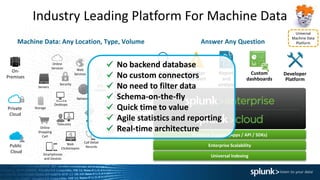
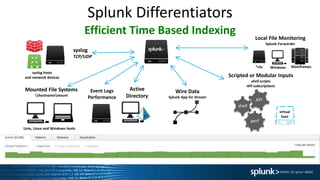
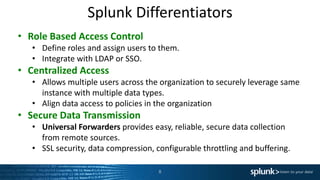
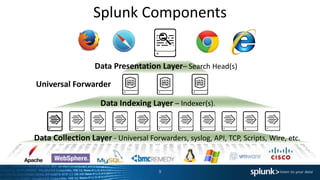
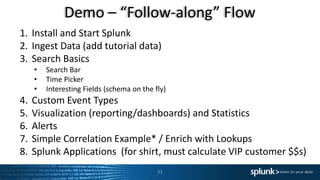
The document provides a comprehensive overview of Splunk Enterprise, detailing its functionalities, differentiating features, and components necessary for data management and analysis. It emphasizes the rapid growth and complexity of machine data and outlines the steps for getting started with Splunk, including installation and data ingestion. Additionally, it encourages users to utilize available educational resources and emphasizes the importance of community engagement.