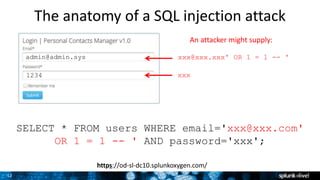
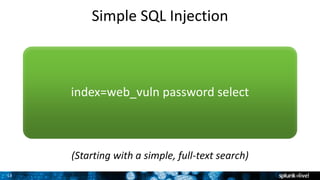
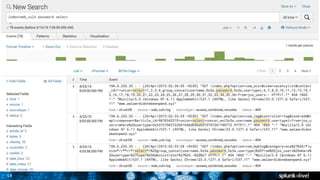
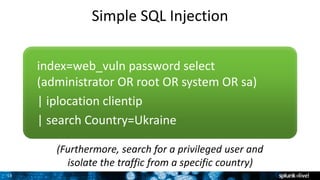
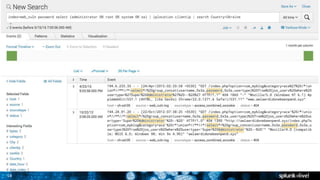
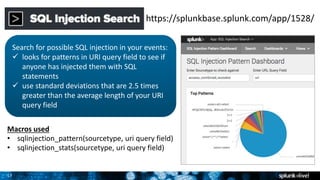
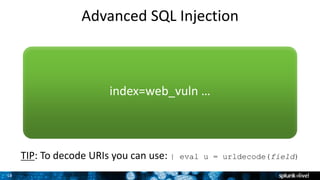
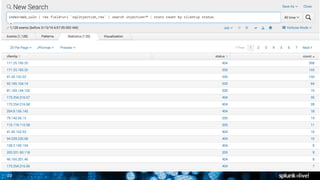
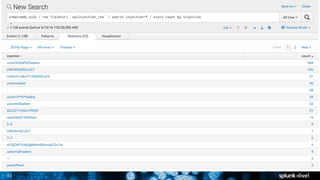
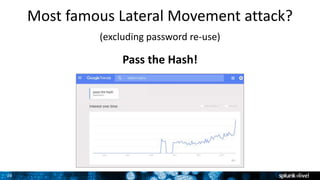
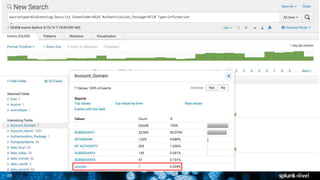
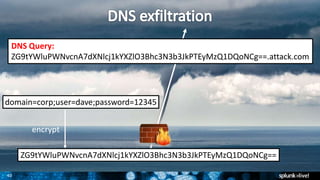
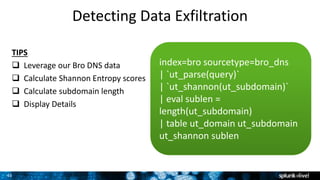
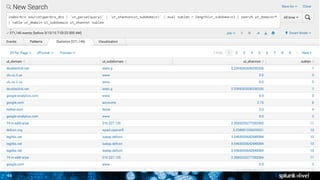
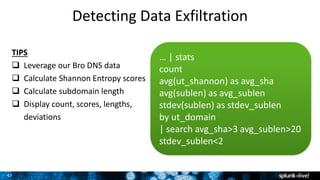
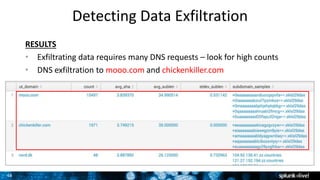
The document is a presentation on leveraging Splunk for information security, covering topics such as web attacks, lateral movement, and DNS exfiltration. It discusses various attack methodologies like SQL injection and pass-the-hash and emphasizes the importance of detecting these threats using Splunk's capabilities. The conclusion highlights the need for comprehensive detection across all phases of modern attacks and invites participants to engage further at the Splunk conference.







![9
OWASP 2013 Top 10
[10] Unvalidated redirects and forwards
[9] Using components with known vulnerabilities
[8] Cross-site request forgery
[7] Missing function level access control
[6] Sensitive data exposure
[5] Security misconfiguration
[4] Insecure direct object reference
[3] Cross-site scripting (XSS)
[2] Broken authentication and session management](https://image.slidesharecdn.com/splunklivedc2016-securityhandson-2-160419151531/85/Splunk-Enterpise-for-Information-Security-Hands-On-9-320.jpg)
![10
[1] Injection
SQL injection
Code injection
OS commanding
LDAP injection
XML injection
XPath injection
SSI injection
IMAP/SMTP injection
Buffer overflow](https://image.slidesharecdn.com/splunklivedc2016-securityhandson-2-160419151531/85/Splunk-Enterpise-for-Information-Security-Hands-On-10-320.jpg)