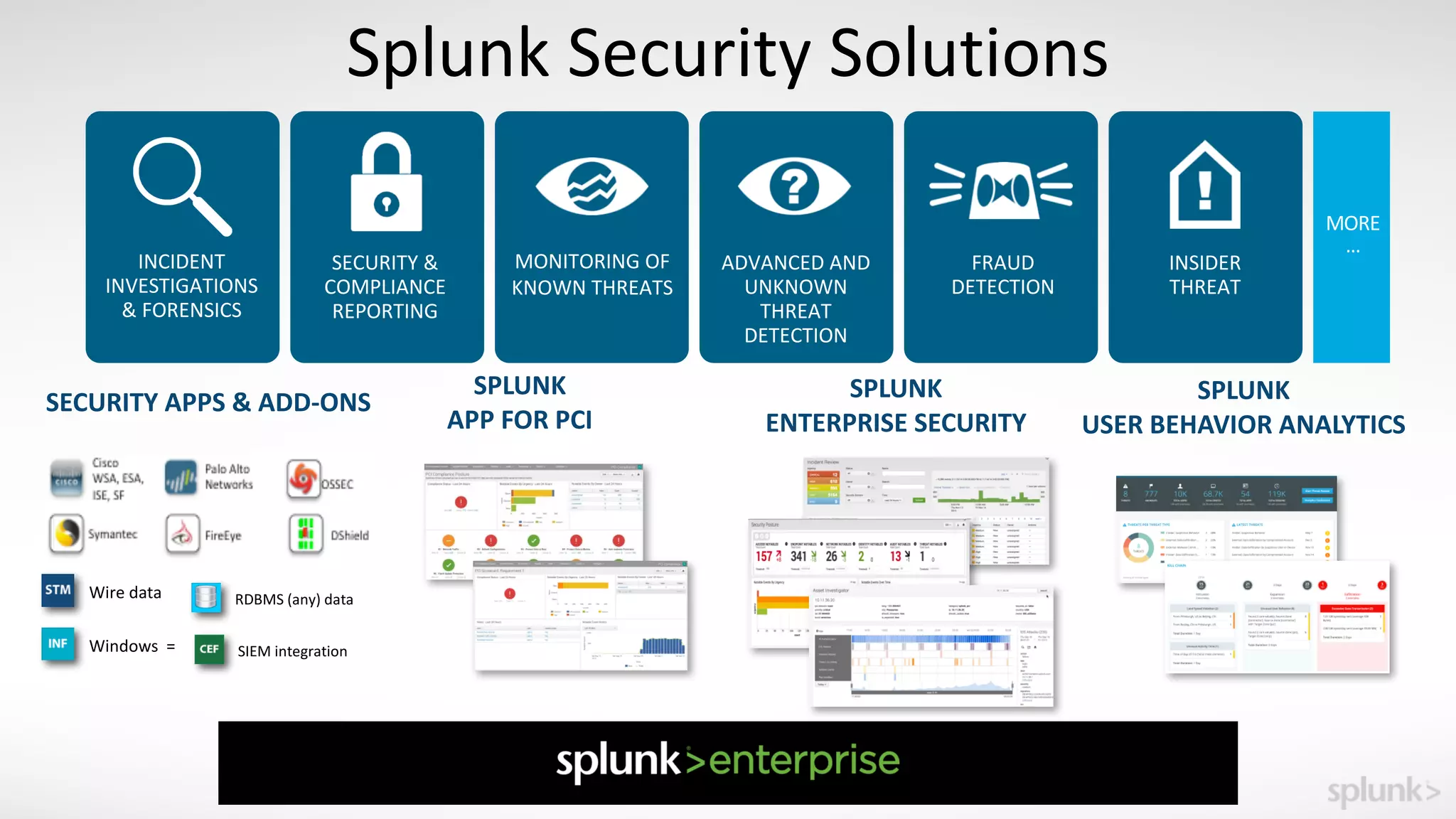
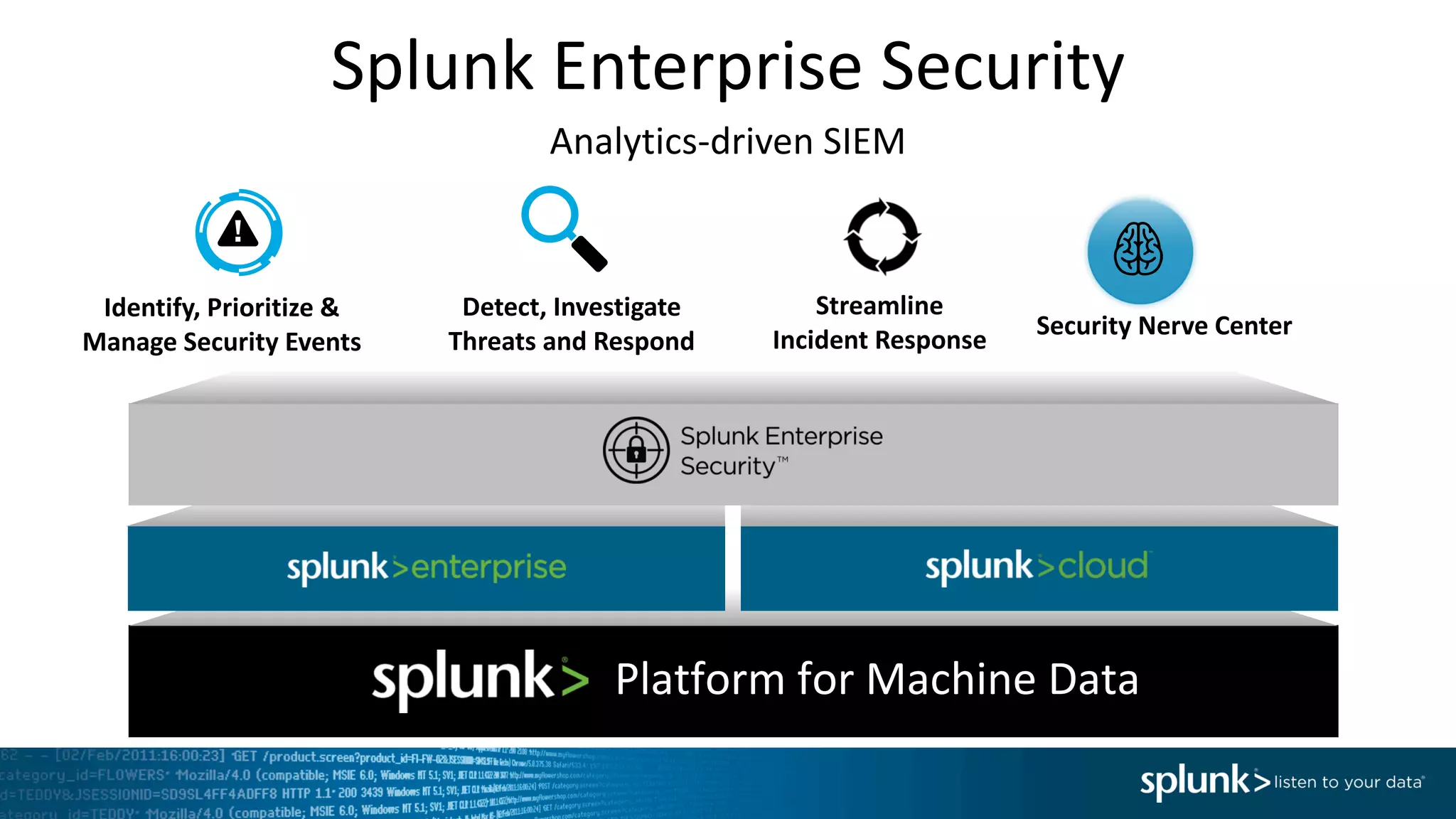
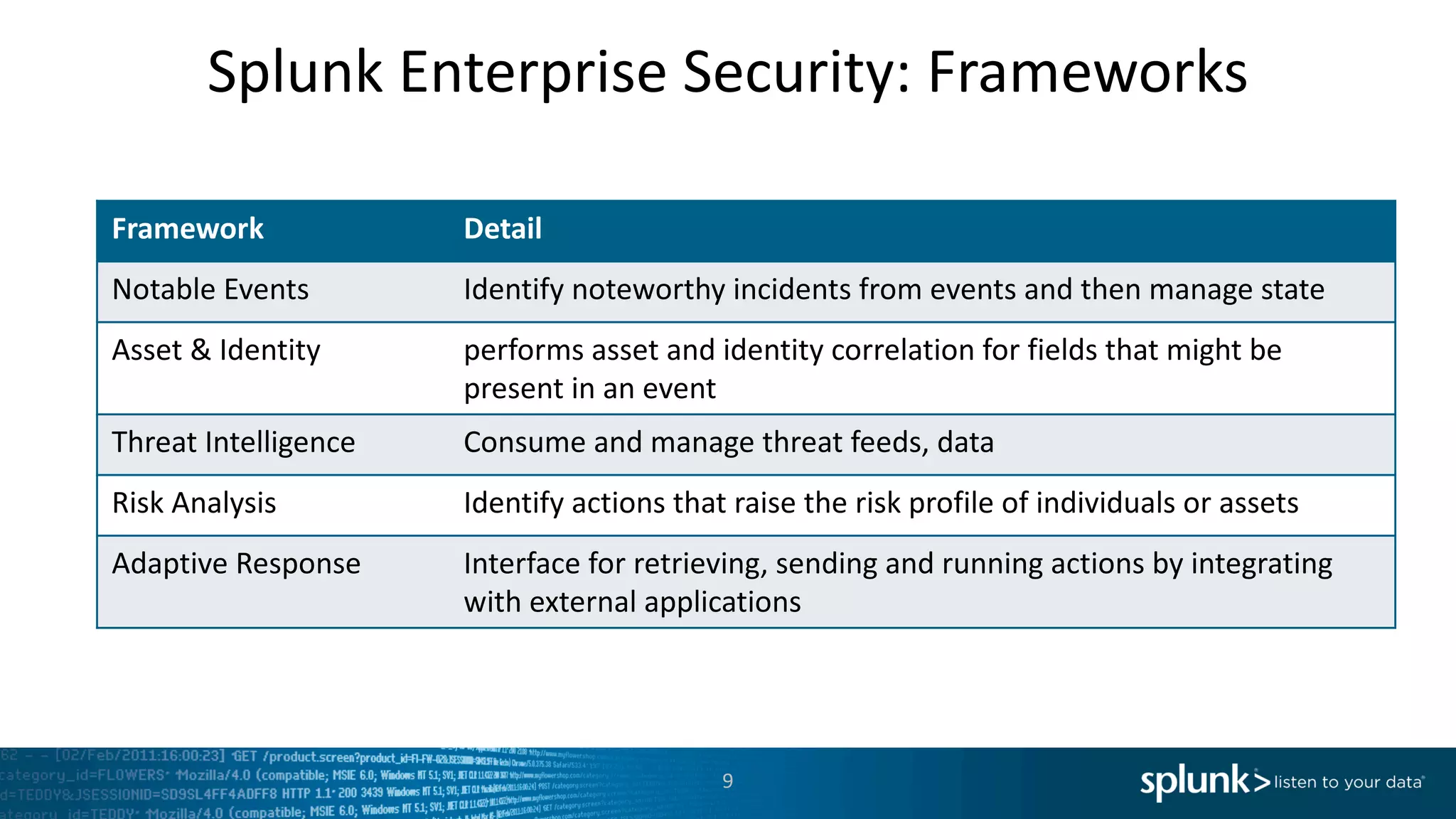
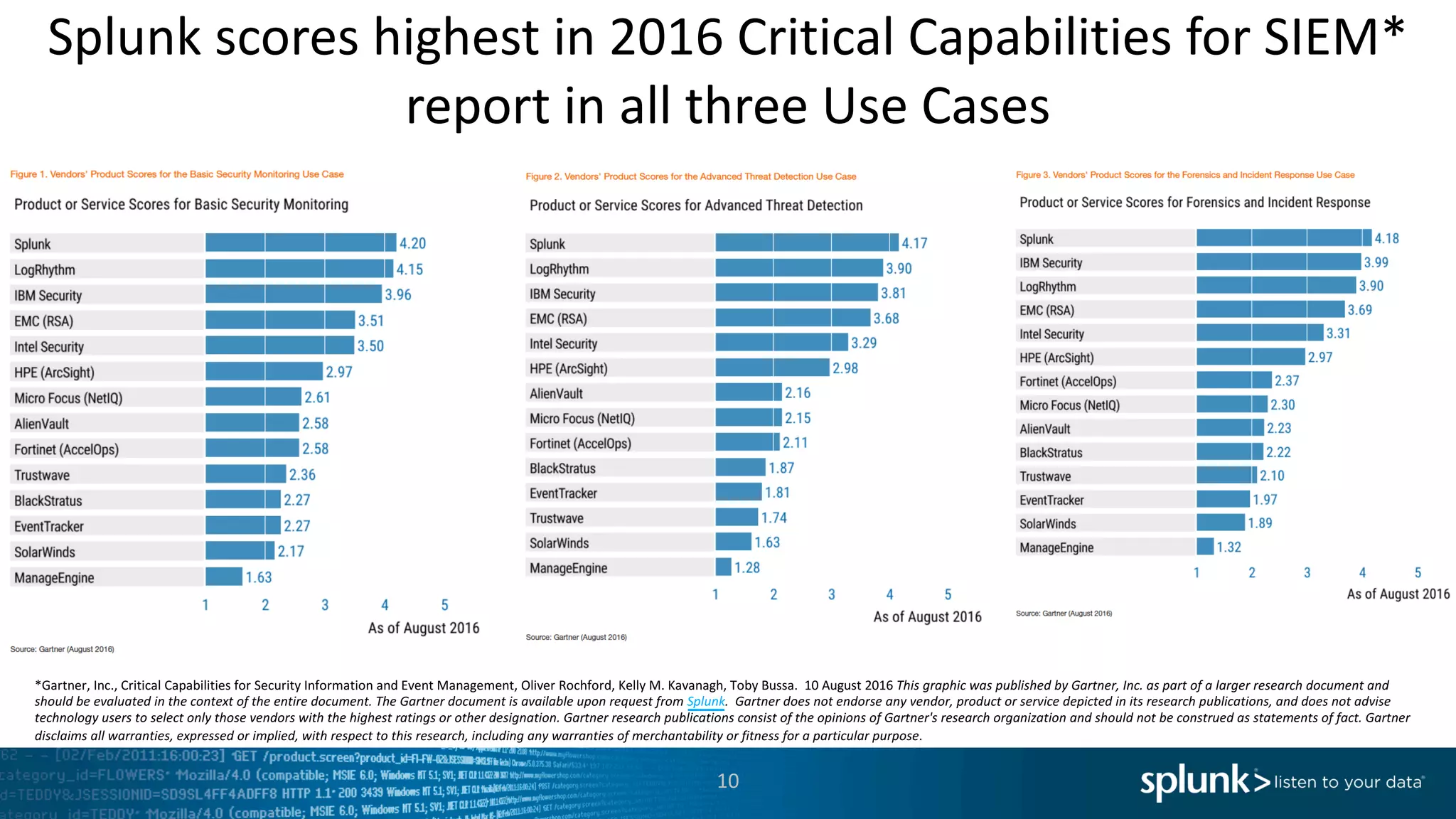
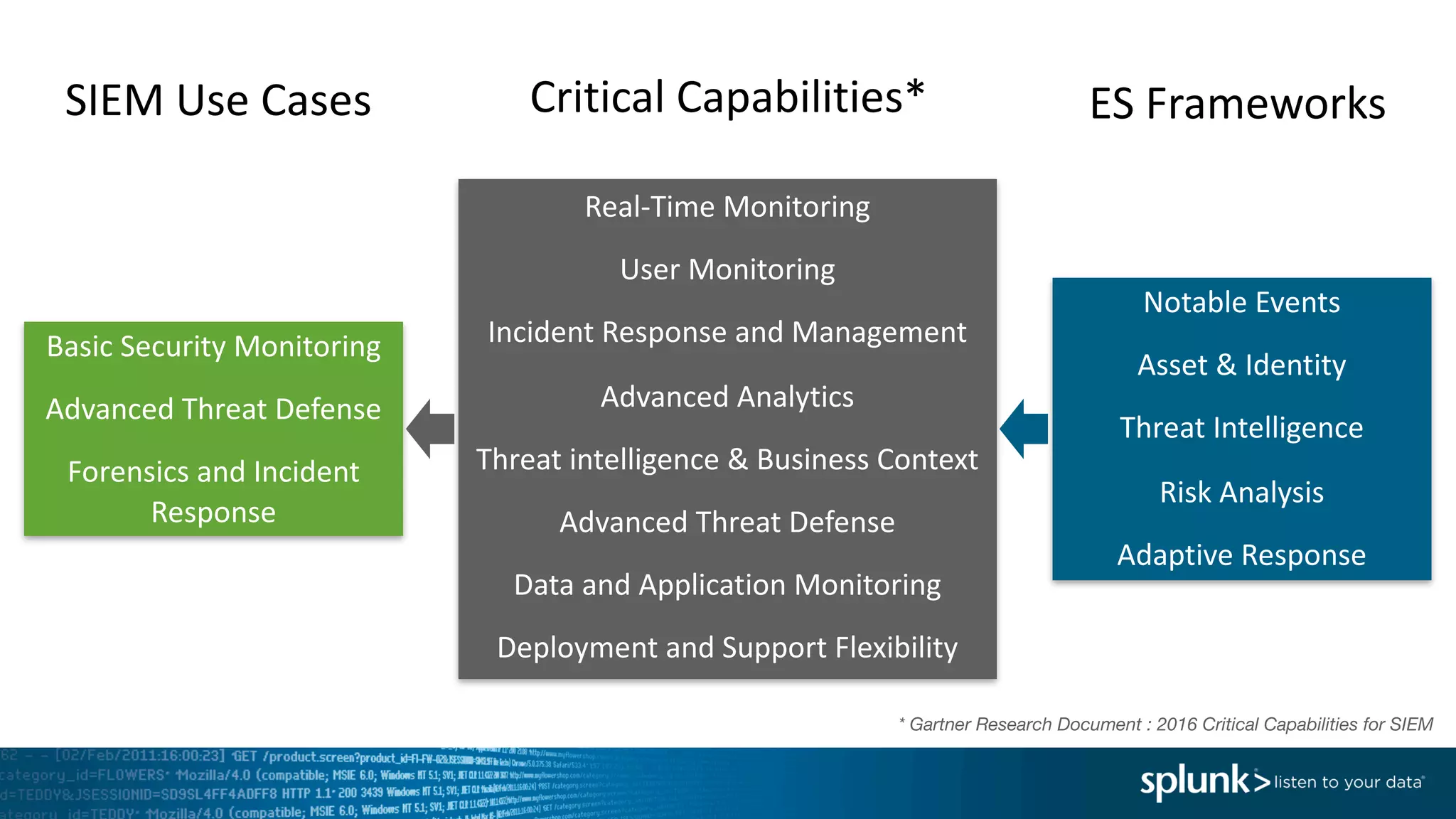
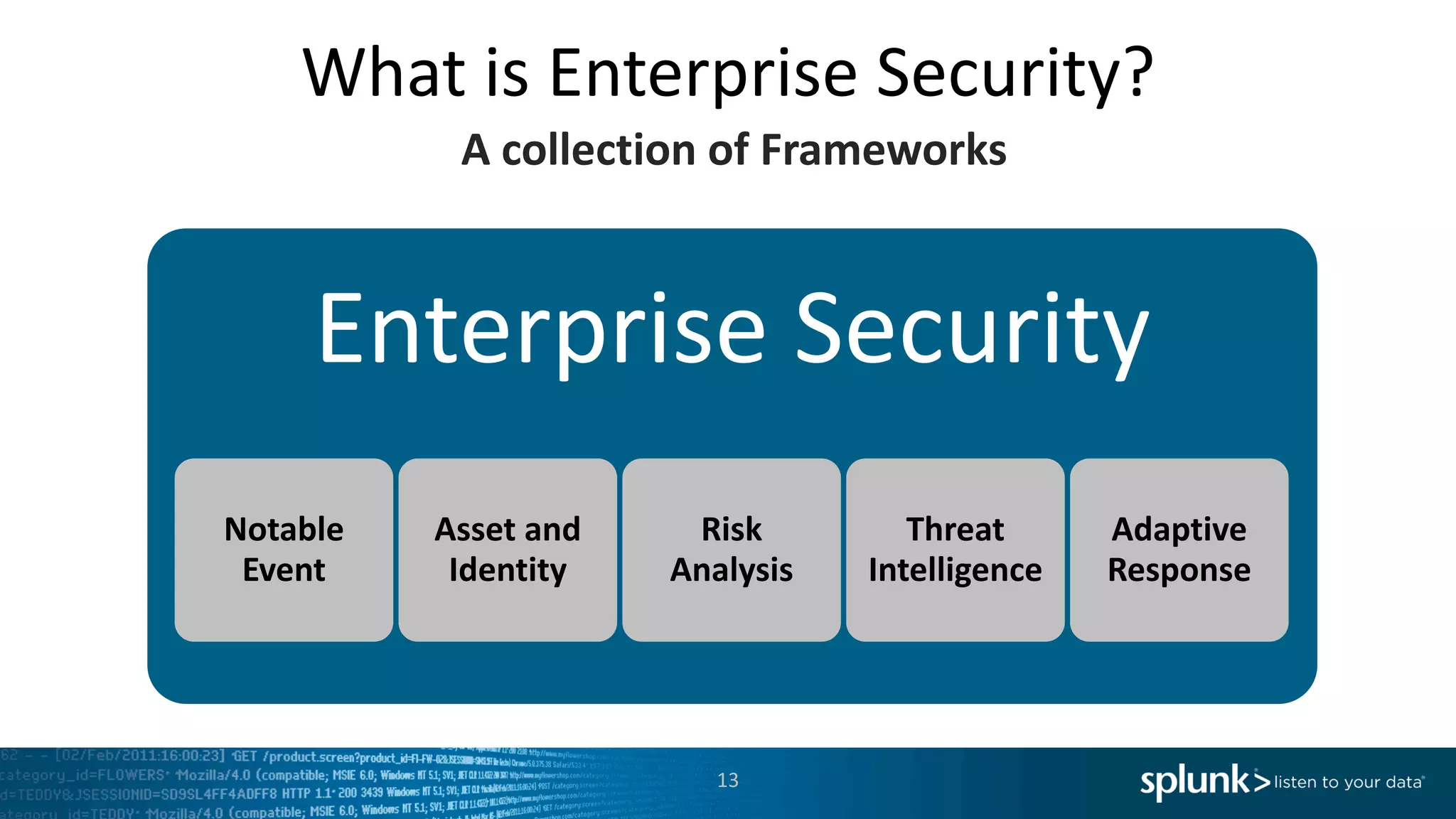
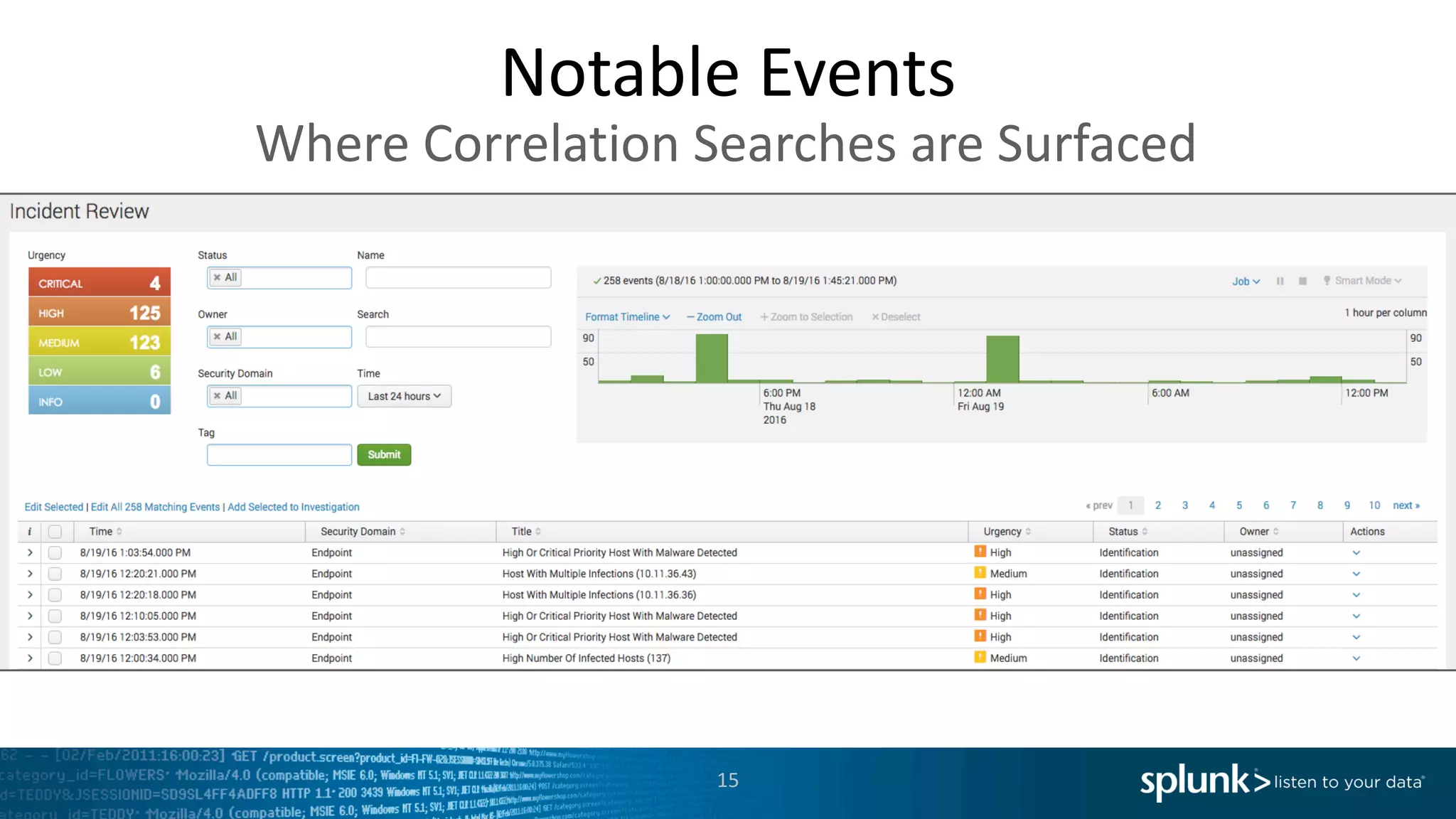
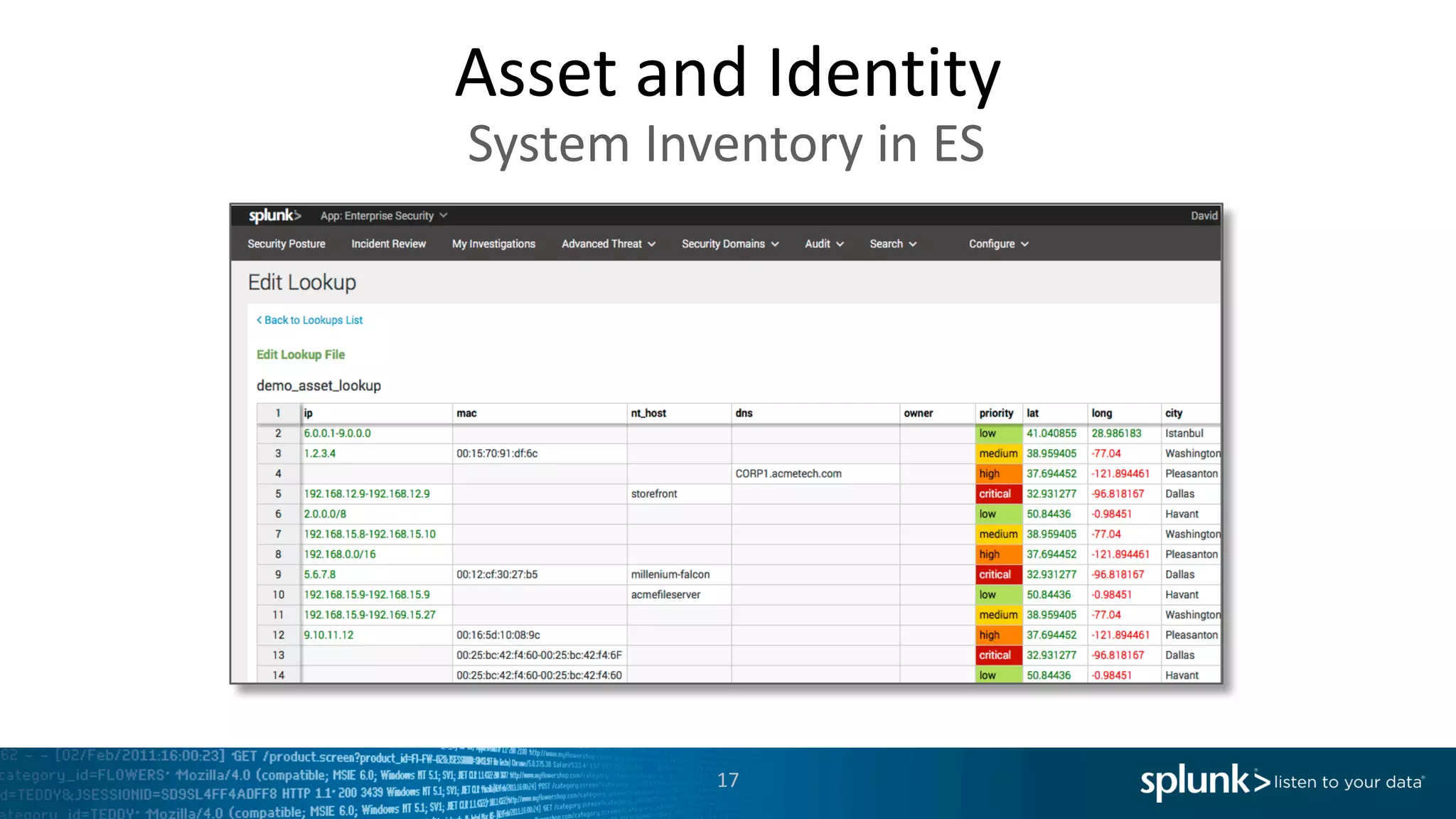
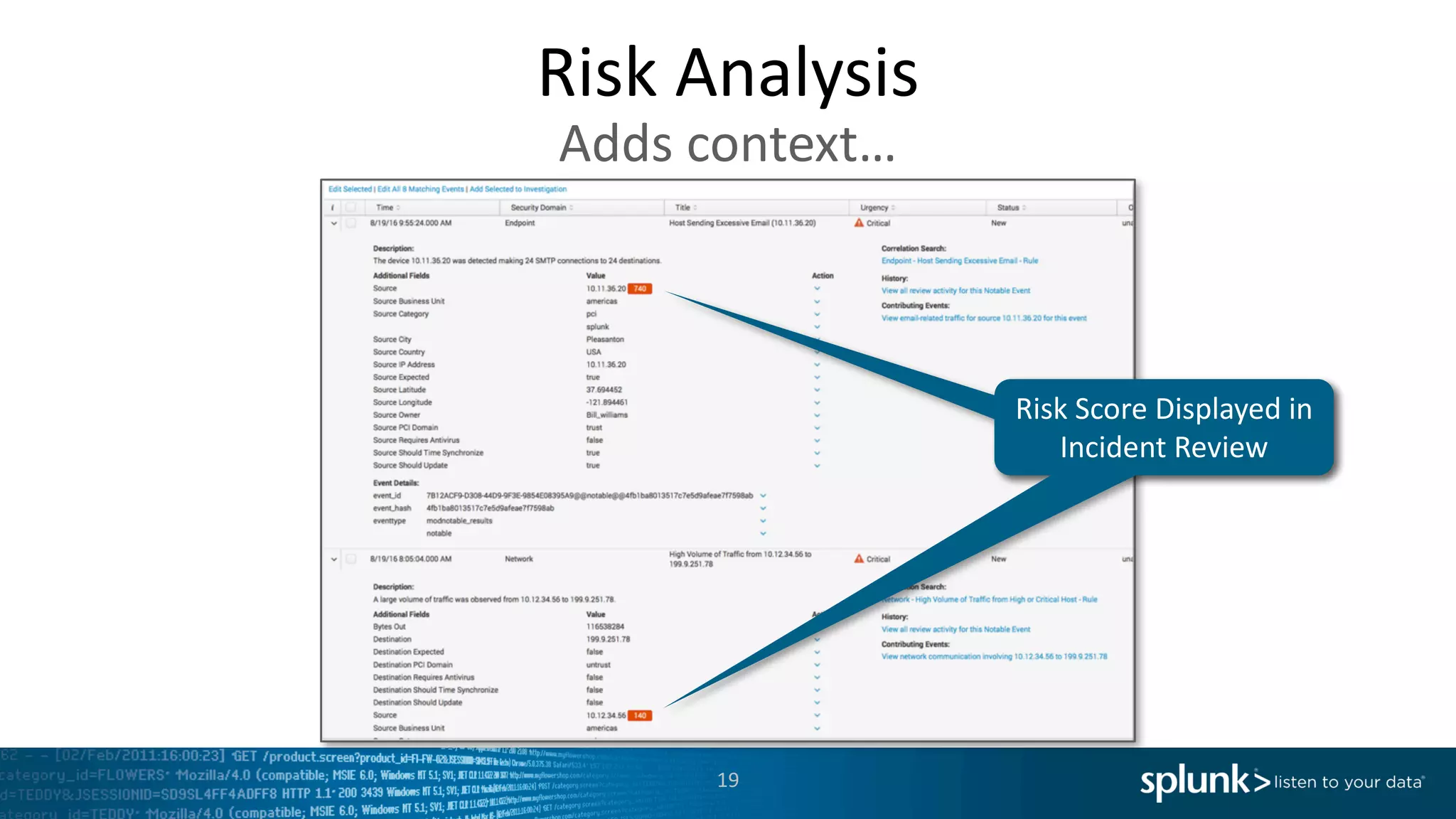
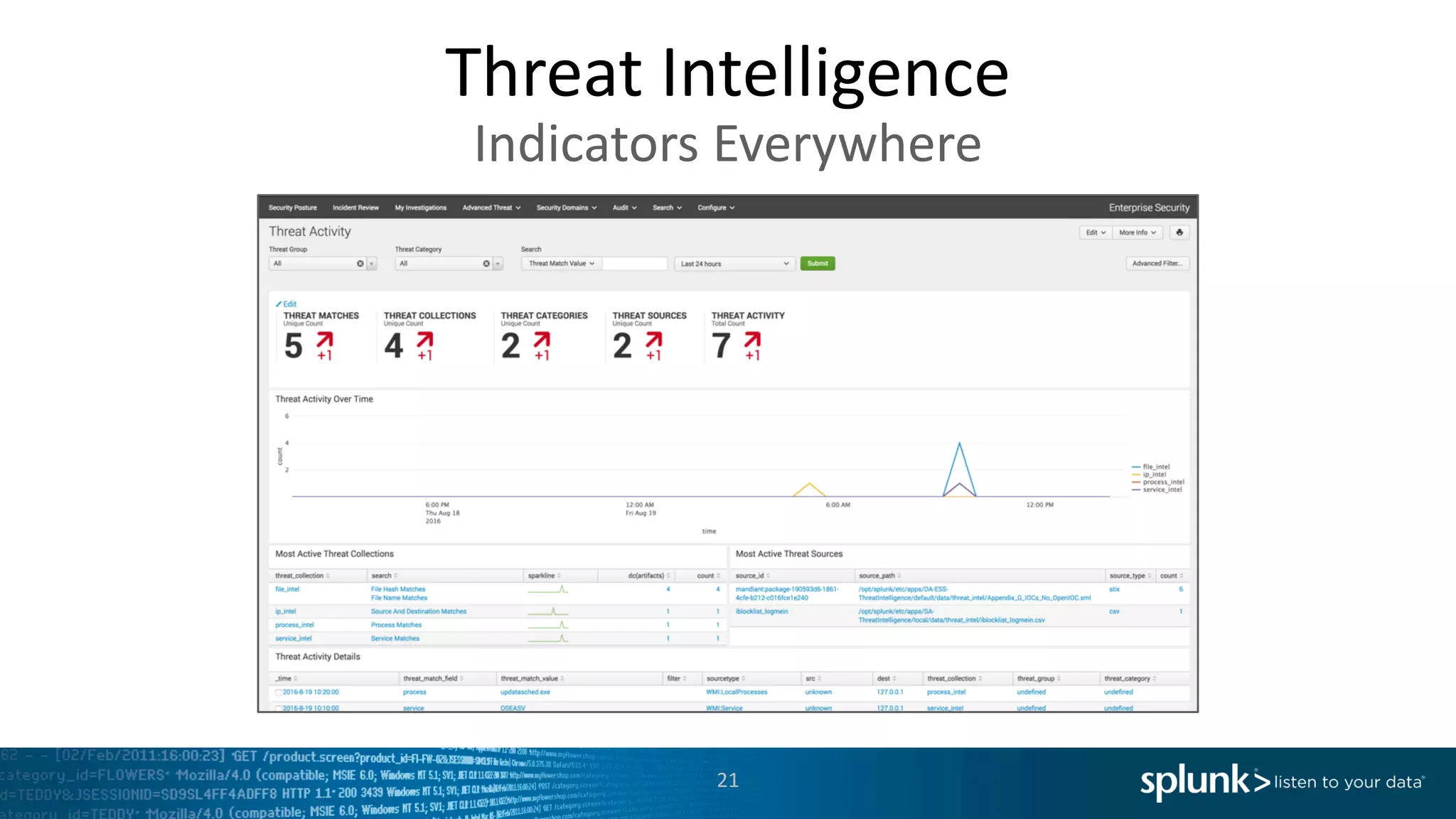
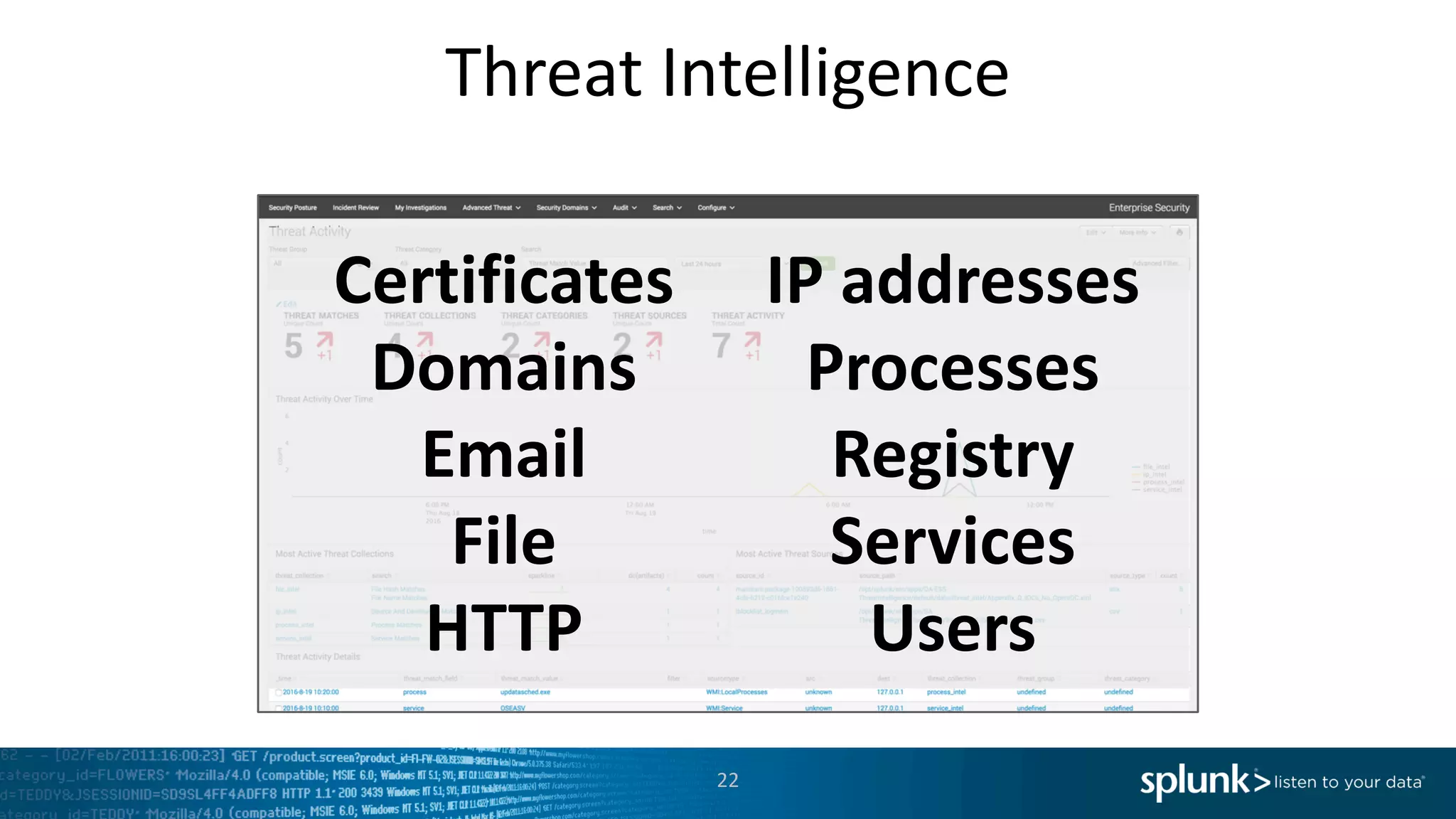
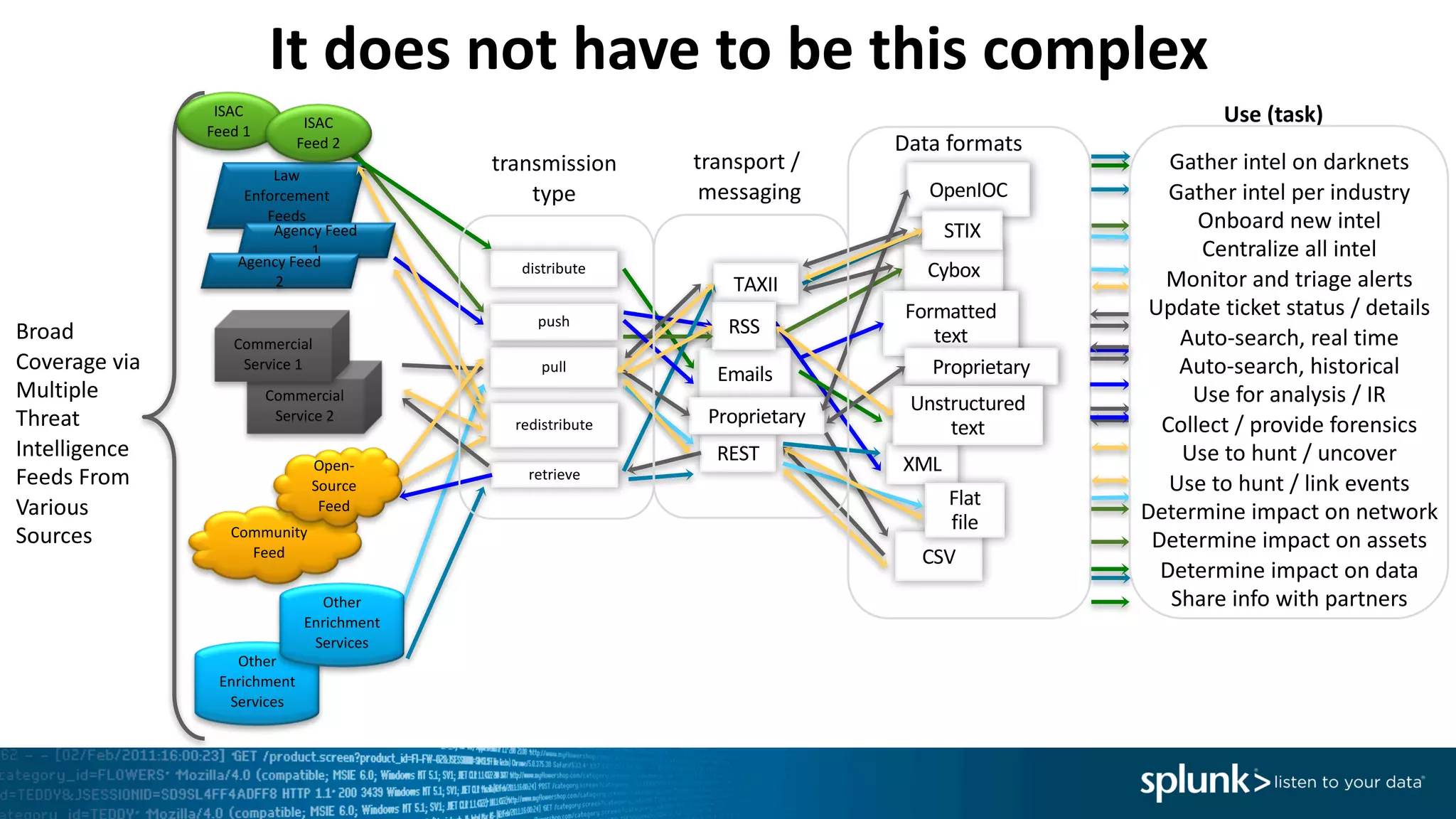
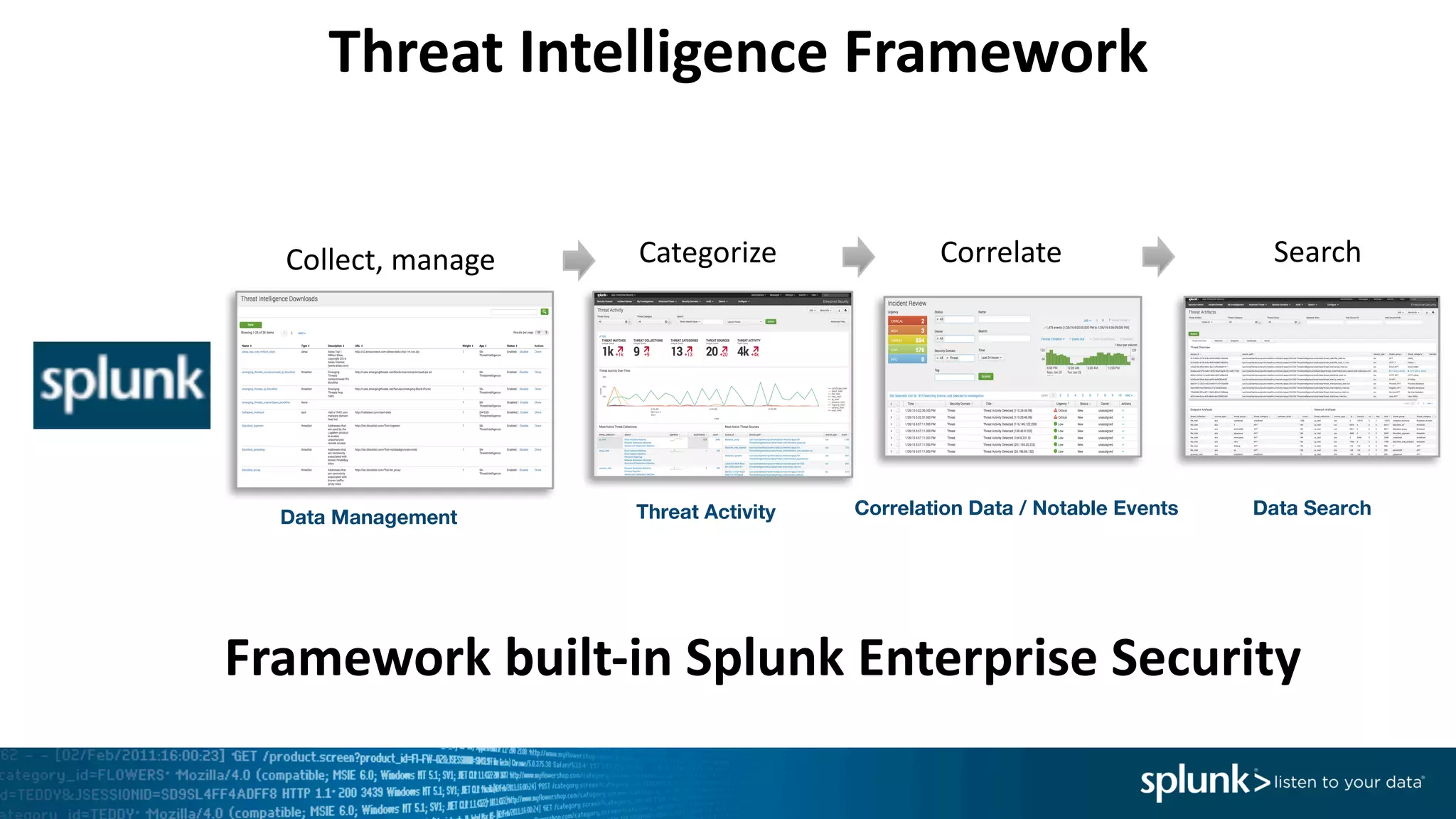
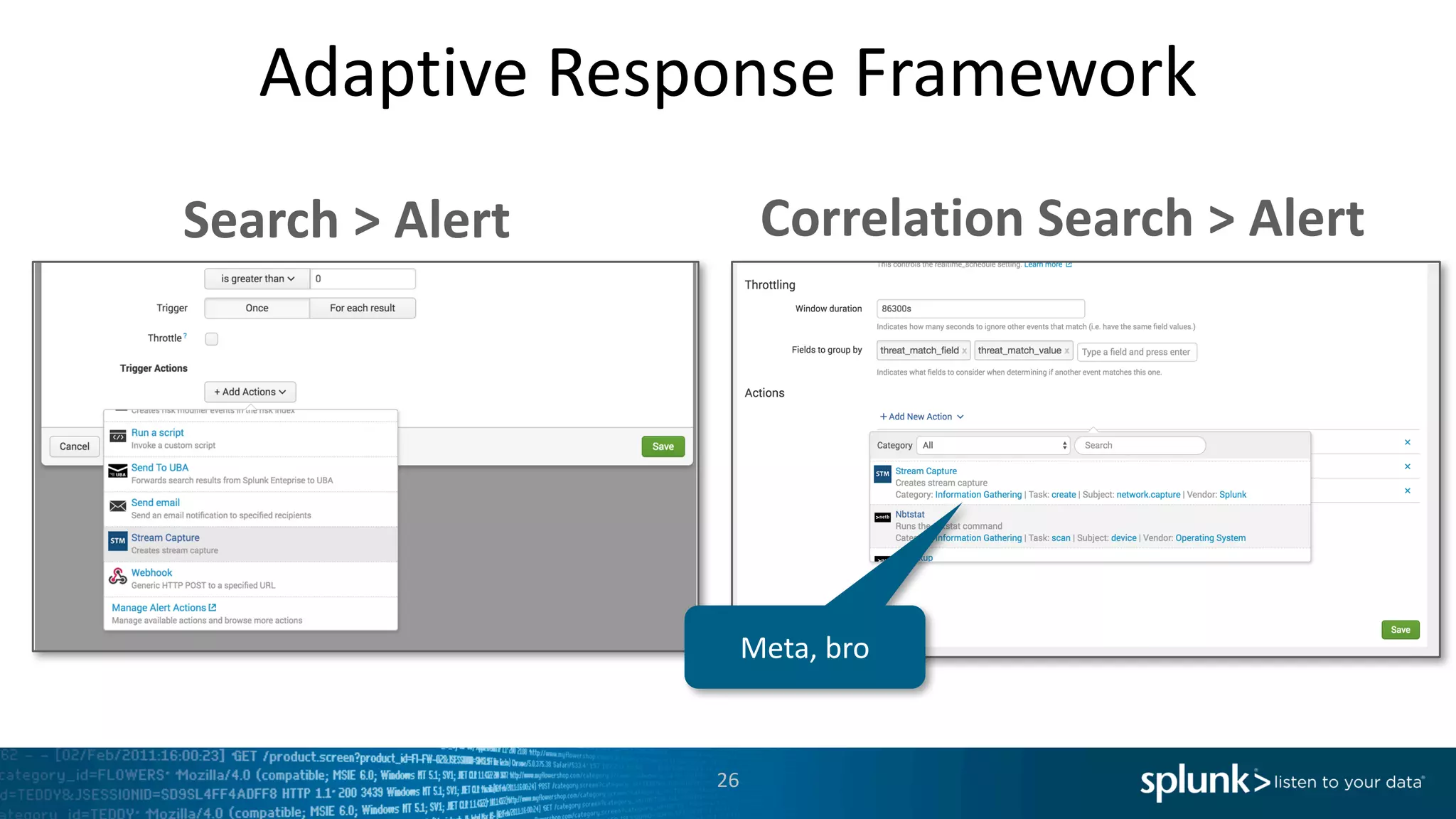
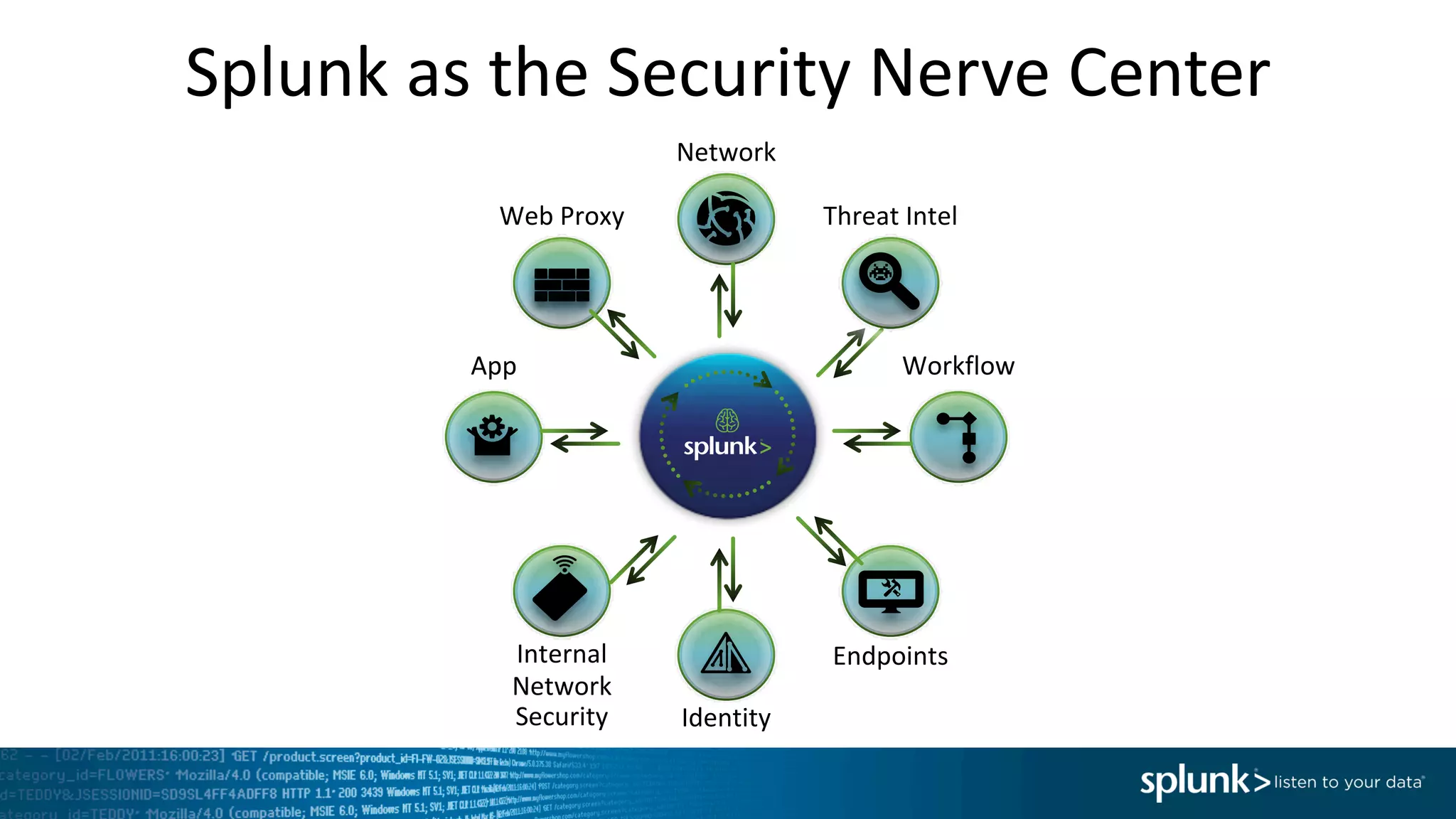
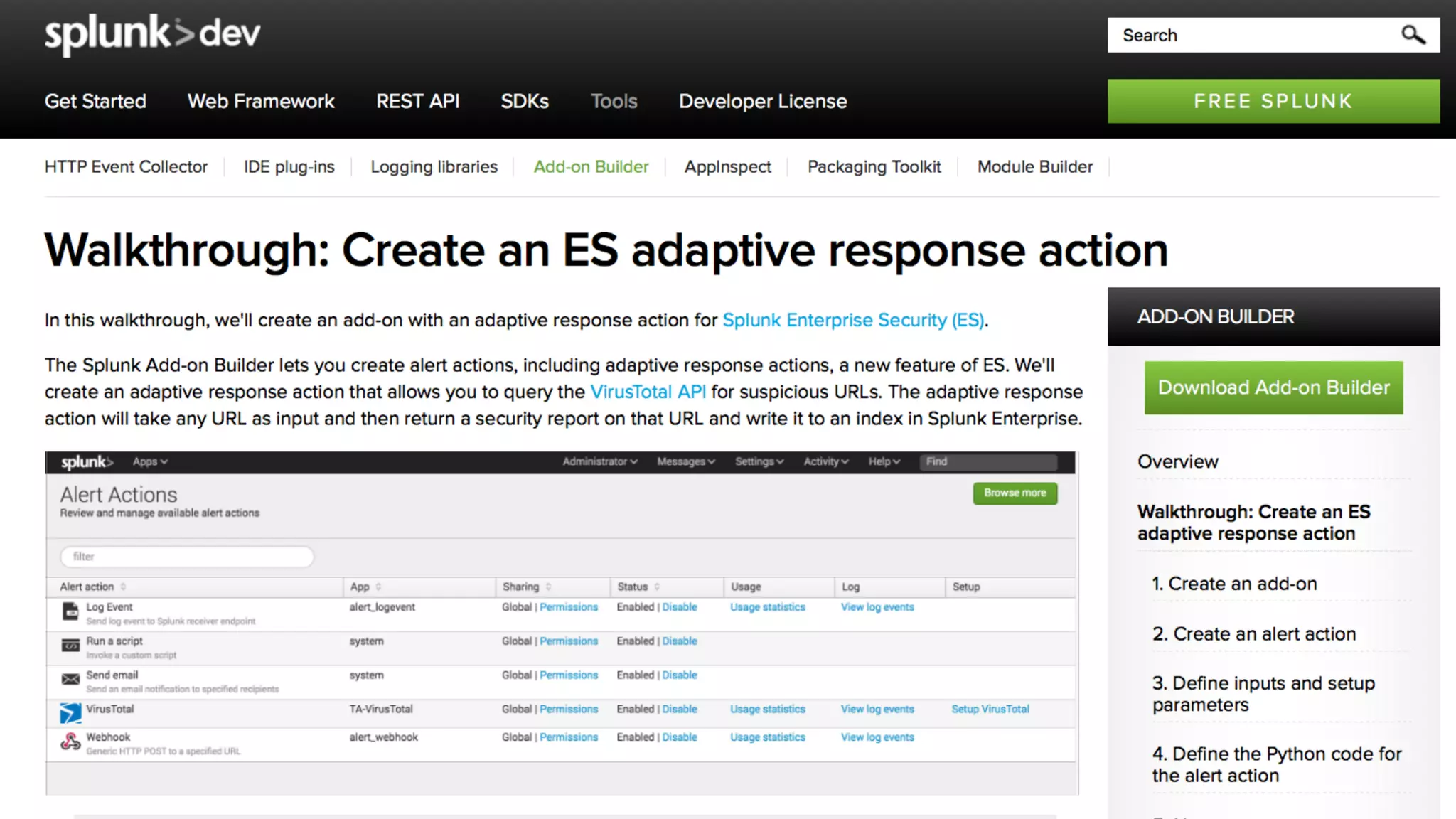
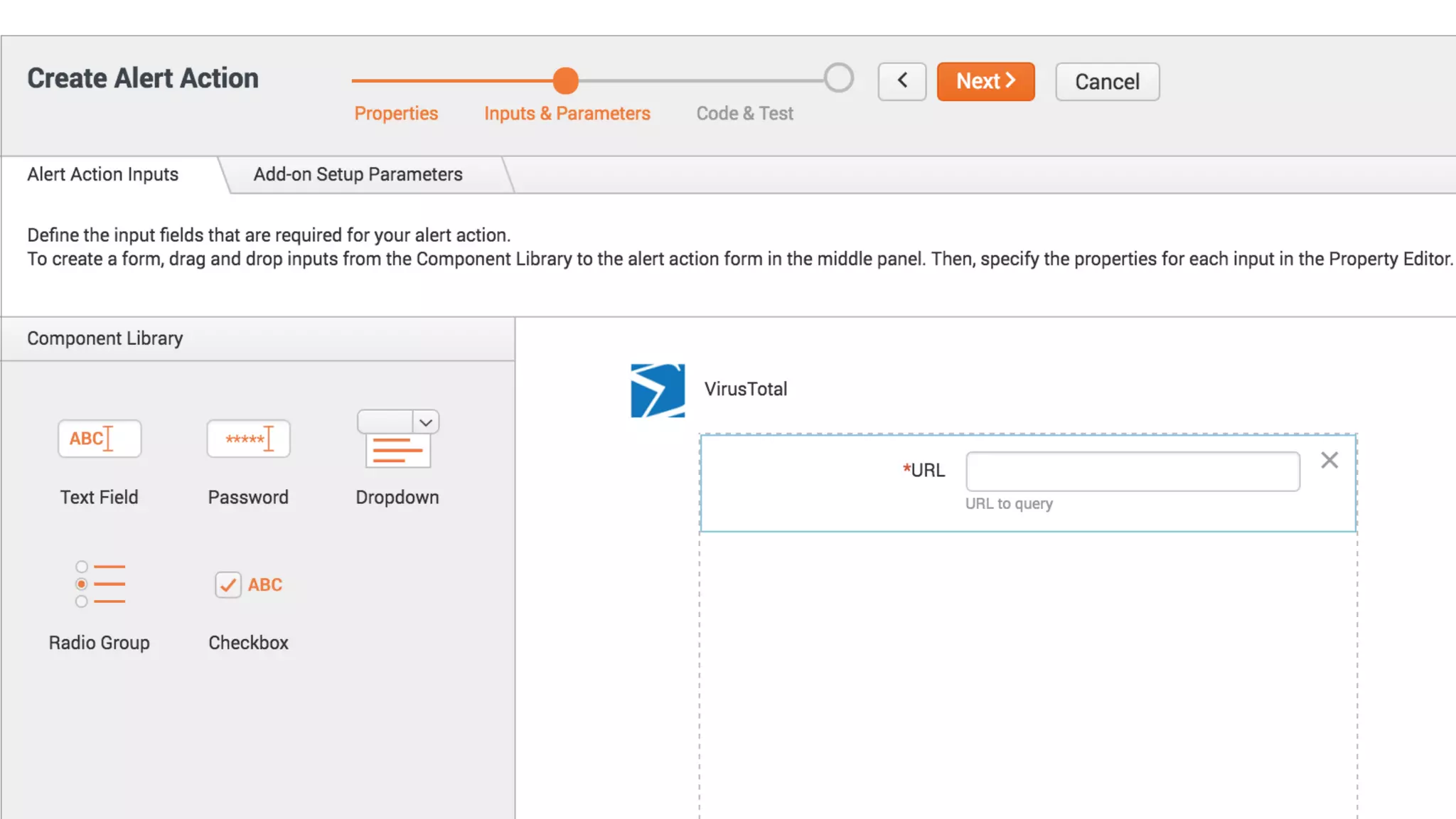
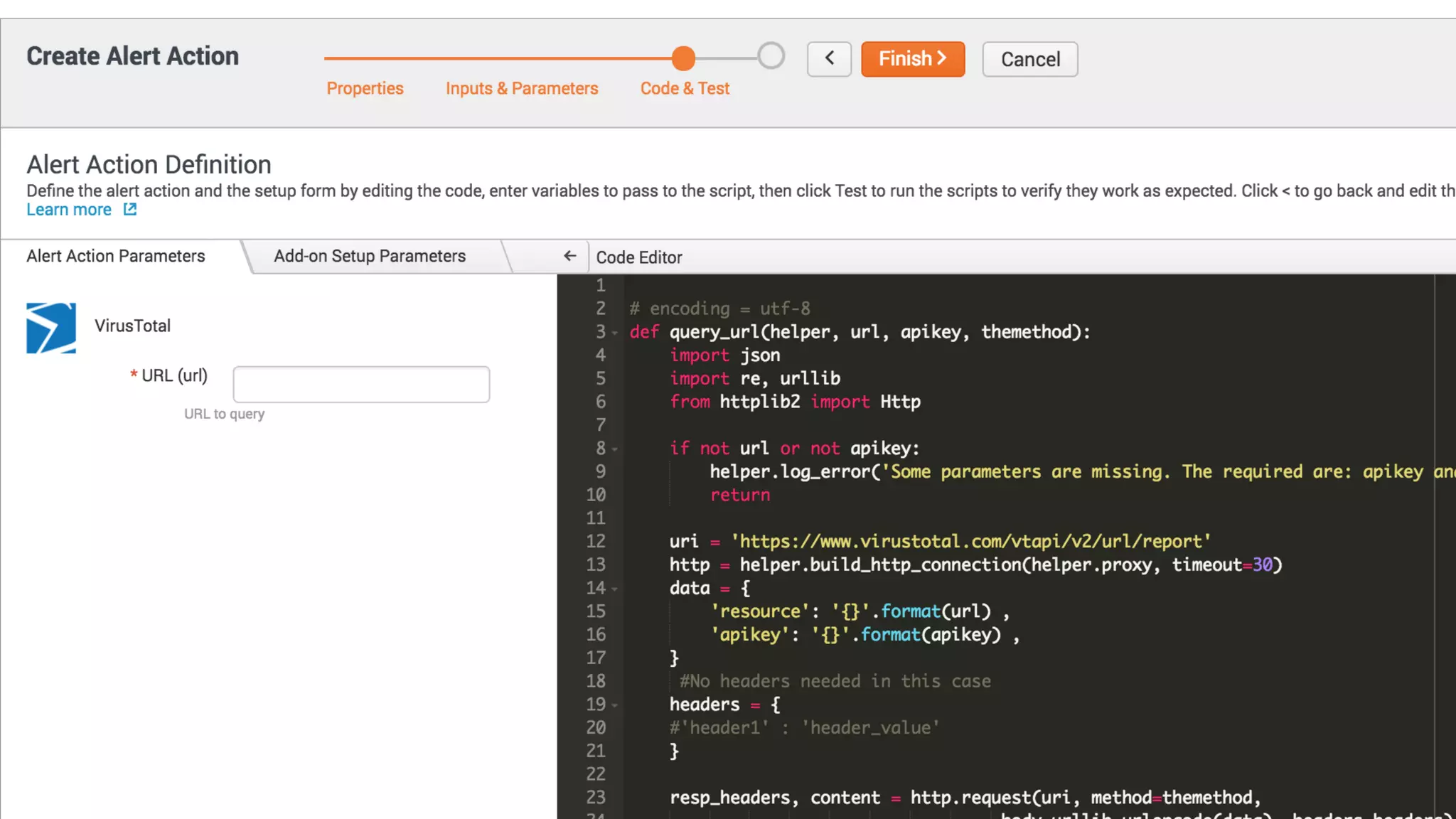
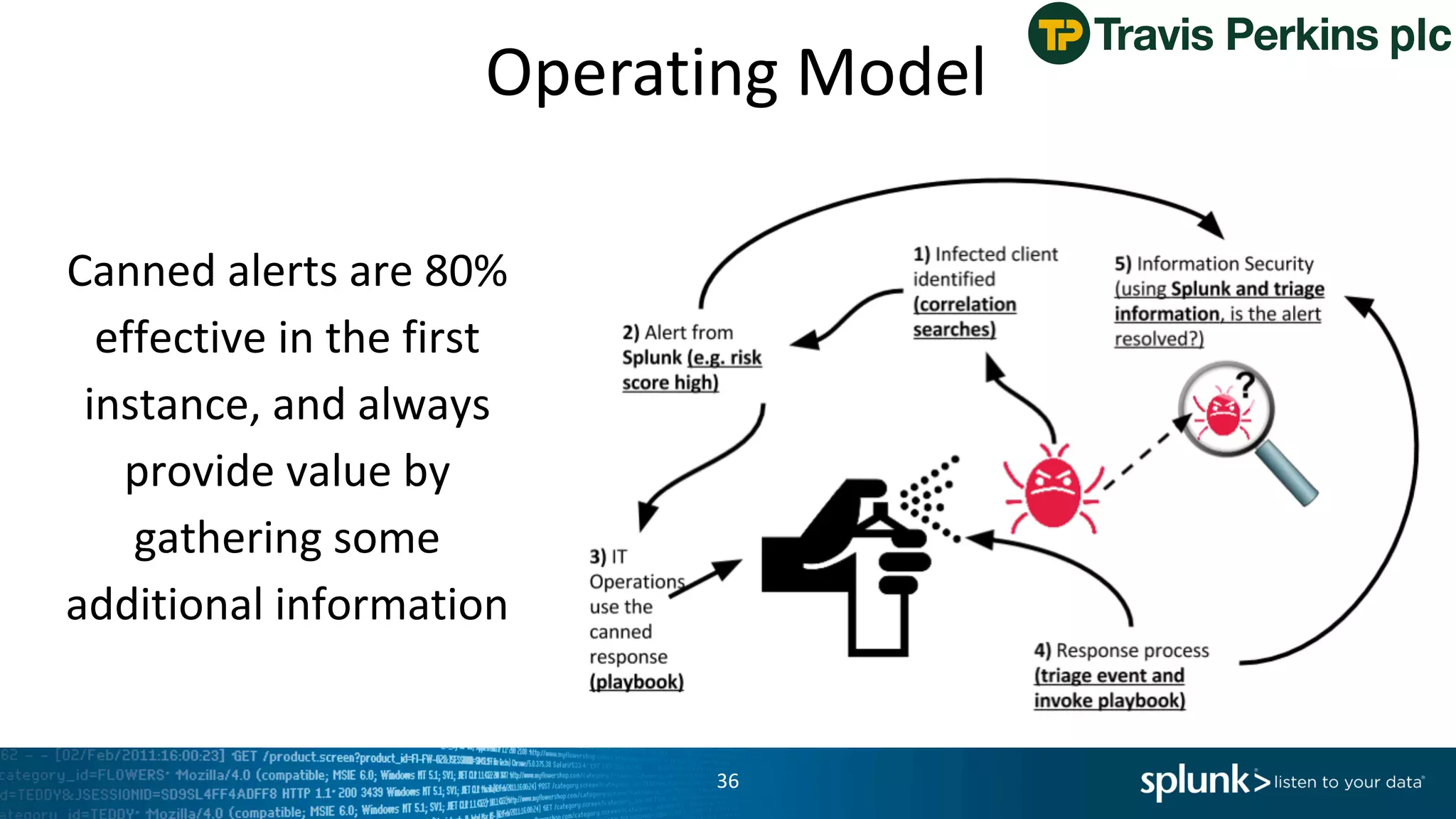
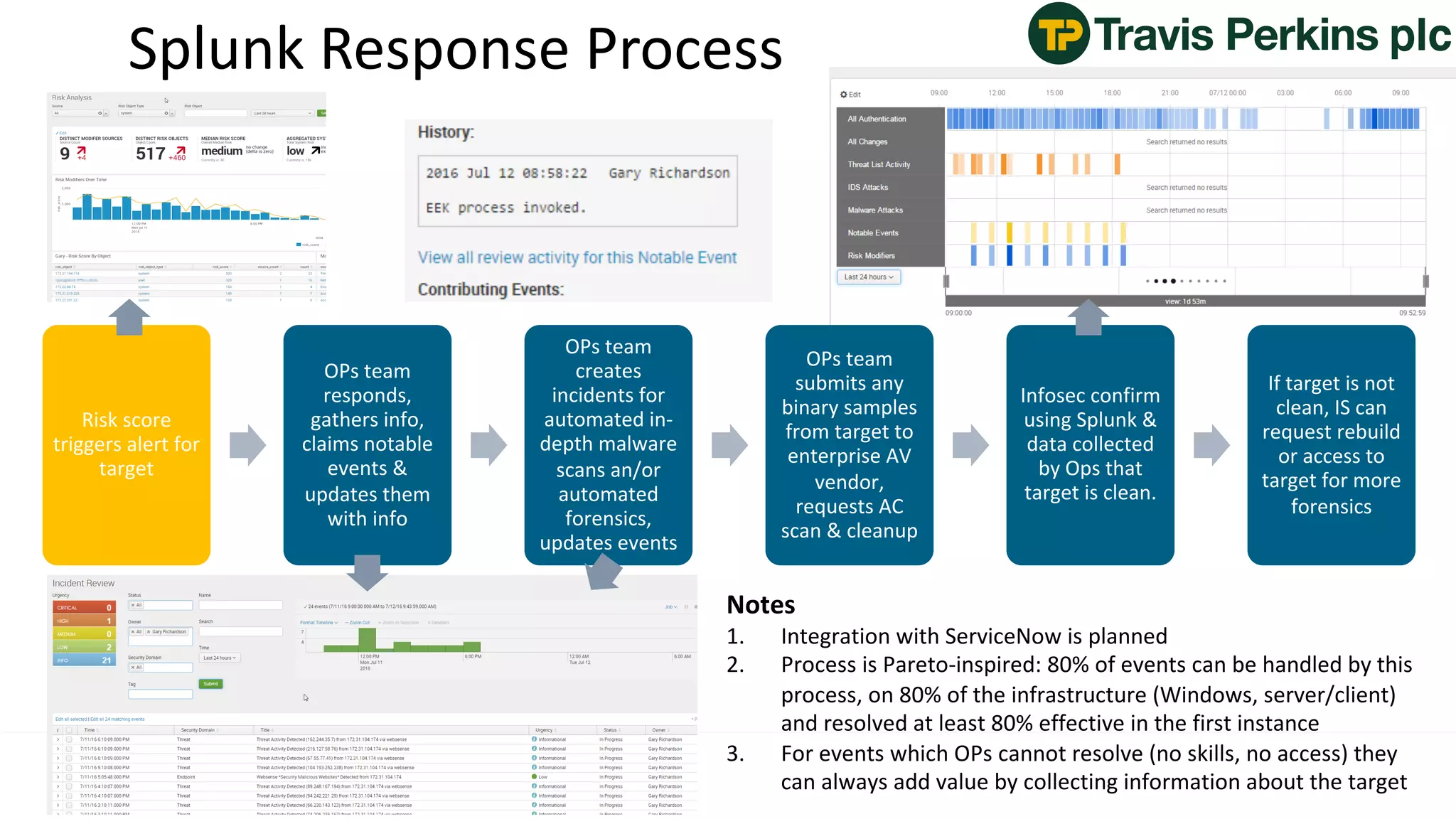
The document is a presentation by Splunk Inc. detailing their enterprise security solutions, including forward-looking statements about the company's performance and product direction. It highlights their accolades, customer base, and various security frameworks and capabilities related to threat detection, incident response, and risk analysis. Splunk emphasizes their analytics-driven approach to security and integration with external applications to enhance their services.