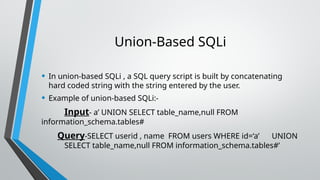
The document discusses SQL injection, a web-based vulnerability that allows attackers to execute malicious SQL queries on databases, leading to issues such as identity spoofing, data modification, and unauthorized access. It outlines different types of SQL injection attacks, methodologies used by attackers, and provides examples of harmful SQL queries, along with prevention strategies like minimizing privileges and using secure coding practices. The increasing severity of these attacks poses significant risks and potential financial losses for organizations relying on databases.