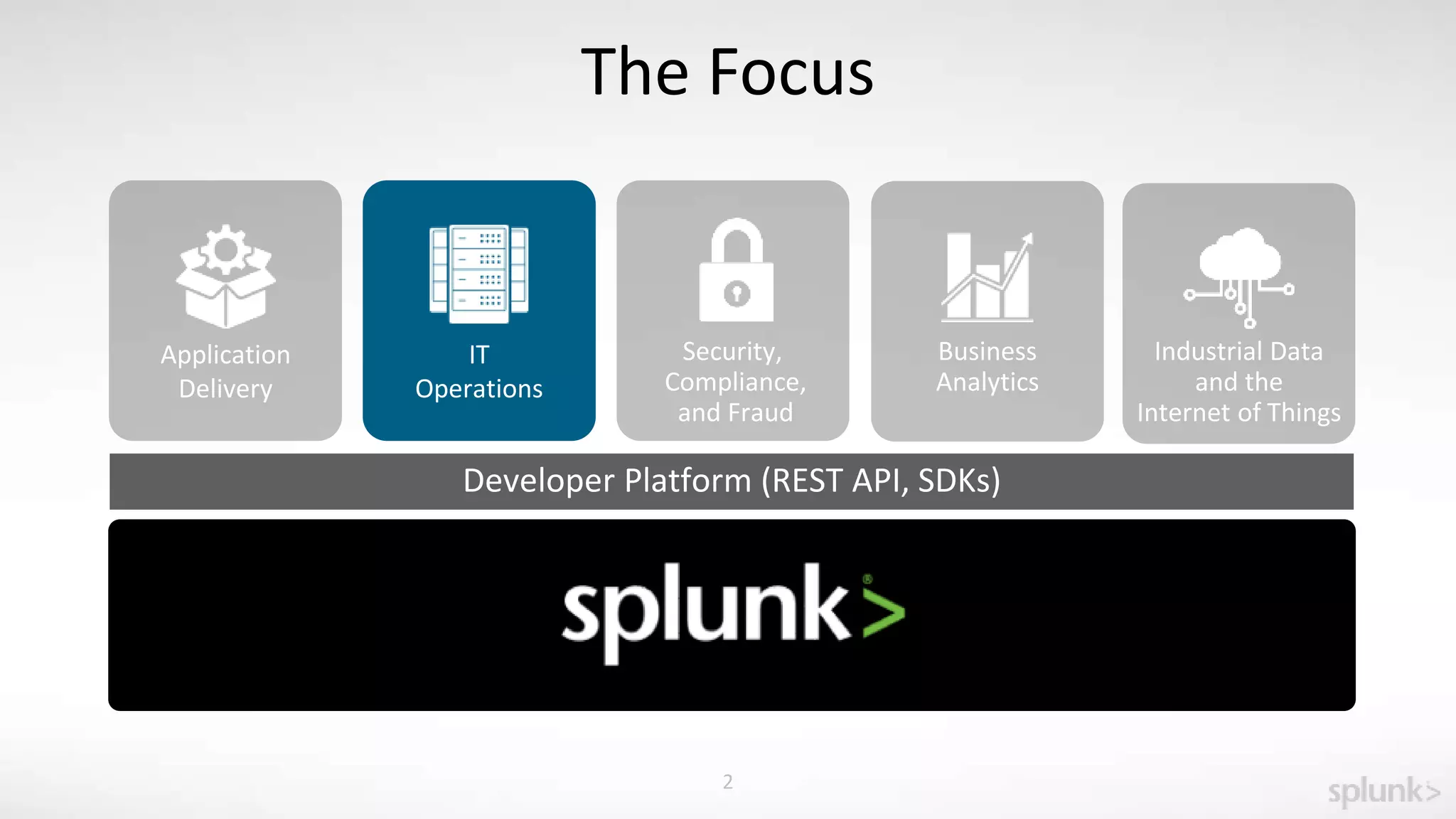
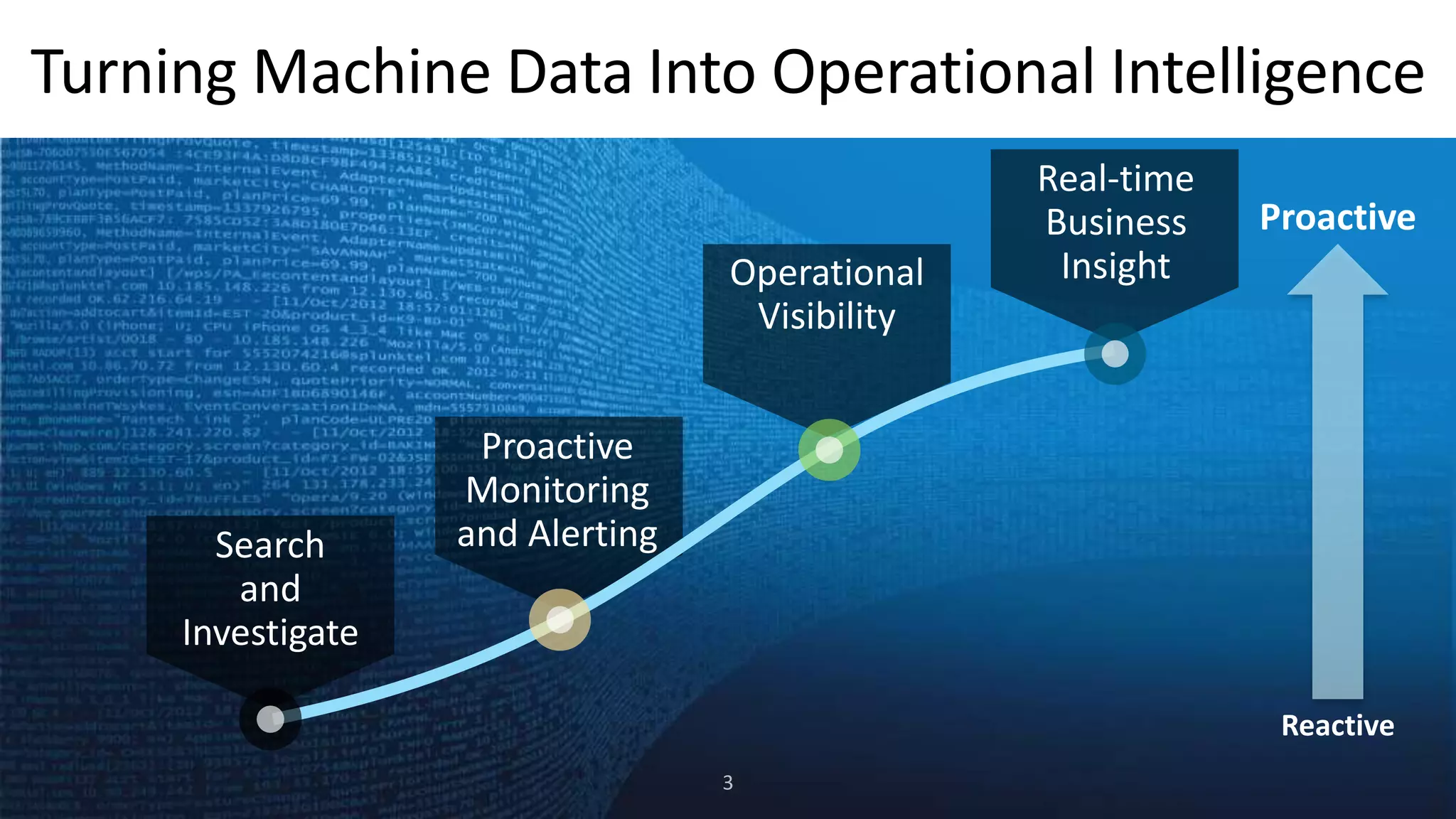
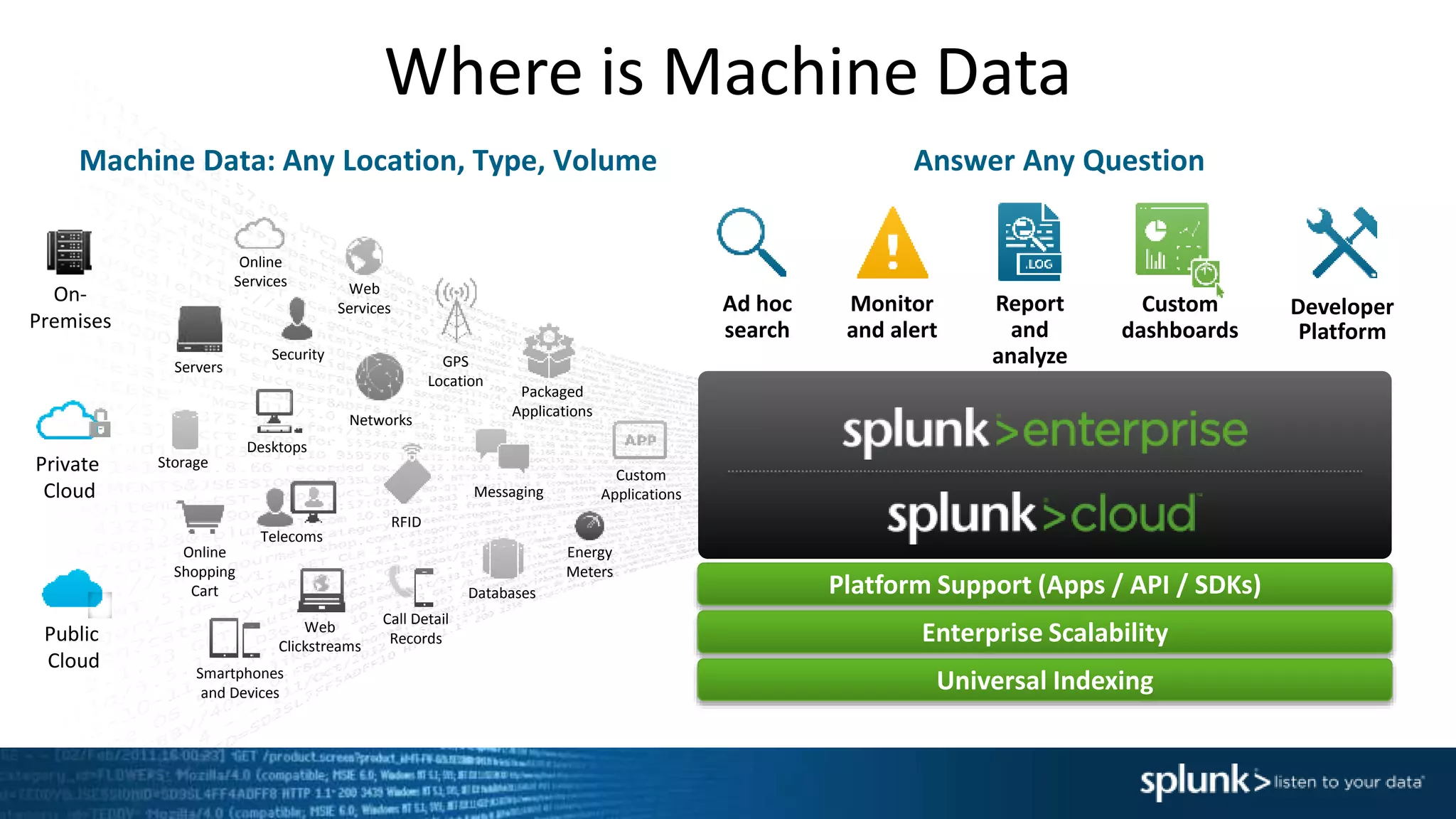
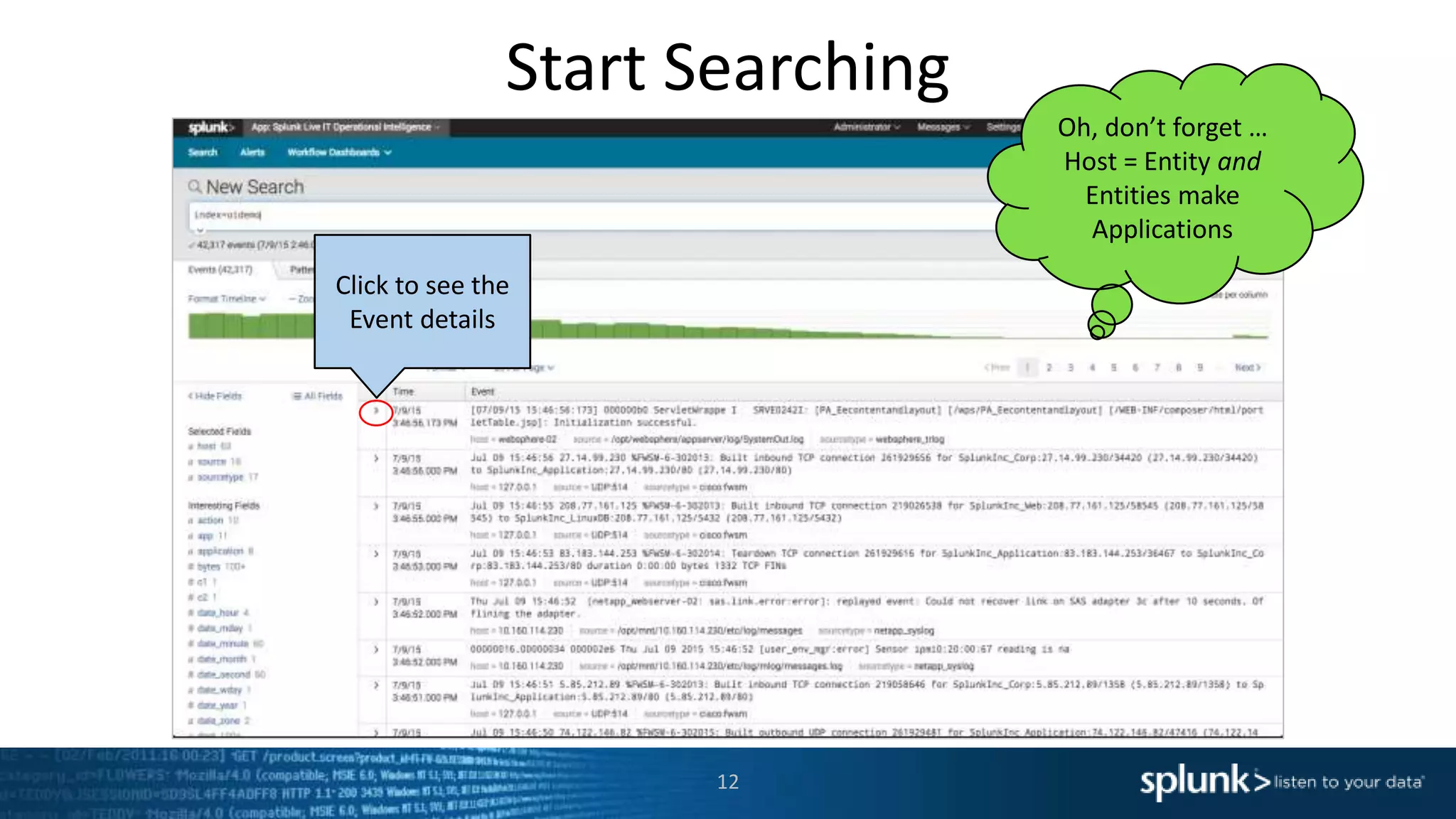
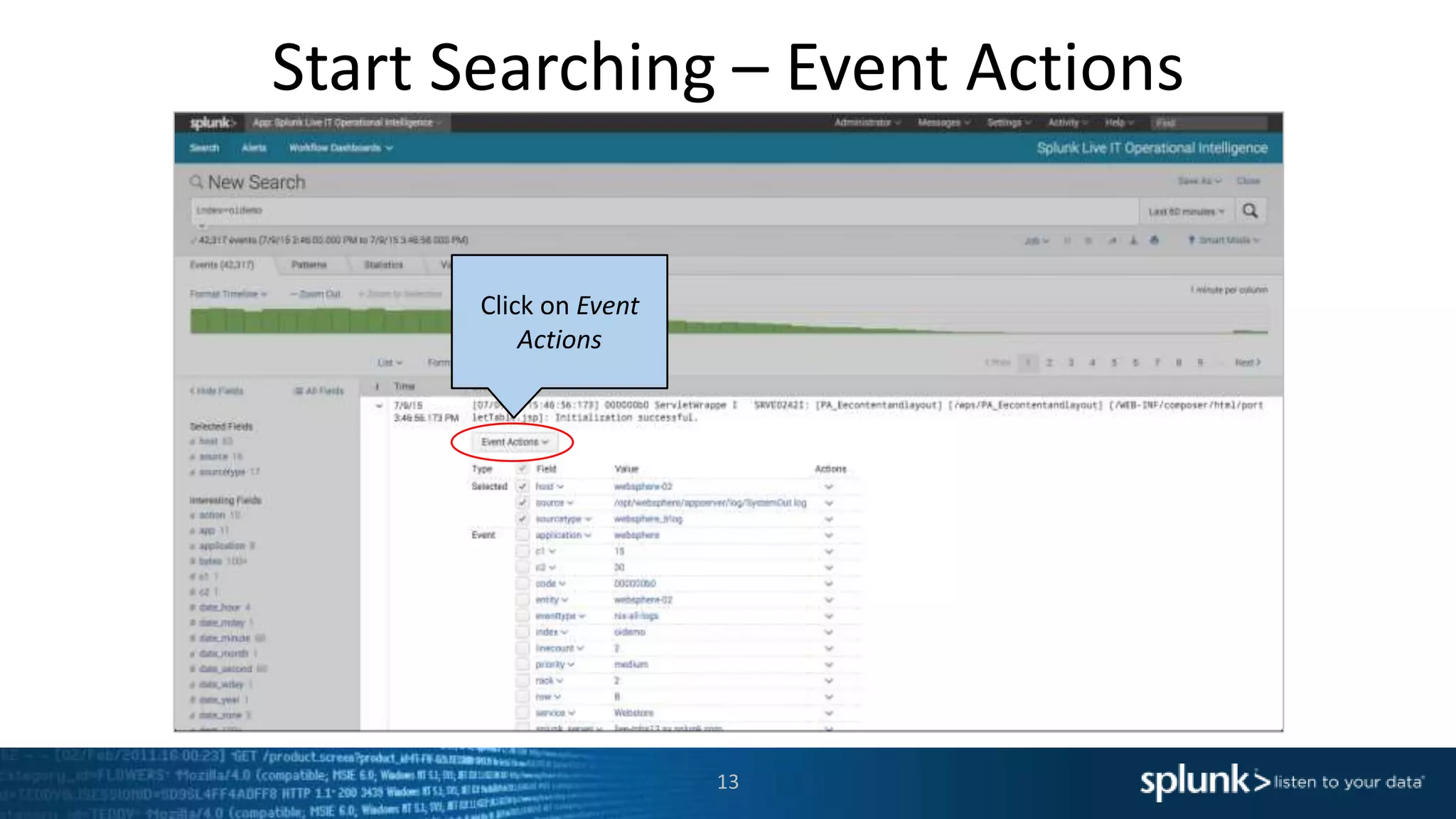
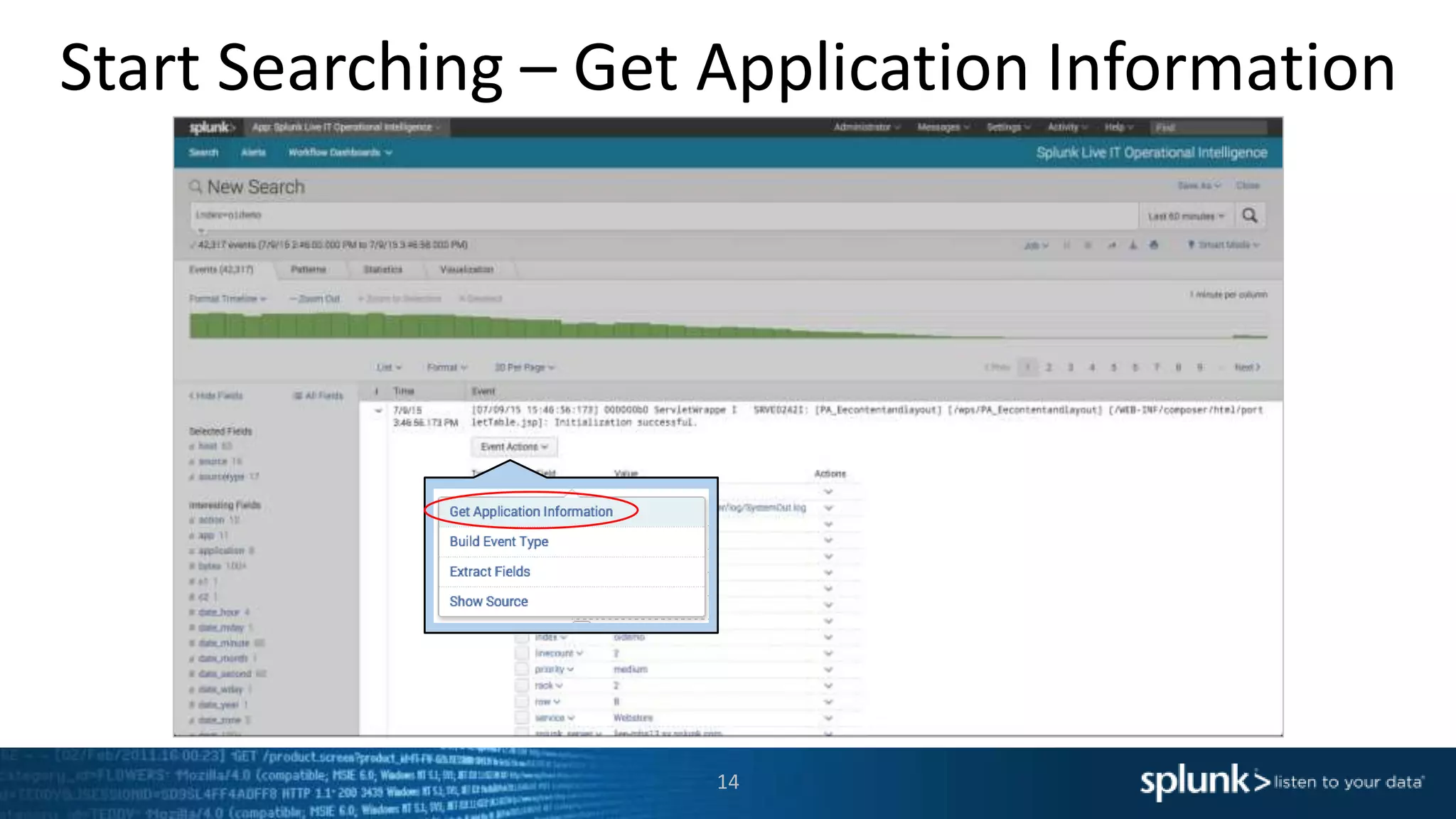
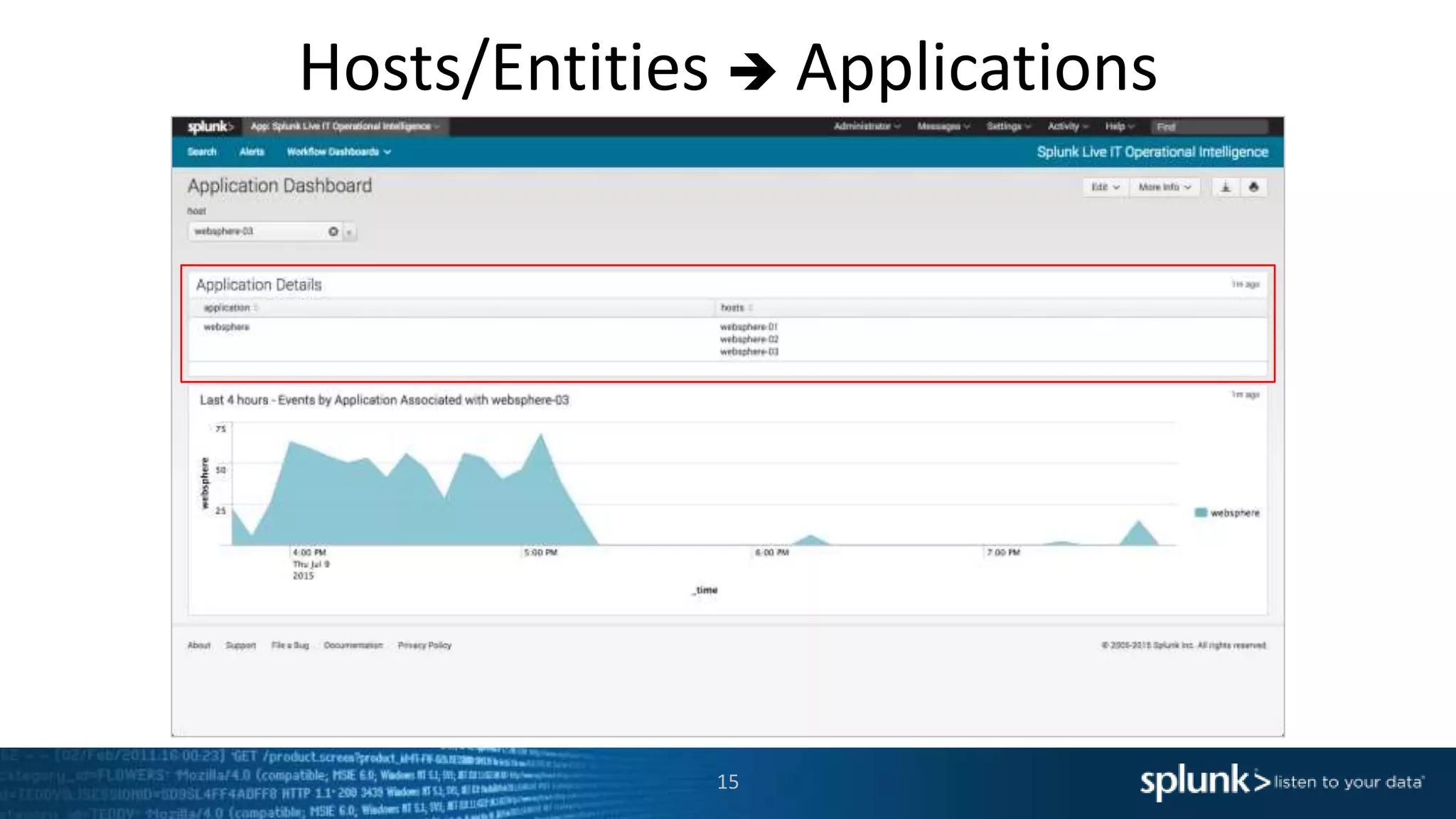
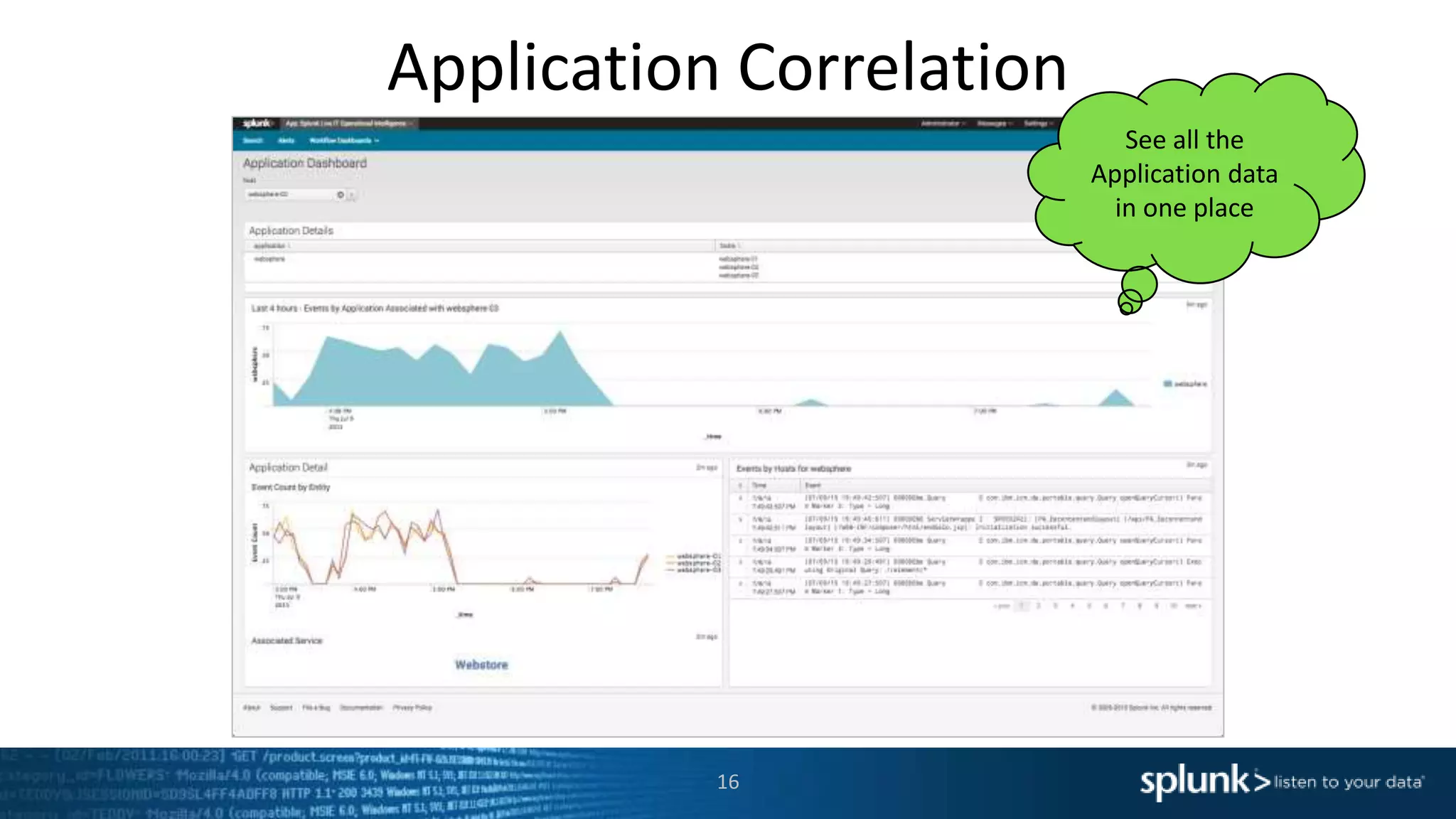
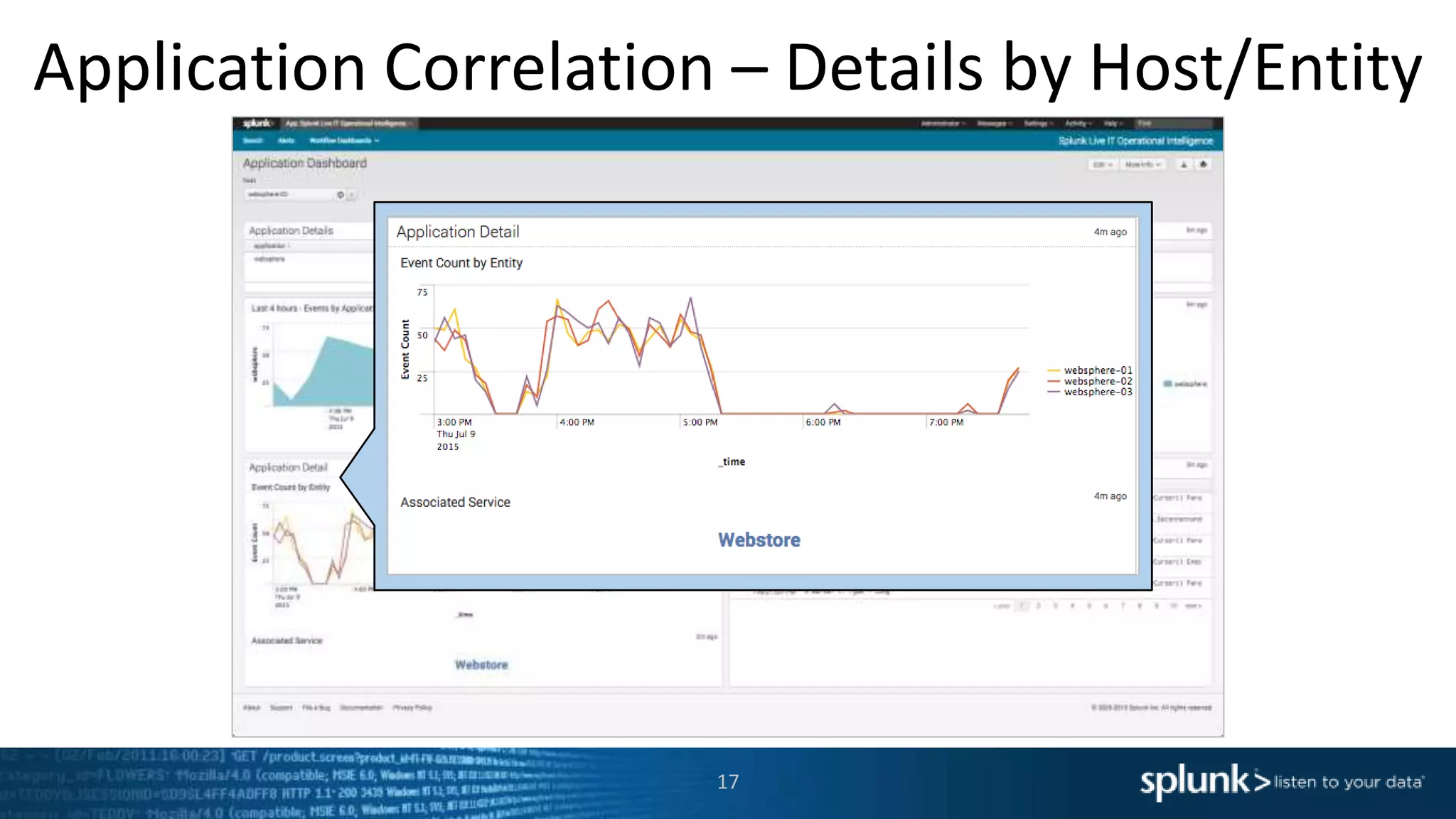
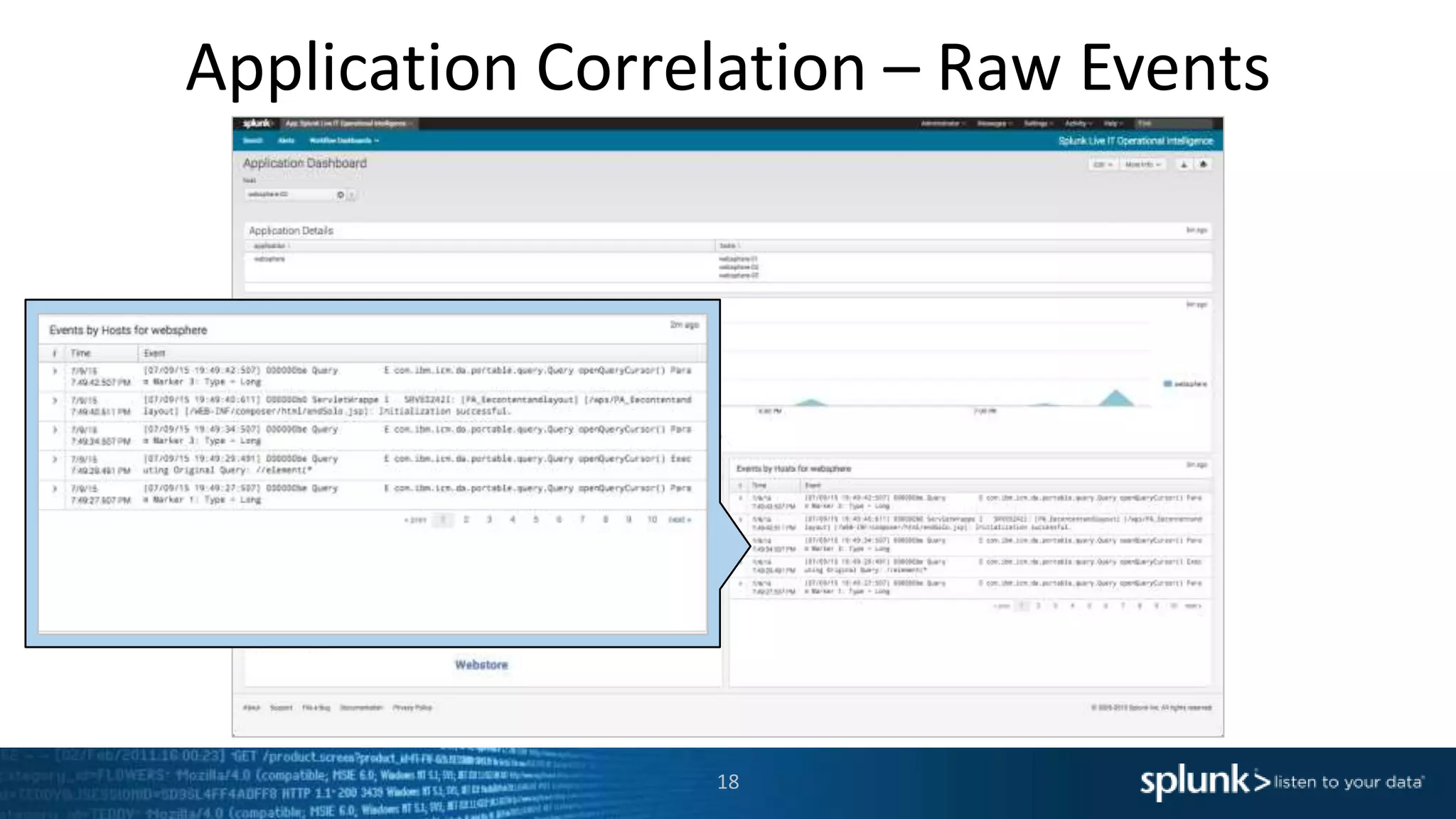
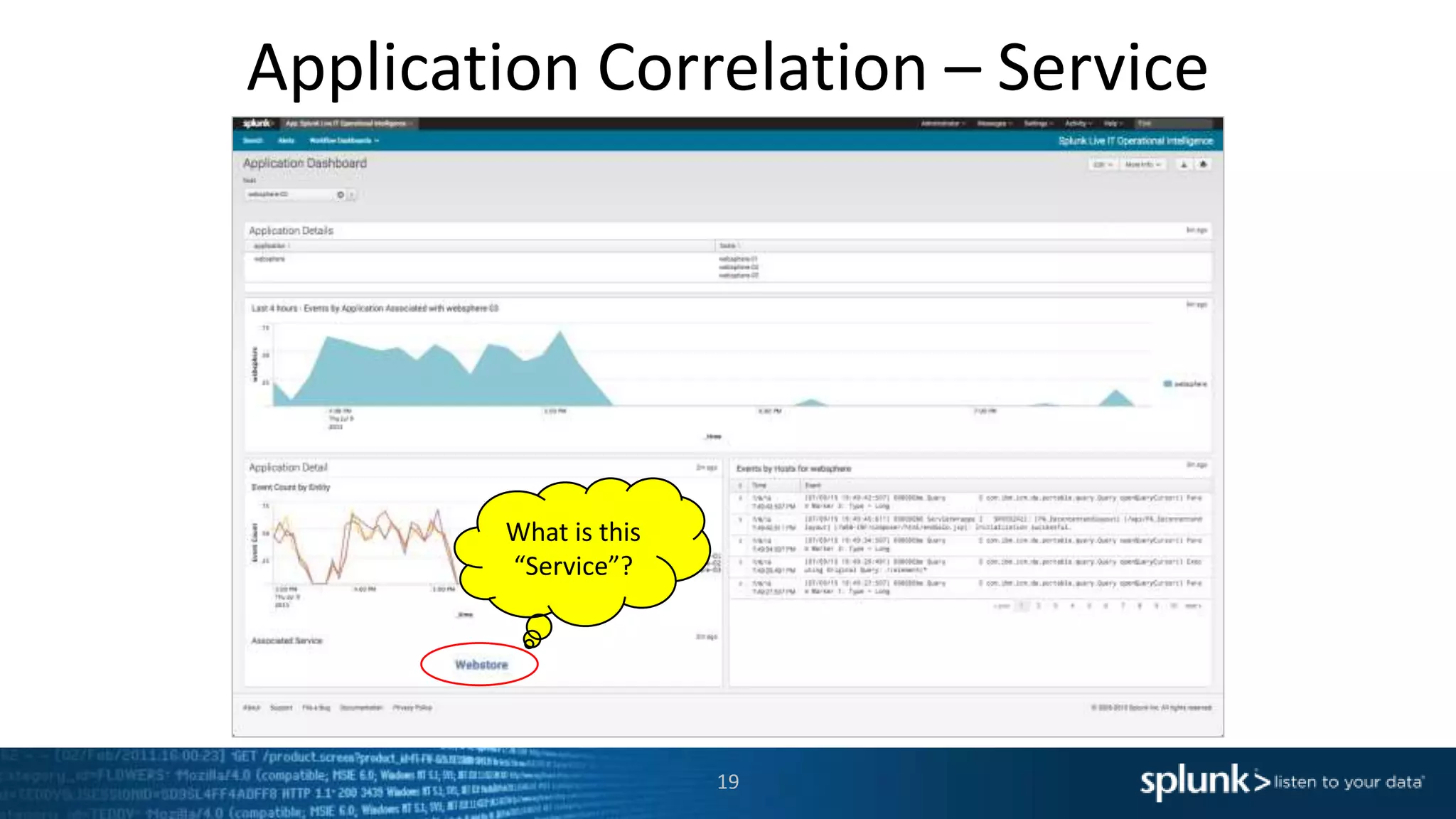
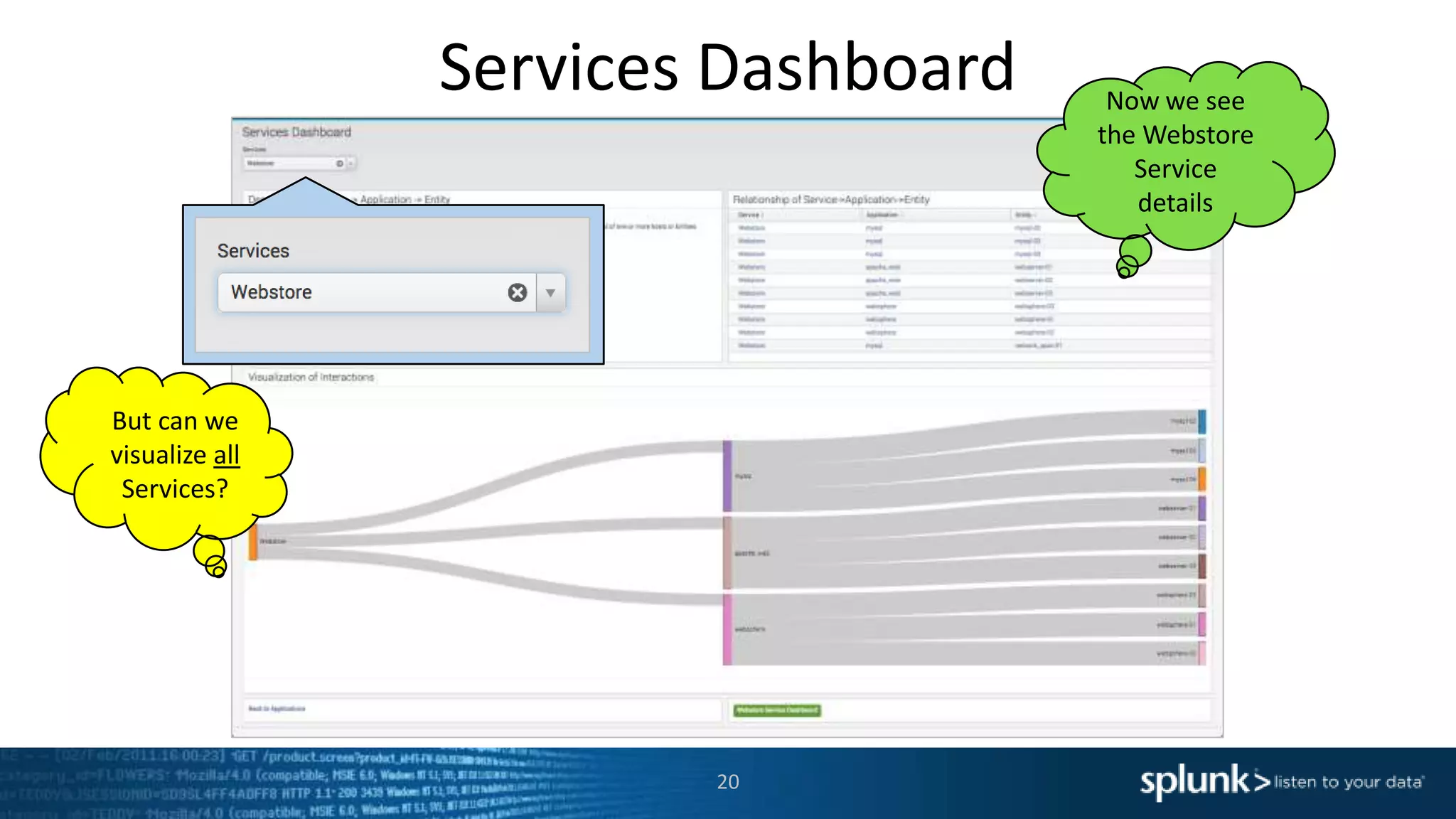
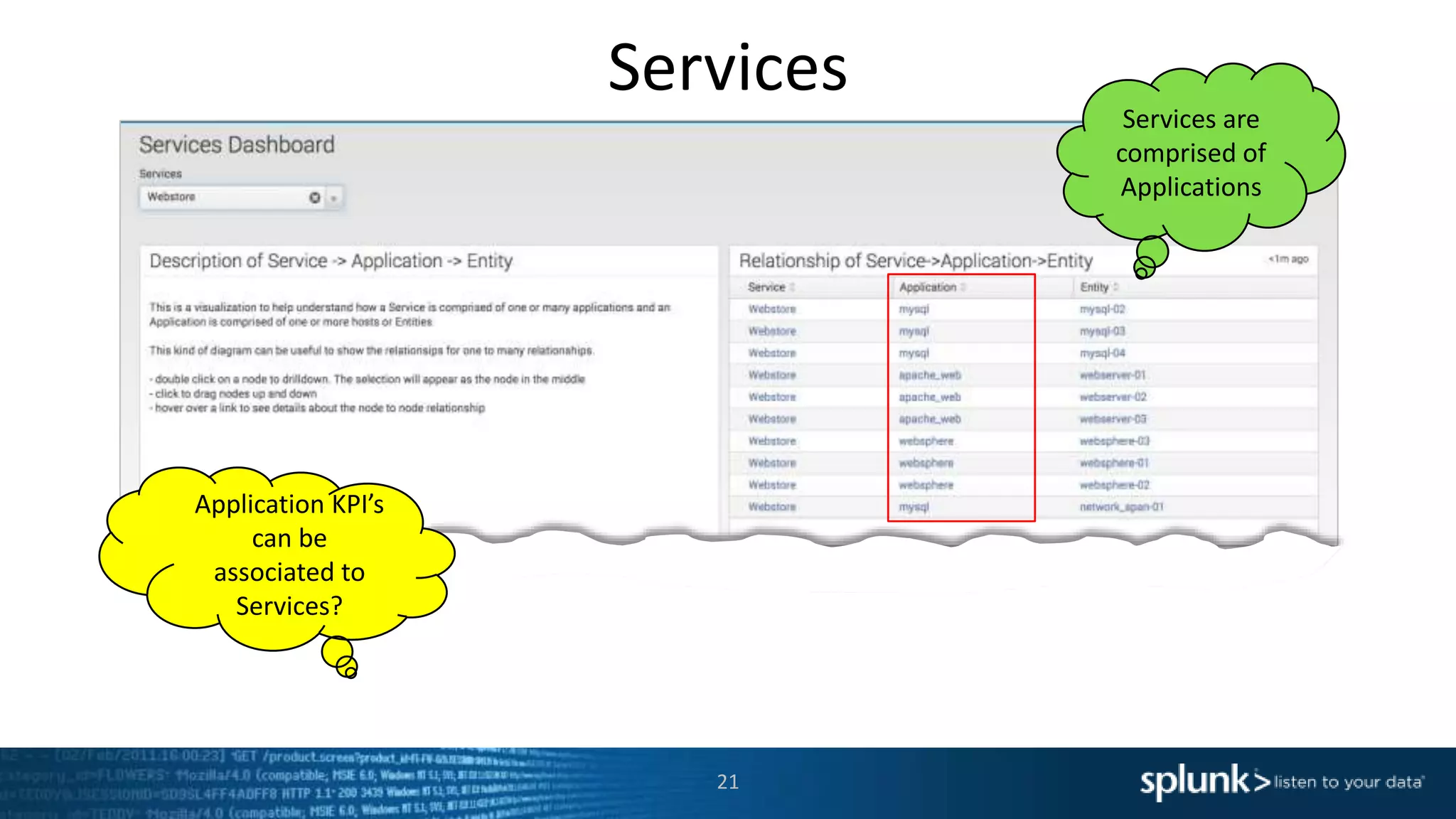
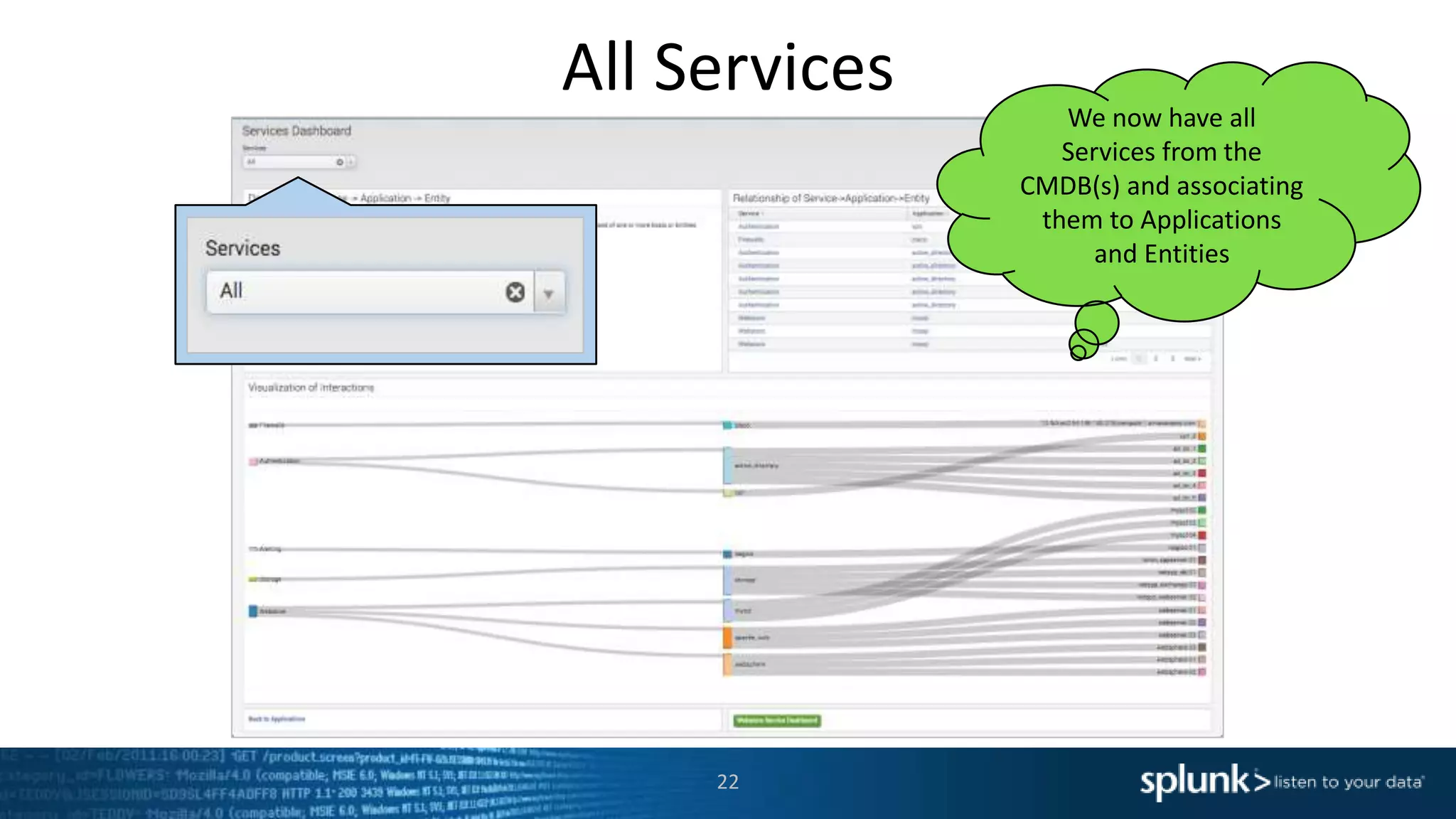
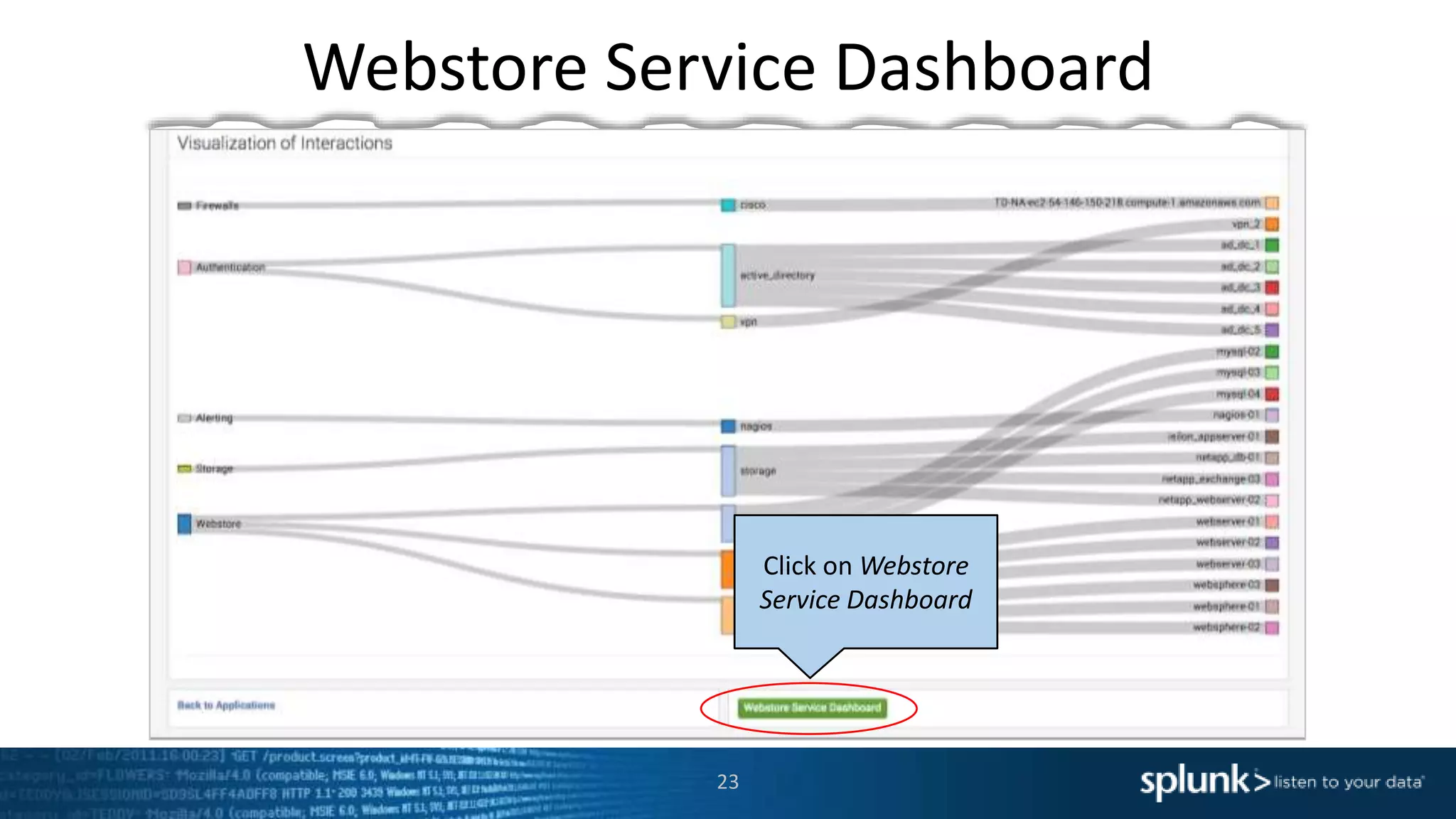
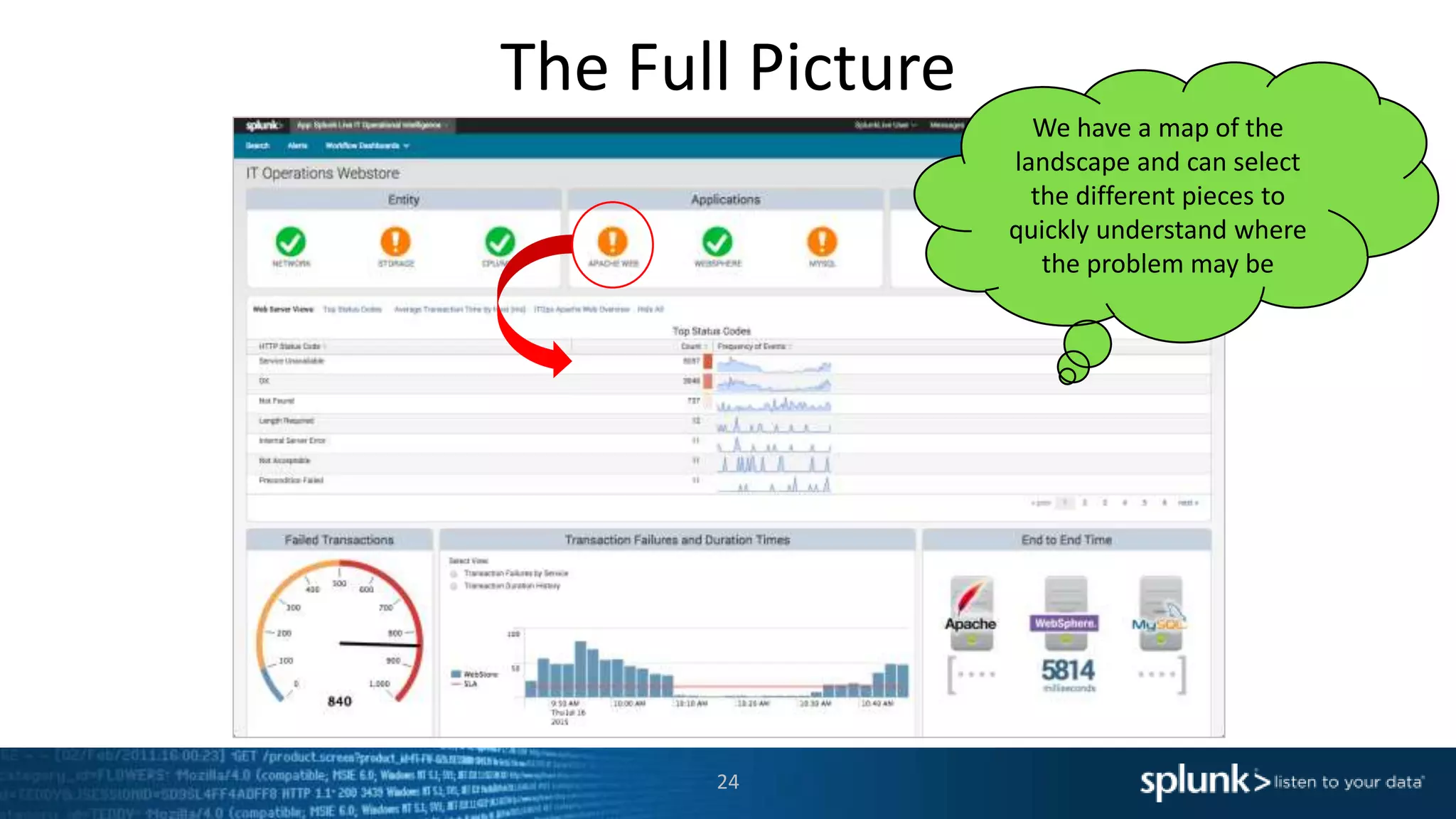
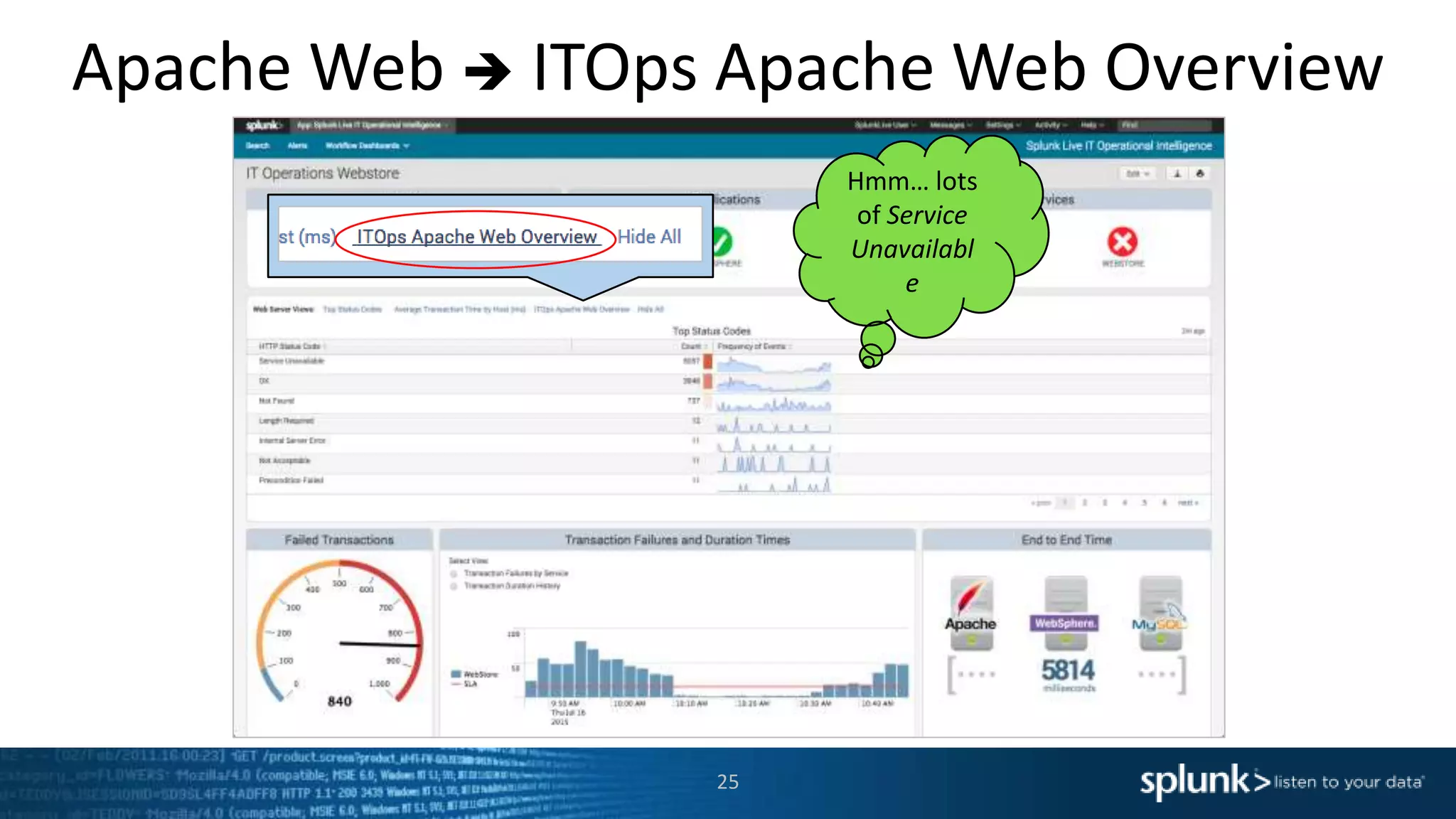
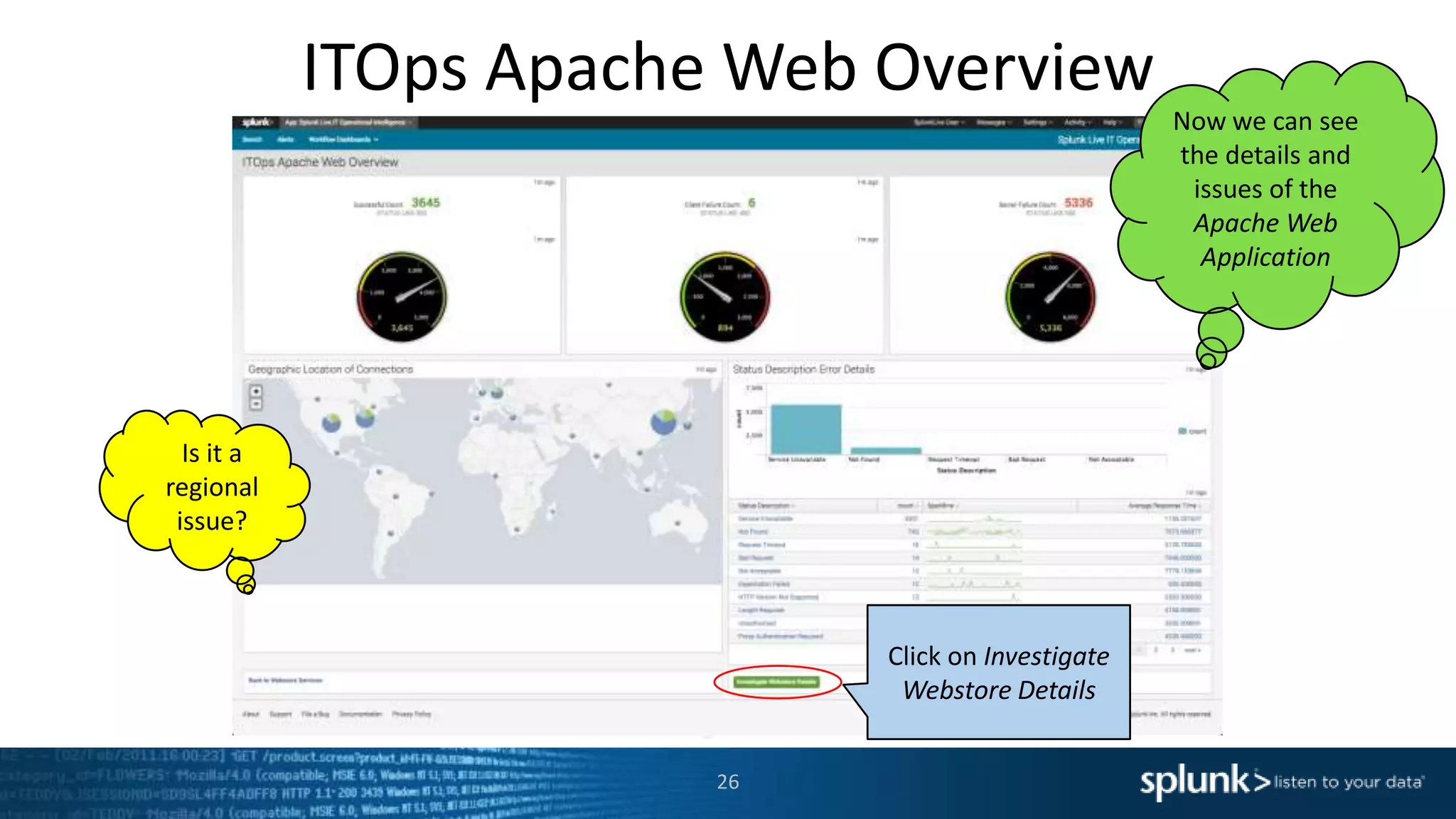
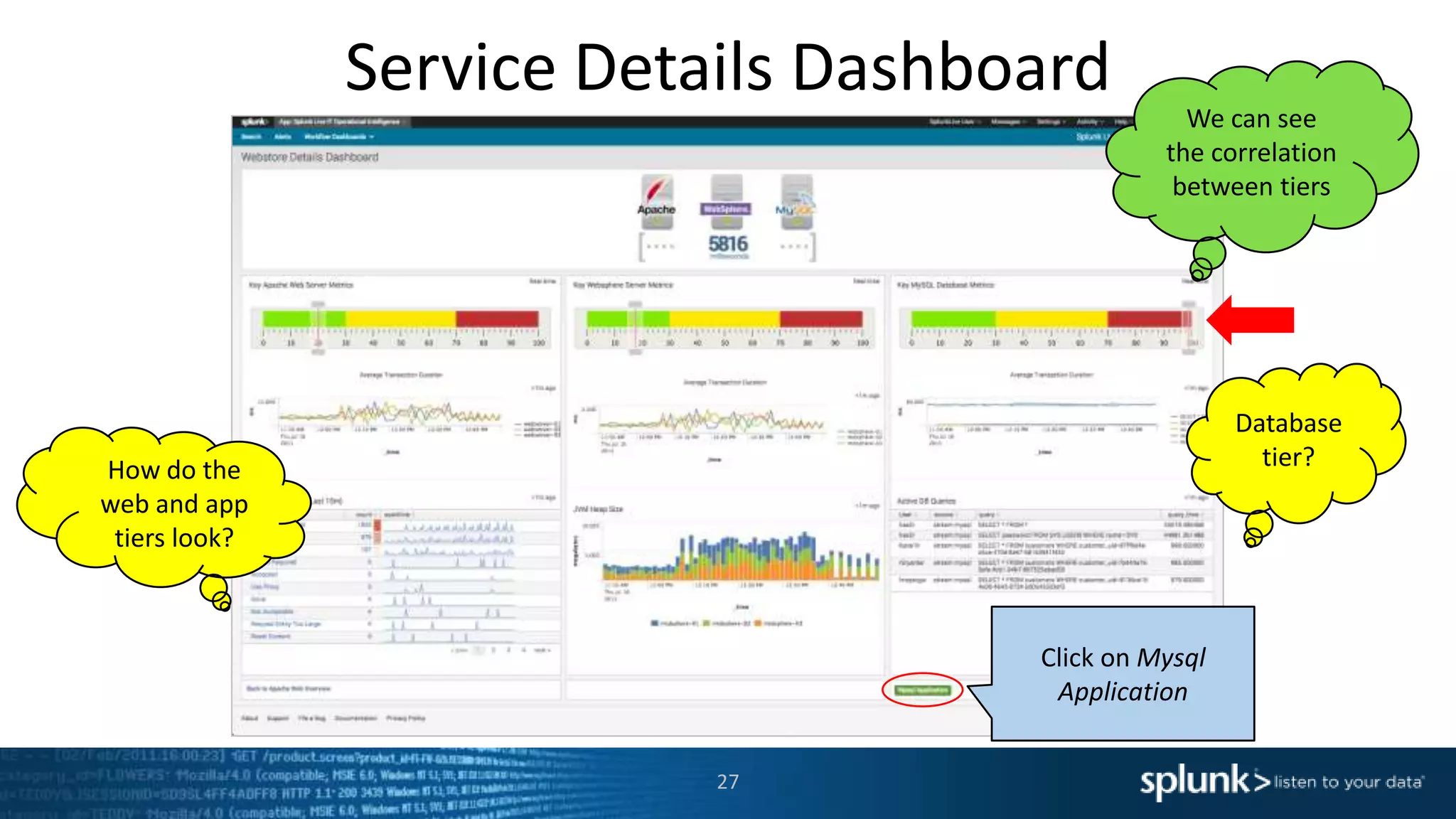
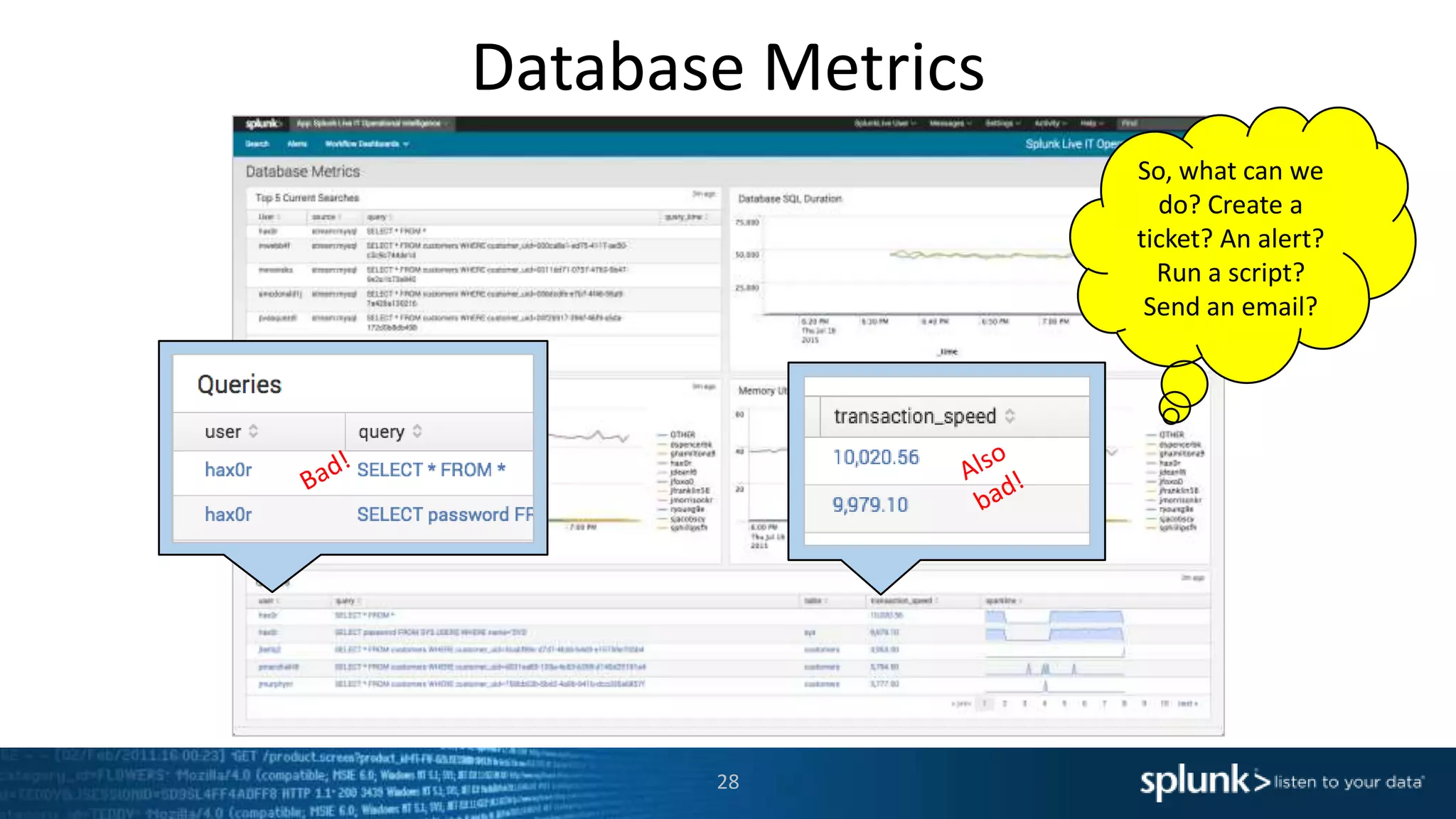
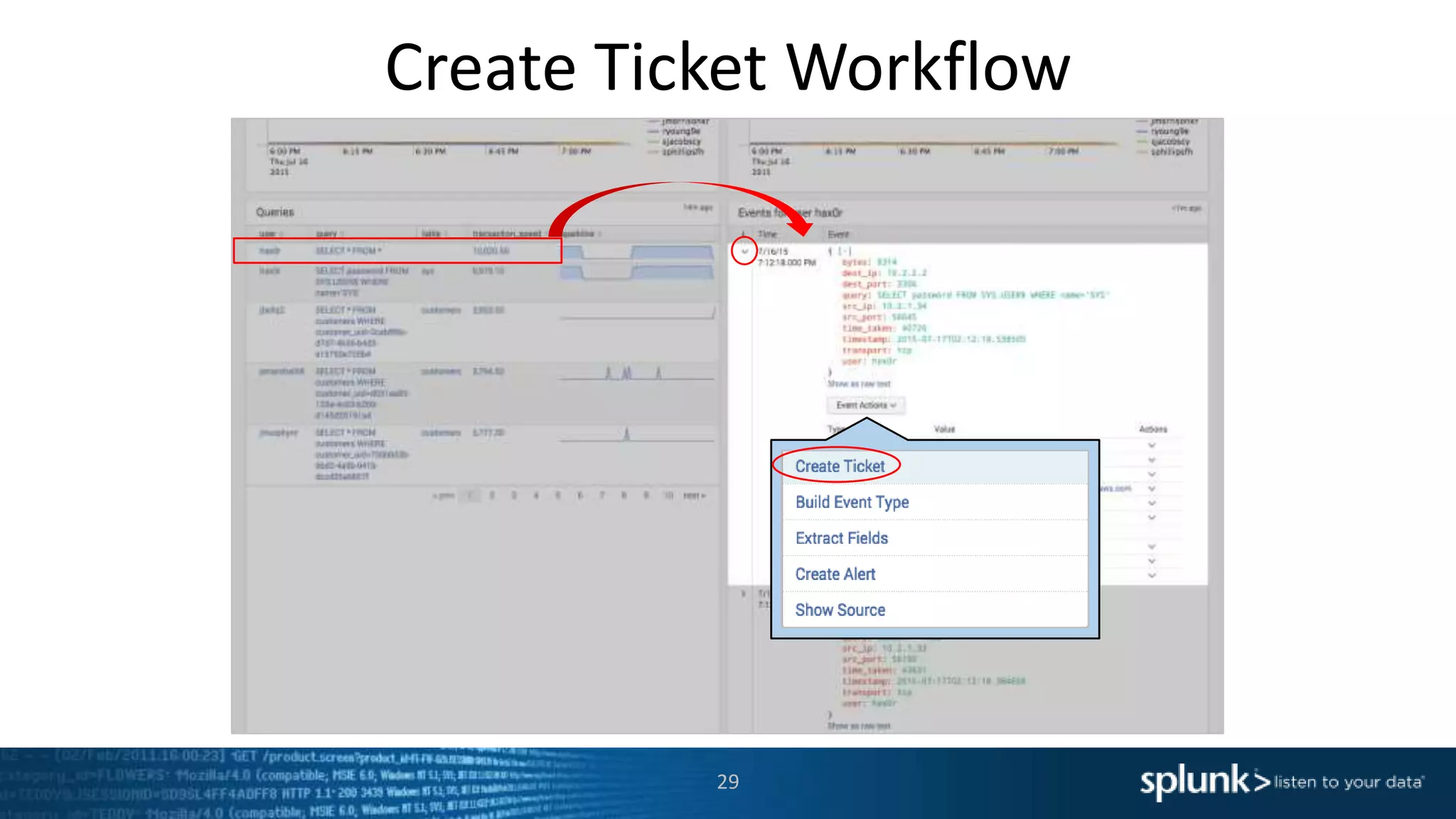
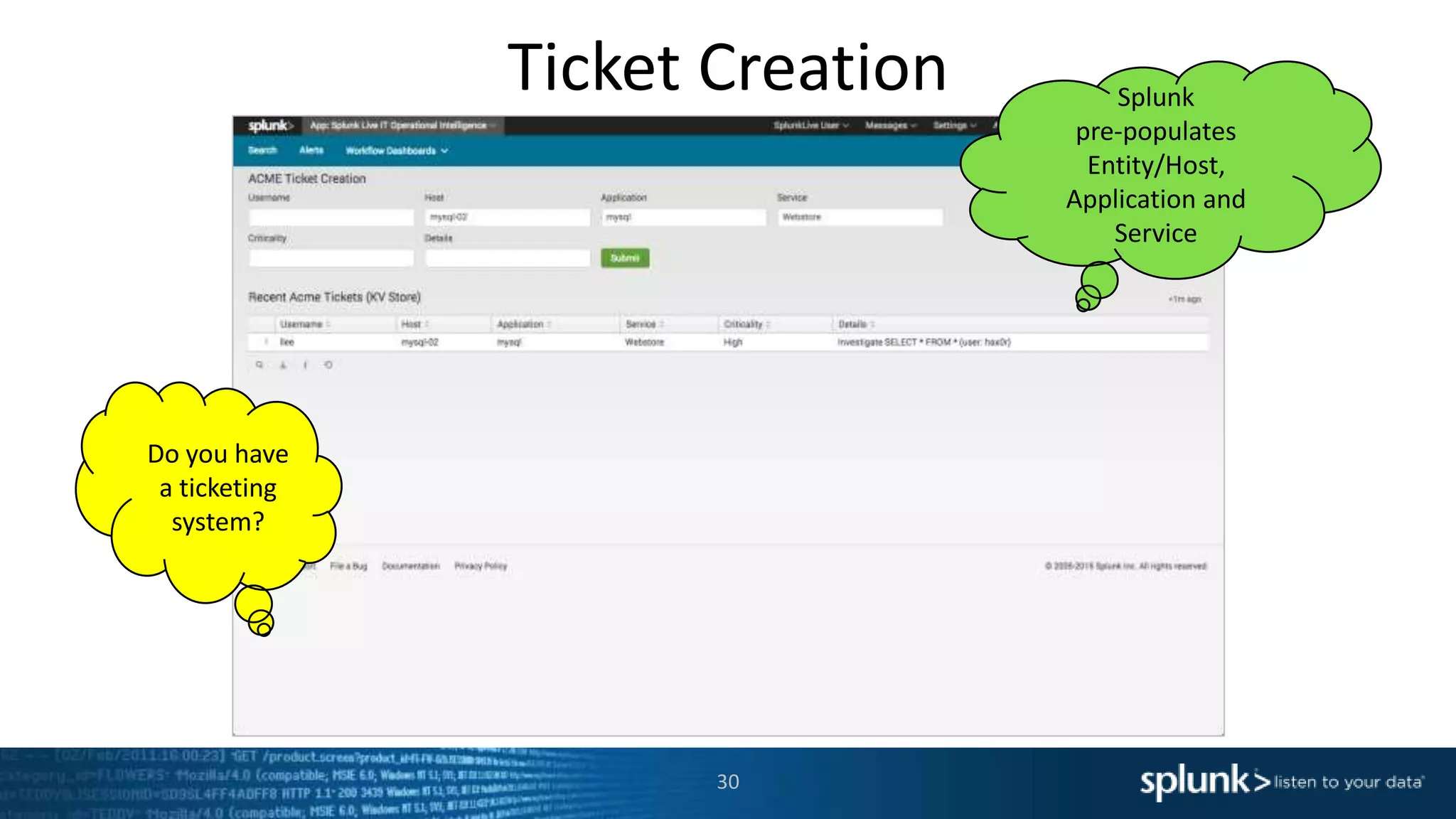
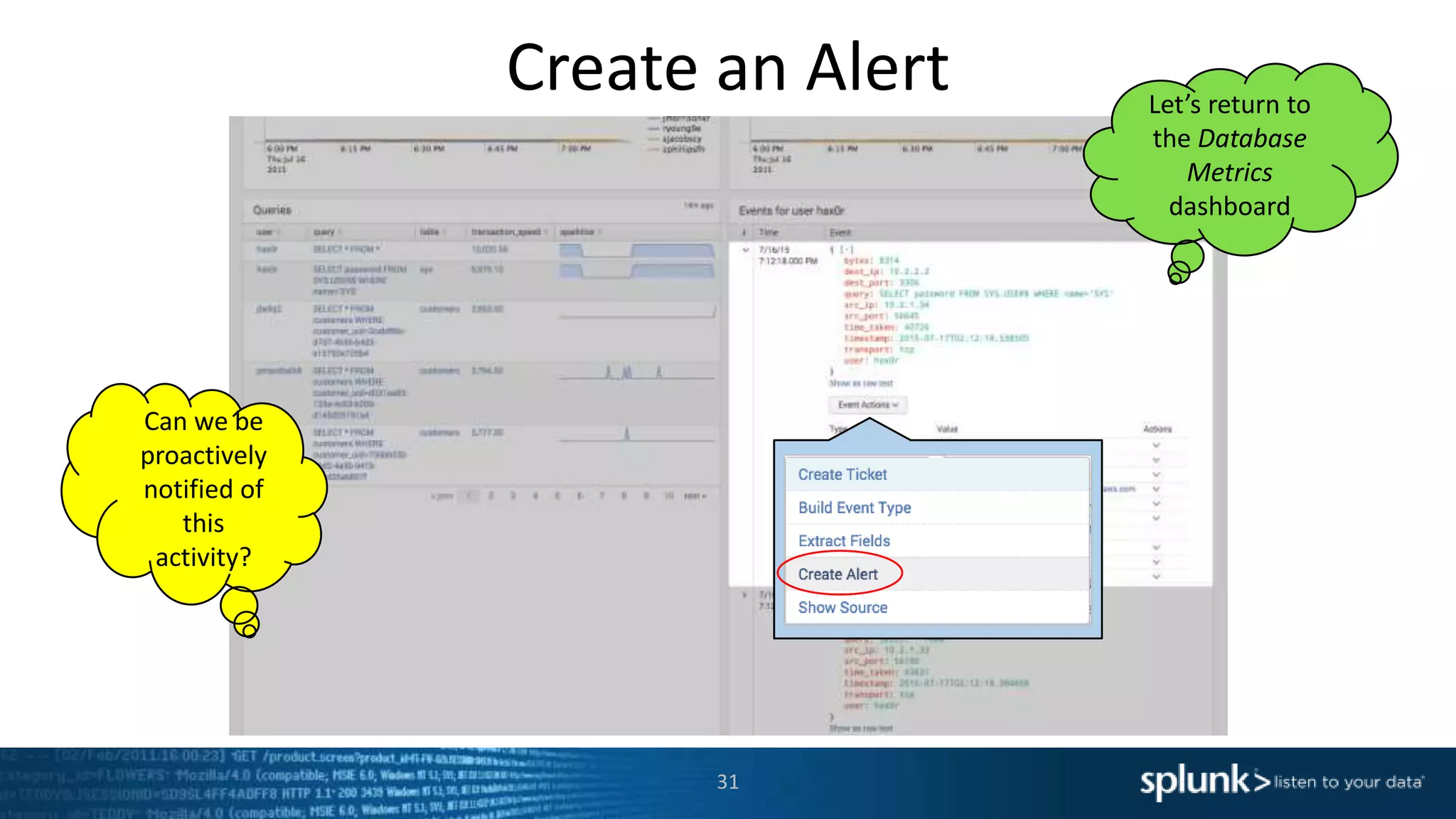
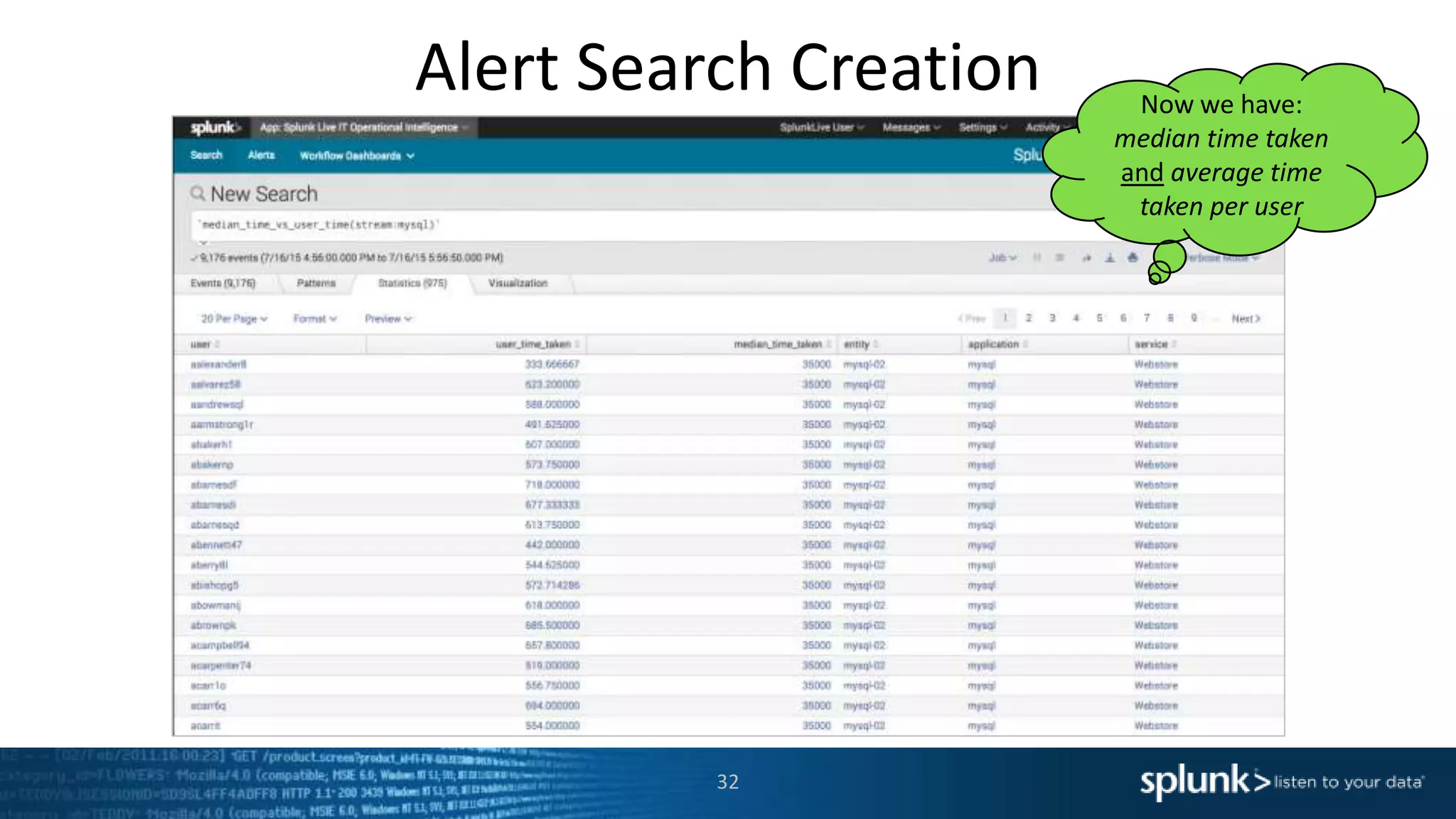
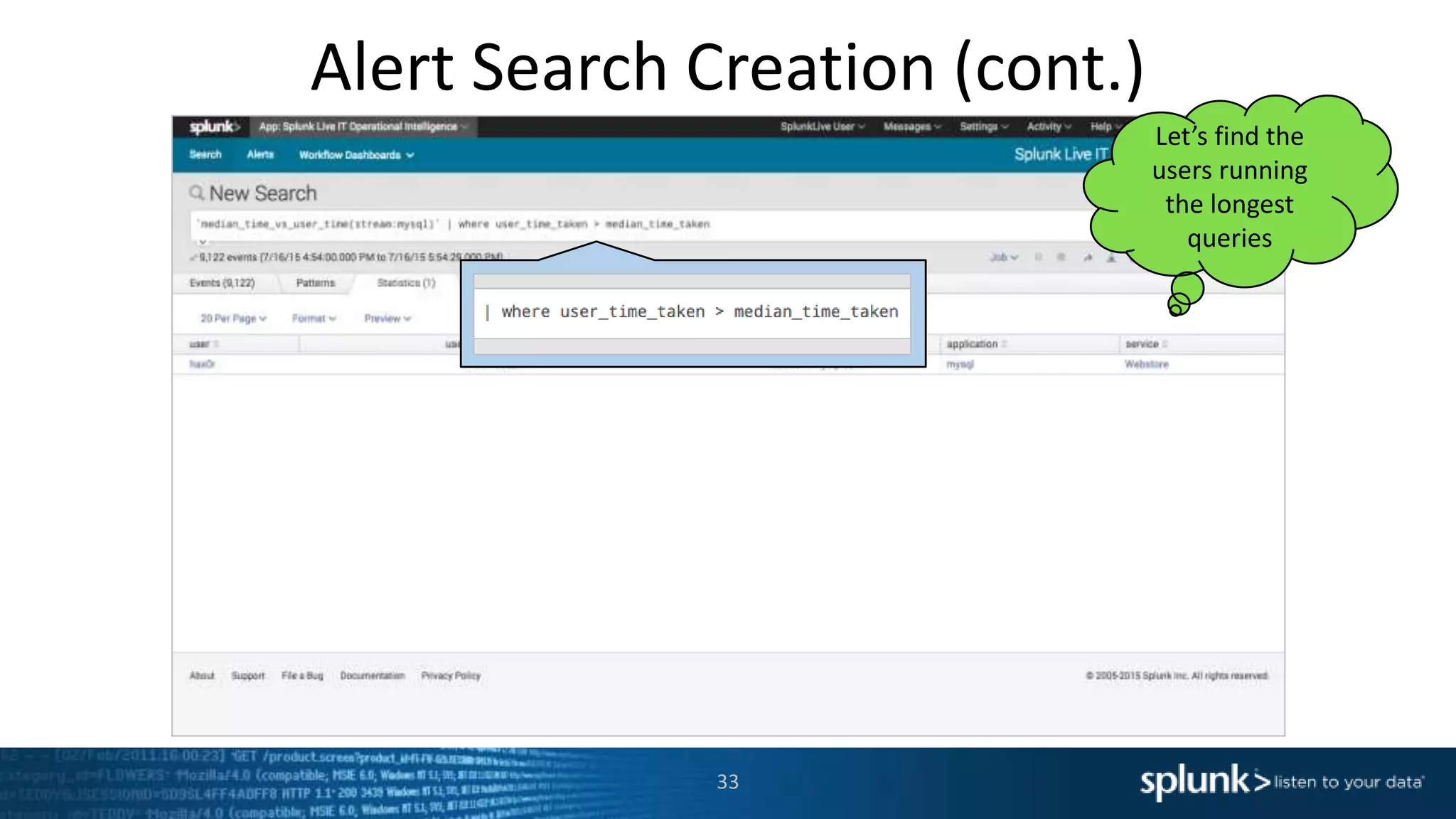
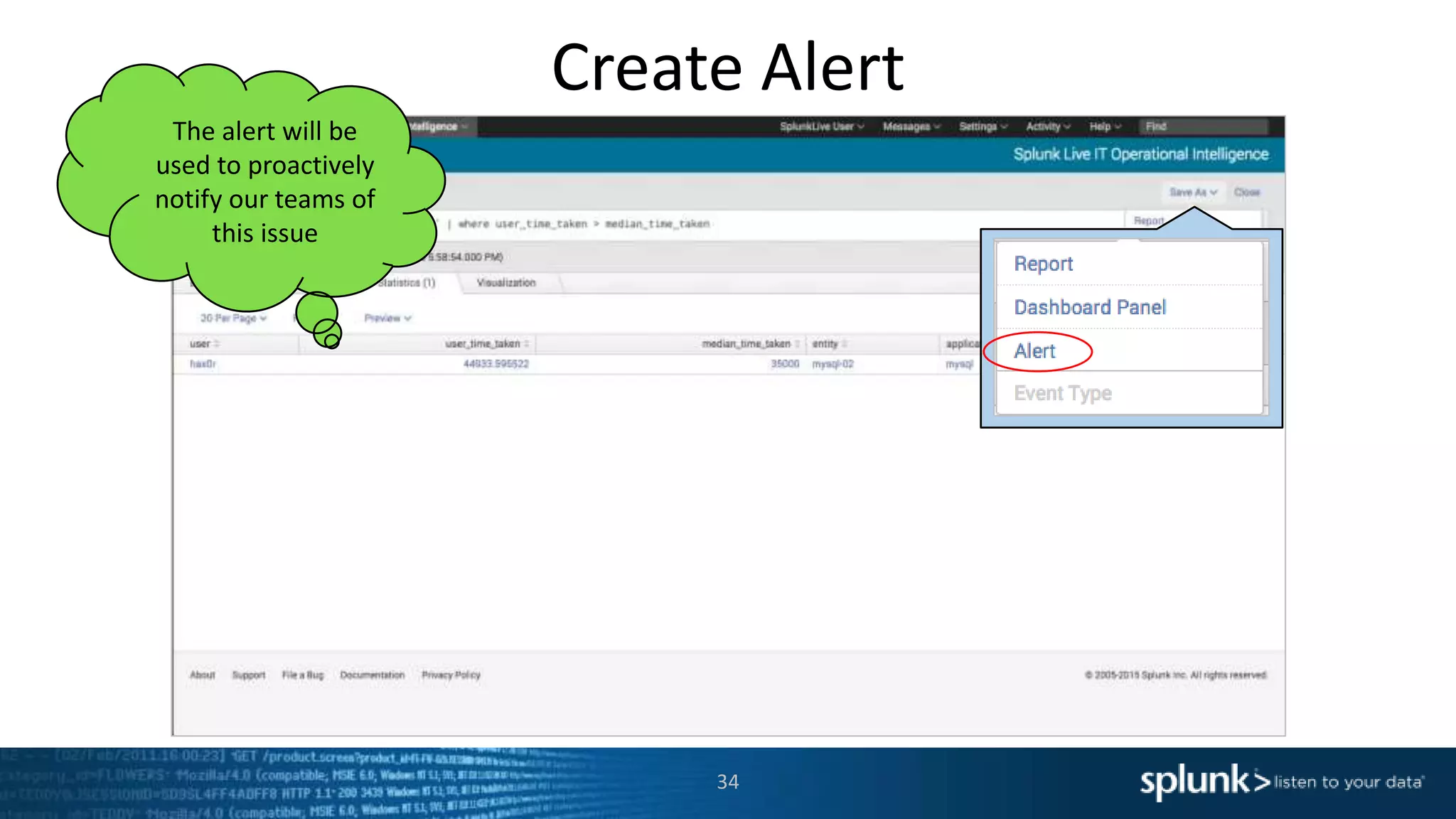
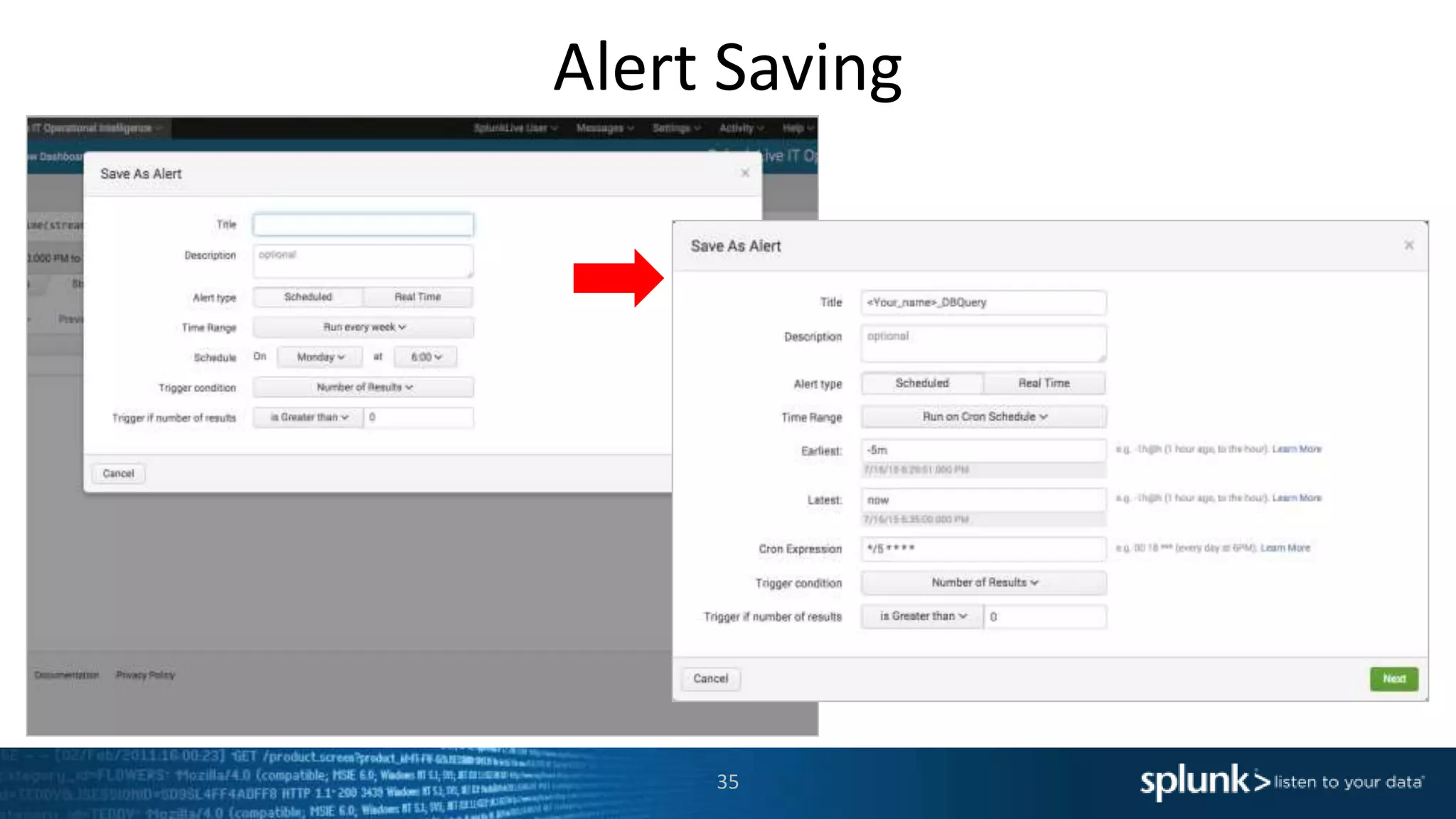
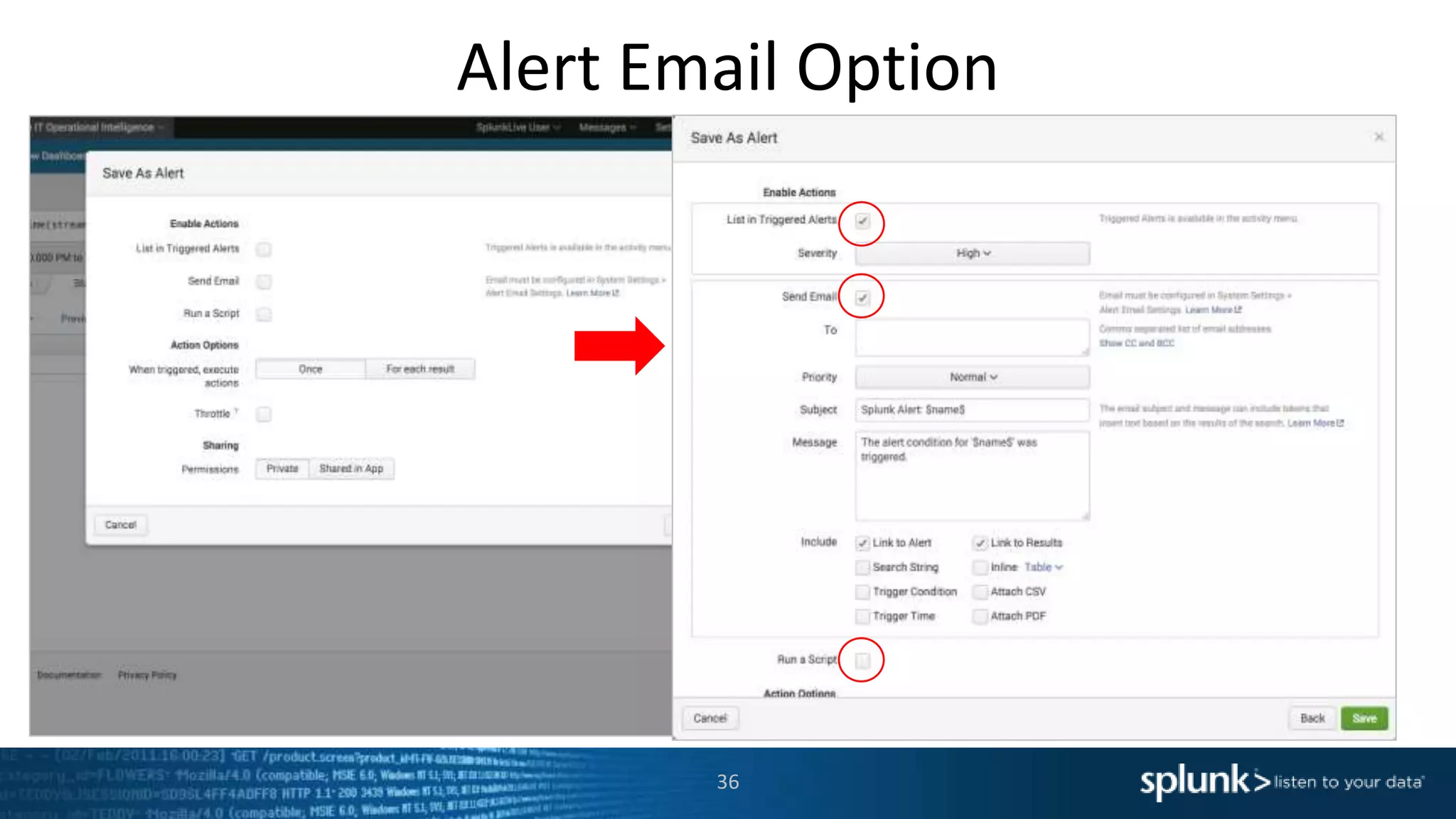
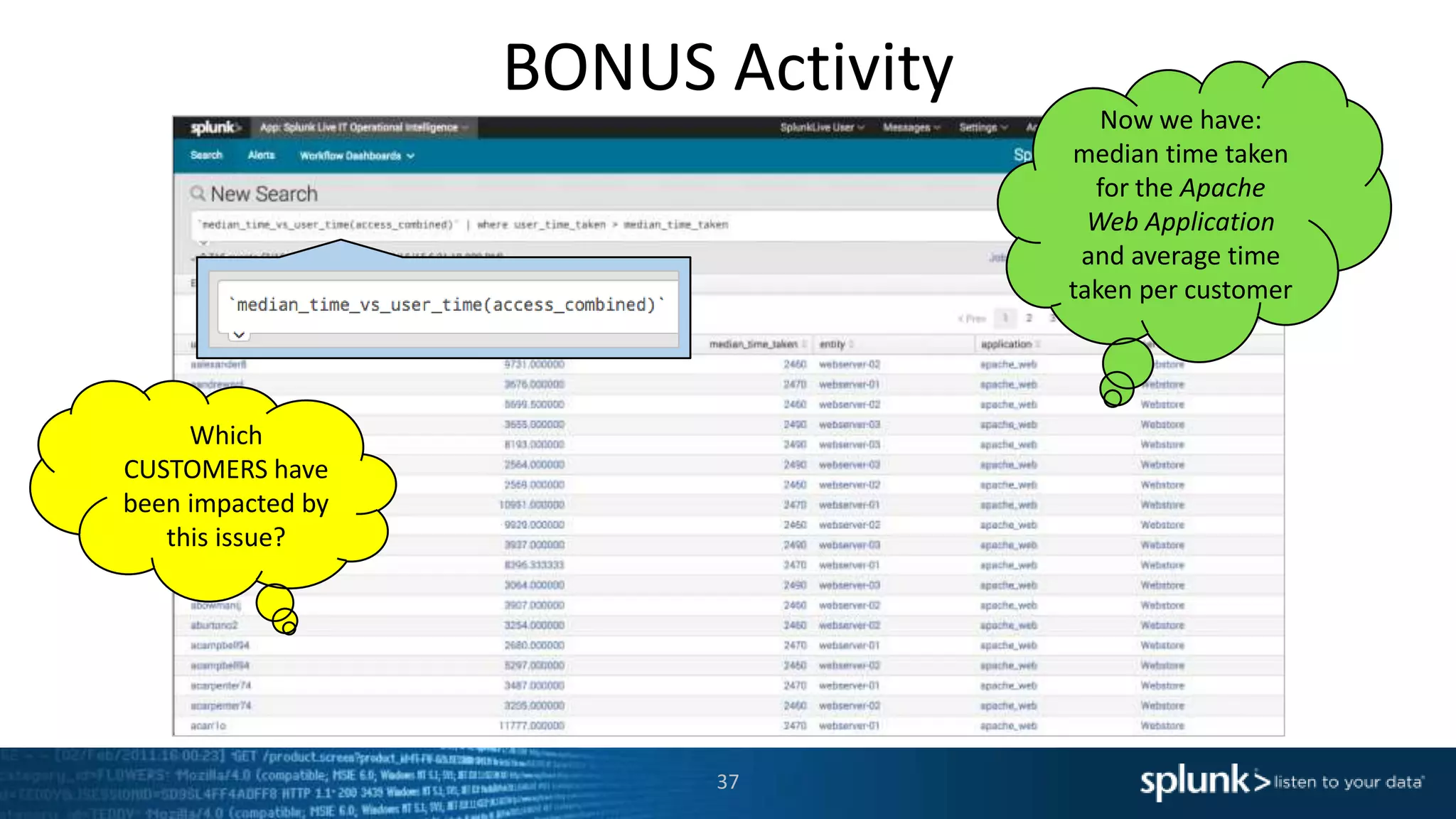
The document is a presentation about using Splunk for IT operations. It demonstrates how Splunk can be used to monitor applications and services, correlate issues across different tiers, create tickets and alerts when issues arise, and provide operational visibility and intelligence. Live demonstrations show searching log data to diagnose a webstore issue, visualizing applications and services, and setting up an alert to be proactively notified of database query performance problems.