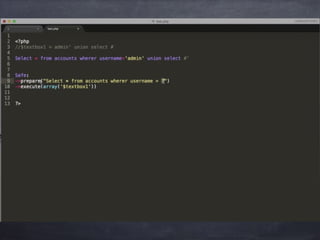
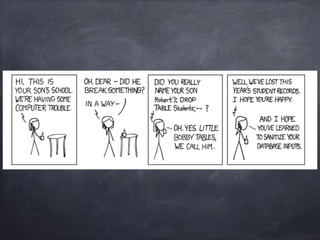
SQL injection is a code injection technique that allows attackers to execute malicious SQL statements to gain unauthorized access to data. It works by inserting SQL code into user input fields for execution by the backend database. This can give attackers full access to the database, including reading local files, uploading files, and accessing administrator privileges. While errors may reveal vulnerabilities, "blind SQL injection" occurs when no errors are displayed, requiring time-based or boolean techniques to exploit. Prevention methods like filtering and blacklisting can be bypassed, so the most secure approach is using parameterized statements to separate data from code.