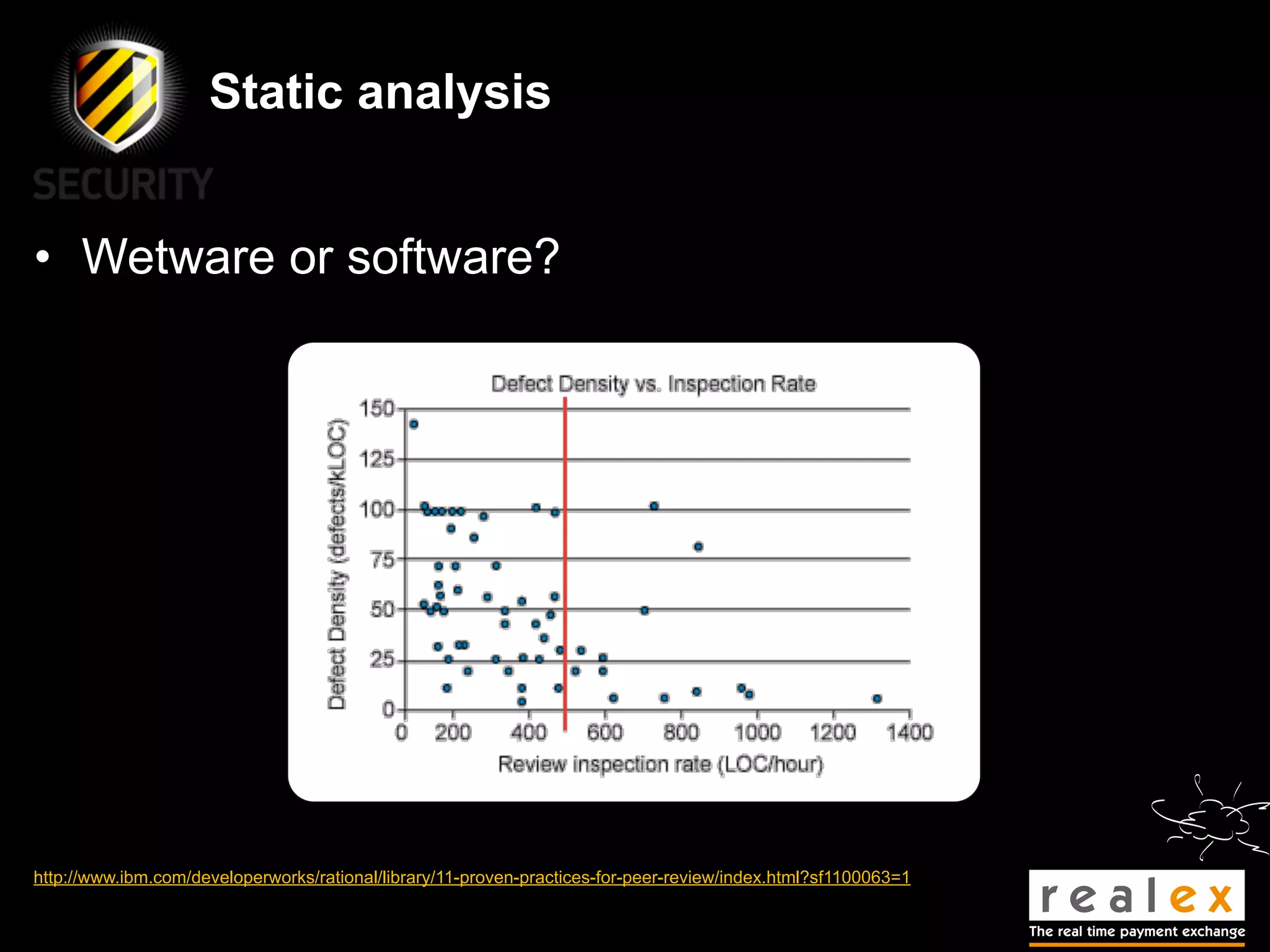
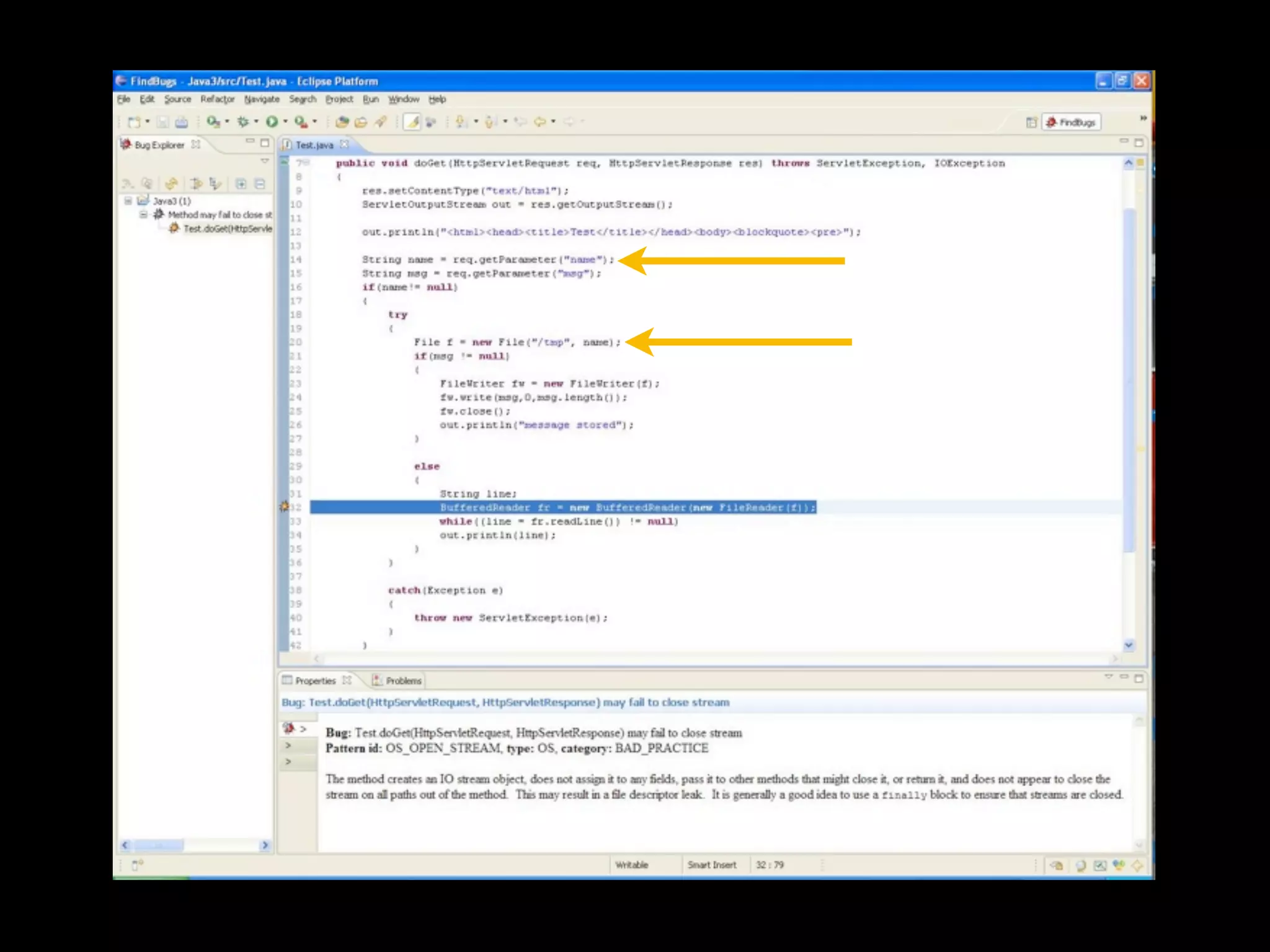
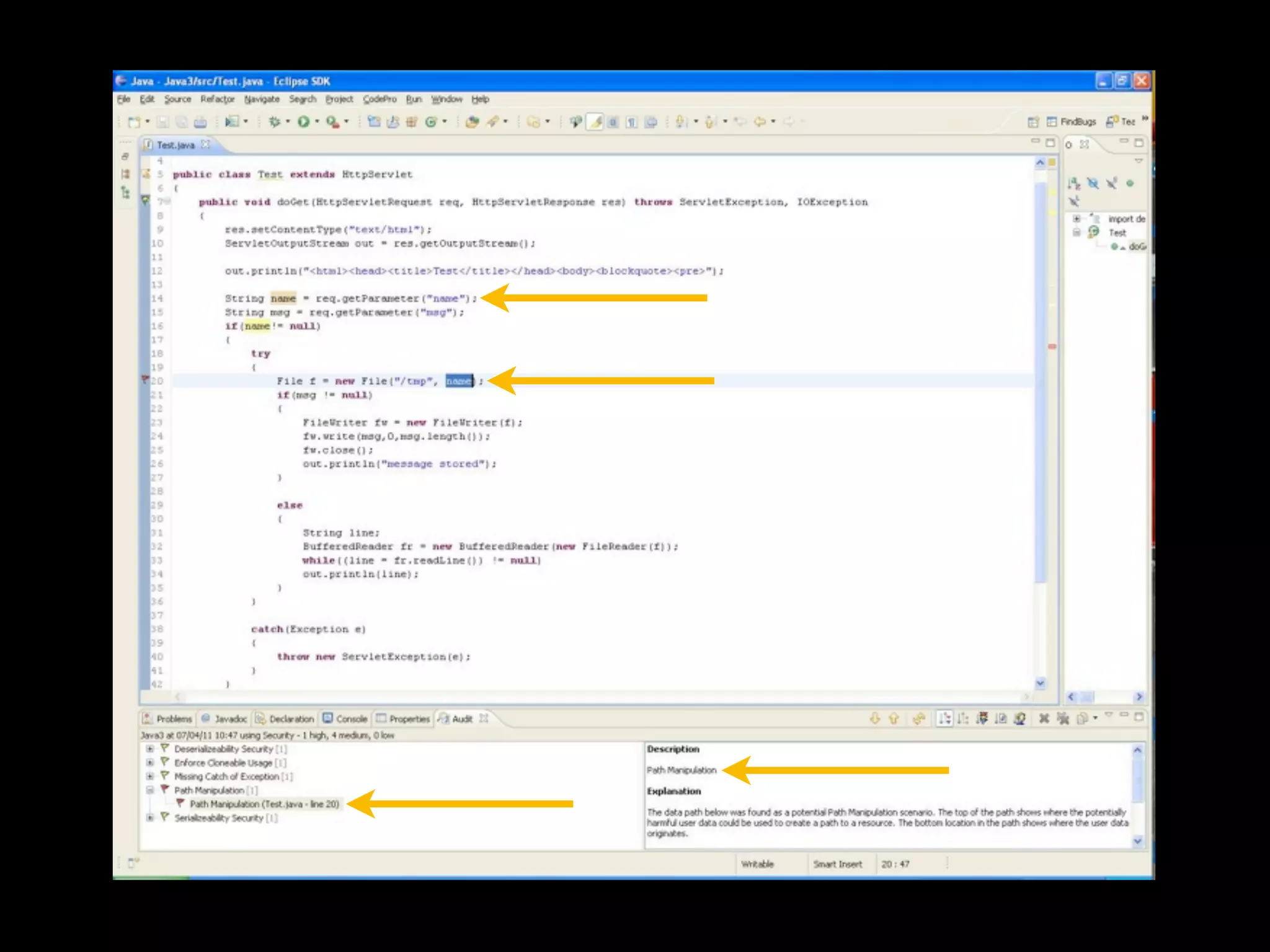
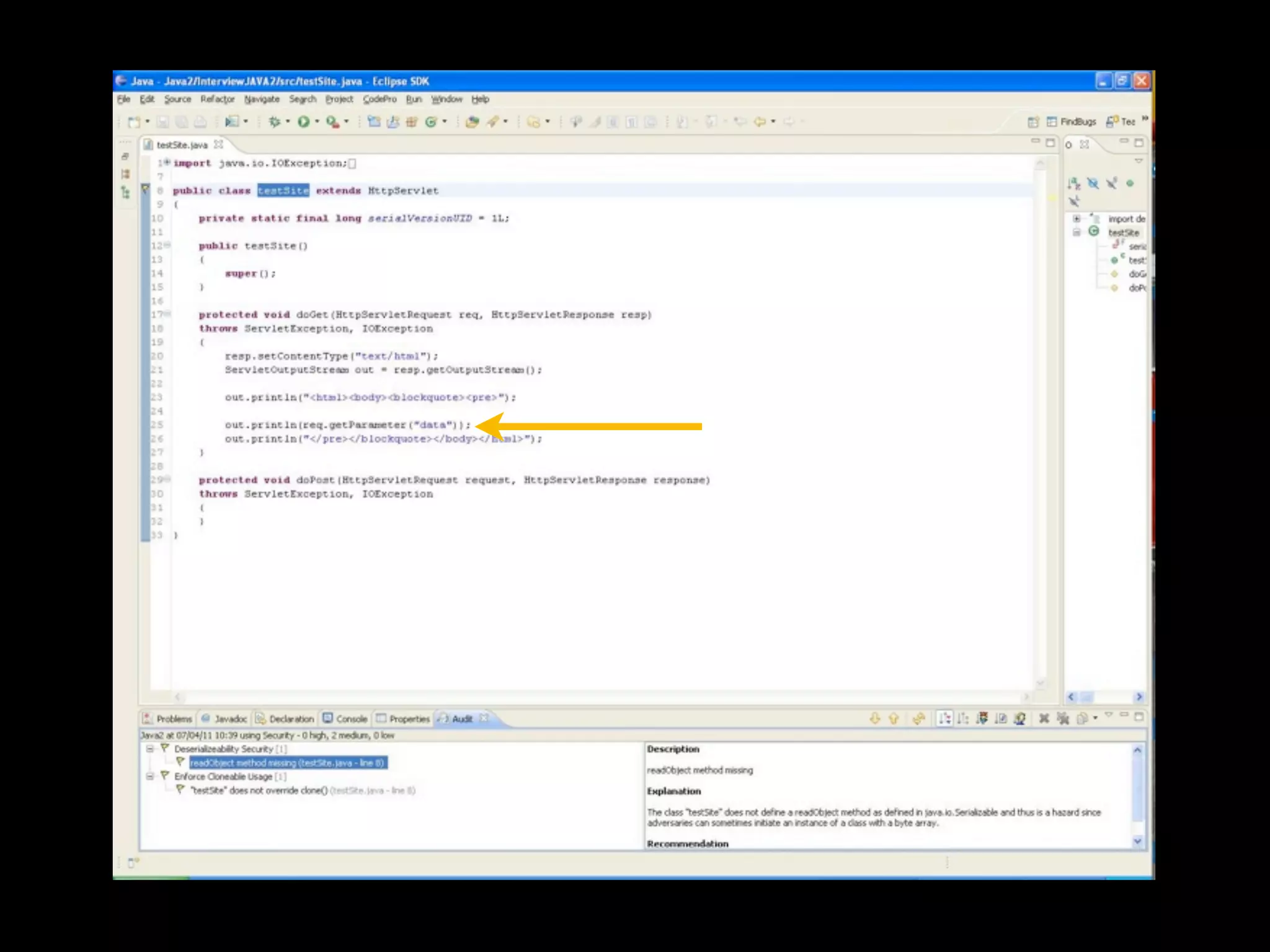
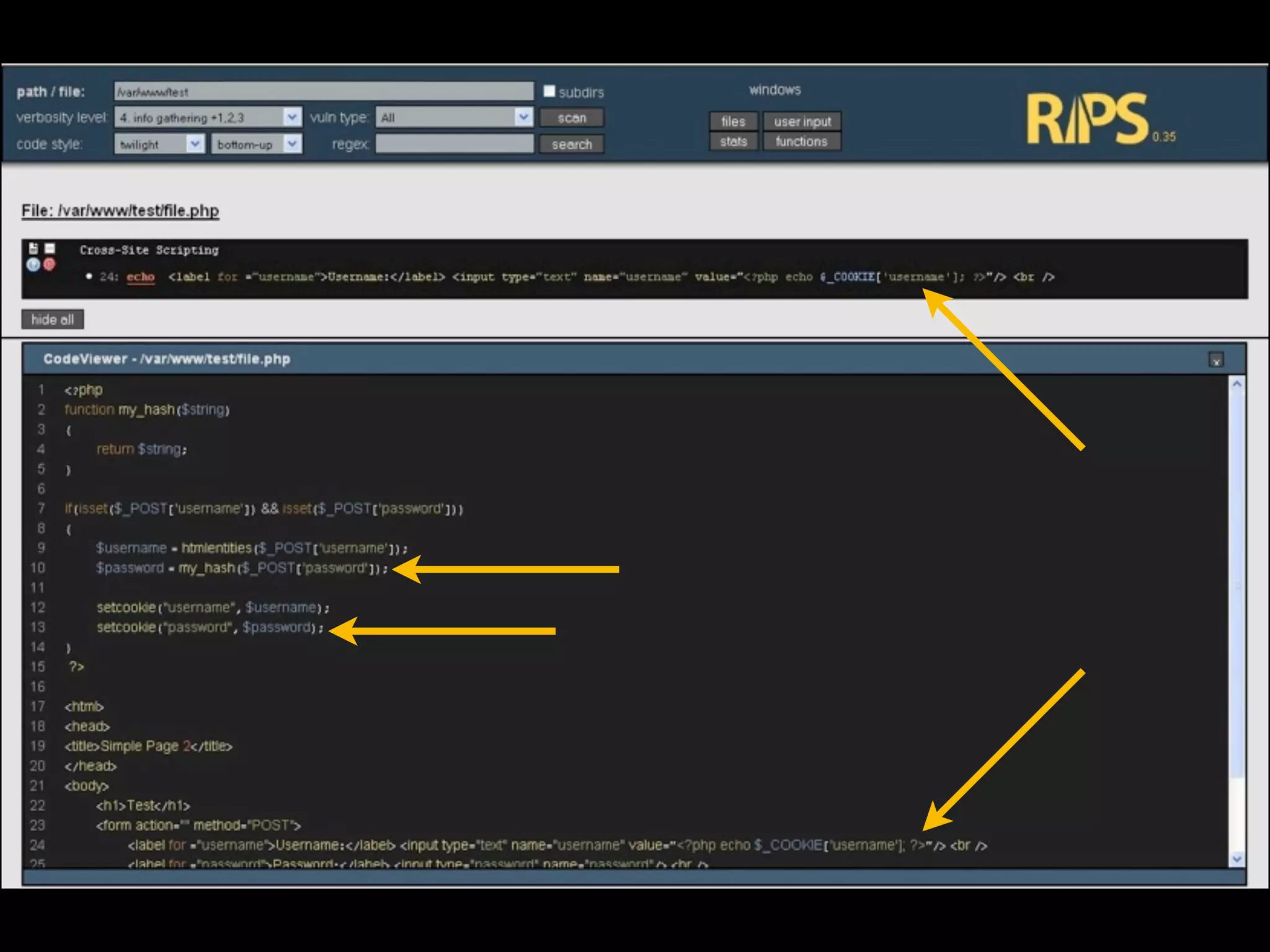
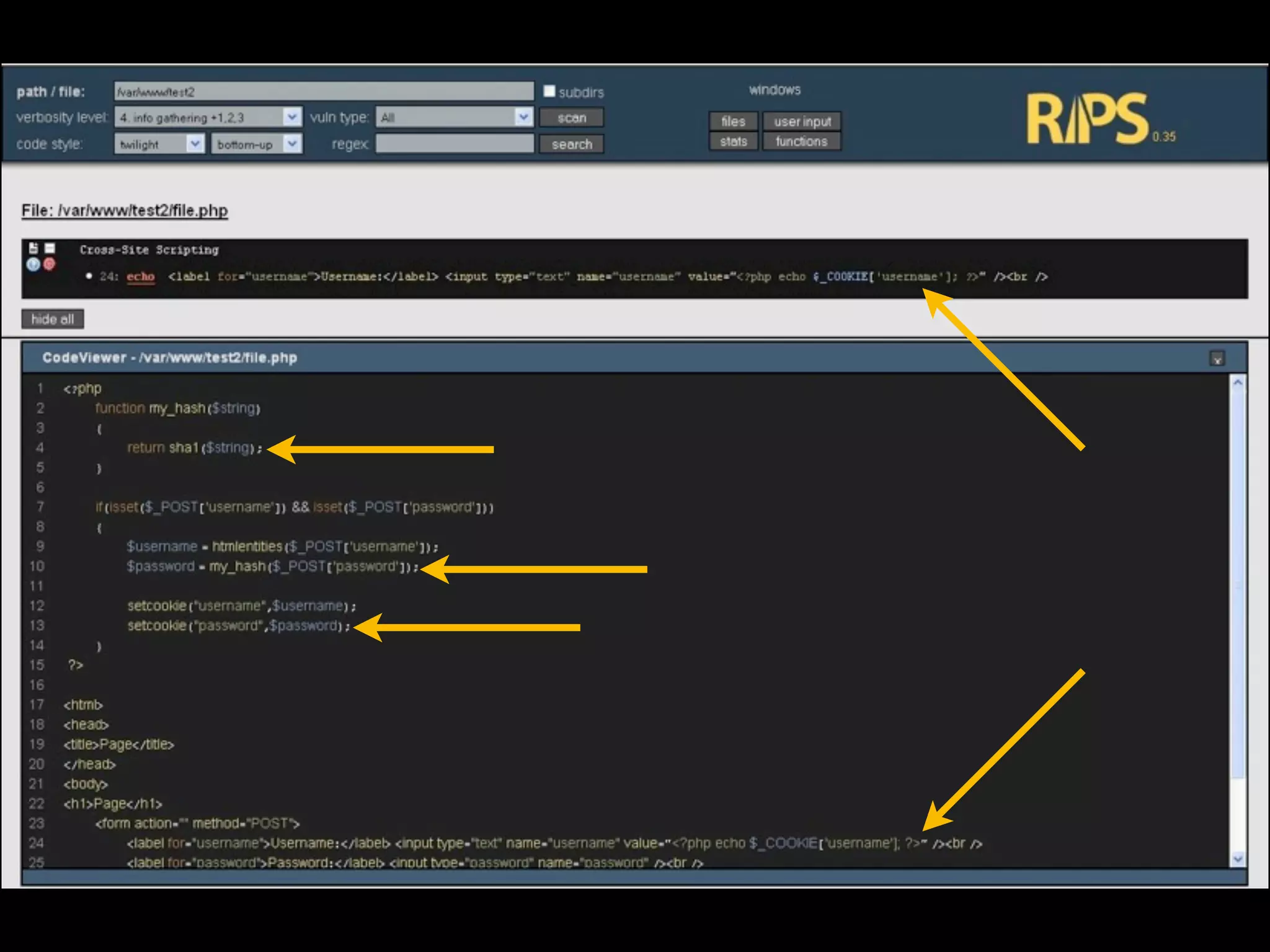
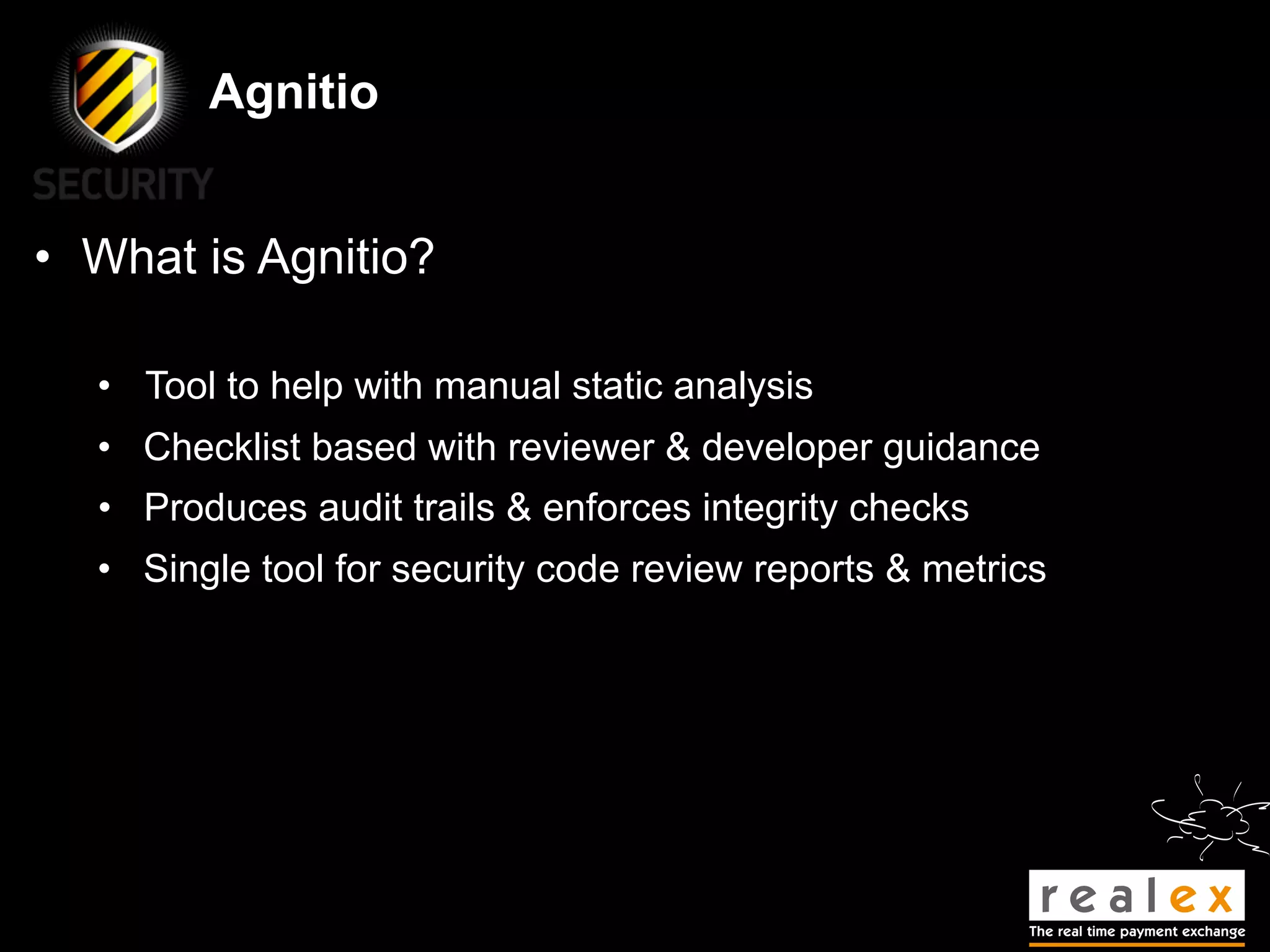
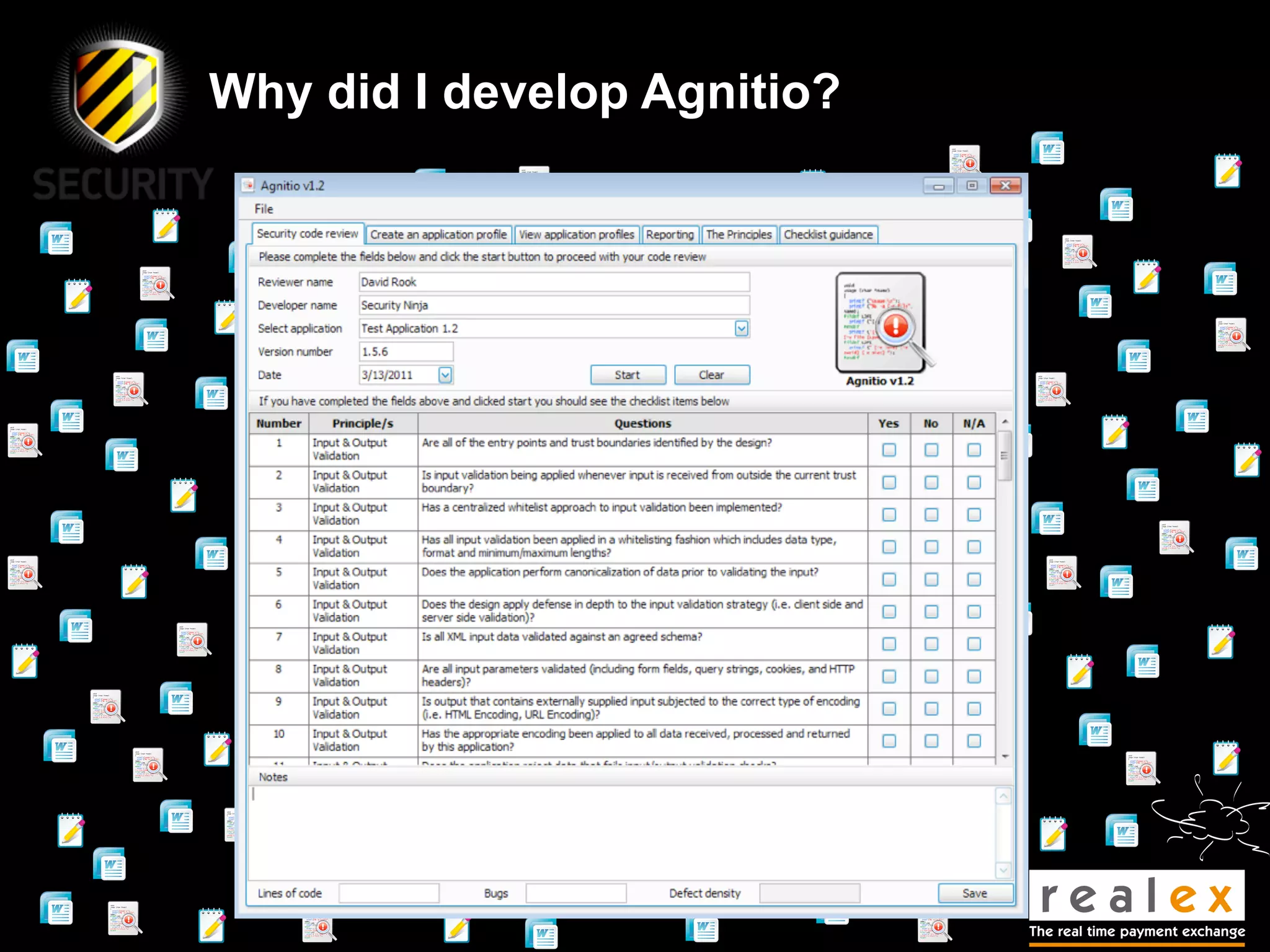
- David Rook is a security analyst and speaker who developed Agnitio, a tool to help with manual static code analysis.
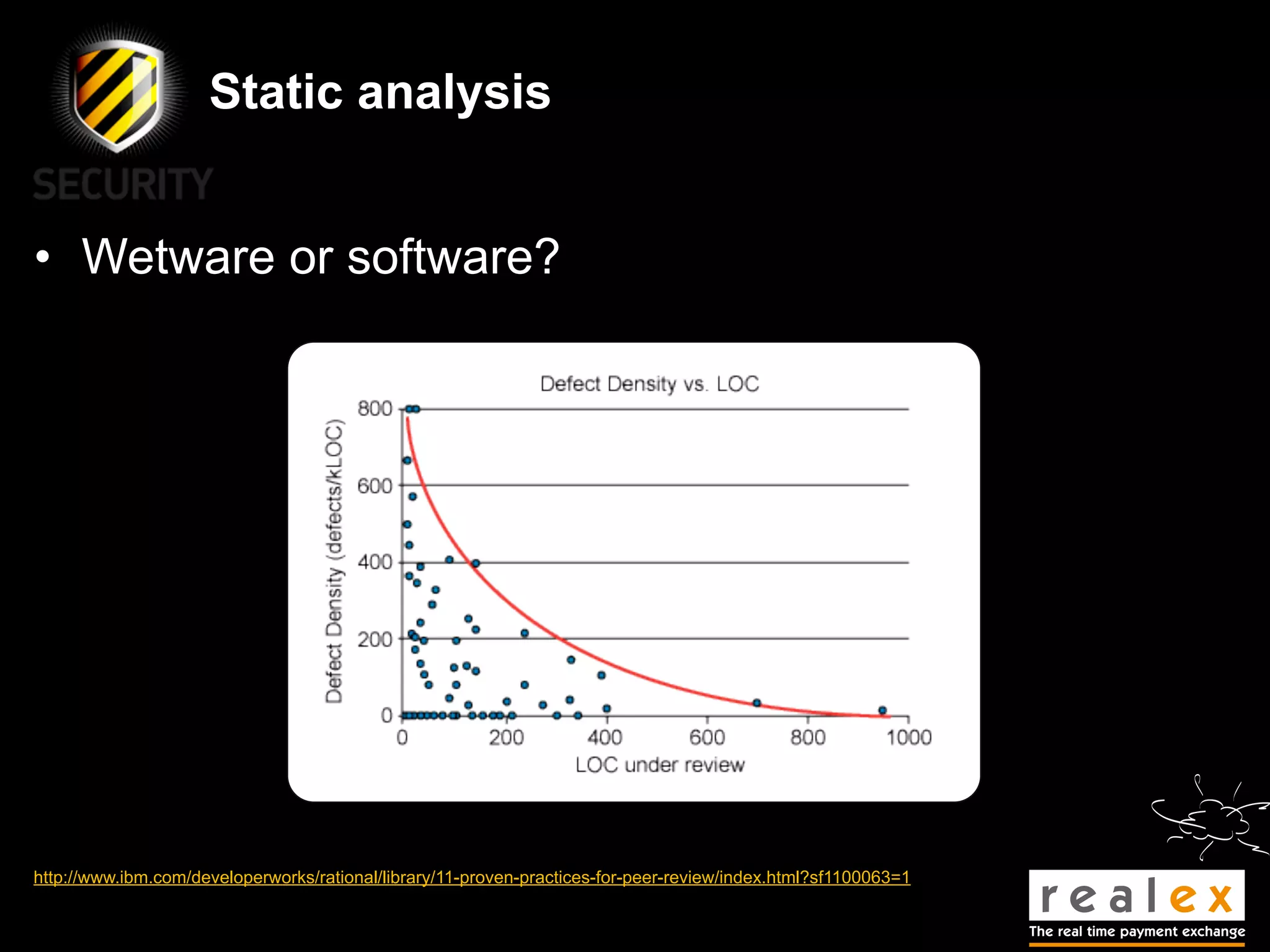
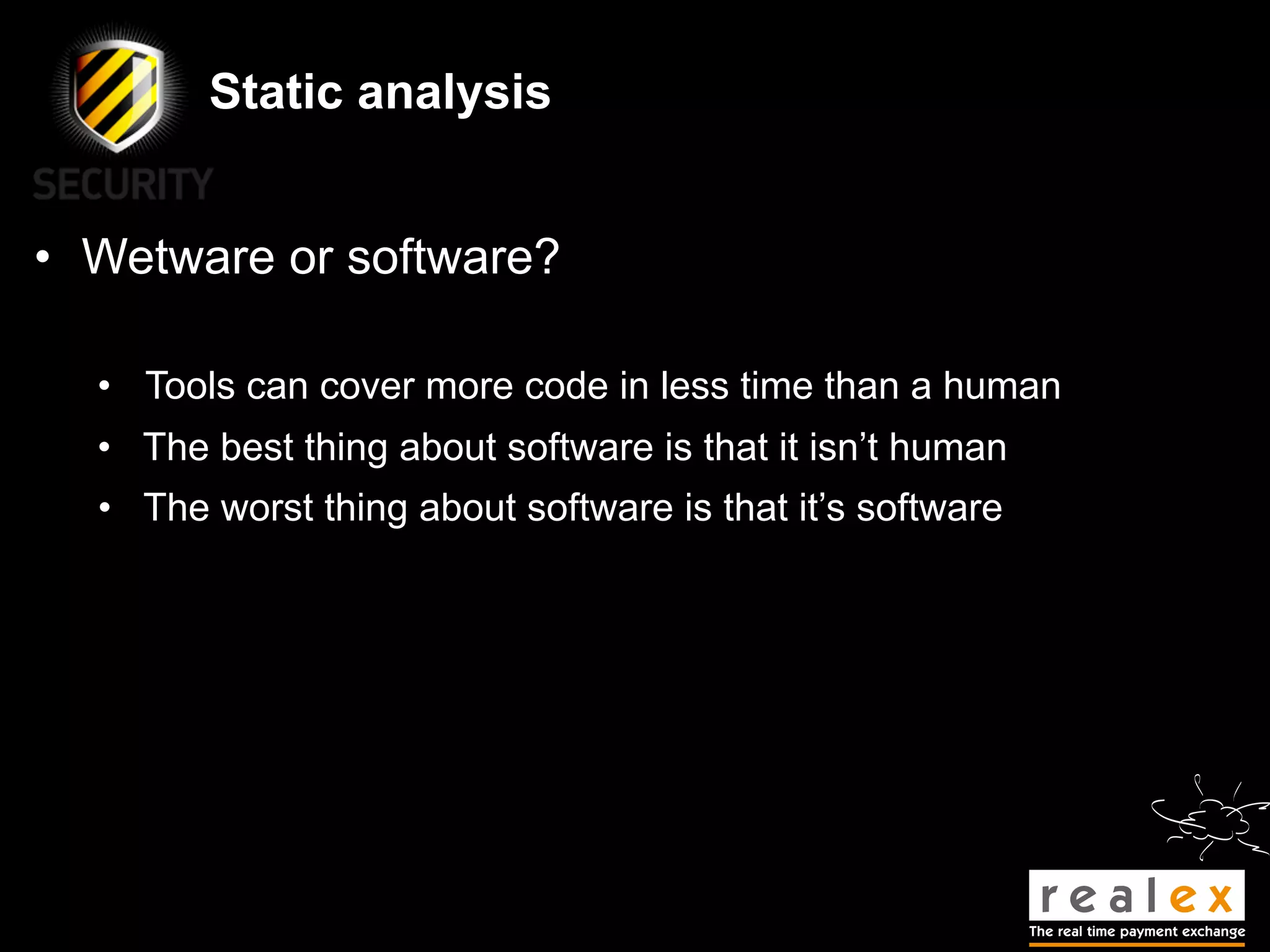
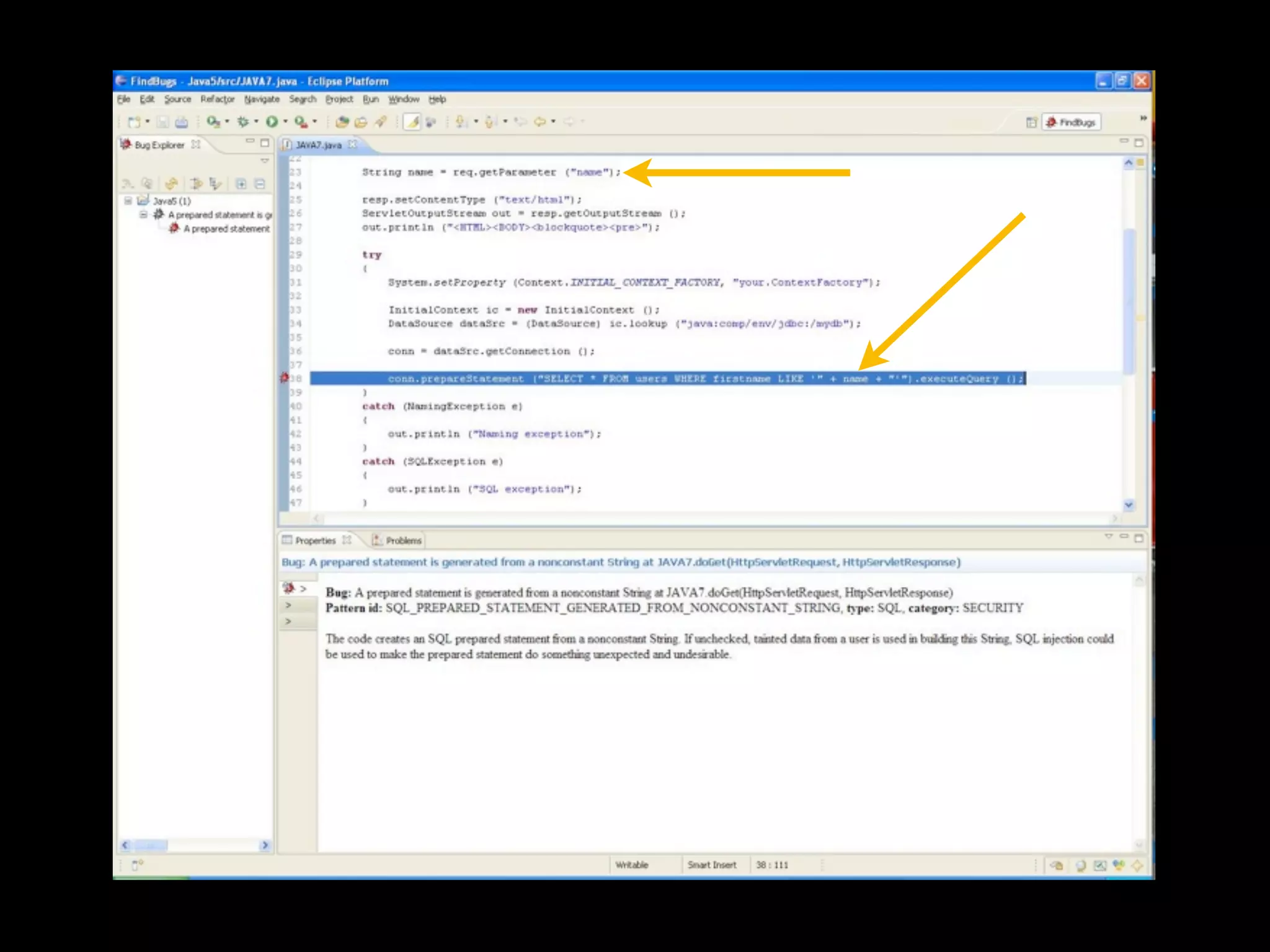
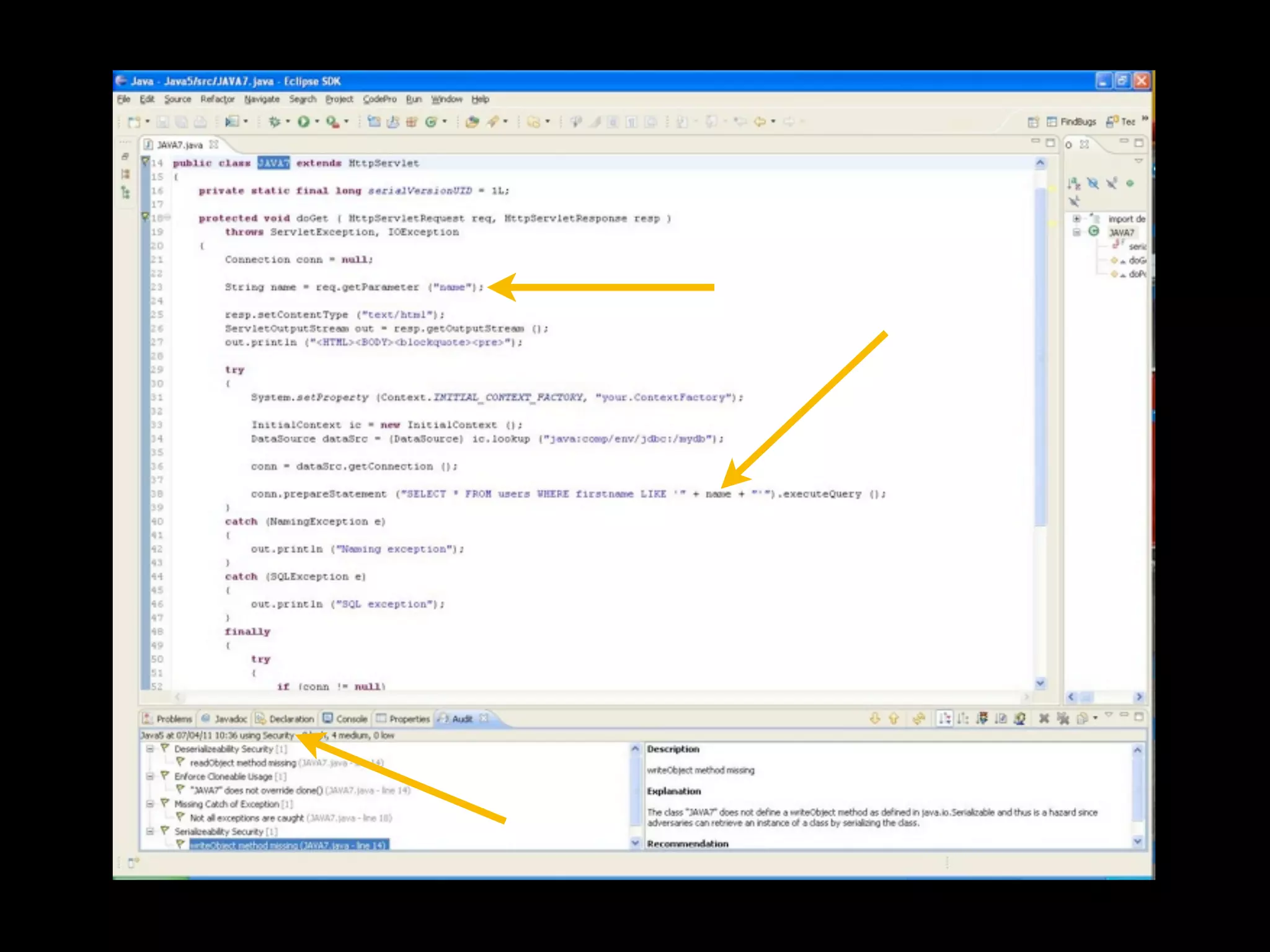
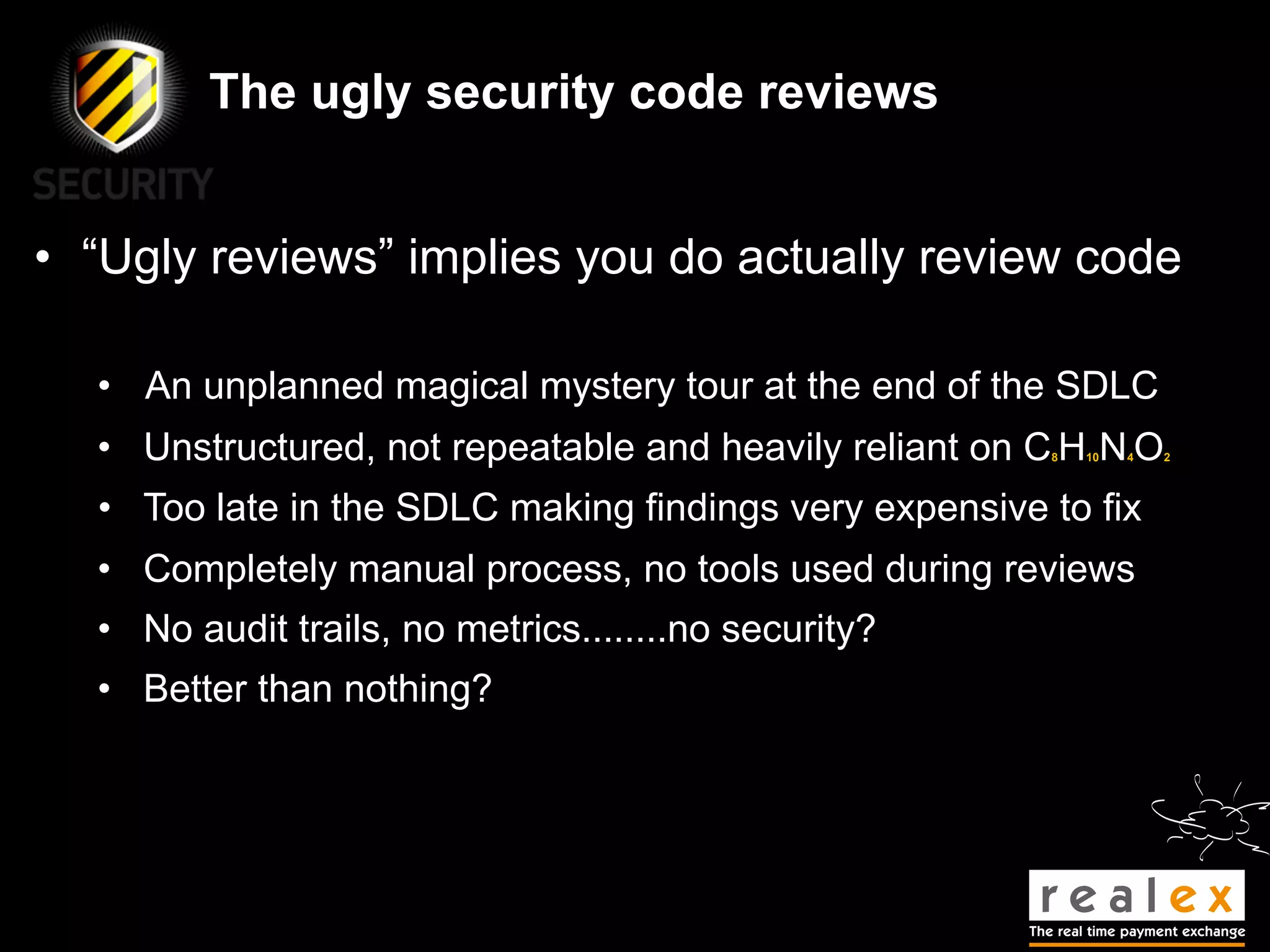
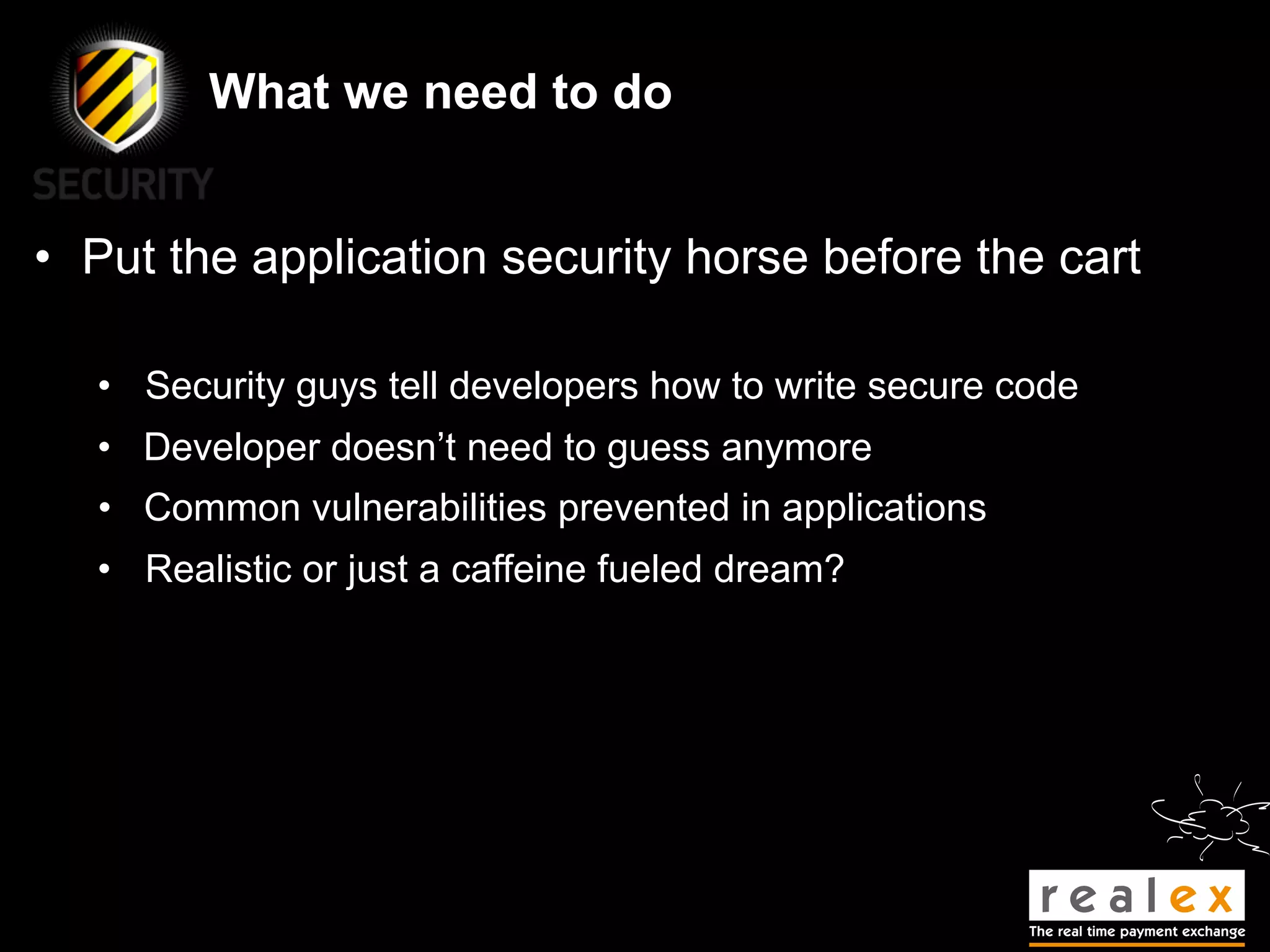
- Traditional static analysis involves human review of source code with or without tools, but humans have limitations. Agnitio aims to address these limitations by providing checklists, guidance, and automated processes to produce audit trails and metrics.
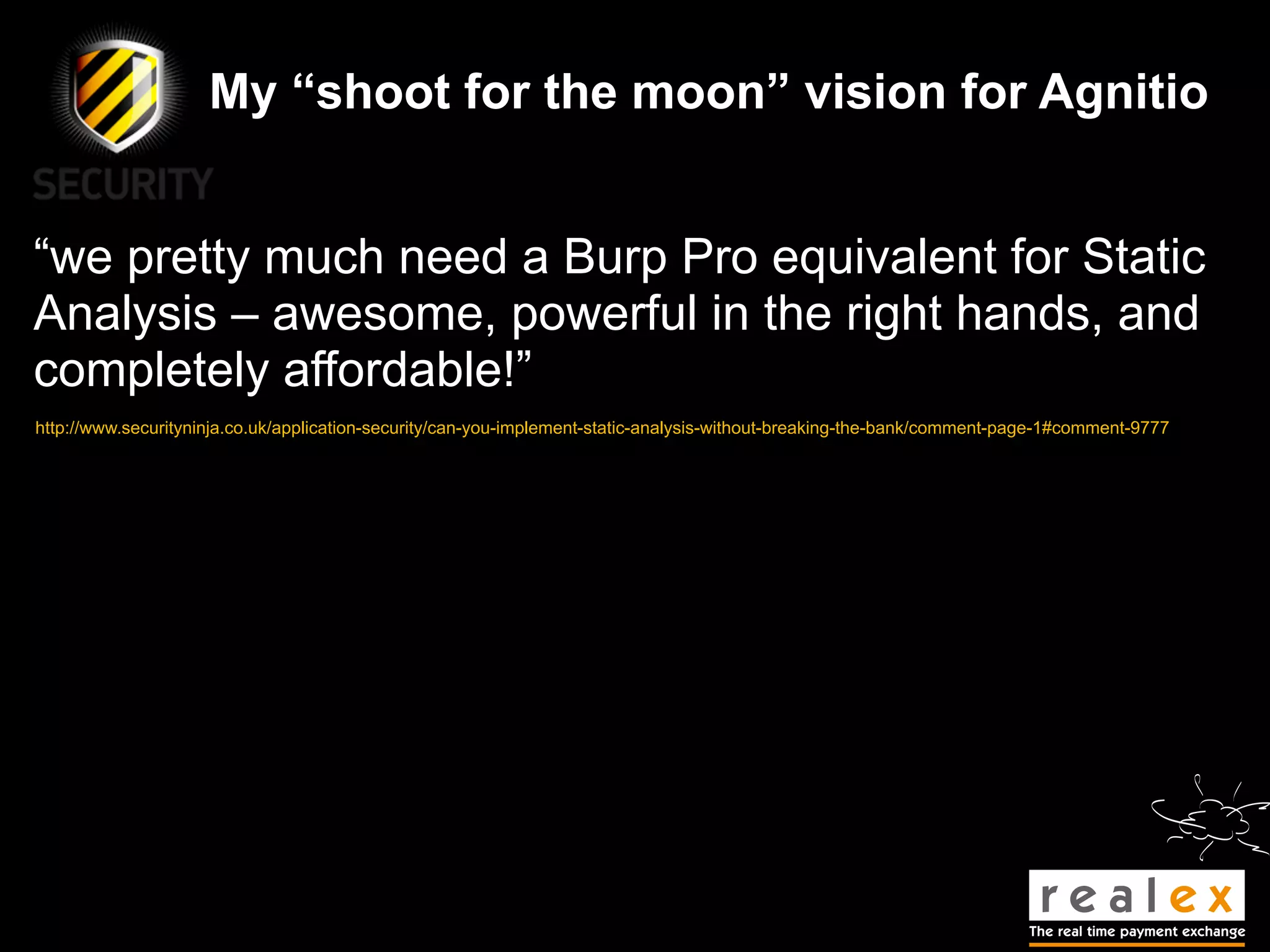
- The presentation will discuss traditional static analysis approaches, principles of secure development, and provide a sneak preview of new features in Agnitio version 2.0 to help improve the security code review process.