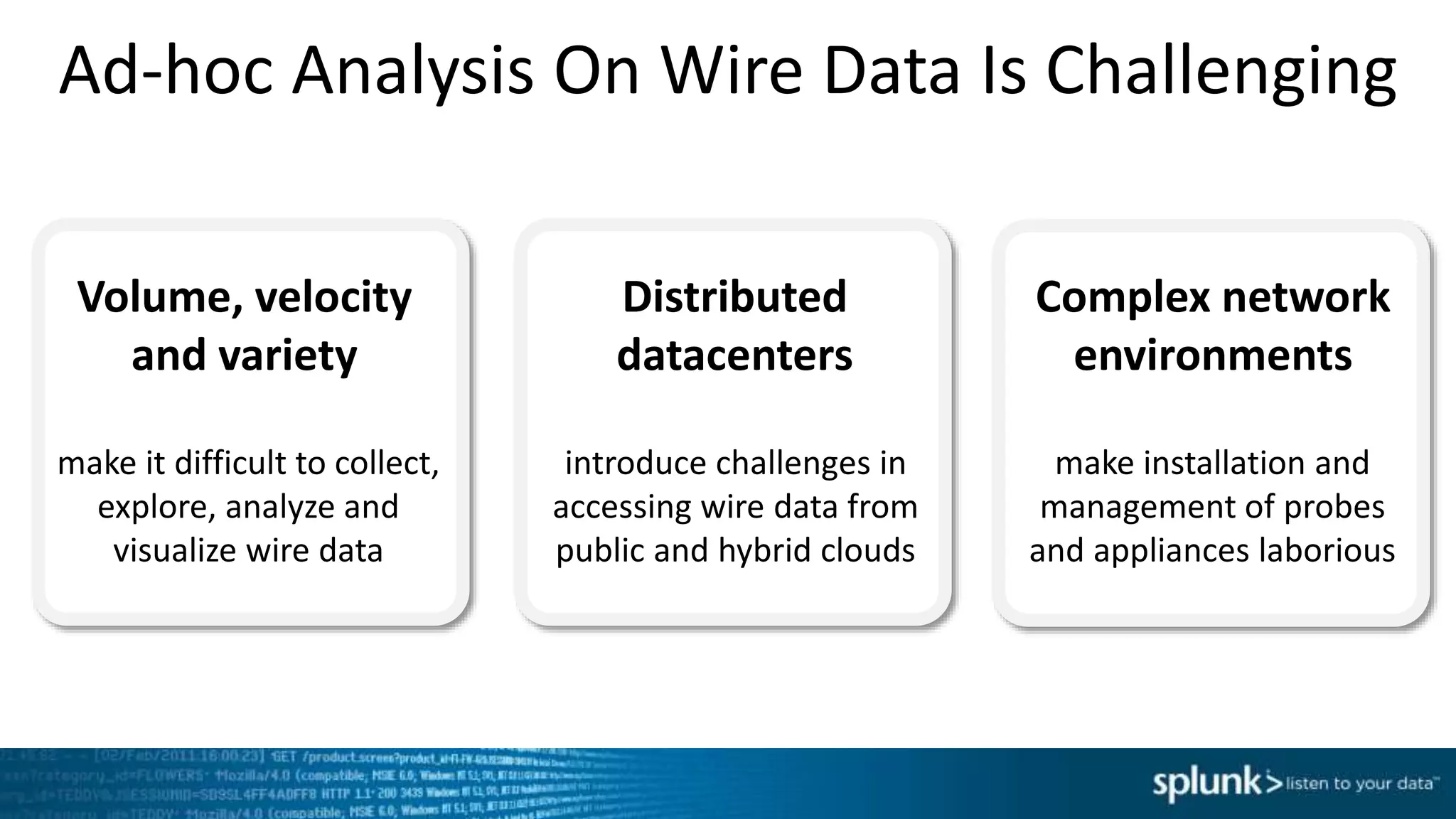
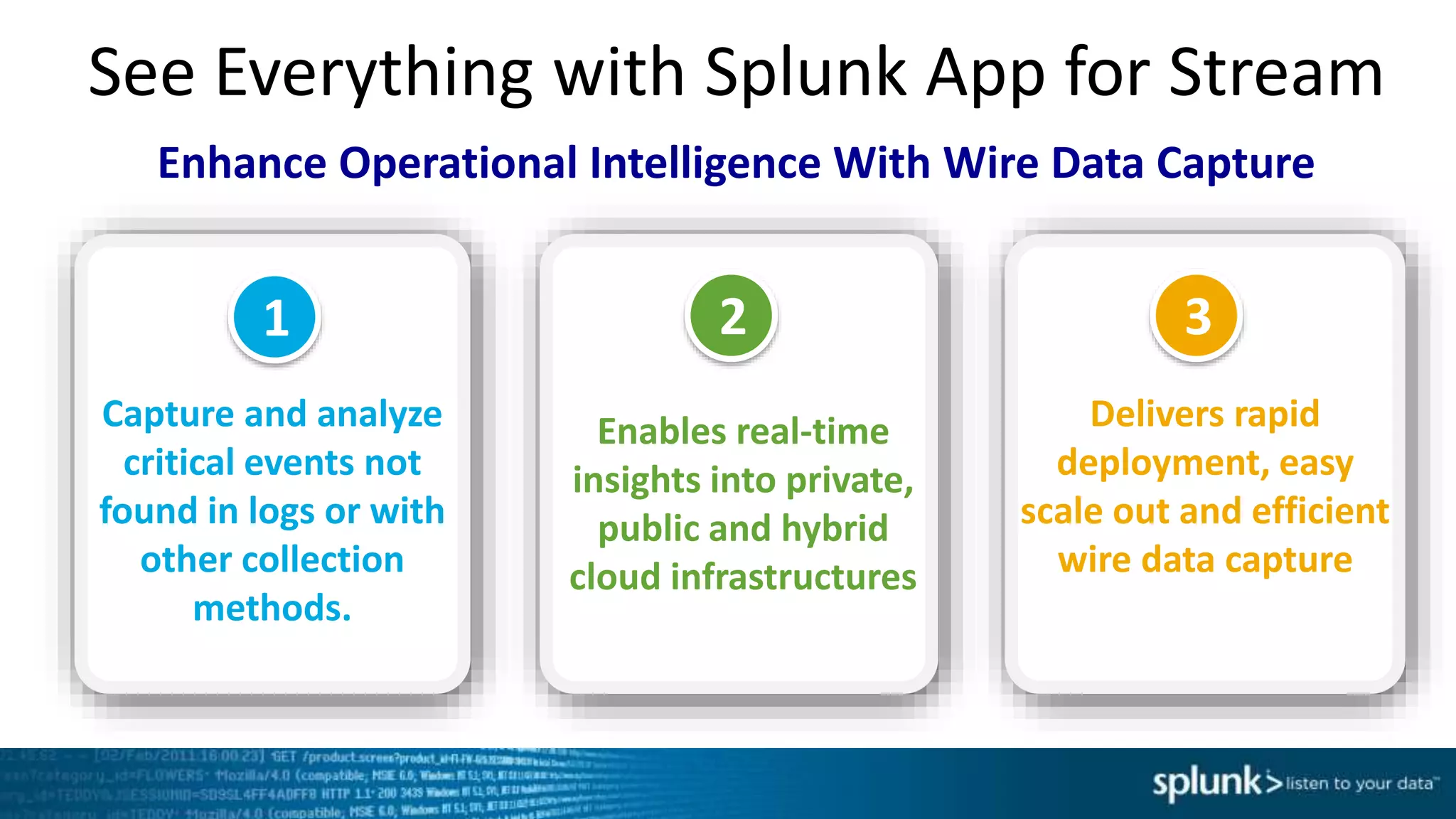
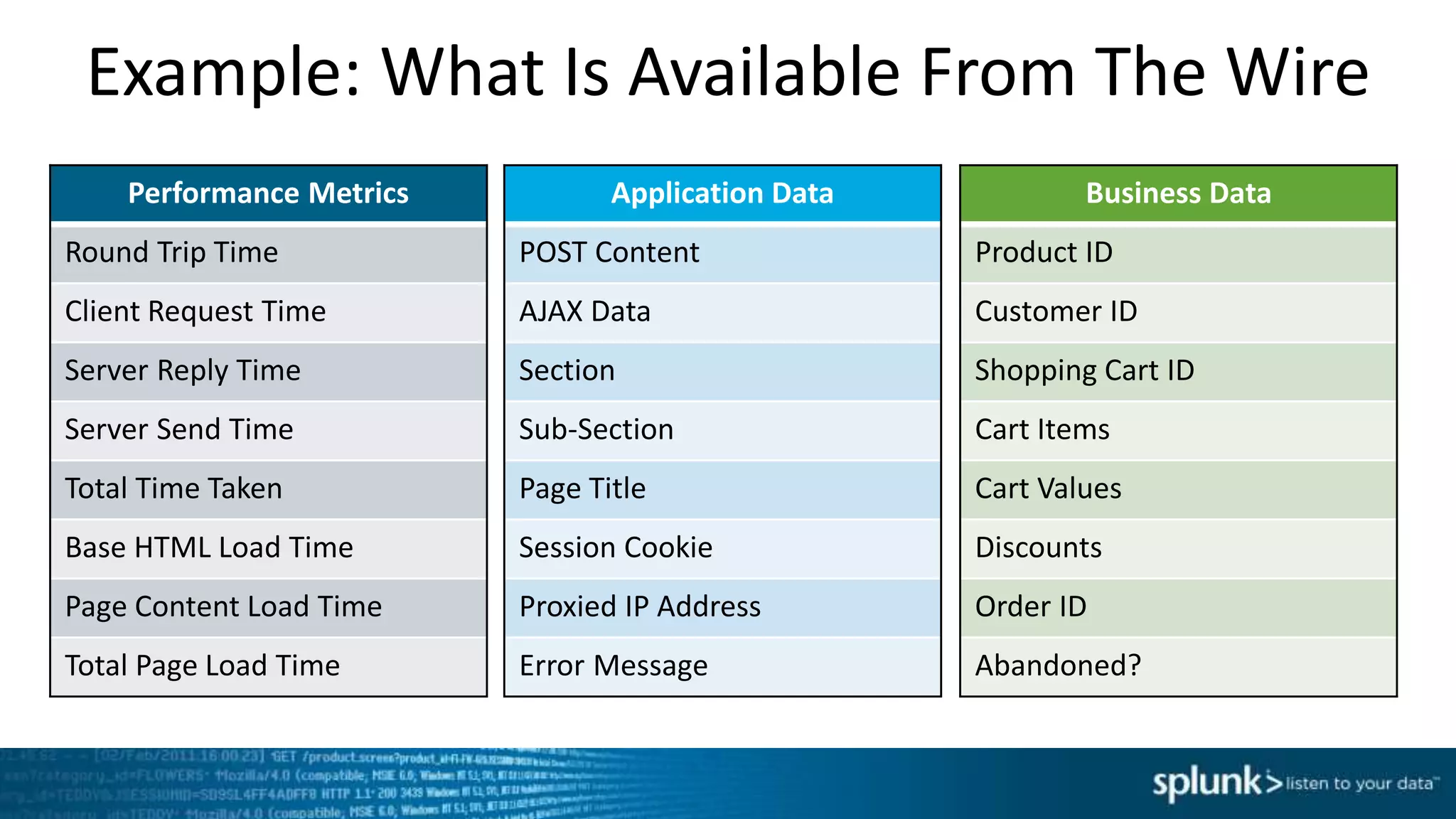
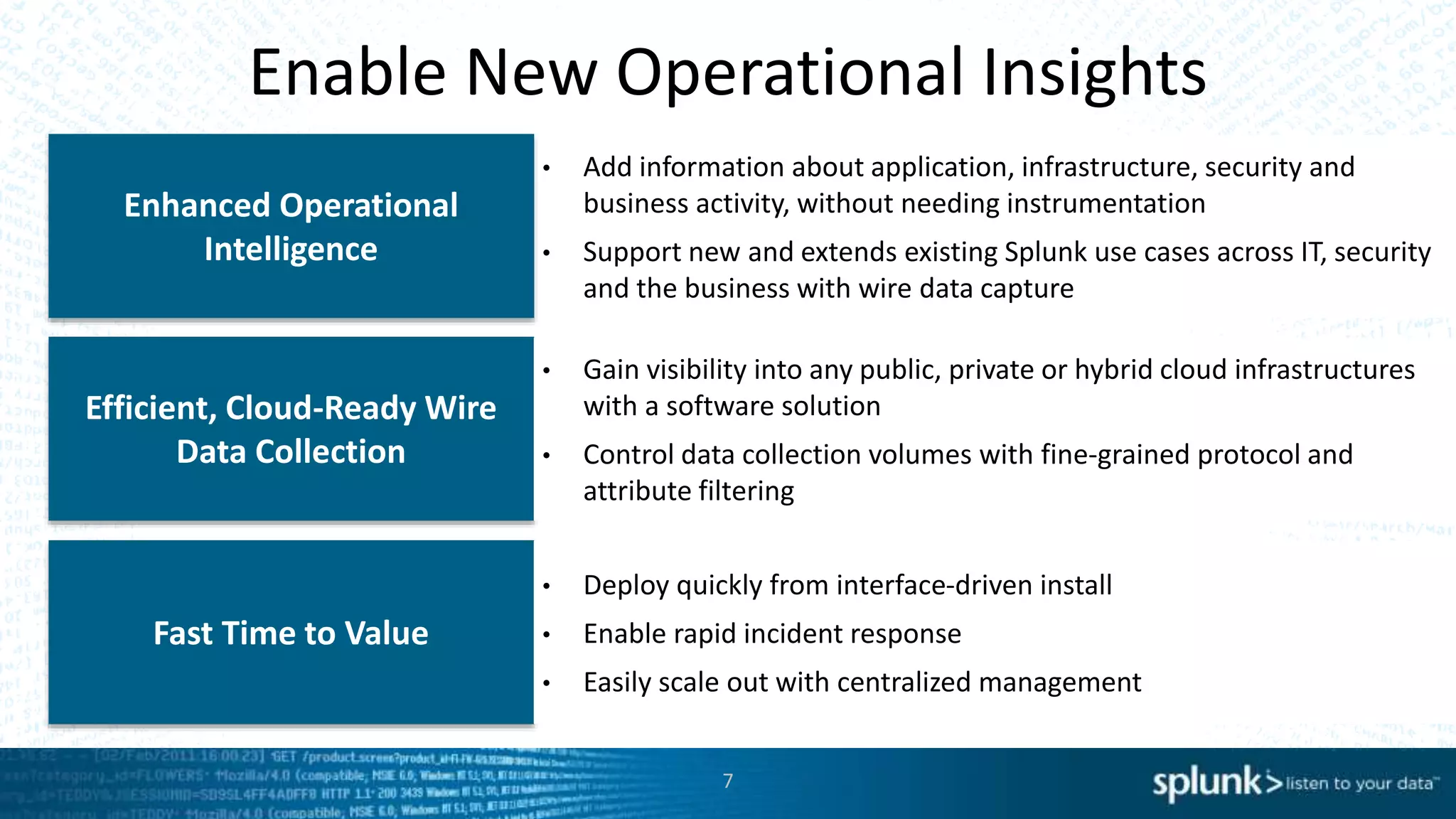
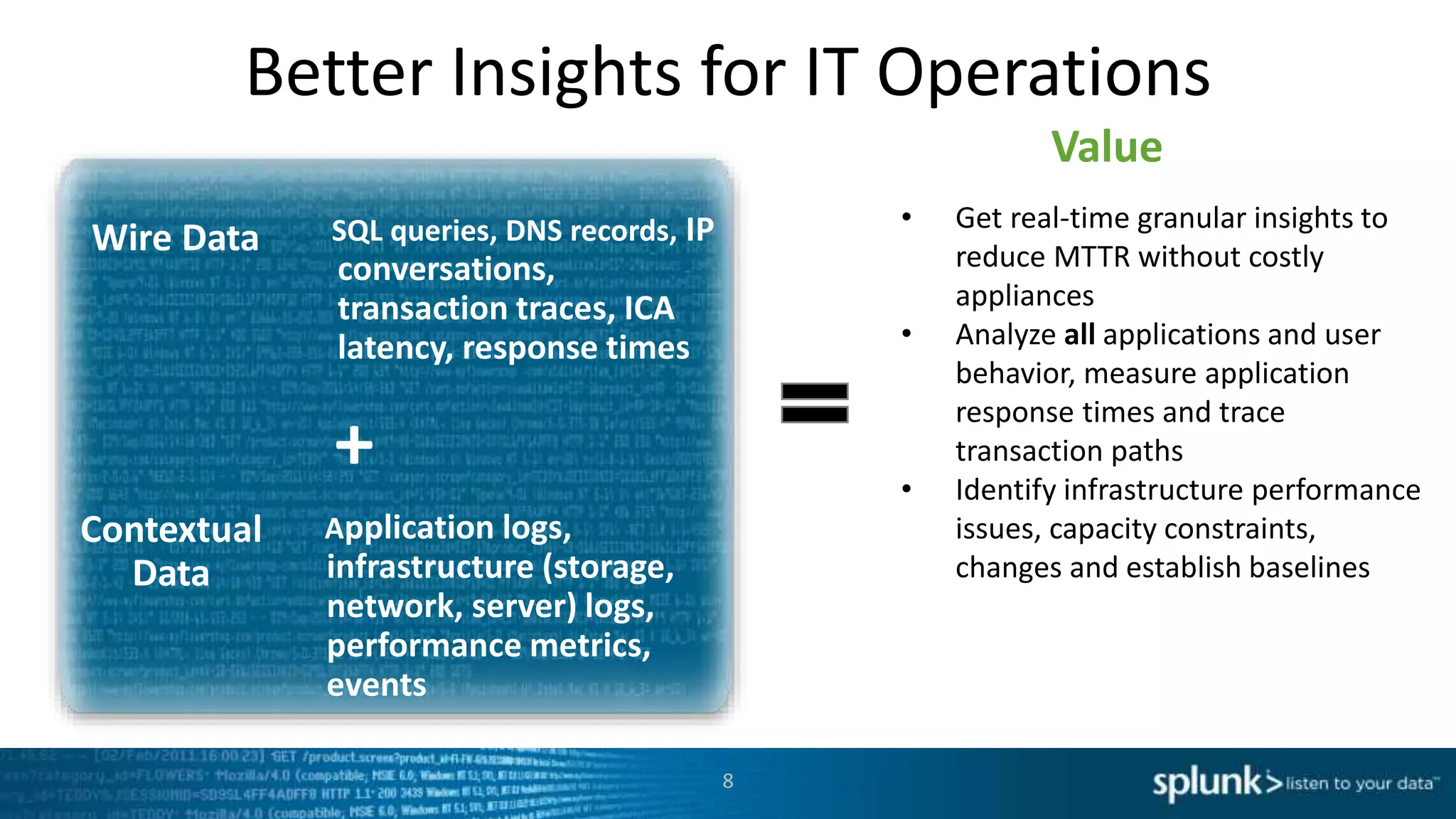
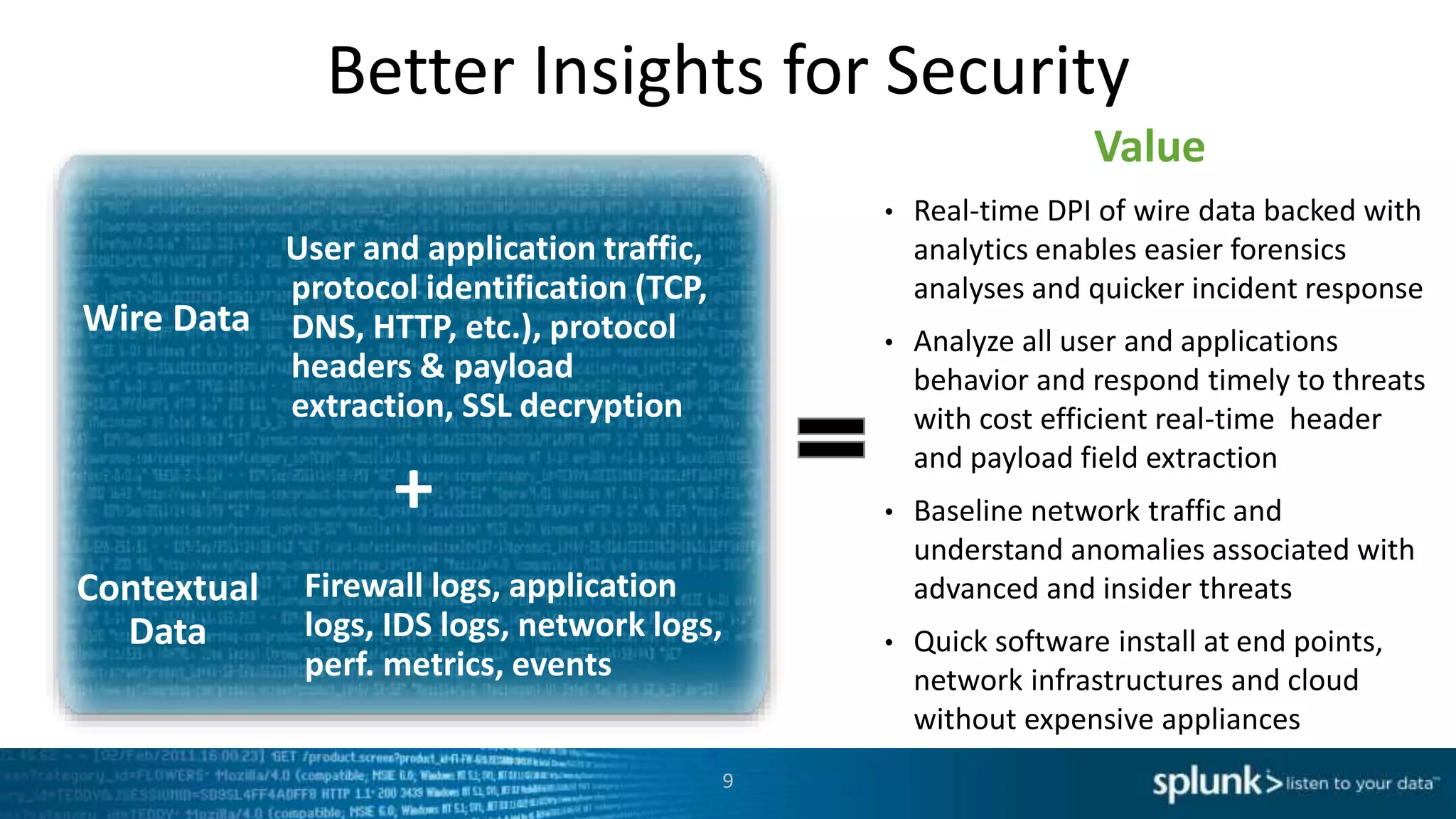
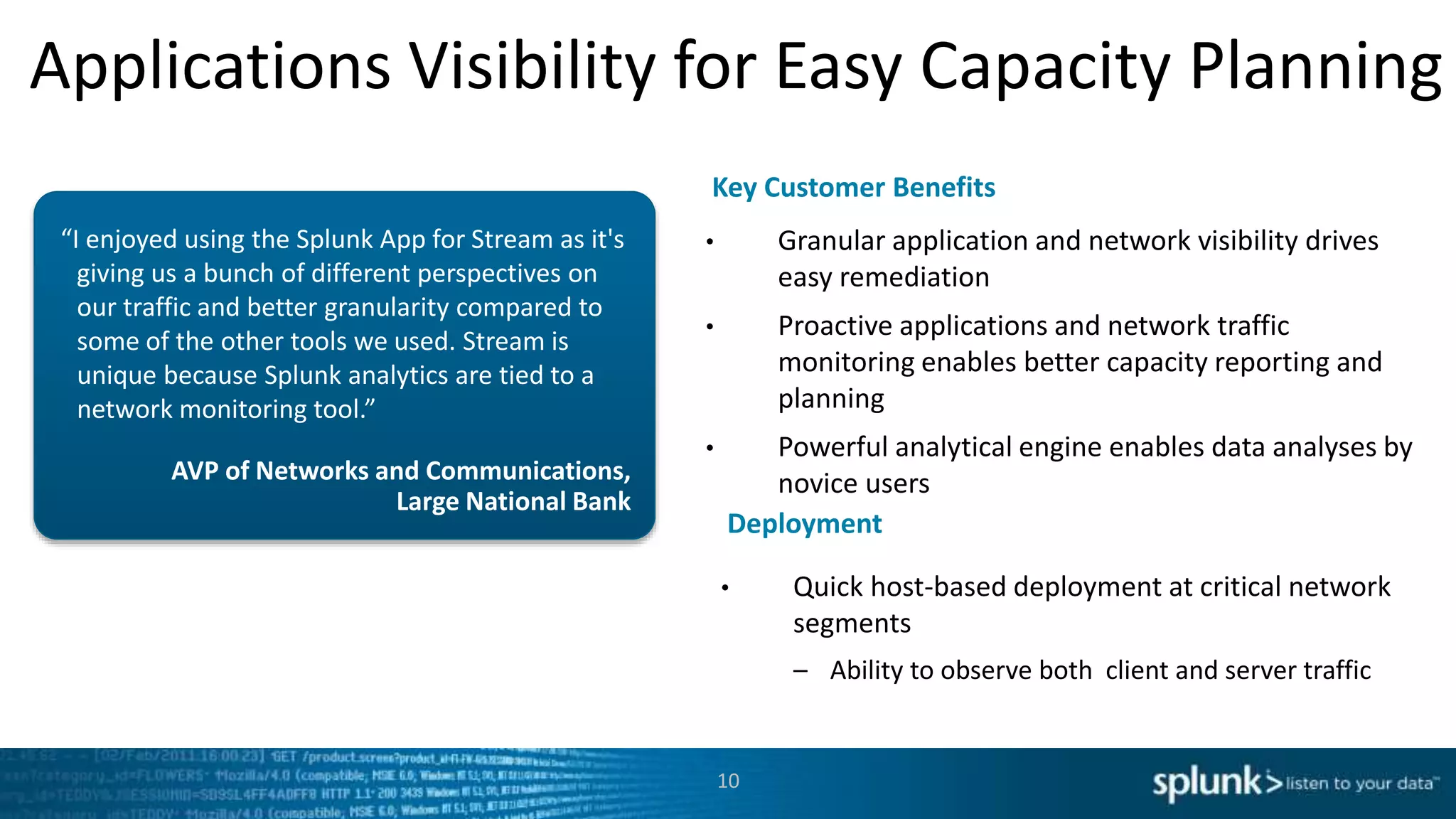
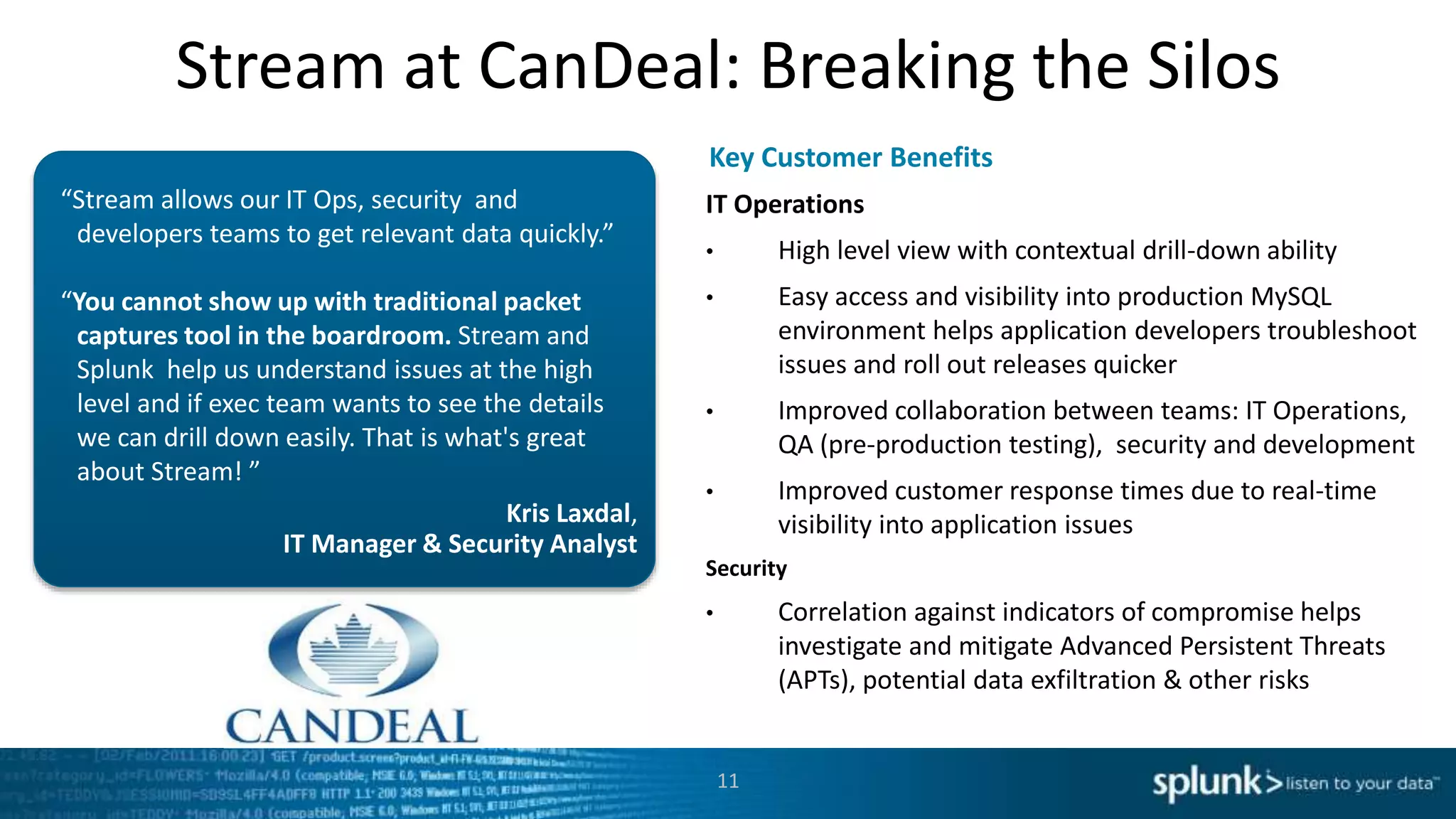
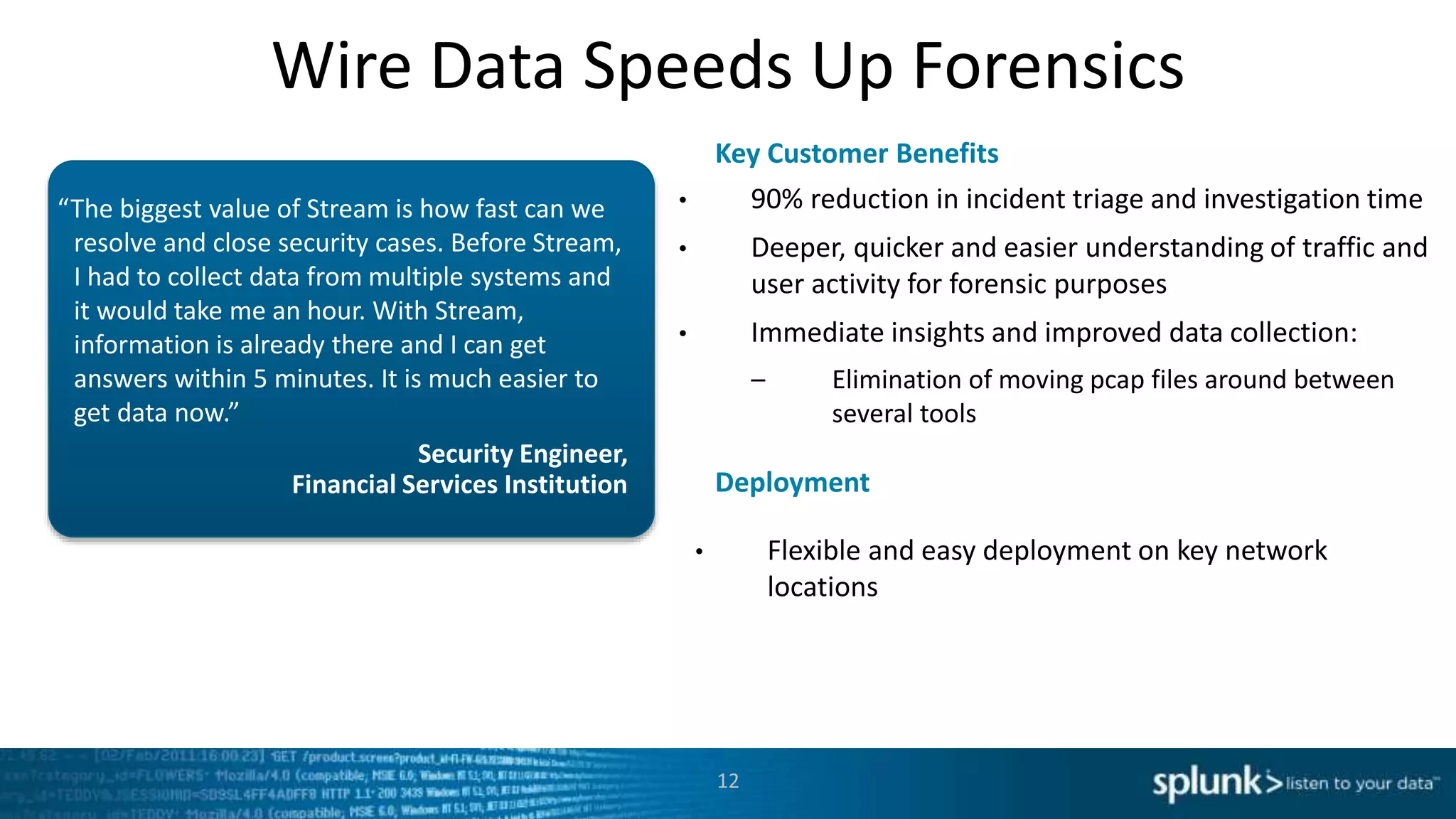
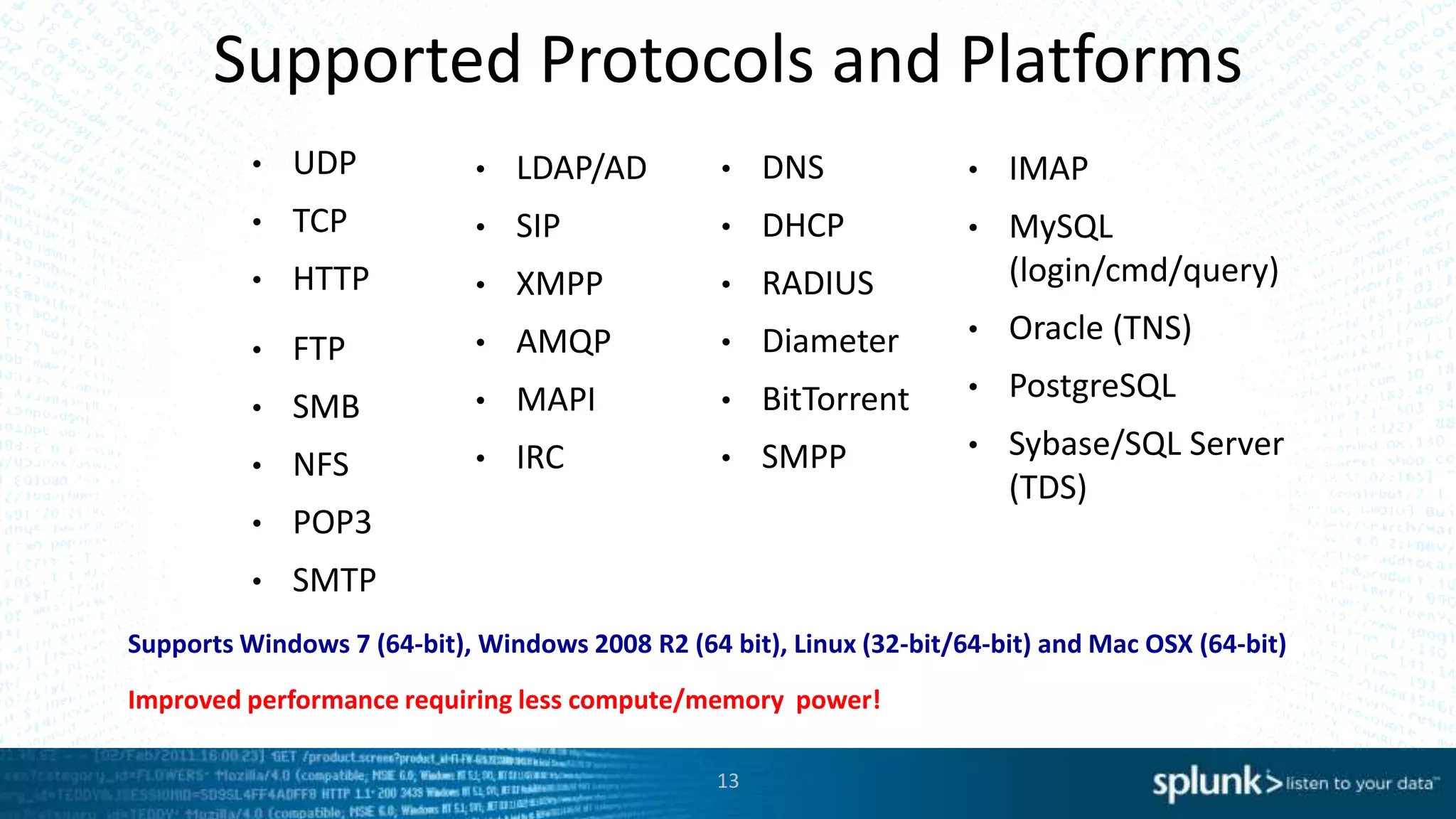
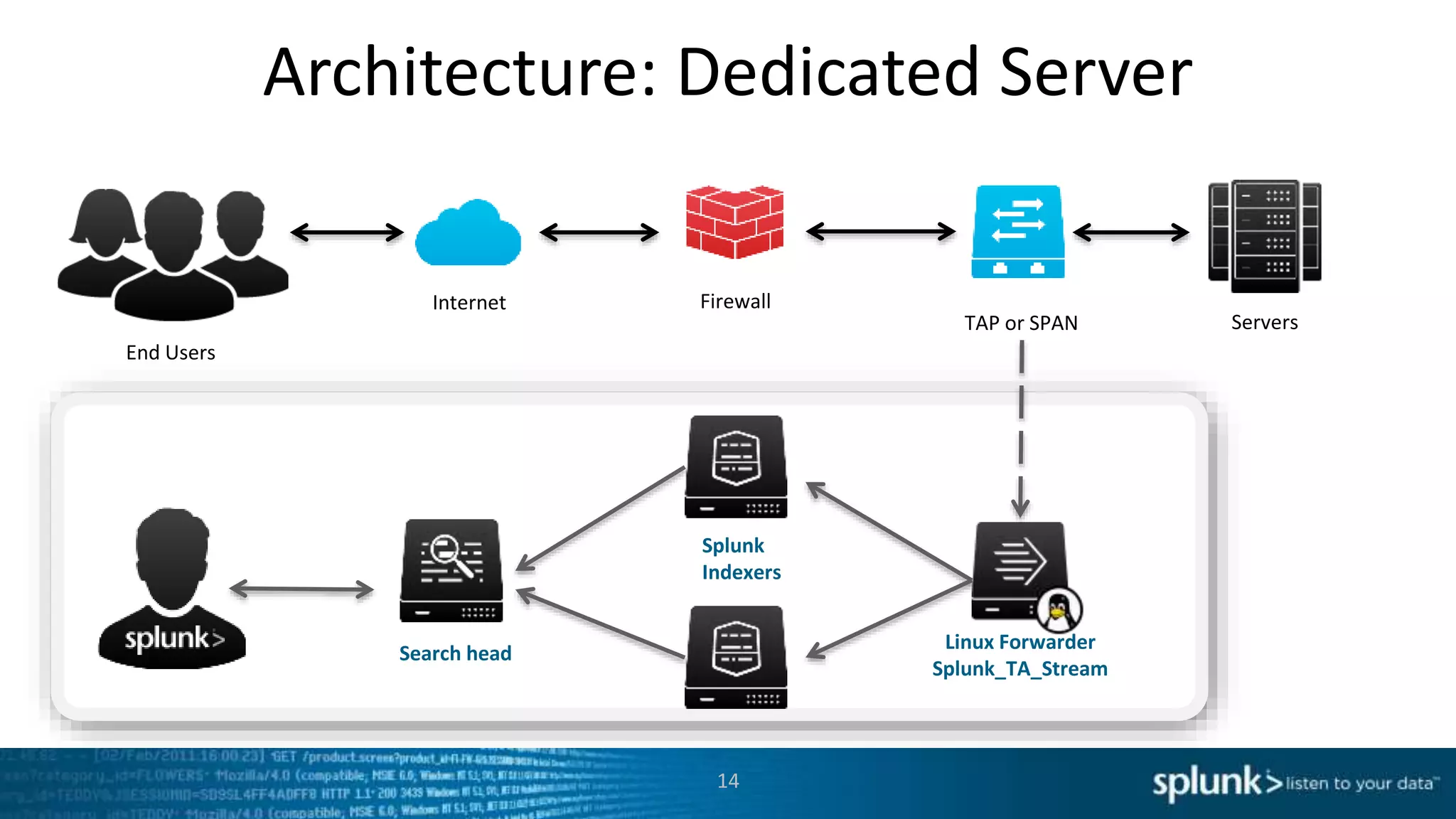
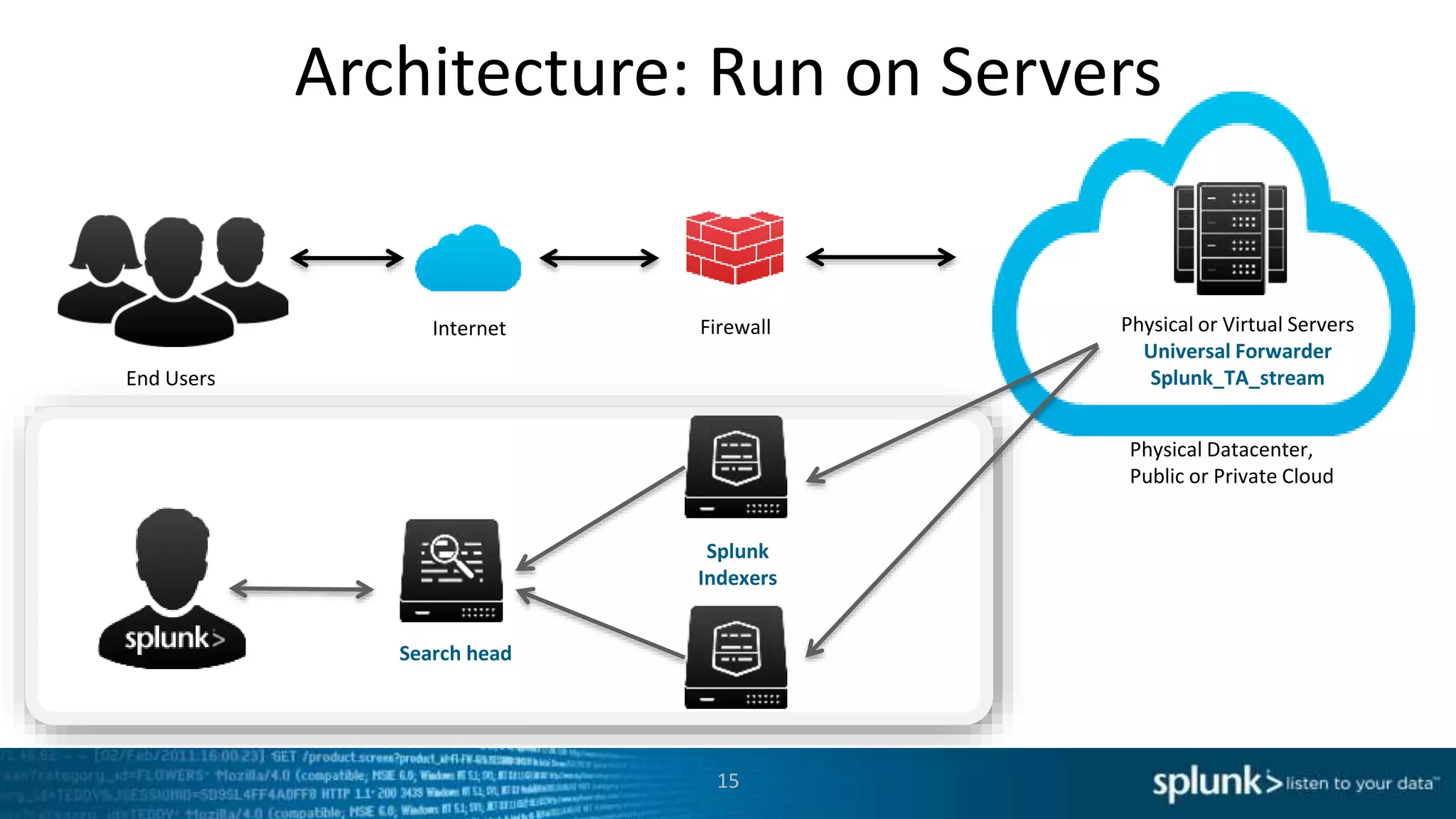
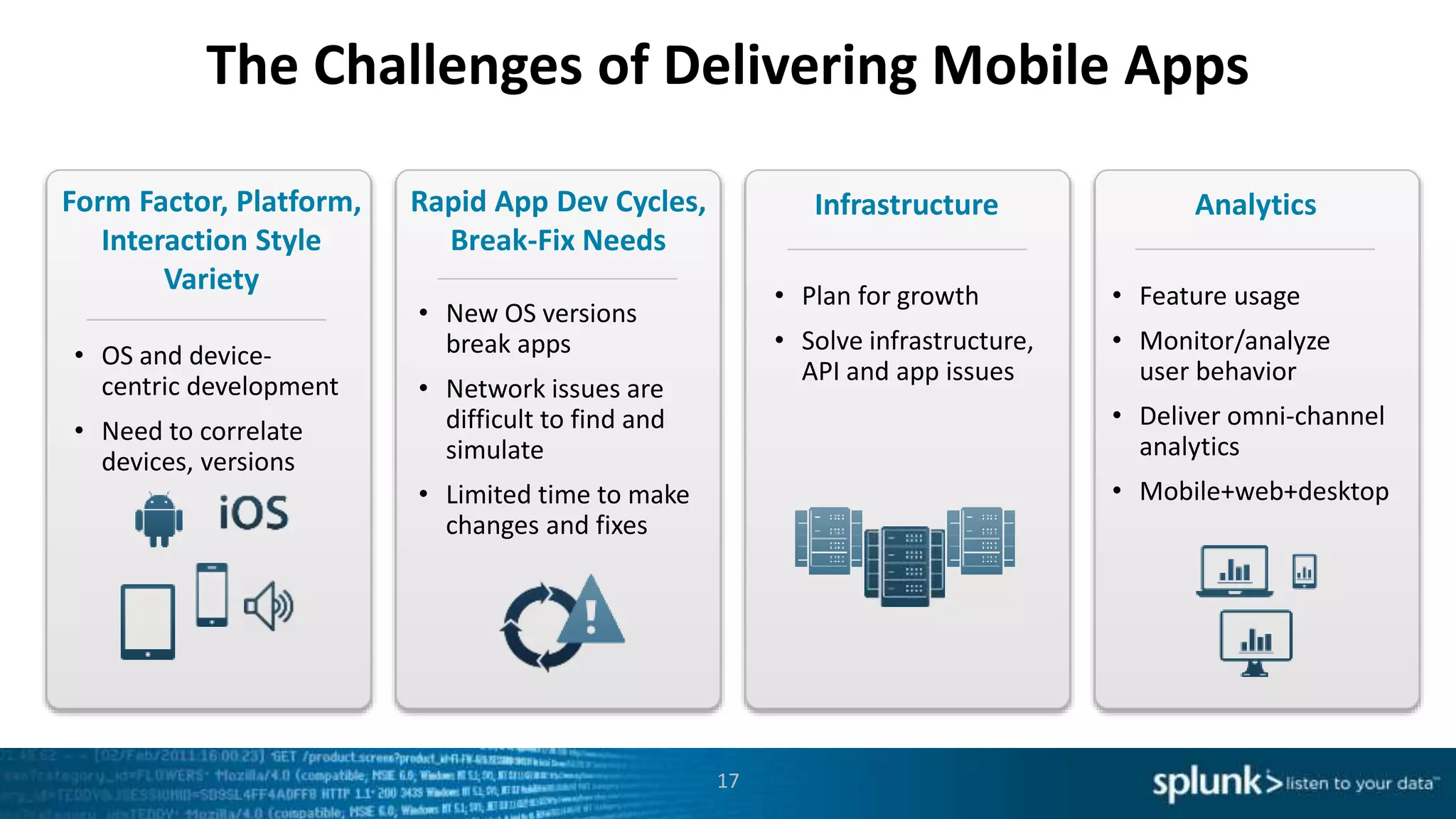
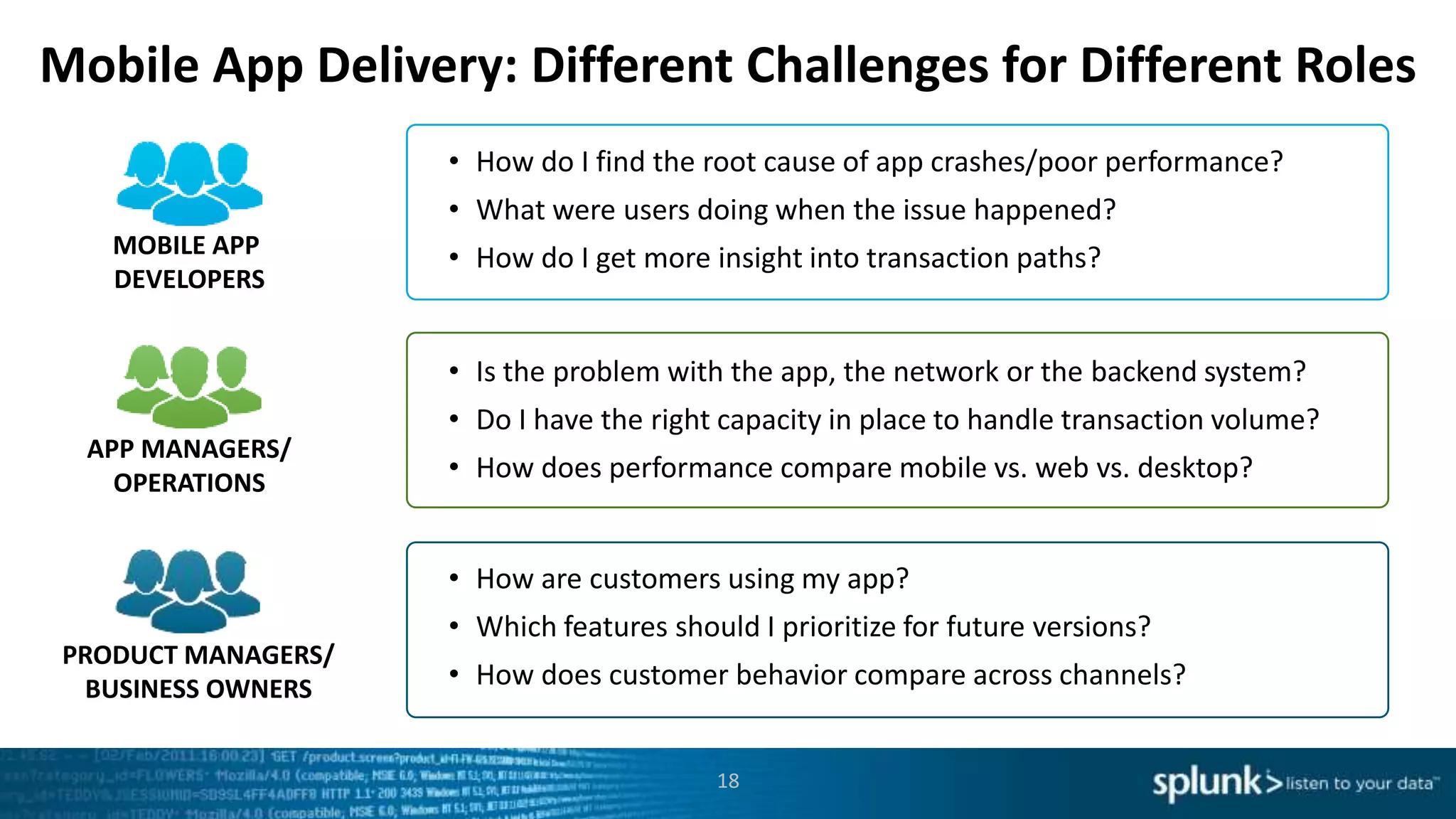
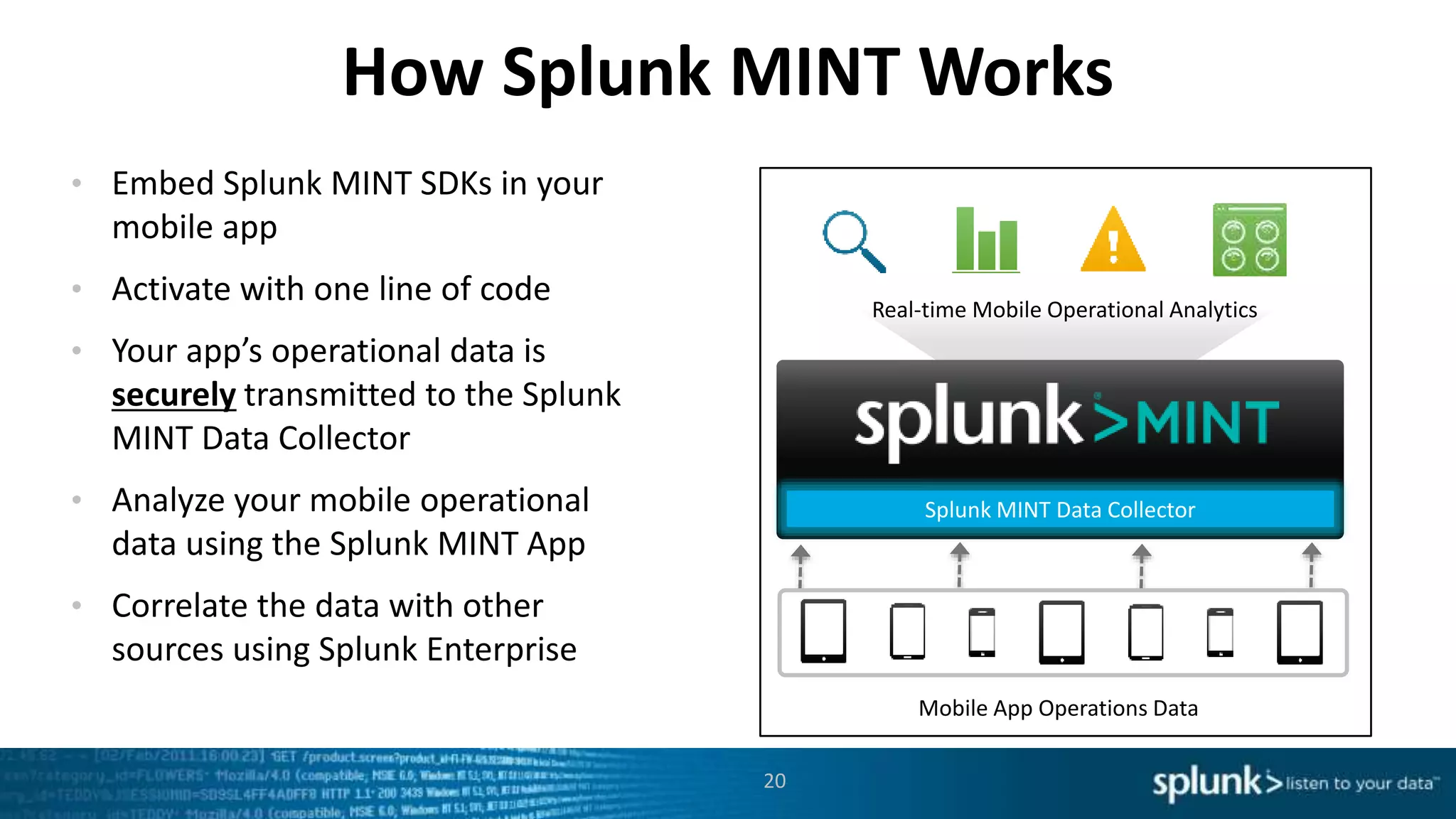
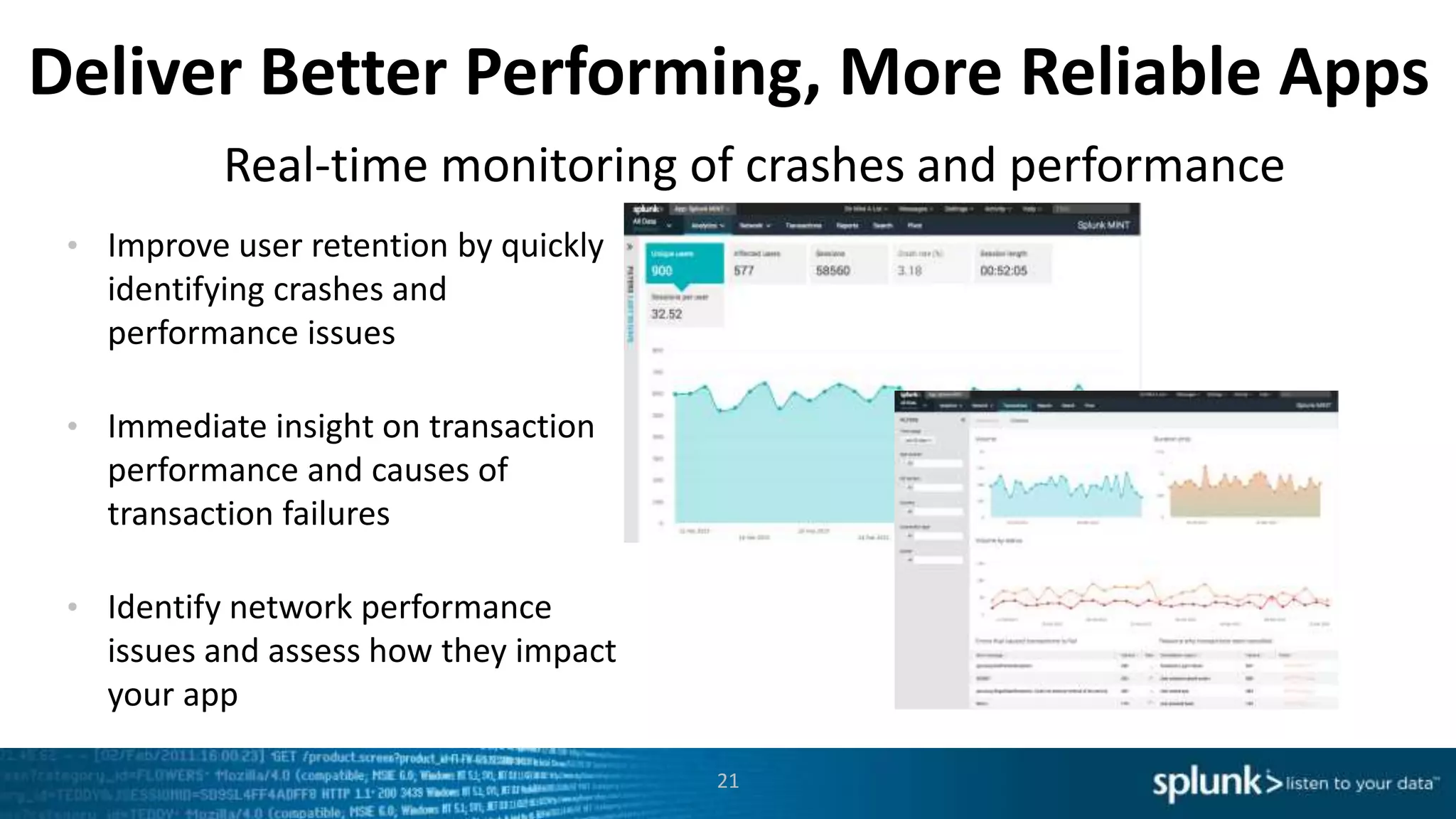
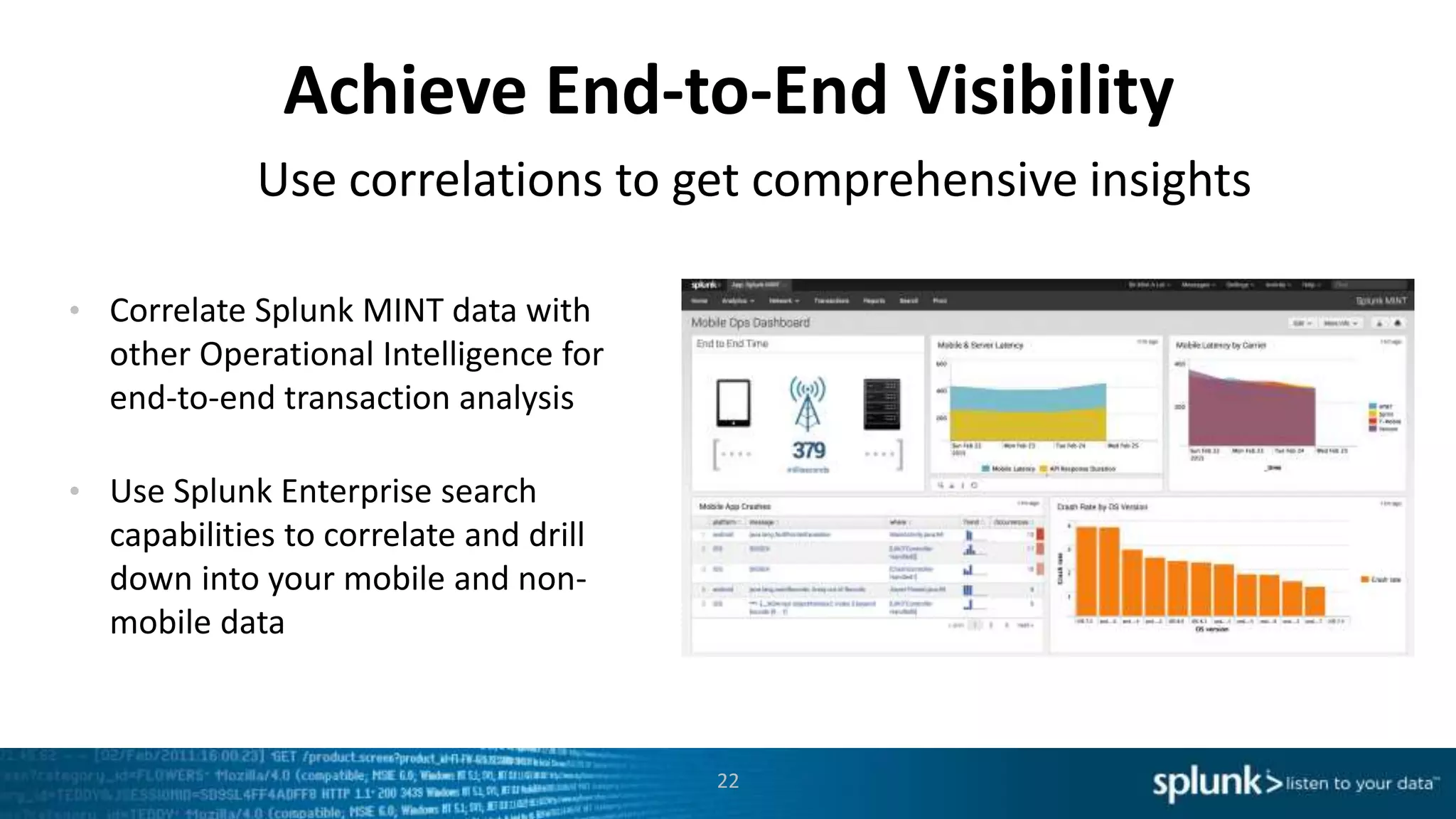
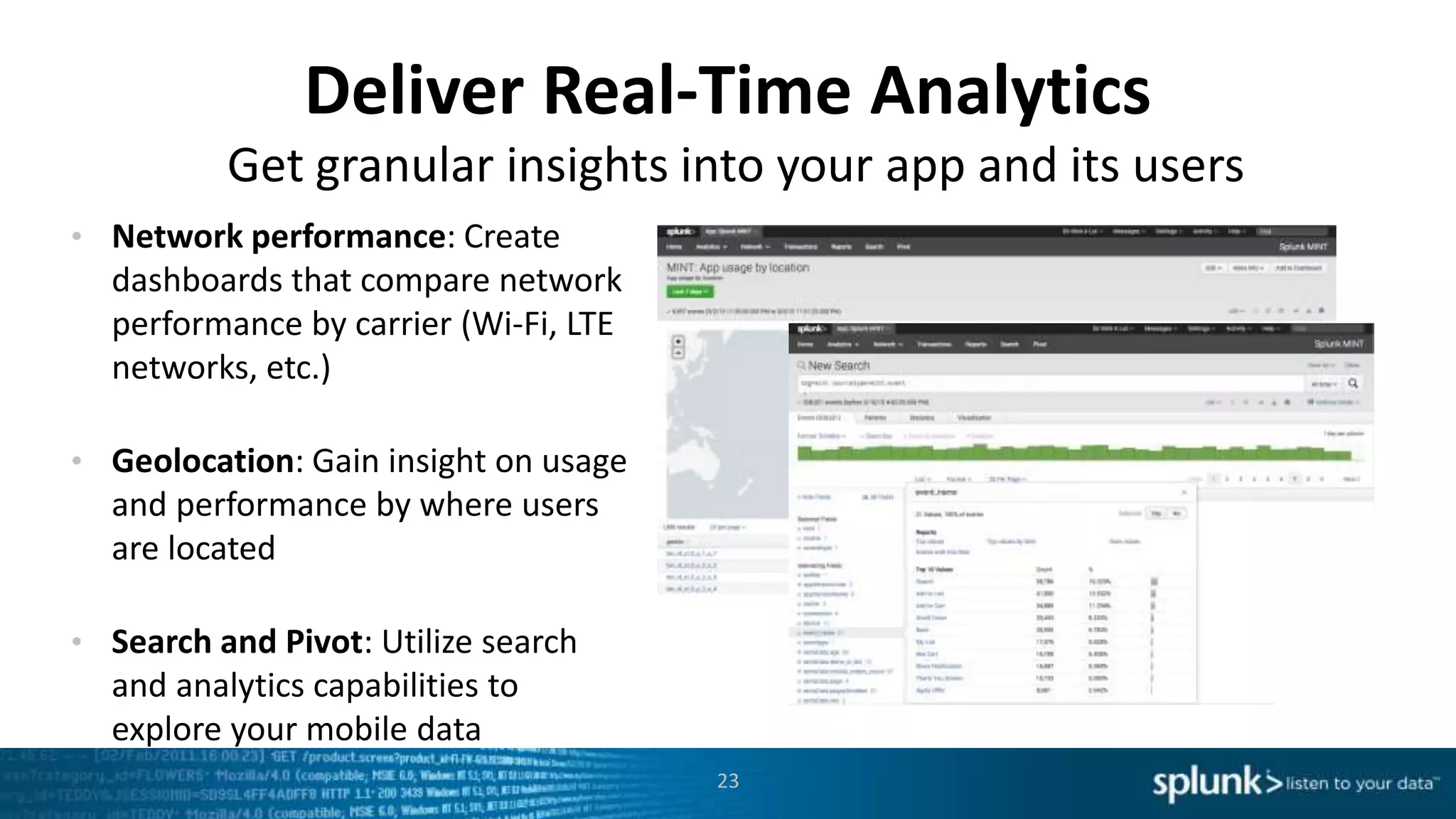
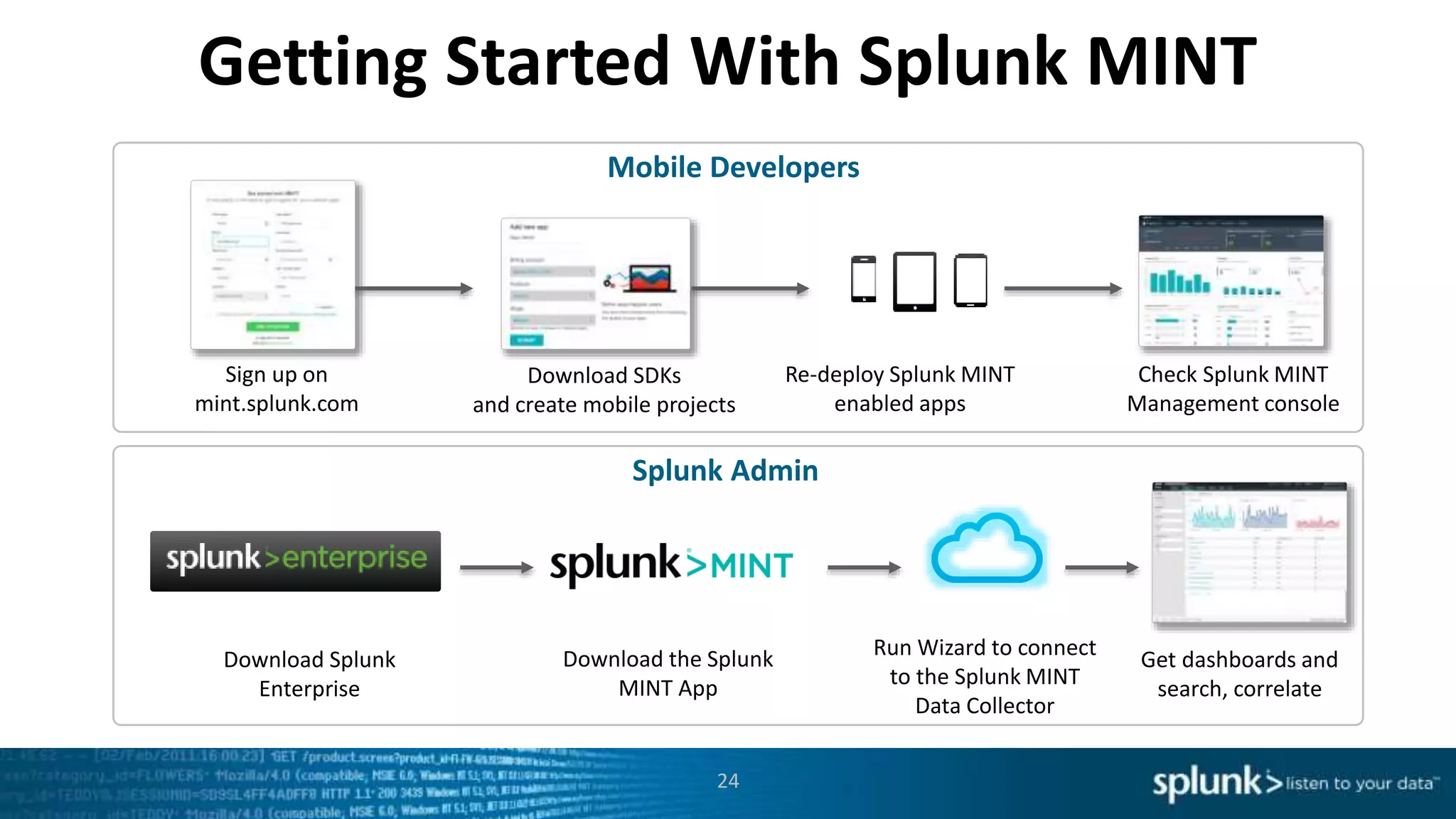
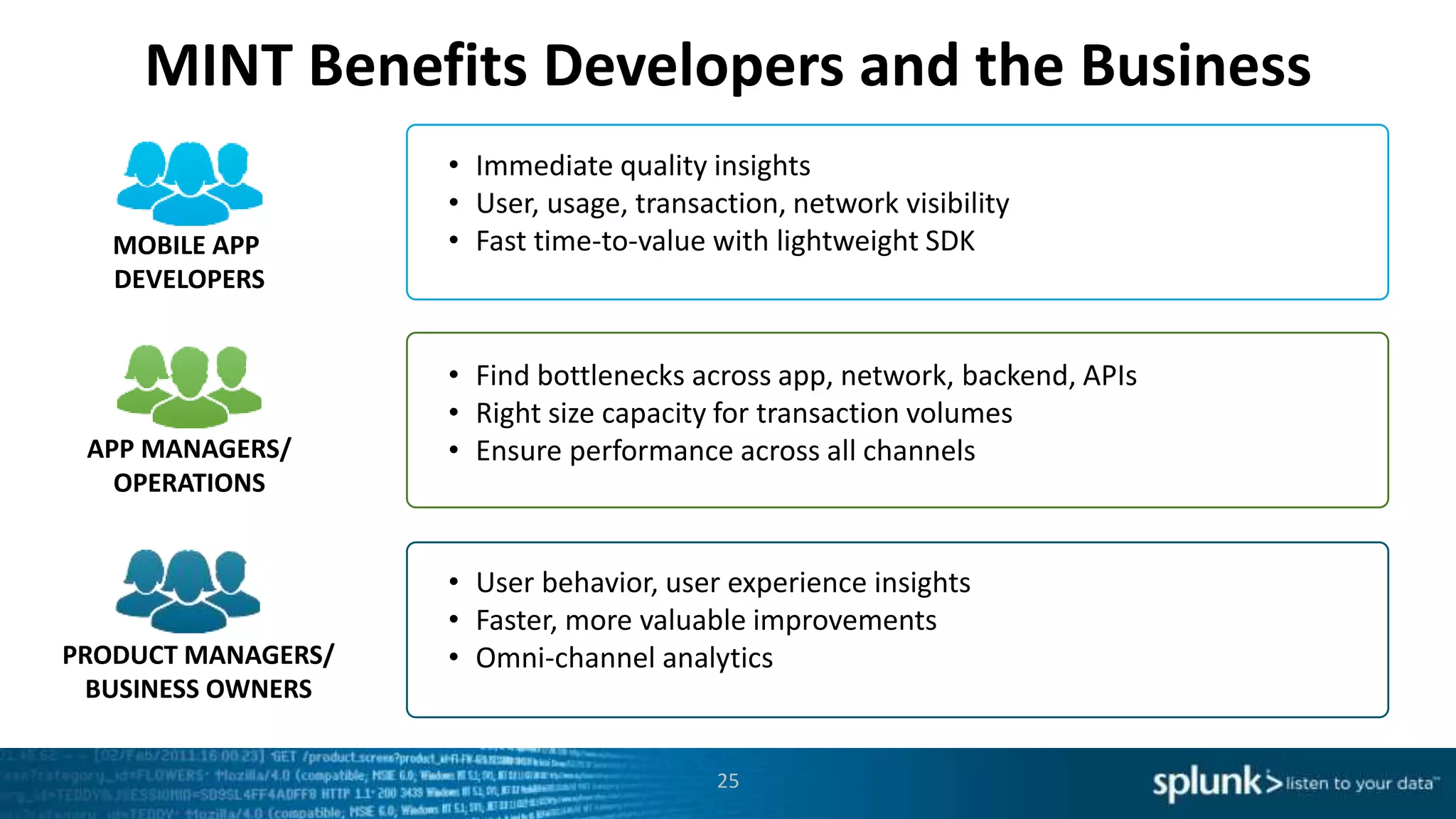
This document discusses new capabilities in Splunk's App for Stream and Splunk MINT products. It begins with an introduction and overview of each product. It then discusses key benefits like real-time insights, efficient cloud data collection, and fast time to value. Example use cases are provided for IT operations, security, and applications visibility. Supported protocols, platforms, and architecture options are also outlined. The document concludes by discussing challenges in mobile app delivery and how Splunk MINT addresses them through mobile data collection and correlation with other data sources.