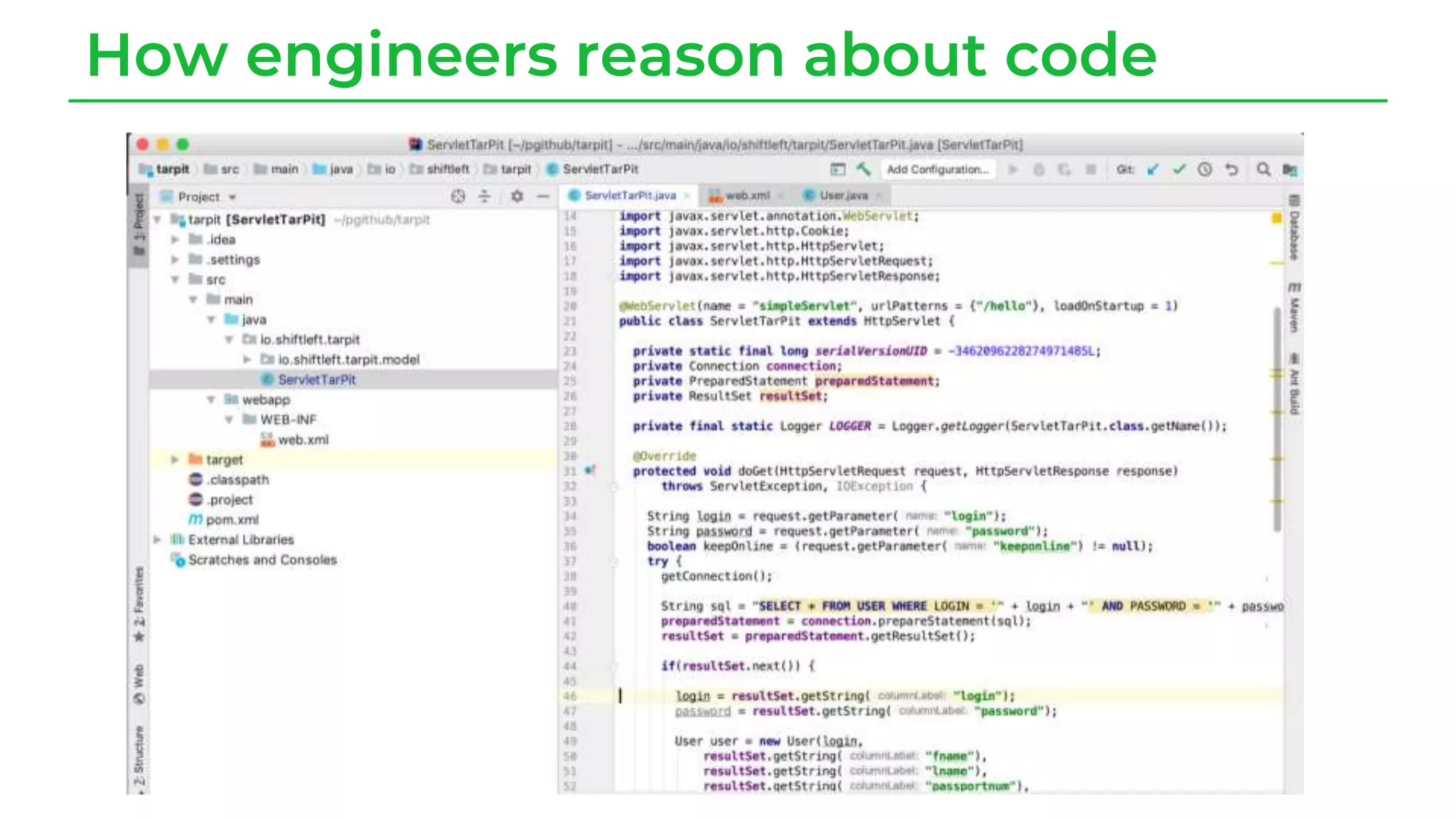
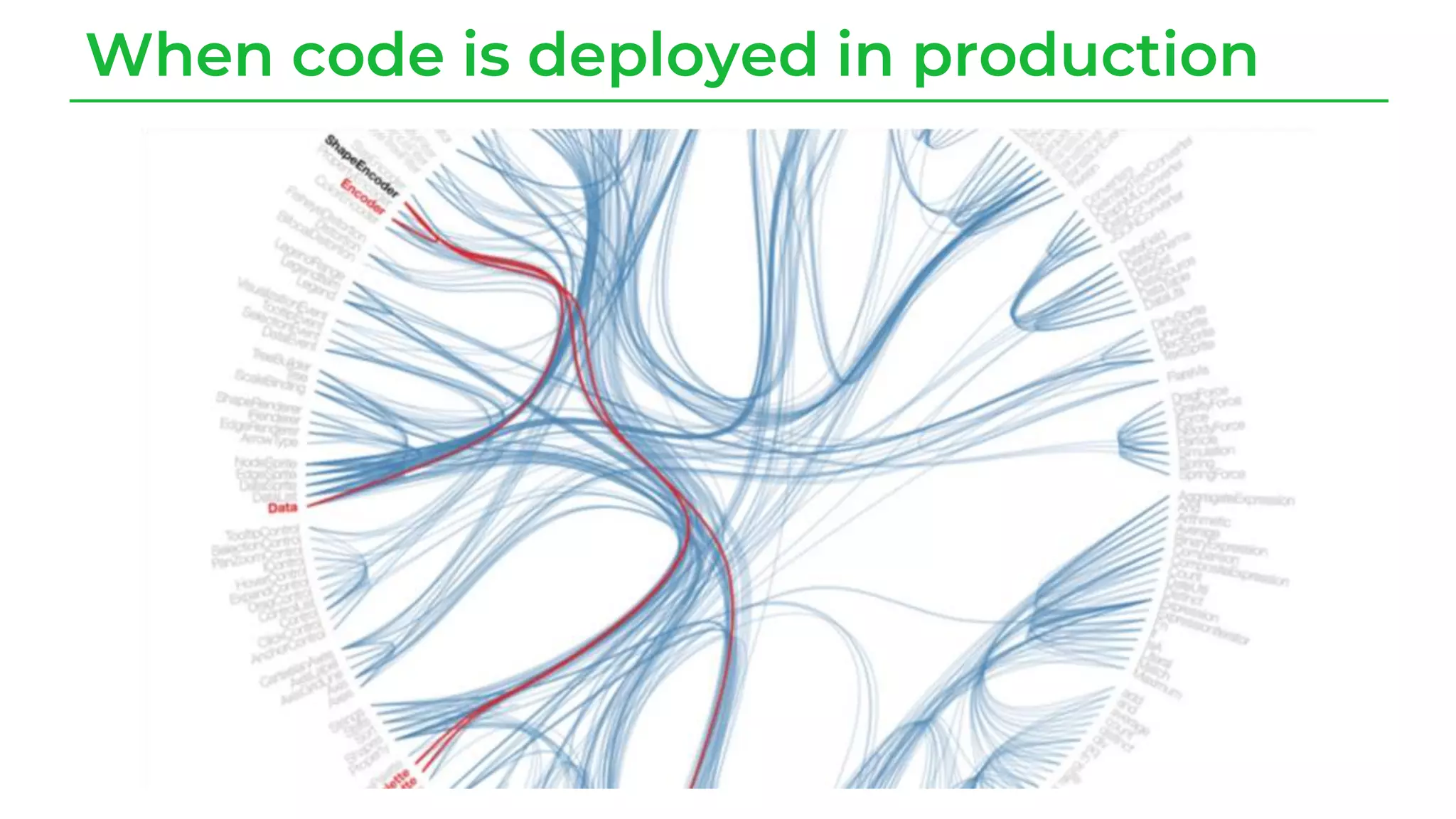
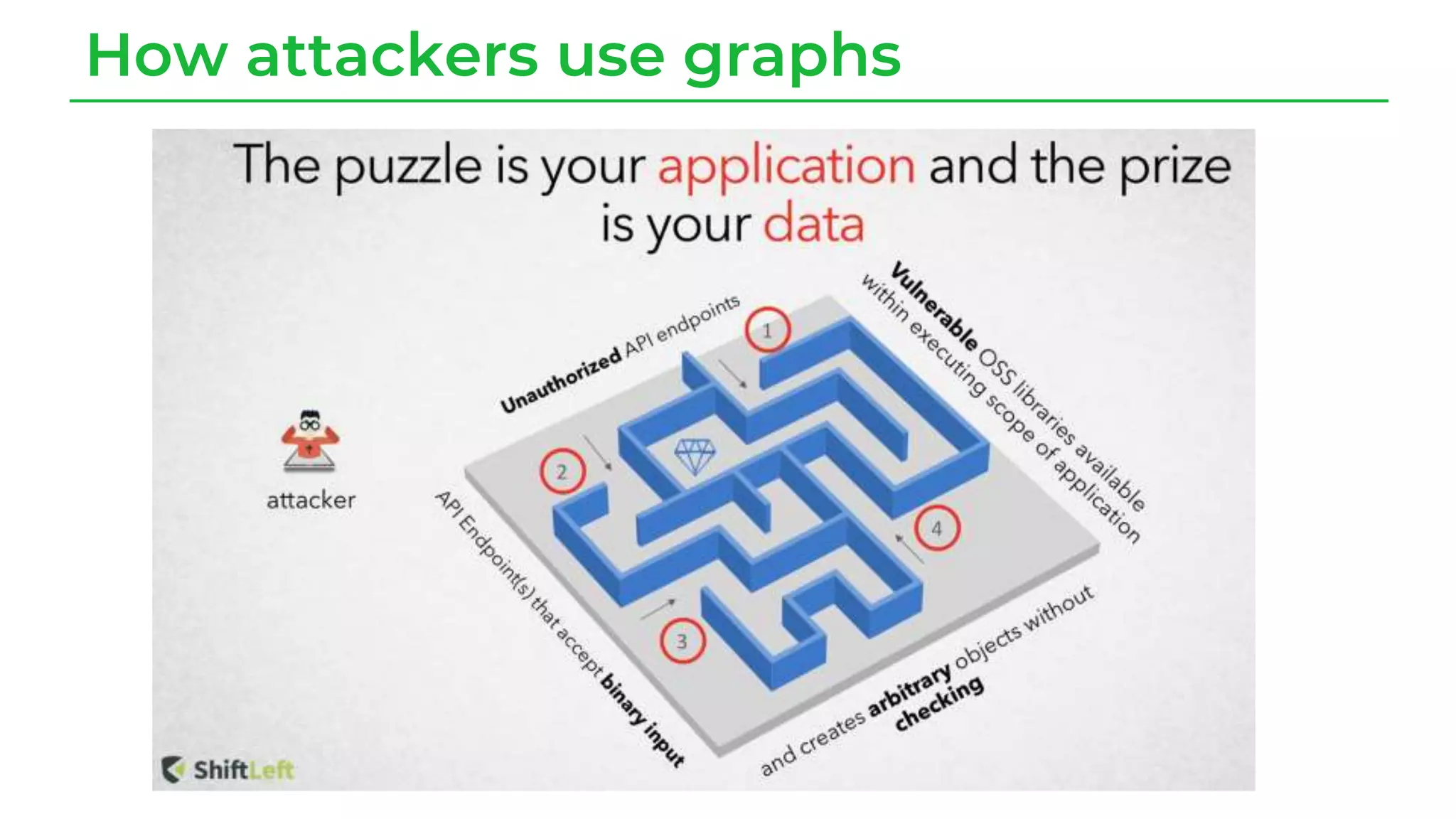
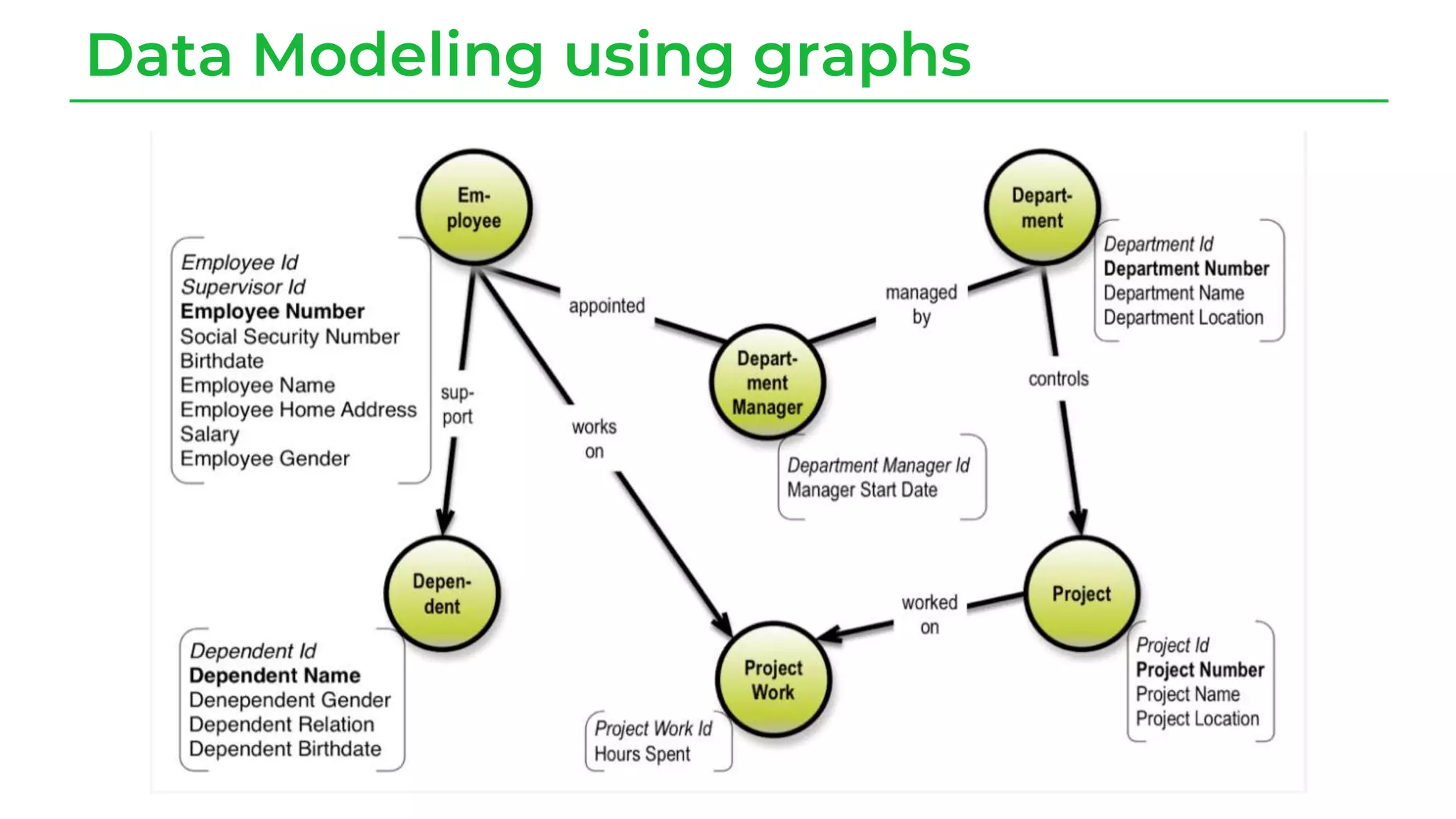
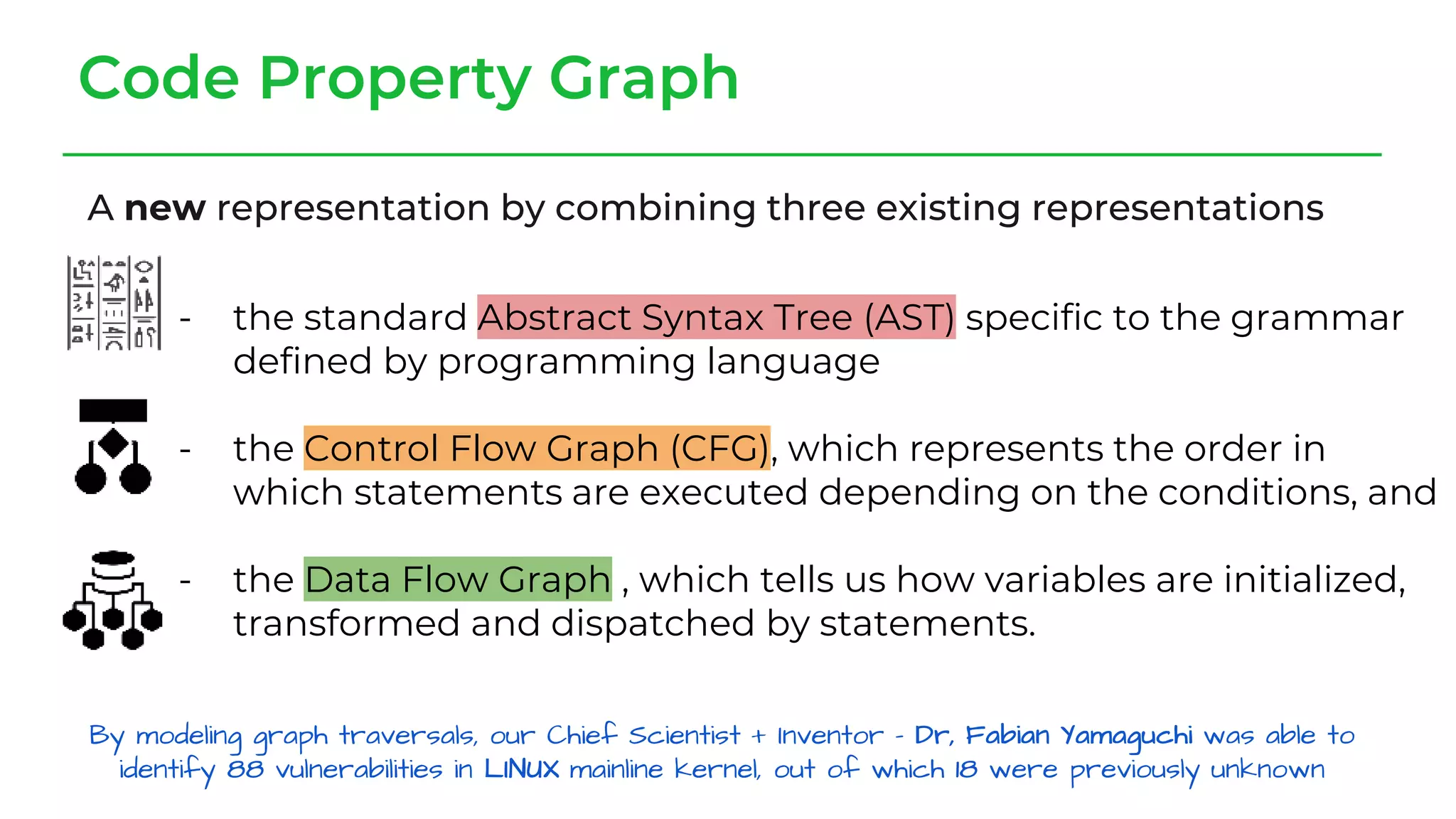
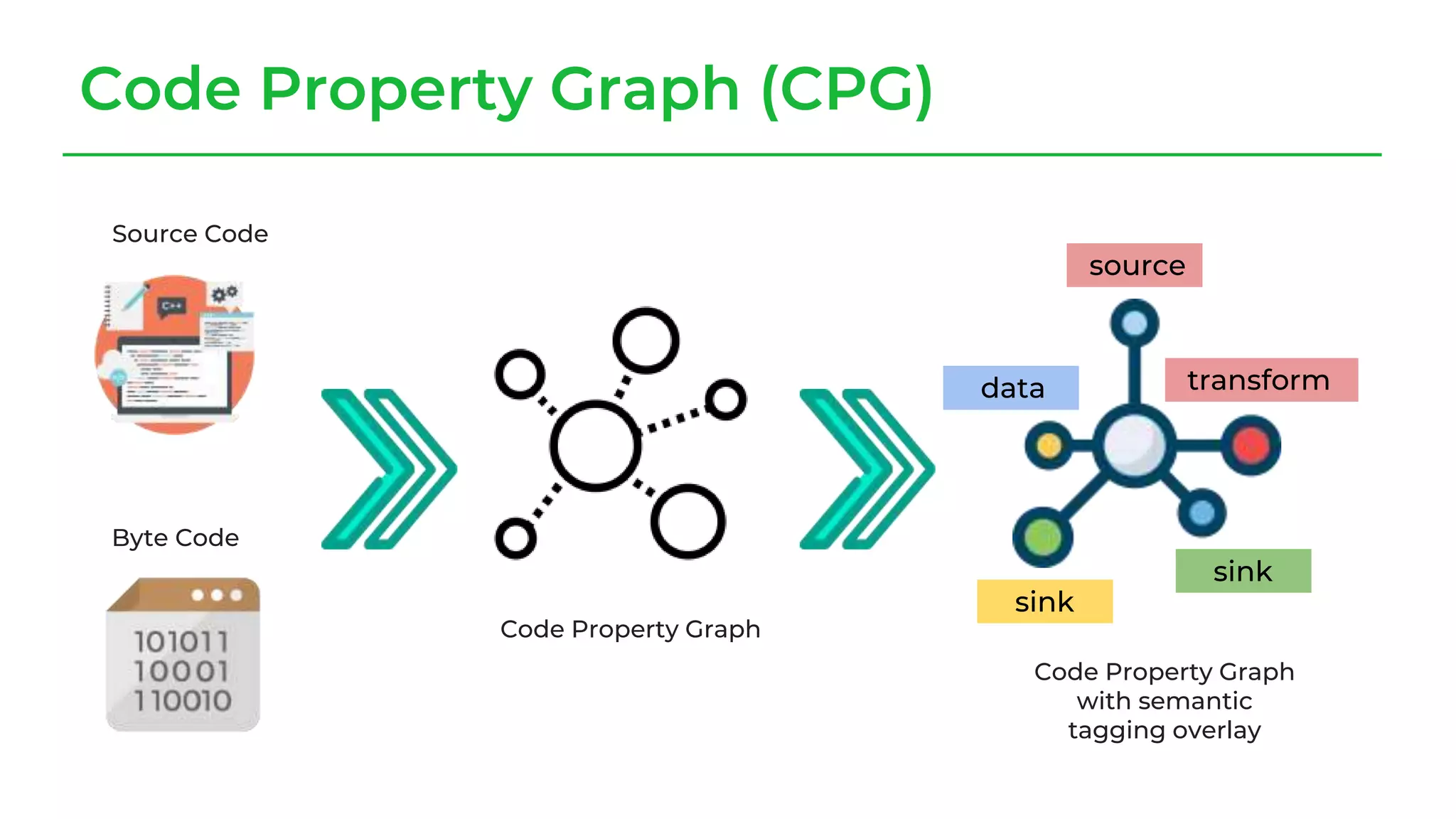
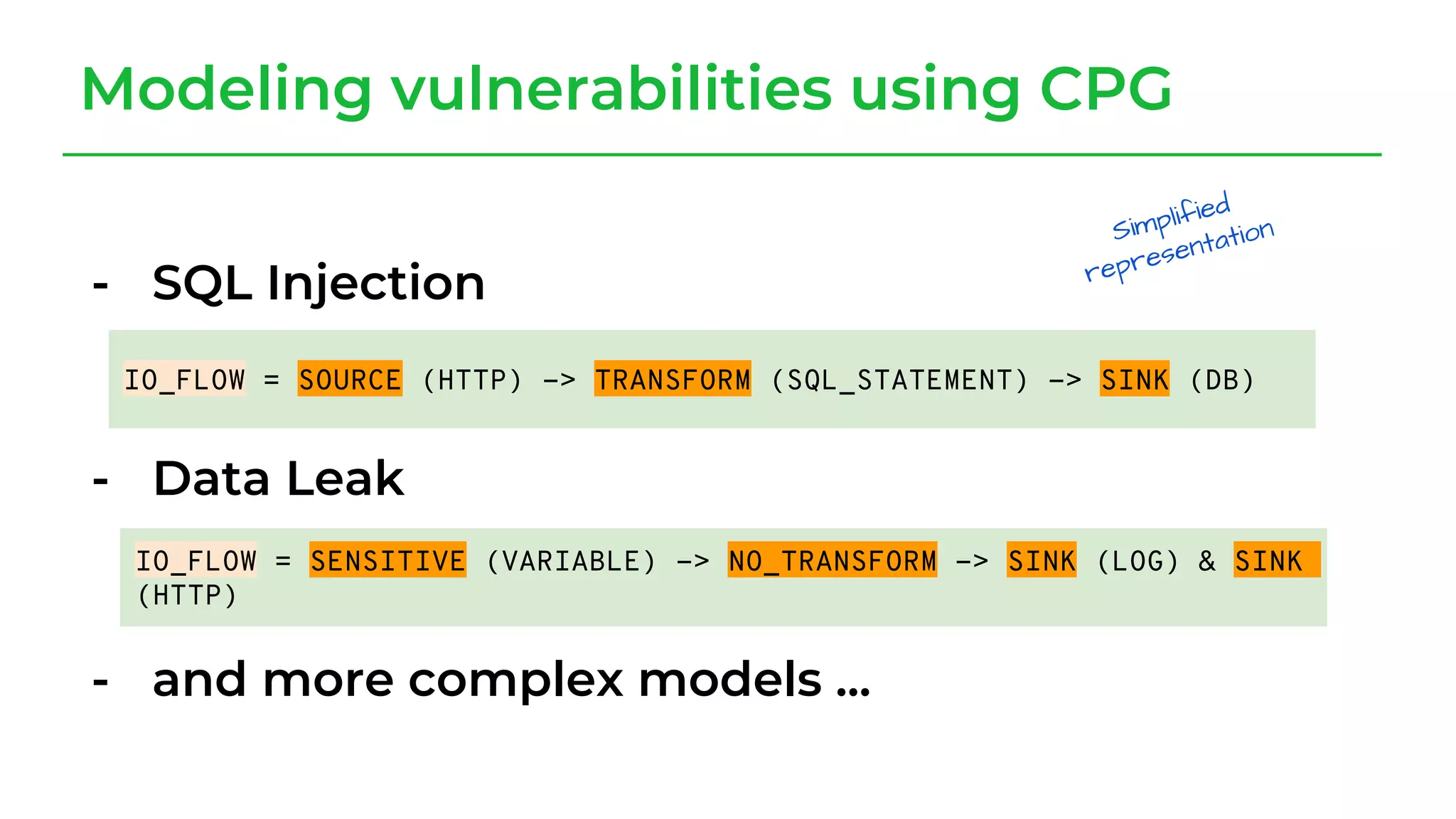
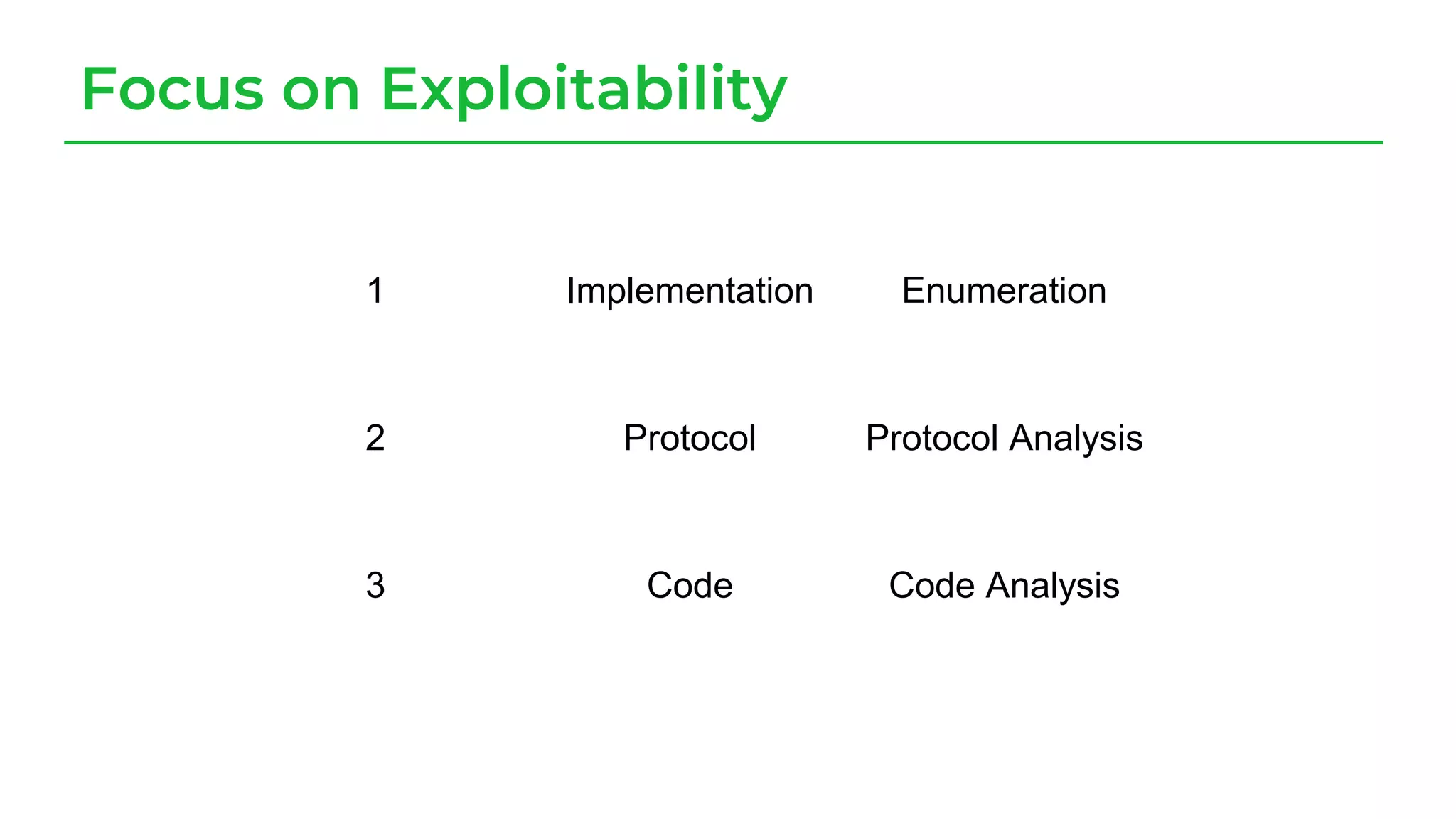
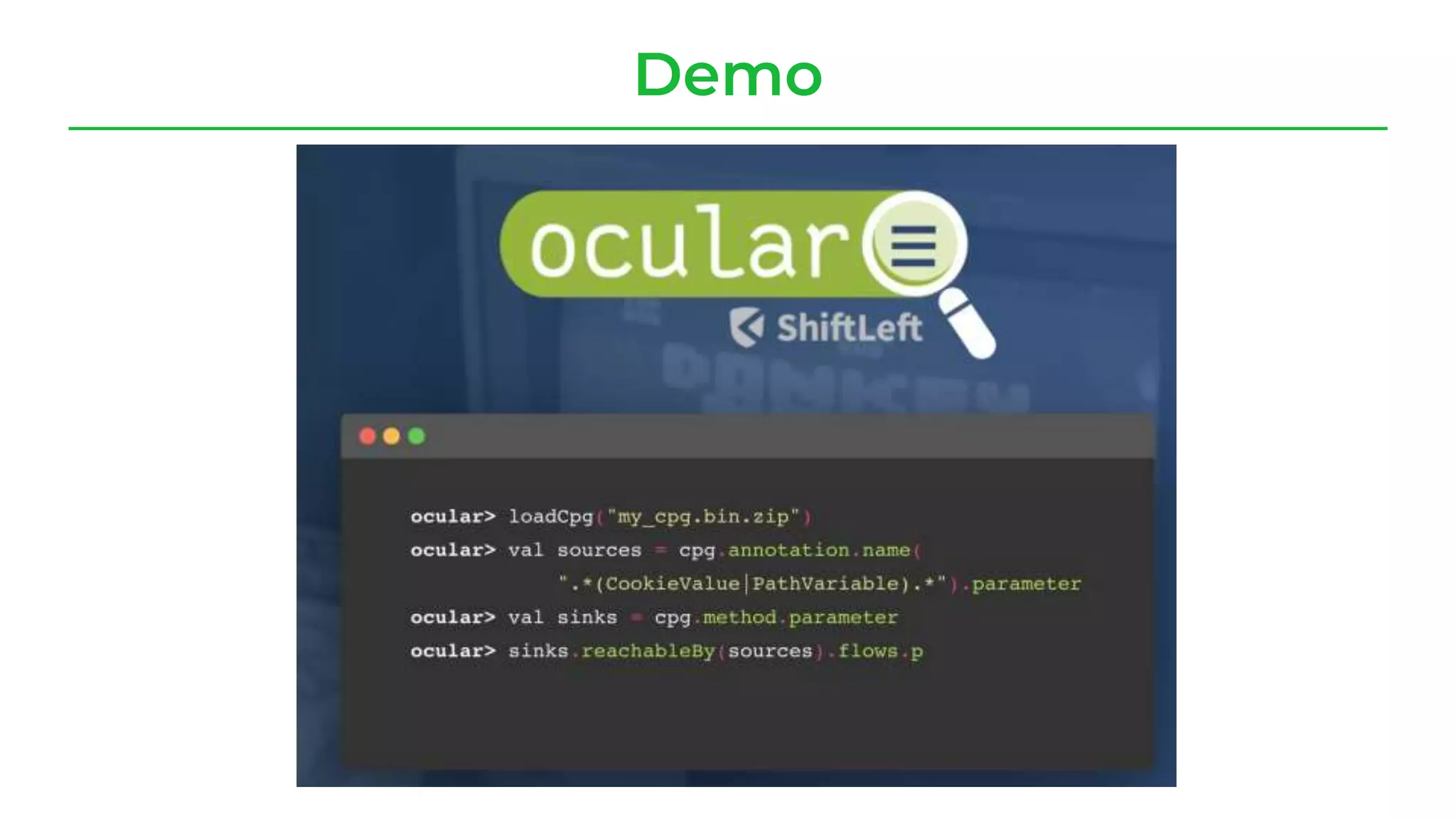
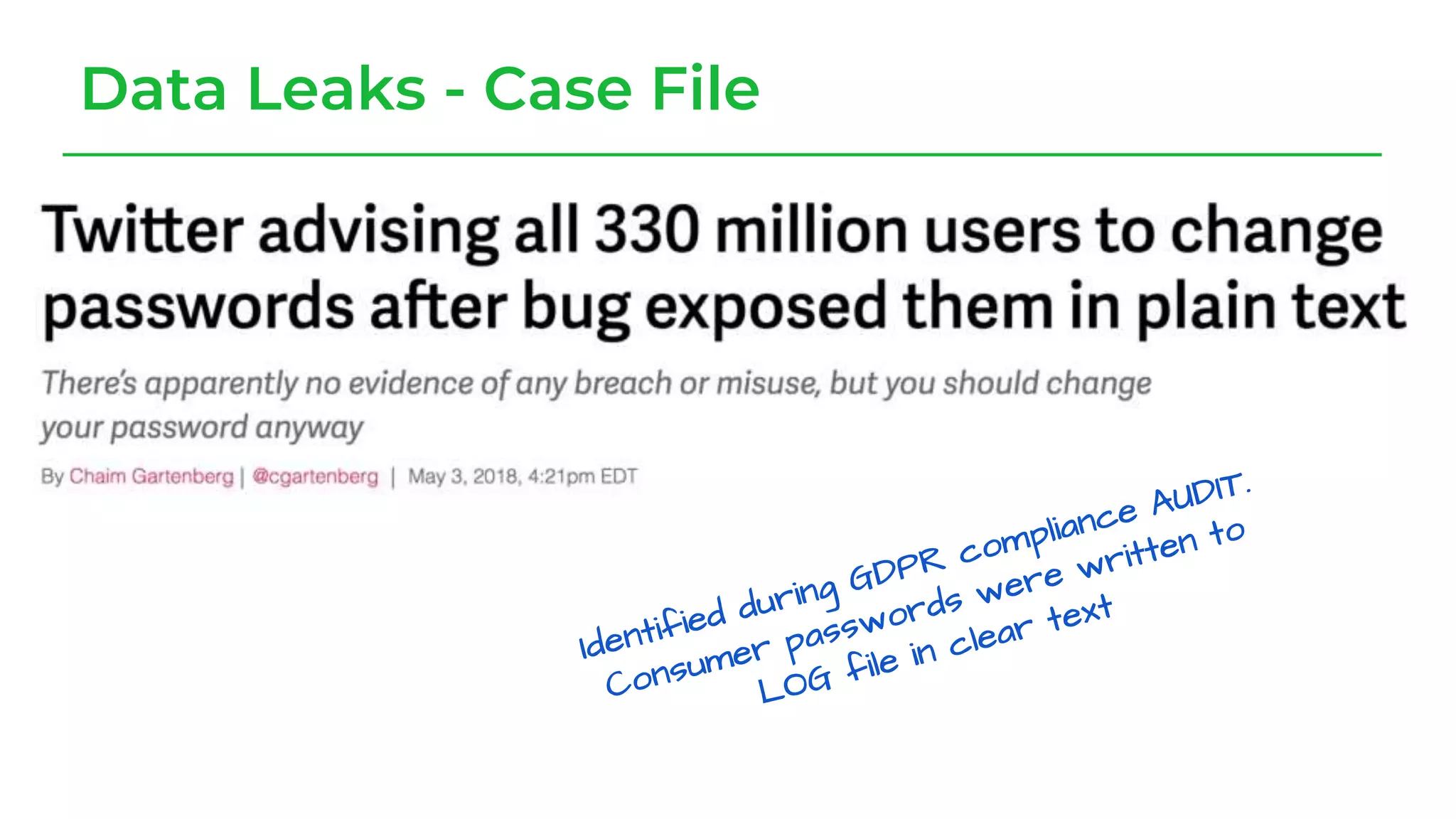
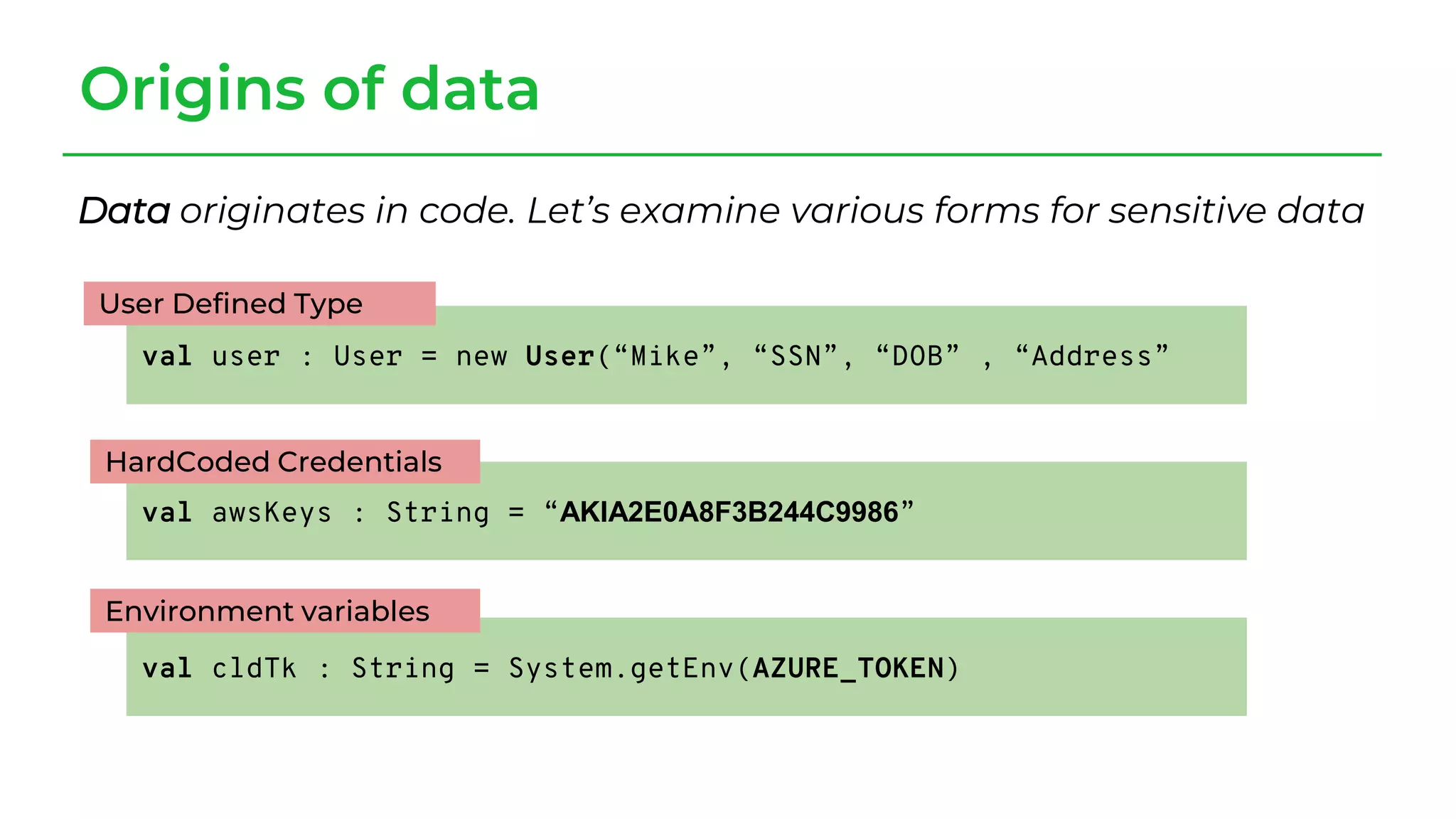
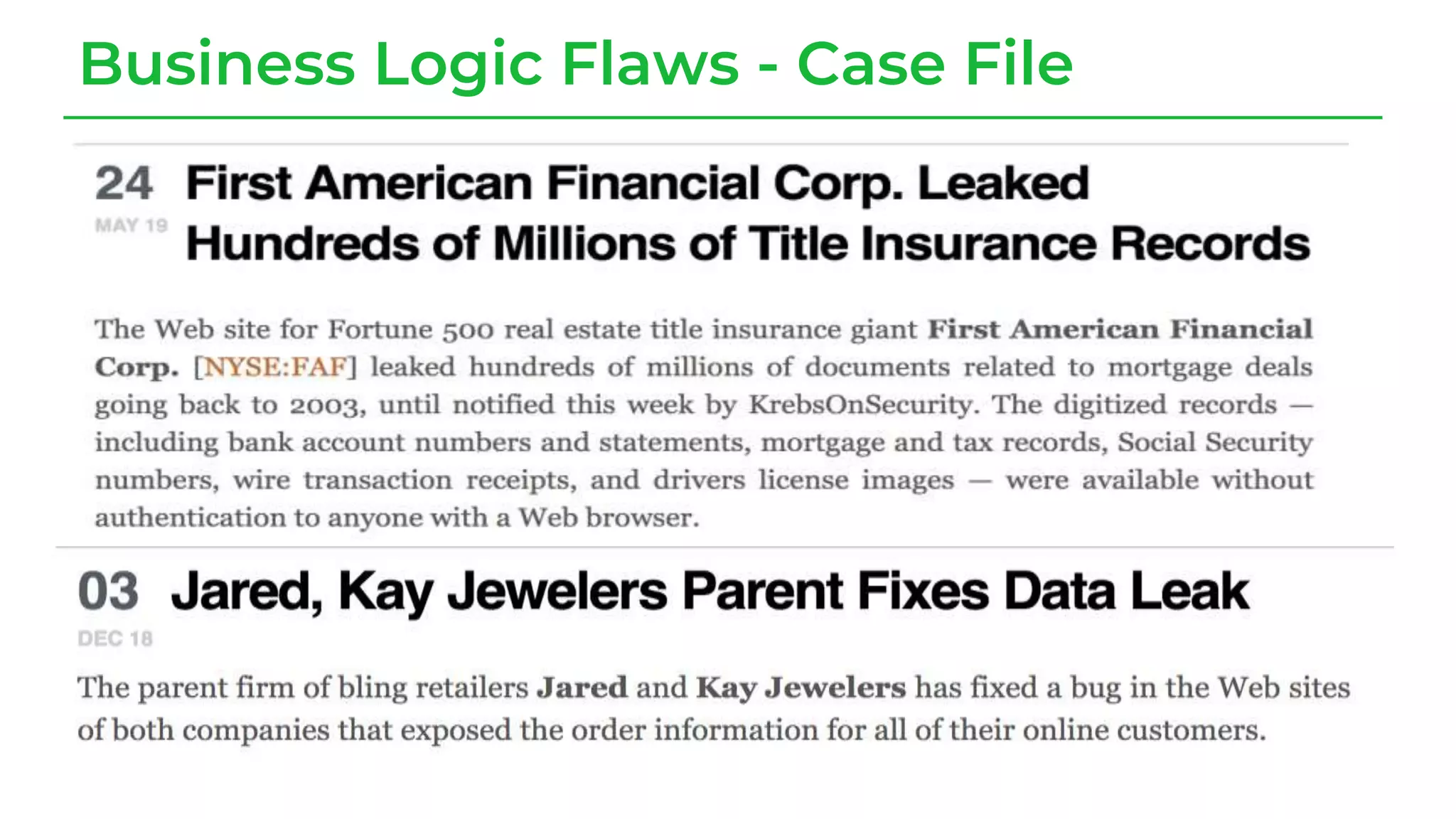
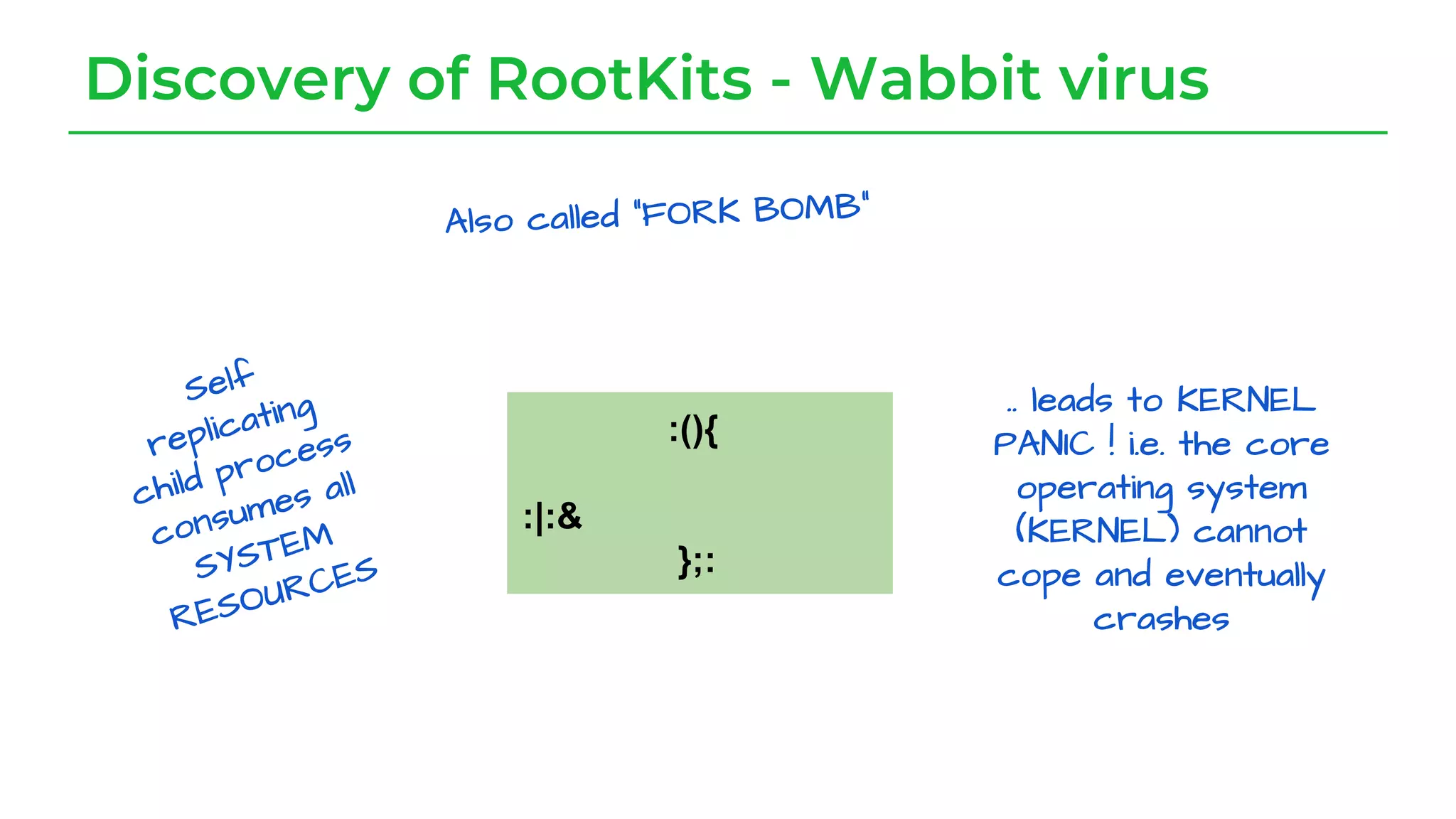
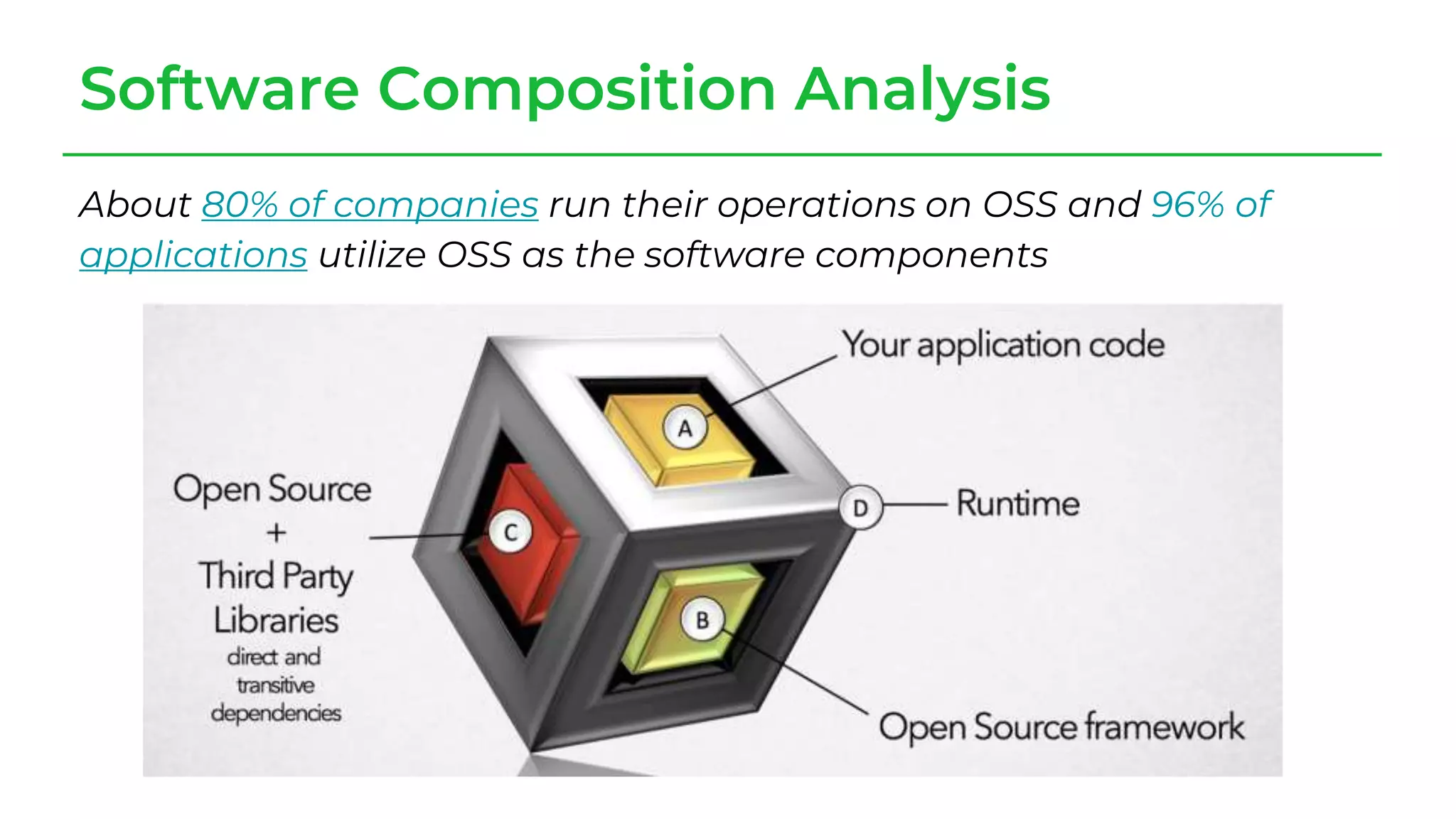
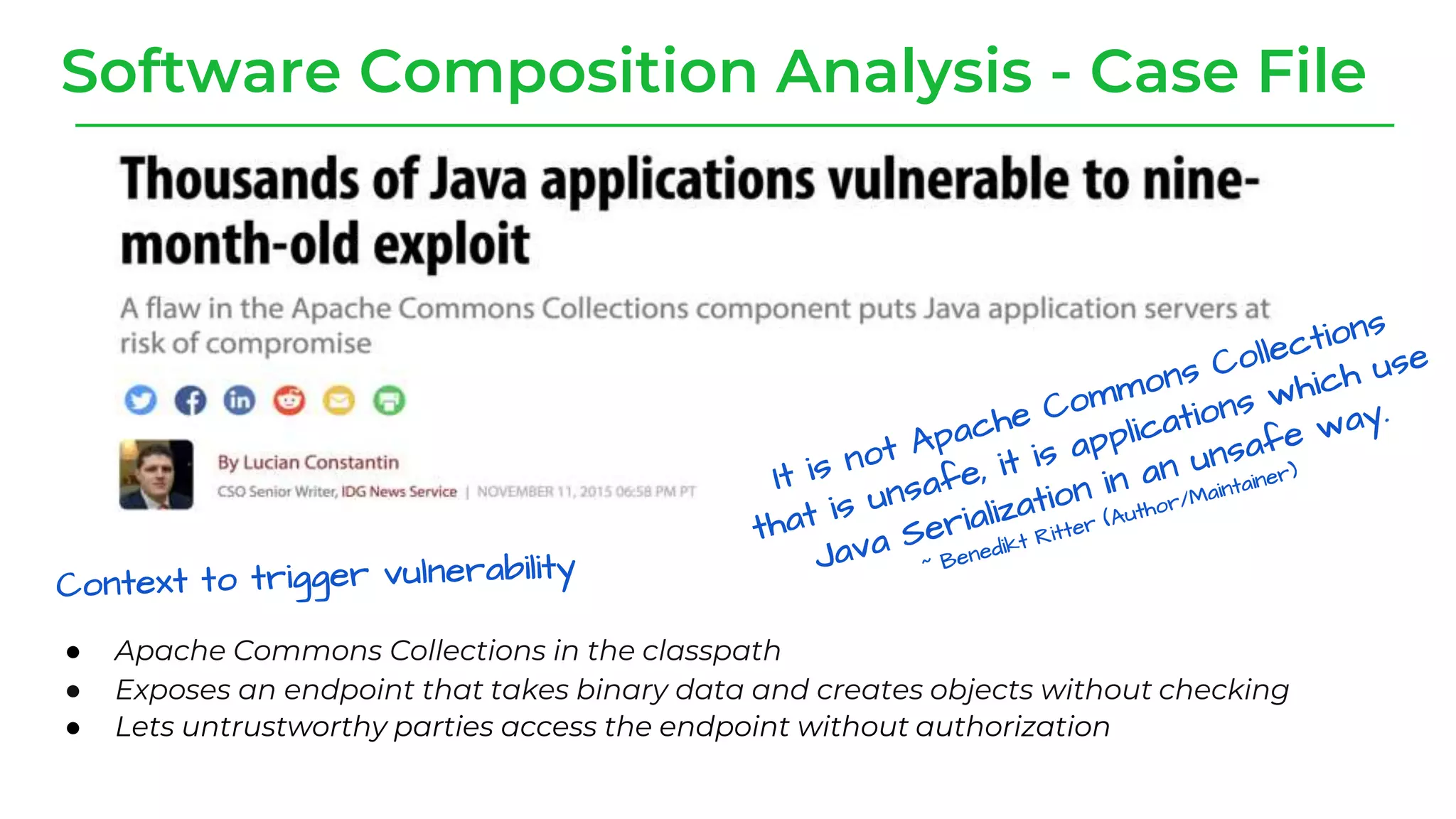
The document discusses a case study from a Fortune 500 fintech company focused on leveraging graph-based models to identify zero-day vulnerabilities in source code. It highlights the development of a Code Property Graph (CPG) to represent source code and track sensitive data flows, along with challenges related to manual testing, static analysis tools, and the need for advanced security practices. The study emphasizes automation and the integration of security measures to improve vulnerability detection and mitigate risks associated with data exposure and logic flaws.