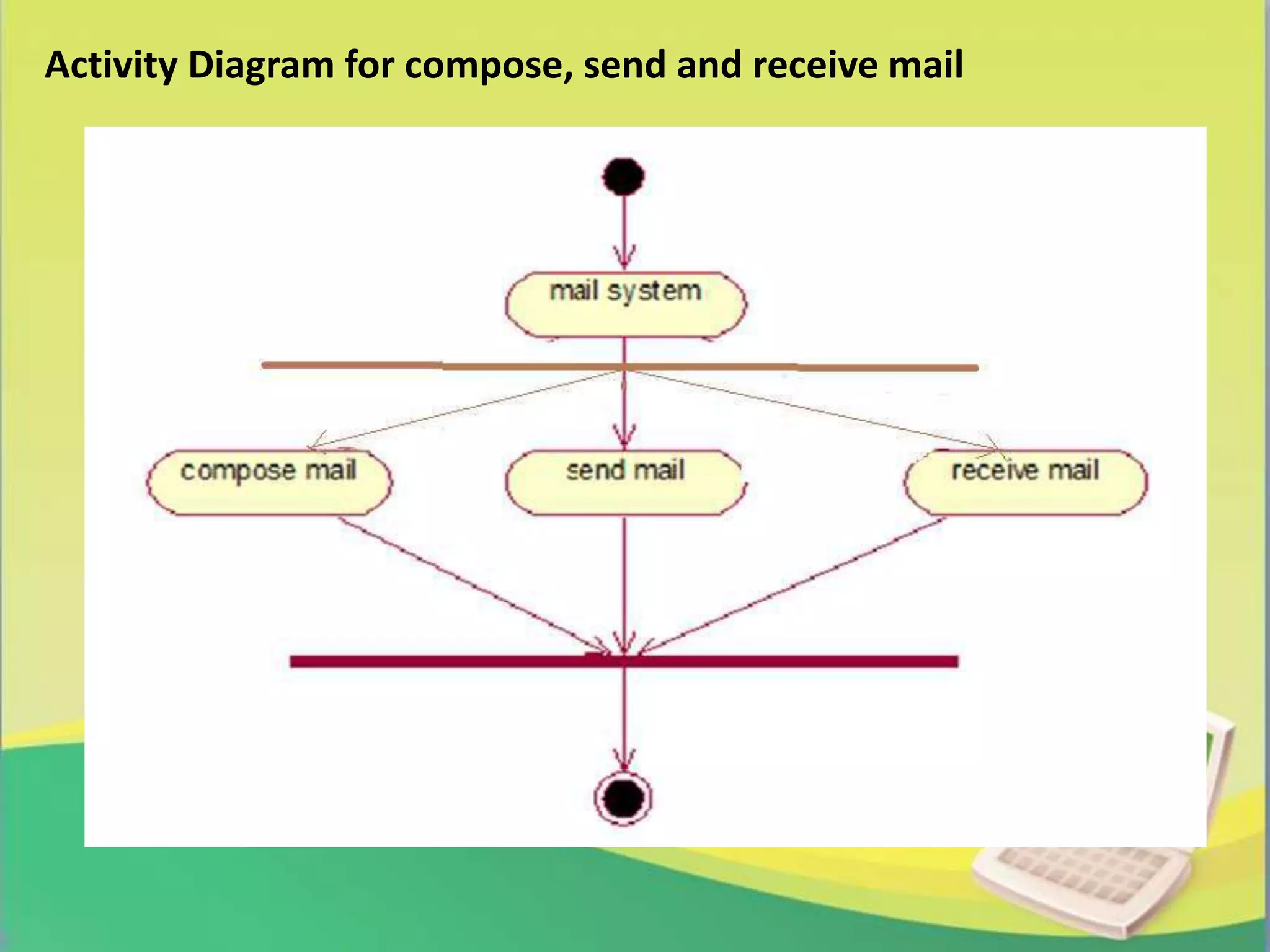
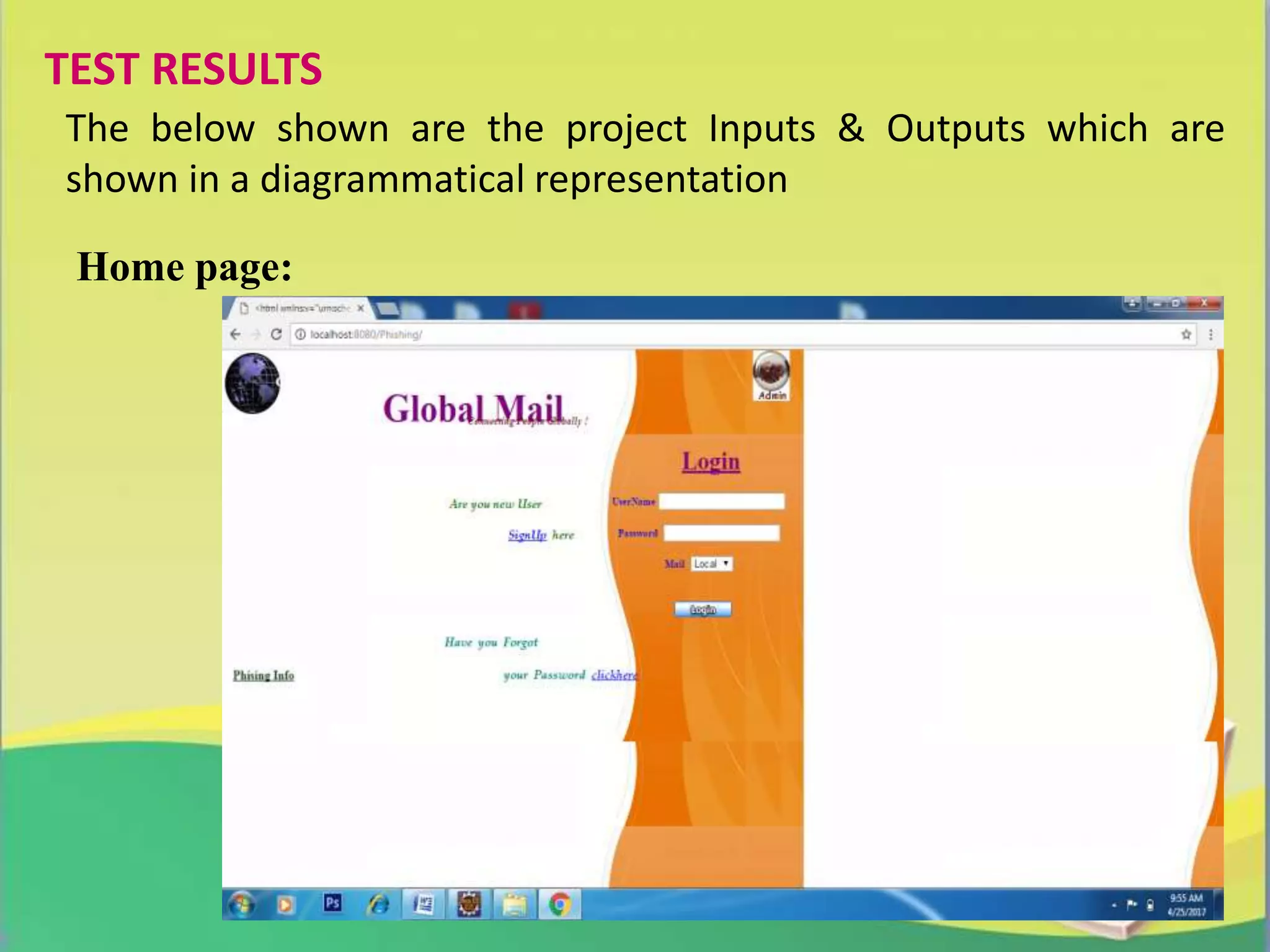
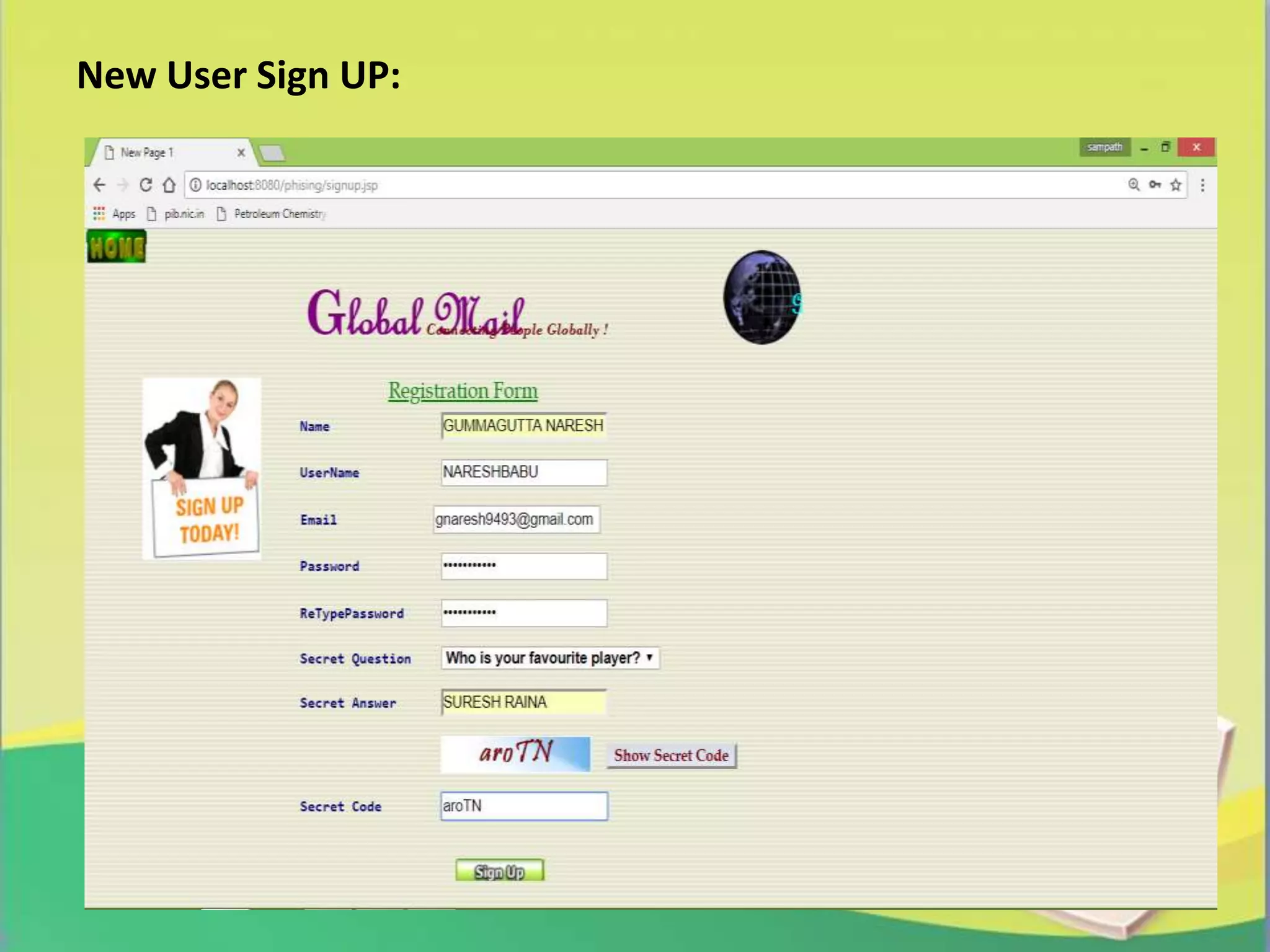
The report presents a project on 'Link Guard', an end-host based algorithm for detecting and preventing phishing attacks by analyzing the characteristics of phishing hyperlinks. It identifies common features of phishing links and proposes a software solution to help users recognize phishing attempts, achieving a 96% detection rate for unknown attacks. The study emphasizes the growing threat of phishing and the need for effective prevention methods in network security.