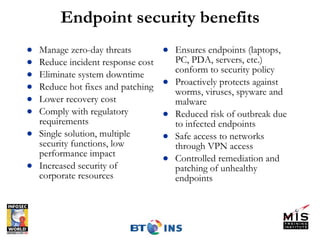
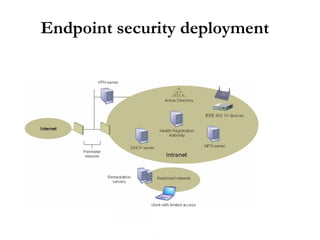
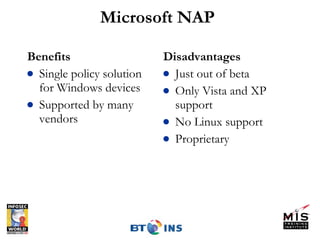
Endpoint security involves securing devices like laptops and ensuring they comply with security policies before being granted network access. Major endpoint security solutions include Cisco NAC, Microsoft NAP, and TCG's Trusted Network Connect standard, but all take the approach of evaluating devices and enforcing admission control policies using tools like 802.1x and RADIUS. While endpoint security is important, it also requires significant resources to deploy and its solutions are still evolving.



















































![QA/Thanks for attending Any questions? comments? Please fill out your evaluation sheets Ben Rothke CISSP, CISM BT PS [email_address]](https://image.slidesharecdn.com/infosec2007-endpointfinal-100112122246-phpapp02/85/Info-Sec2007-End-Point-Final-57-320.jpg)