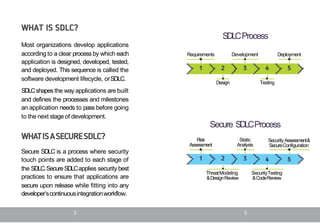
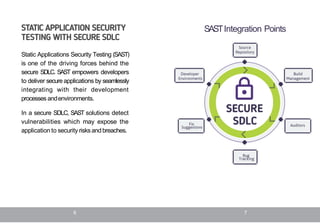
The document provides an overview of application security concepts and terms for beginners. It defines key terms like the software development lifecycle (SDLC) and secure SDLC, which incorporates security best practices into each stage of development. It also describes common application security testing methods like static application security testing (SAST) and dynamic application security testing (DAST). Finally, it outlines some common application security threats like SQL injection, cross-site scripting, and cross-site request forgery and their potential impacts.