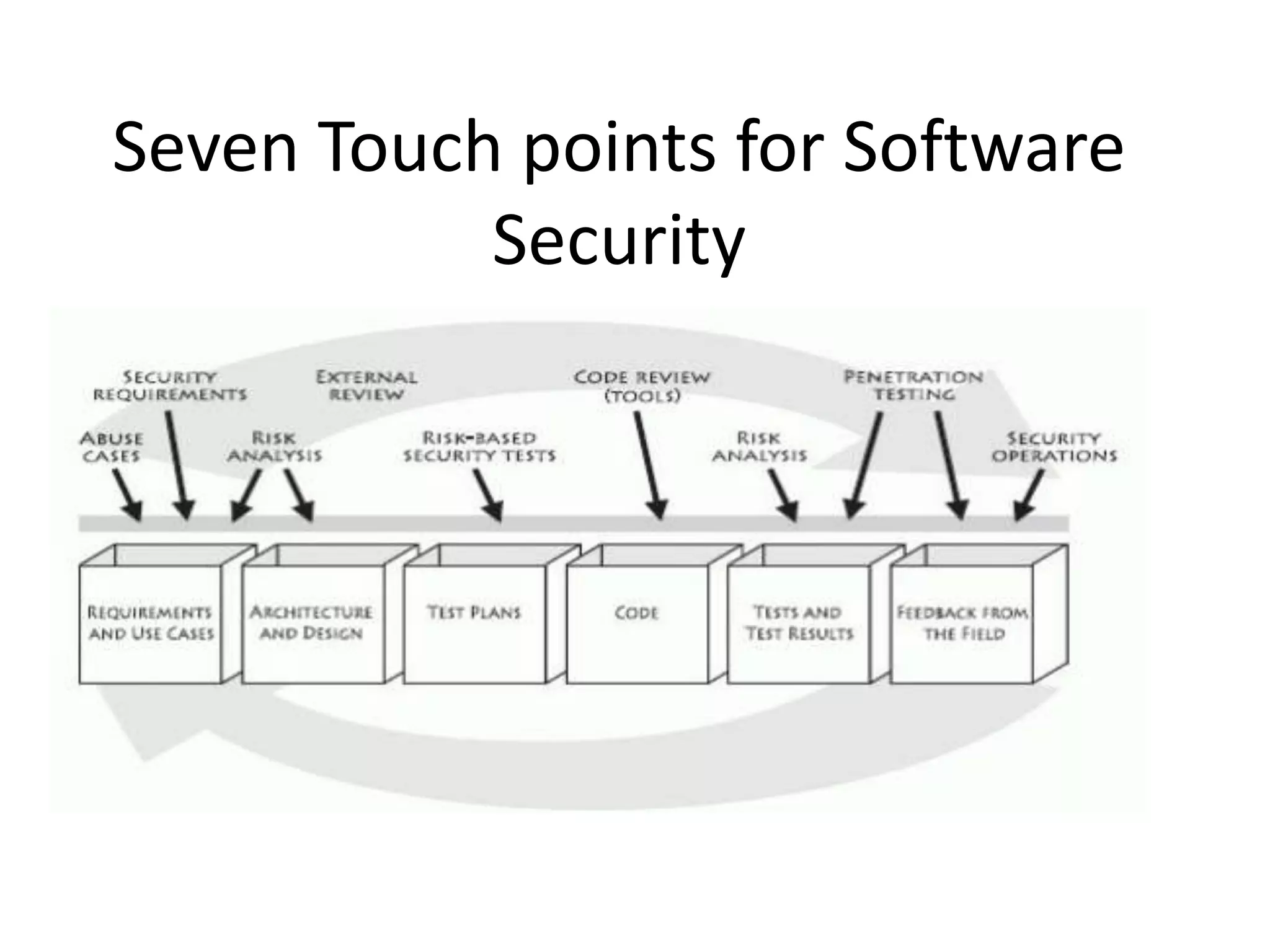
The document discusses seven touchpoints for building security into software systems. The touchpoints are ordered from most to least effective and include code review, architectural risk analysis, penetration testing, risk-based security testing, abuse cases, security requirements, and security operations. Conducting code reviews alone can find around 50% of security issues, so a comprehensive approach using multiple touchpoints is recommended to holistically address security risks.