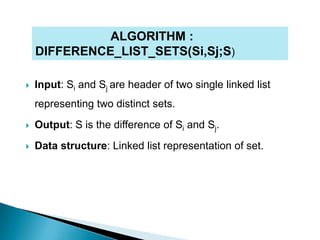
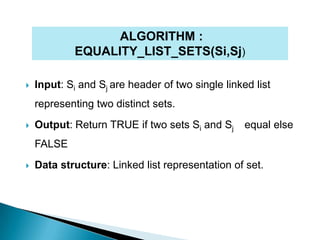
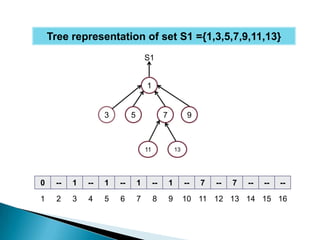
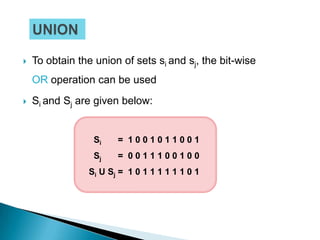
The document discusses various data structures for representing sets and algorithms for performing set operations on those data structures. It describes representing sets as linked lists, trees, hash tables, and bit vectors. For linked lists, it provides algorithms for union, intersection, difference, equality testing, and other set operations. It also discusses how bit vectors can be used to efficiently represent the presence or absence of elements in a set and perform operations using bitwise logic.






























![1. li=LENGTH(Si) //Size of Si.
2. li=LENGTH(Sj) //Size of Sj.
3. If (li != lj) then
1.Print “Two sets are not compatible for union”
2.Exit
4. End if
/*Loop over the under lying bit arrays and bit-
wise OR on its constituents data.*/
5. For i=1 to li do
1.S[i] = Si[i] OR Sj[i]
6. EndFor
7. Return(S)
8. Stop](https://image.slidesharecdn.com/setdatastructure-2-120903115336-phpapp01/85/Set-data-structure-2-35-320.jpg)


![1. li=LENGTH(Si) //Size of Si.
2. li=LENGTH(Sj) //Size of Sj.
3. If (li != lj) then
1.Print “Two sets are not compatible for
intersection”
2.Exit
4. End if
/*Loop over the under lying bit arrays and
bit-wise AND on its constituents data.*/
5. For i=1 to li do
1.S[i] = Si[i] AND Sj[i]
6. EndFor
7. Return(S)
8. Stop](https://image.slidesharecdn.com/setdatastructure-2-120903115336-phpapp01/85/Set-data-structure-2-38-320.jpg)


![STEPS:
1. li=LENGTH(Si) //Size of Si.
2. lj=LENGTH(Sj) //Size of Sj.
3. If (li != lj) then
1.Print “Two sets are not compatible for difference”
2.Exit
4. End if /*To find the inverse (NOT) of Sj.*/
5. For i=1 to li do
1.Sj[i] = NOT Sj[i]
6. EndFor /*Loop over the under lying bit arrays and
bit-wise AND*/
7. For i=1 to li do
1.S[i] = Si[i] AND Sj[i]d
8. EndFor
9. Return(S)
10. Stop](https://image.slidesharecdn.com/setdatastructure-2-120903115336-phpapp01/85/Set-data-structure-2-41-320.jpg)


![1. li=LENGTH(Si) //Size of Si.
2. li=LENGTH(Sj) //Size of Sj.
3. If (li != lj) then
1.Return (FALSE) //return with failure
2.Exit
4. End if
/*Loop over the under lying bit arrays and compare*/
5. For i=1 to li do
1.SJ[i] != Sj[i] then
1.Return (FALSE) //return with failure
2.Exit
2.EndIf
6. EndFor
/*Otherwise two sets are equal */
7. Return(TRUE)
8. Stop](https://image.slidesharecdn.com/setdatastructure-2-120903115336-phpapp01/85/Set-data-structure-2-44-320.jpg)


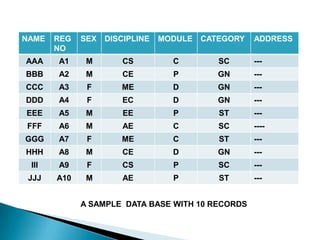


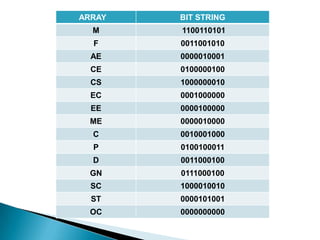
![ How many students are there in engineering and
computer discipline?
To retrieve this information only bit arrays CS needs to
be searched for the number of 1‟s in it.
Who are the female students in CS discipline?
For this information do F CS or
[0 0 1 1 0 0 1 0 1 0] [1 0 0 0 0 0 0 0 1 0] =
[000000010]
Thus it gives the 9th record only.
How many students of General Category are there in
diploma or degree Module?
GN [P D]](https://image.slidesharecdn.com/setdatastructure-2-120903115336-phpapp01/85/Set-data-structure-2-51-320.jpg)


