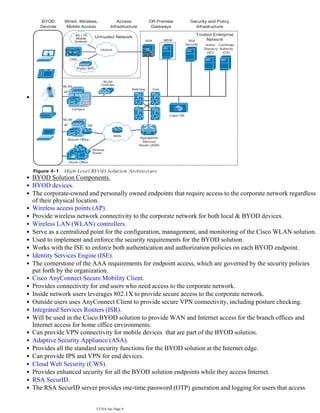
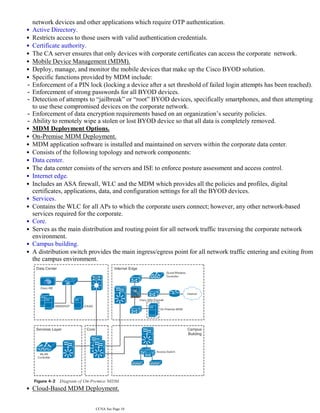
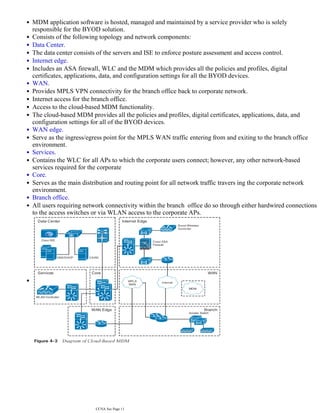
The document discusses the basics of IT security including the CIA triad of confidentiality, integrity and availability. It also covers common security concepts such as assets, vulnerabilities, threats, countermeasures and risks. Additionally, it summarizes authentication, authorization and accounting (AAA) protocols, common attacks and how to implement secure network architecture.
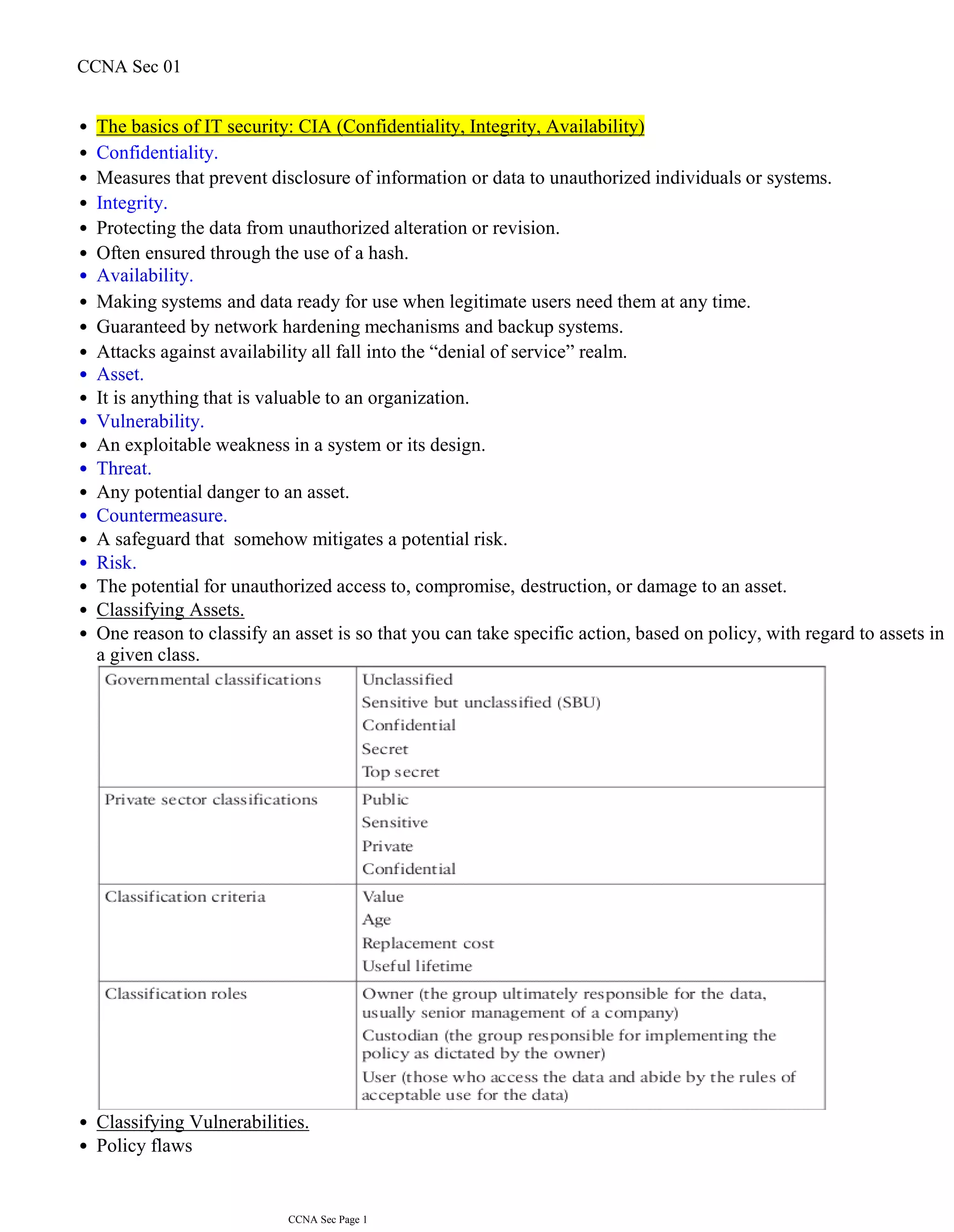



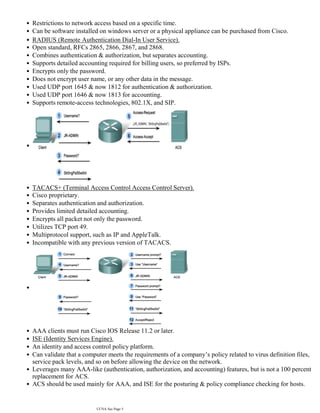
![Login method types:
•
Enable.
•
Uses the enable password for authentication.
•
Line.
•
Uses the line password for authentication.
•
Local.
•
Uses the local username database for authentication.
•
Local-case.
•
Uses case-sensitive local username authentication.
•
Group radius.
•
Uses the list of all RADIUS servers for authentication.
•
Group tacacs+.
•
Uses the list of all TACACS+ servers for authentication.
•
Group group-name.
•
Uses a subset of RADIUS or TACACS+ servers for authentication as defined by the aaa group server radius
or aaa group server tacacs+ command.
•
None.
•
To ensure that the authentication succeeds even if all methods return an error.
•
AAA lists.
•
When AAA is enabled, the default list is automatically applied to all interfaces and lines but with no methods
defined unless a predefined list is assigned.
•
If the default method list is not set and there is no other list, only the local user database is checked.
•
Authorization.
•
What a user can and cannot do on the network after that user is authenticated.
•
Implemented using a AAA server-based solution.
•
When a user has been authenticated, a session is established with the AAA server.
•
The router requests authorization for the requested service from the AAA server.
•
The AAA server returns a PASS/FAIL for authorization.
•
TACACS+ establishes a new TCP session for every authorization request.
•
When AAA authorization is not enabled, all users are allowed full access.
•
To enable AAA.
•
R(config)# aaa new-model
•
To Configure Authentication to Use the AAA Server.
•
R(config)# aaa authentication login list-name|default method method method [maximum 4 methods]
•
R(config)# aaa authentication login default group radius group tacacs+ local …..
•
R(config)# aaa authentication enable list-name|default group tacacs+ enable
•
Methods are used in order, if no response from one, the next is used.
•
To specify the number of unsuccessful login attempts (then the user will be locked out).
•
R(config)# aaa local authentication attempts max-fail n
•
The account (non priv 15) will stay locked until it is cleared by an administrator.
•
To display a list of all locked-out users.
•
R# show aaa local user lockout
•
To unlock a specific user or to unlock all locked users.
•
R# clear aaa local user lockout all | username name
•
To display the attributes that are collected for a AAA session.
•
R# show aaa user all | unique-id
•
To show the unique ID of a session.
•
R# show aaa sessions
•
CCNA Sec Page 6](https://image.slidesharecdn.com/ccnasec01-211223091016/85/Ccna-sec-01-6-320.jpg)