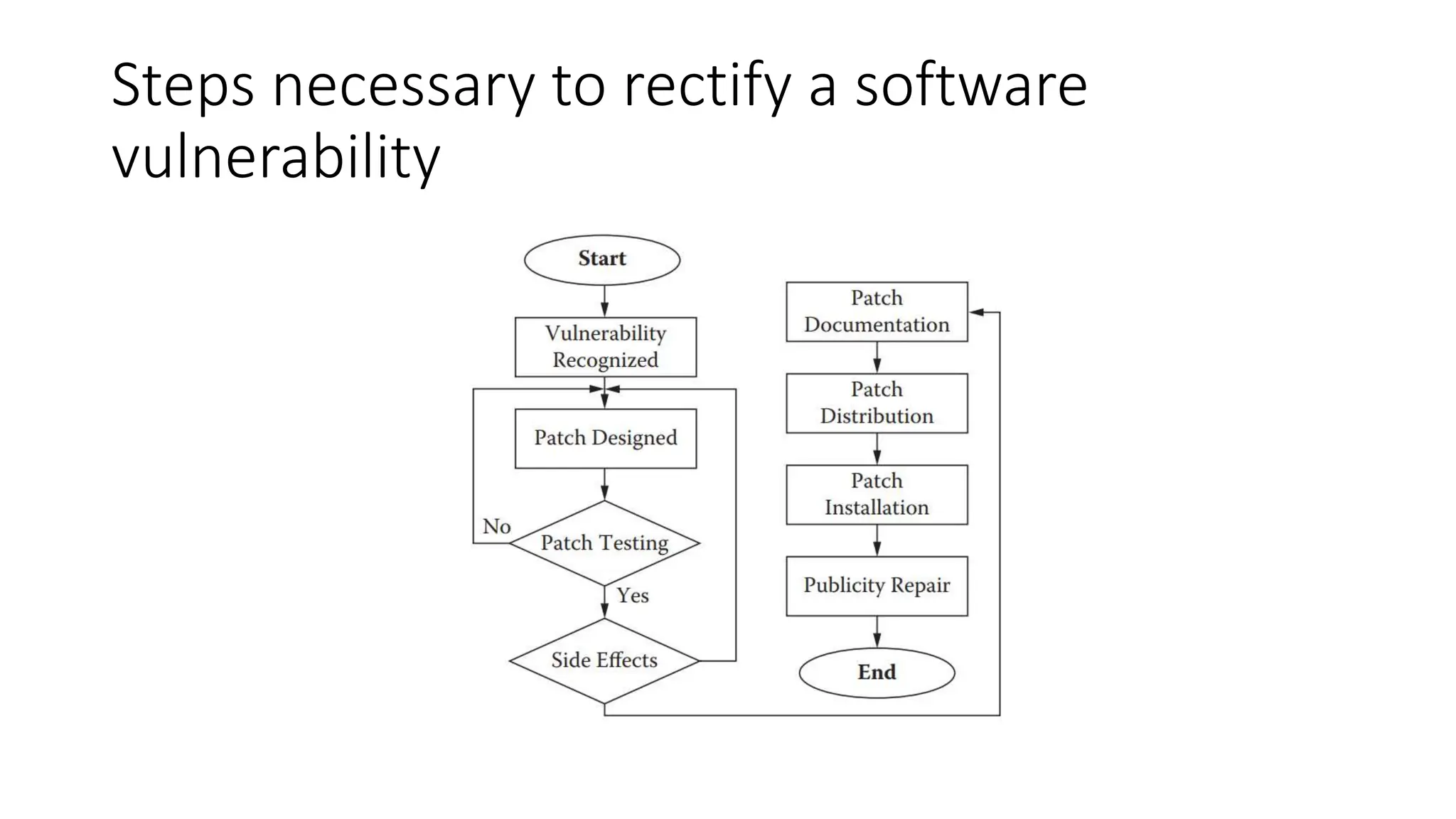
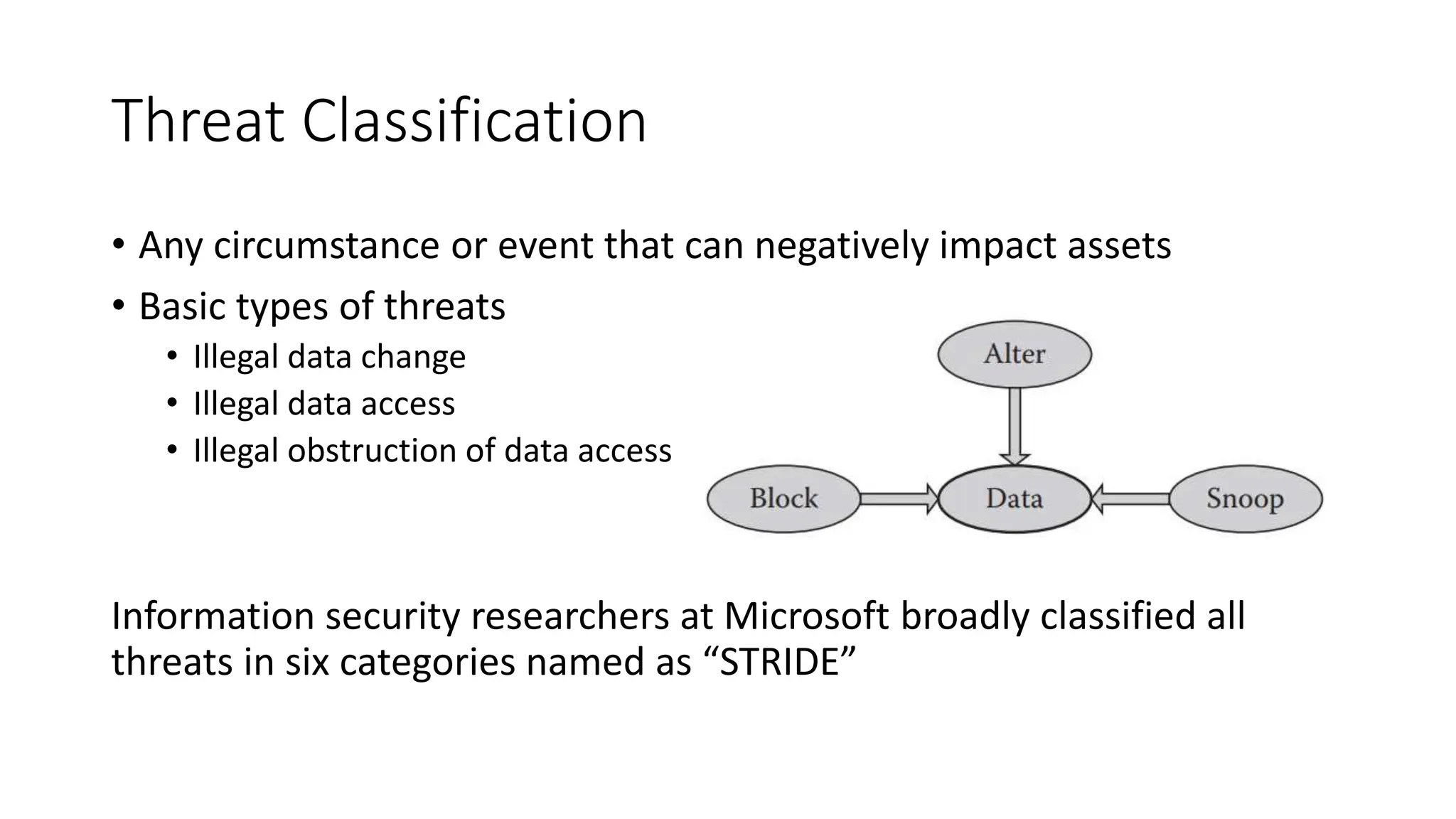
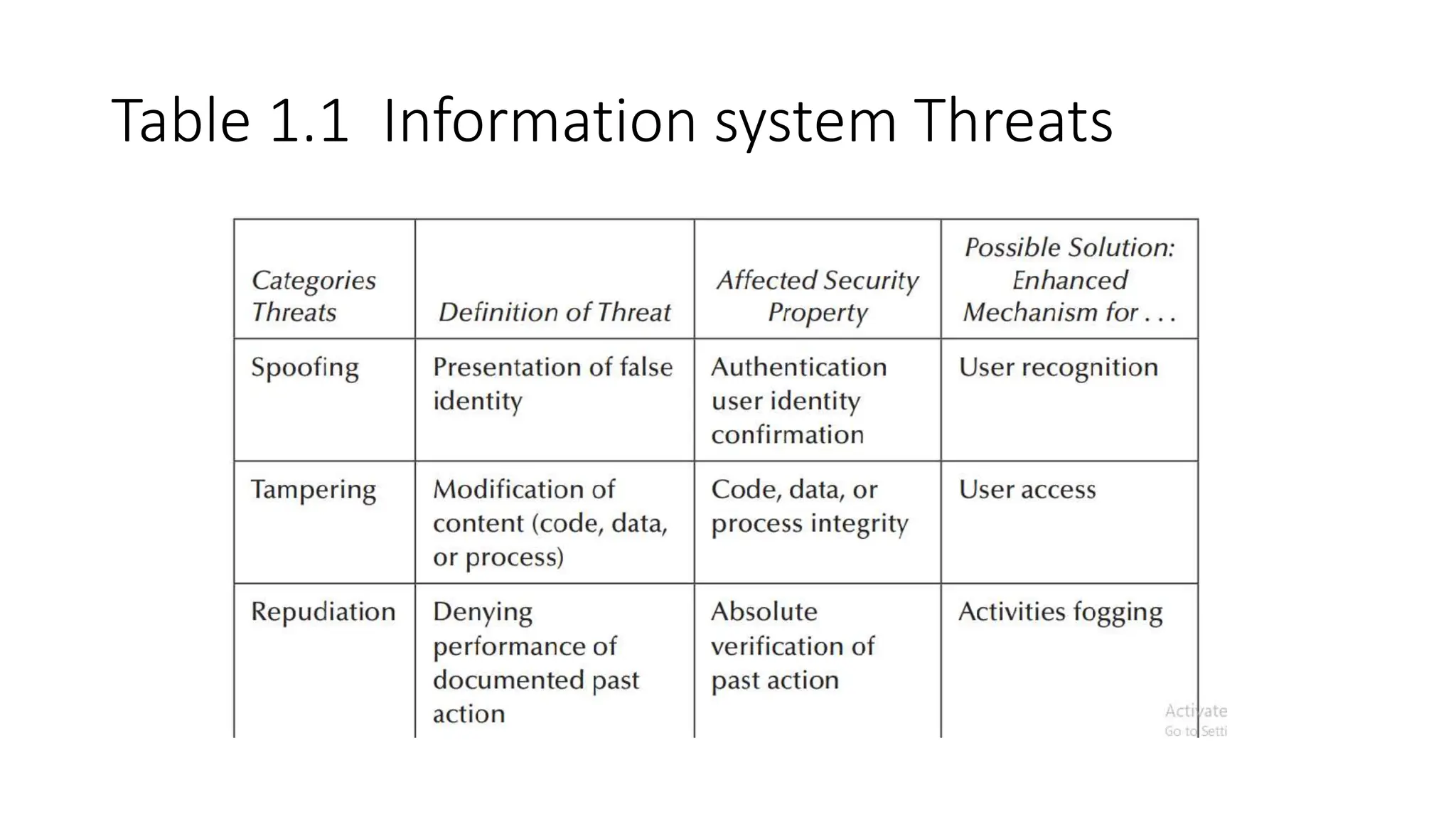
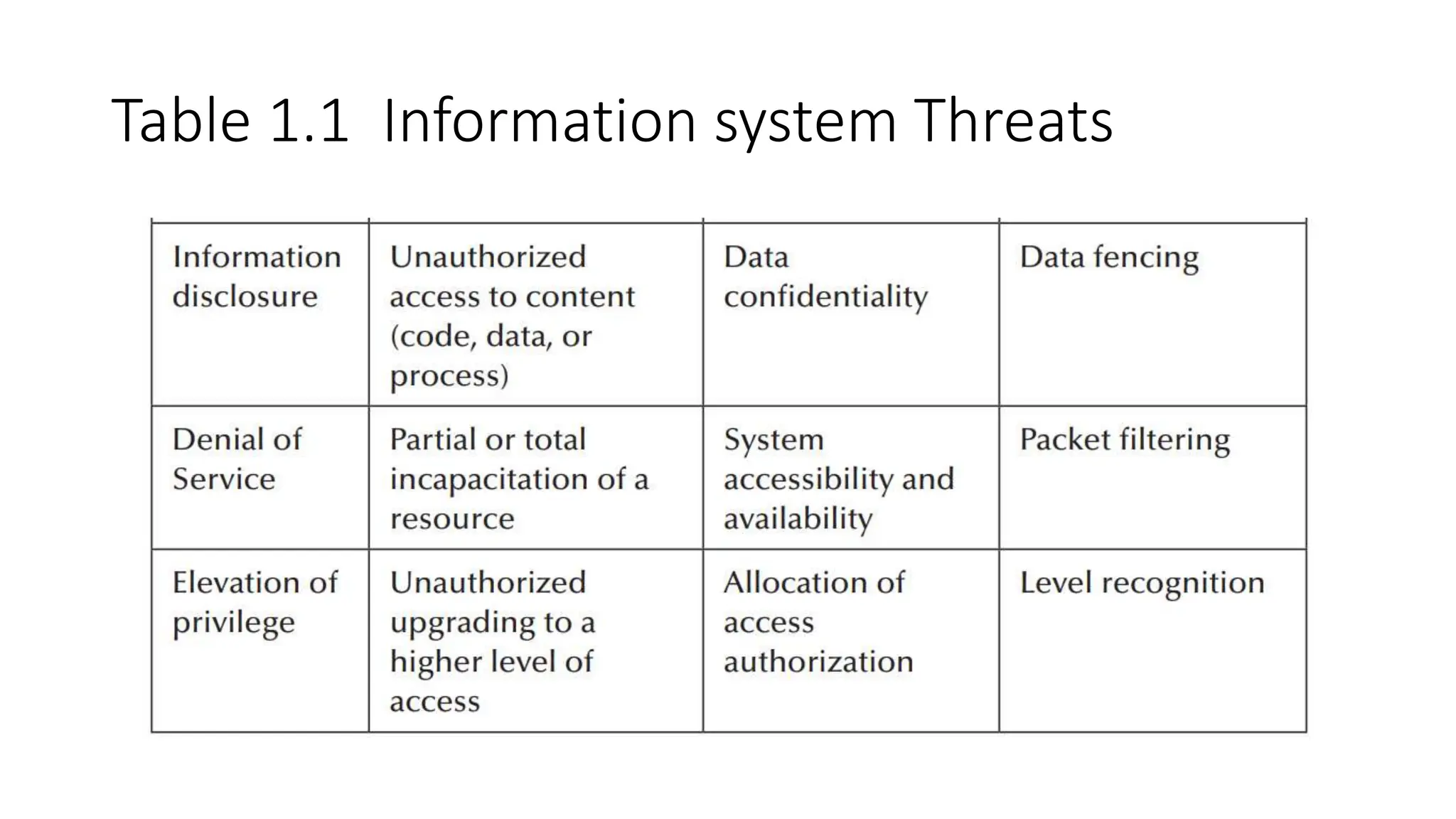
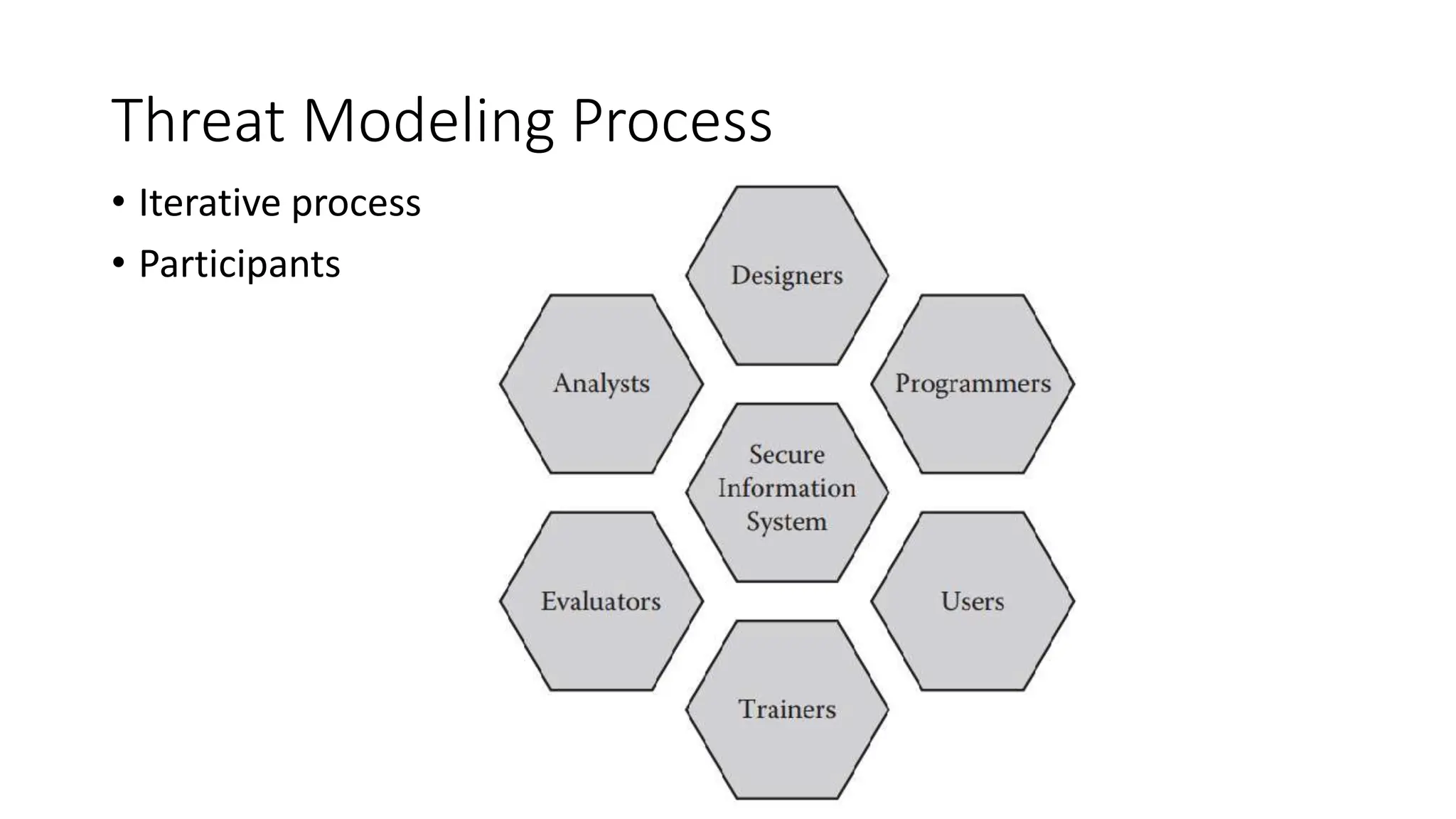
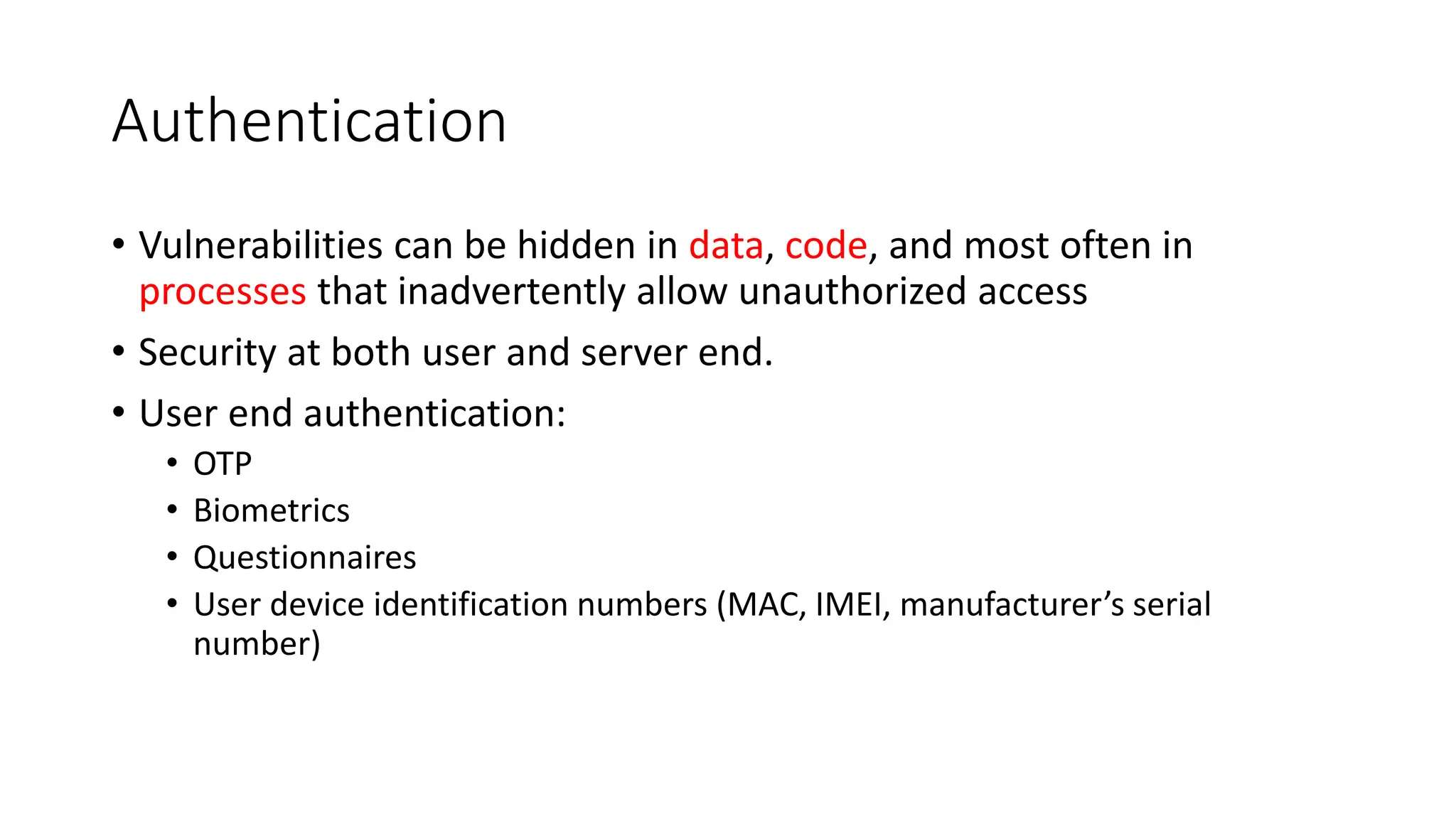
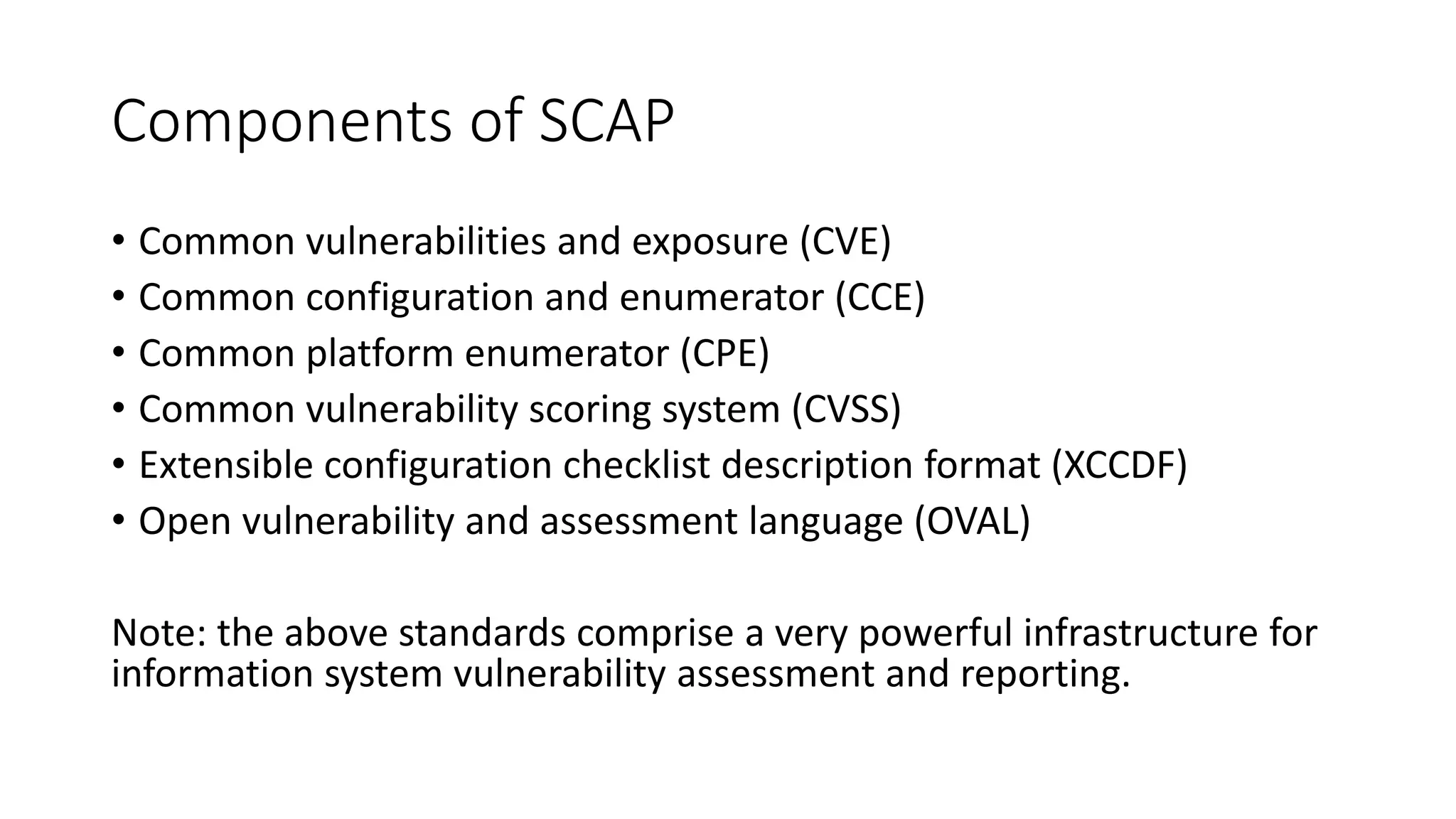
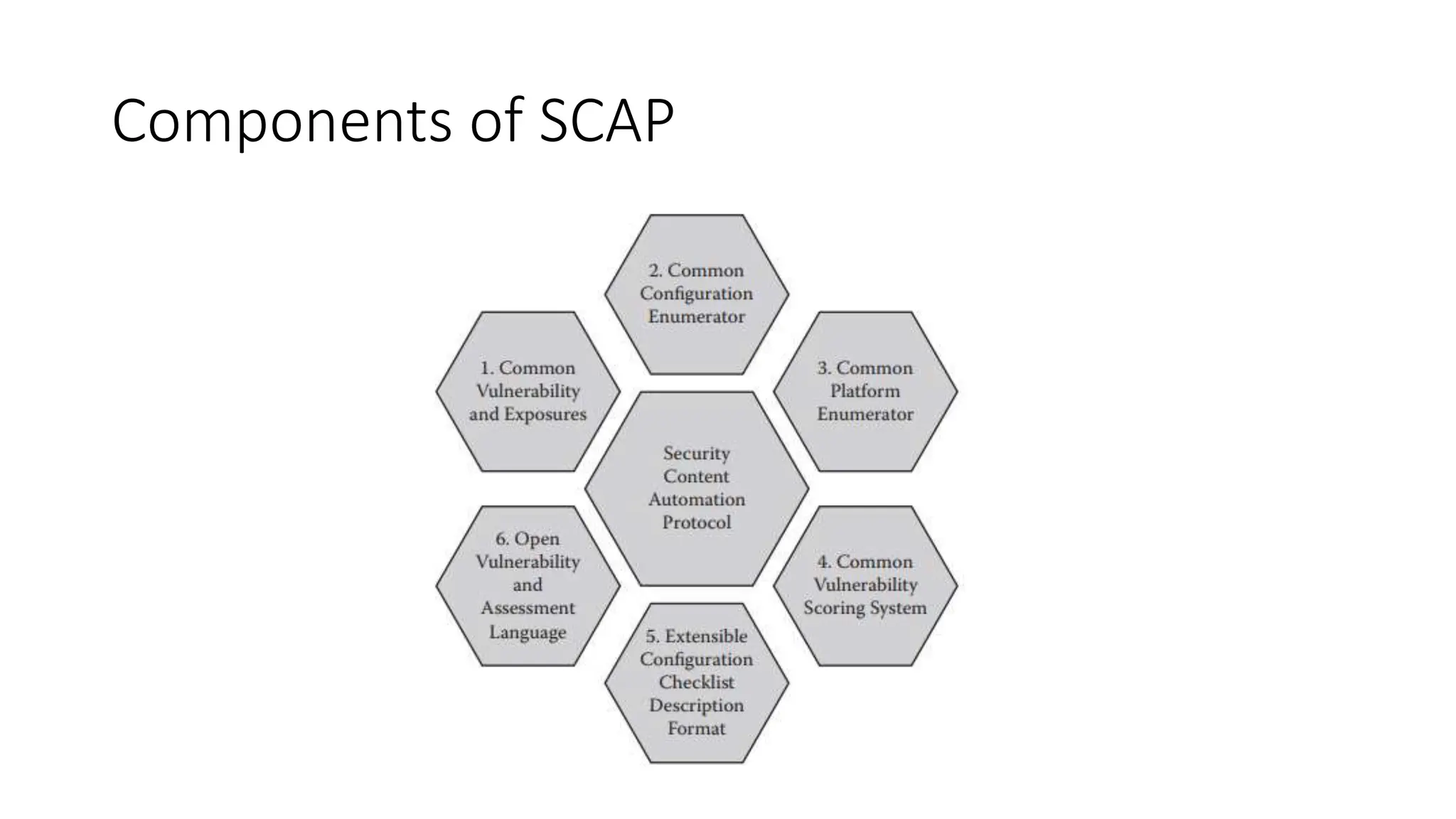
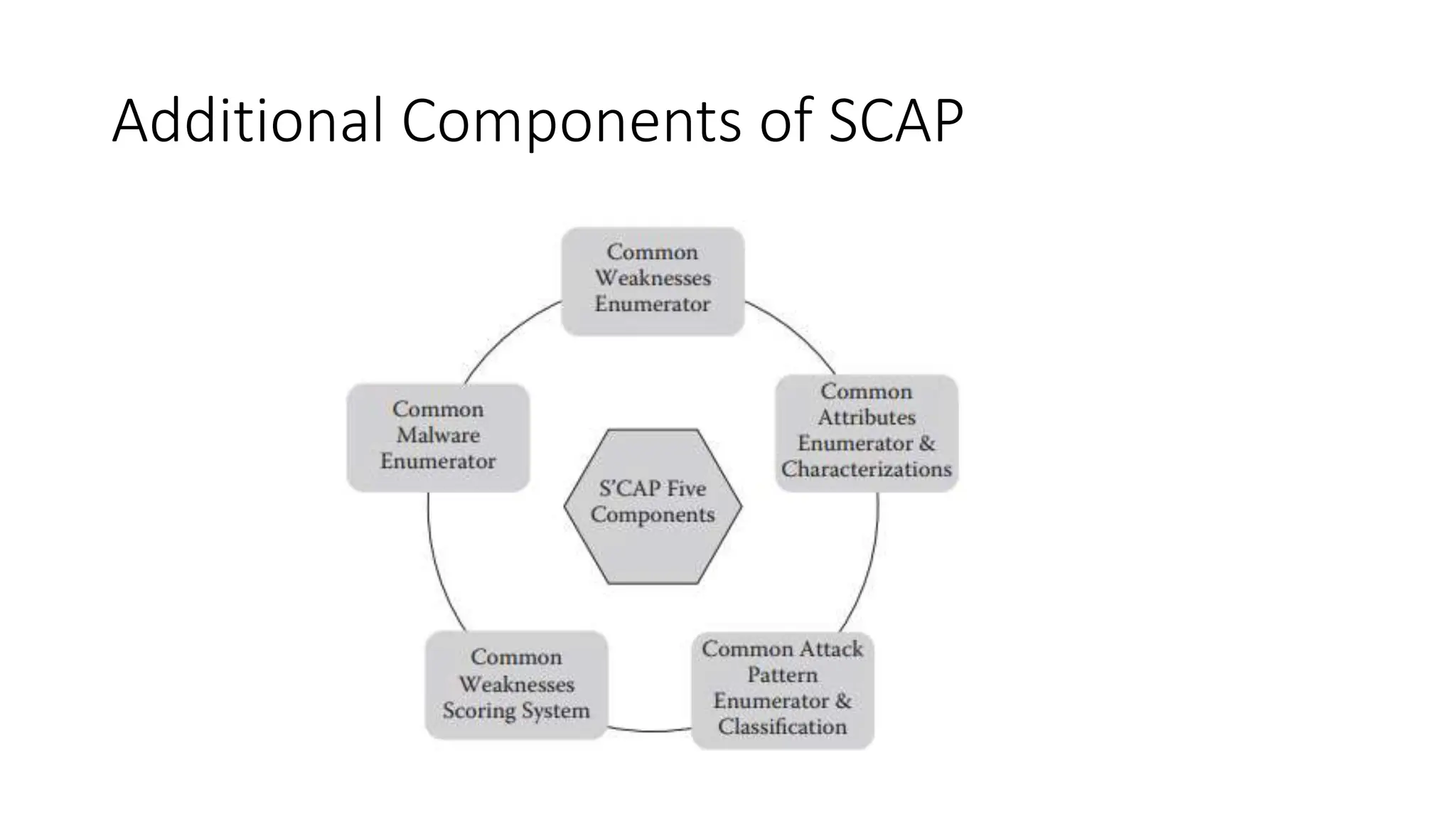
The document outlines vulnerabilities in information systems, defining vulnerability as flaws that compromise the system's security. It discusses various authentication methods, secure coding practices, and emphasizes the importance of threat modeling in identifying and mitigating risks. Additionally, it highlights the steps necessary to rectify software vulnerabilities and the role of security tools in protecting against attacks.








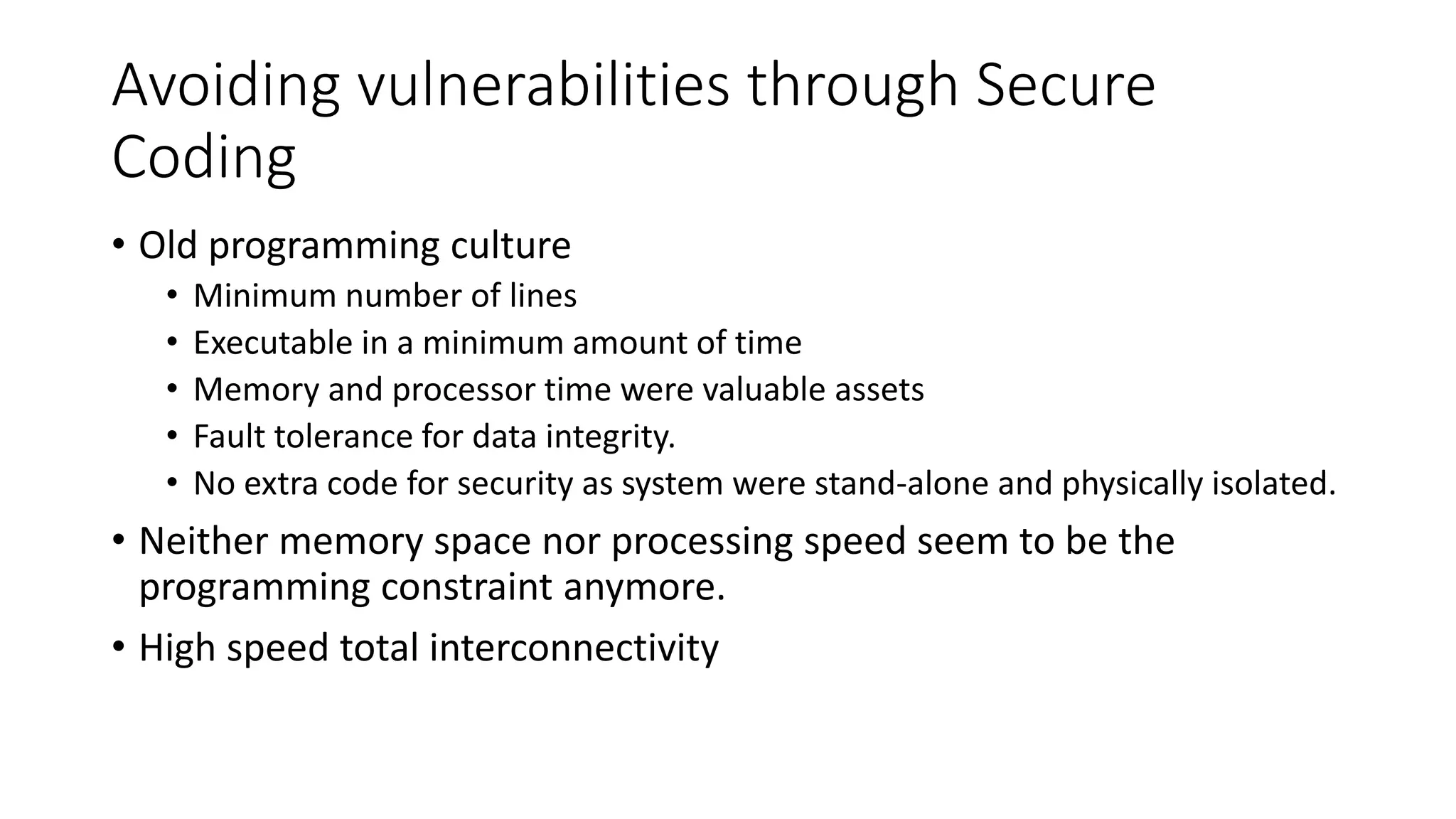
![Avoiding vulnerabilities through Secure
Coding
• vulnerabilities can be minimized by segmenting the code and the data
into resident and transient sections.
• Call the data and application only that is needed rather than bringing
the entire inventory of application.
• Minimize the impact of malware intrusion.
• Experts openly say: “The Internet is a hostile environment, so
you must . . . [be able to] withstand attack[s to survive,” and it is often
referred to as the Wild Wild Web, WWW.](https://image.slidesharecdn.com/chap-1-240104041135-066d9c03/75/chap-1-Vulnerabilities-in-Information-Systems-15-2048.jpg)