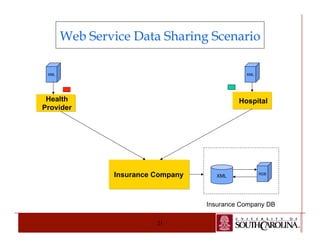
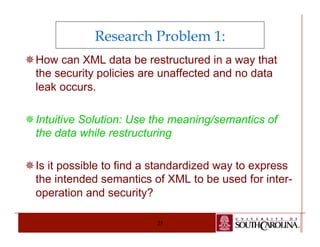
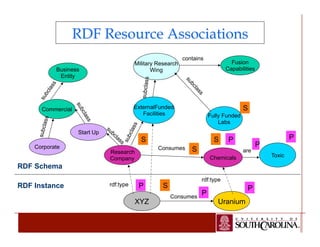
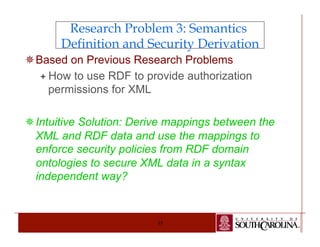
The document details a PhD dissertation defense on a semantic-aware authorization framework for secure data sharing, emphasizing the evolution of web applications and the security challenges they face. It proposes a new framework that incorporates RDF authorization models and semantic mappings to improve access control and data sharing across different systems. The research addresses limitations of existing XML security methods and aims to provide a comprehensive solution for secure, semantic-enhanced data sharing.





![Software Application Evolution
6
¯ Past Web
ª Static HTML Web Pages – rendering focus
ª Data consumed by Humans
¯ Move towards Web Applications
ª Web Apps are the trend [1]
ª Wide audience and reach
ª Thin clients, only browser required
¯ Successful trend making applications
ª Google search engine
ª Mash Ups
ª Social Networking Applications (MySpace, Facebook)
ª Multimedia sharing Applications (YouTube, Slideshare)](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-6-320.jpg)















![Commercial RDF Applications
¯ NASA uses it extensively for document management
¯ Companies are moving towards a RDF backed data creation
and social networking apps
¯ Millions of data triples asserted to bootstrap the knowledge
sources (DbPedia, Twine, Freebase)
ª Freebase stores millions of information entities in RDF
format [2]
ª TWINE: RDF based social networking application [3]
¯ Several Government Agencies are using RDF
¯ Social Networking Graphs
ª Each person is a data generation warehouse
27](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-27-320.jpg)





![Existing Literature
34
¯ RDF security
ª Qin and Atluri [4]: A concept-level access control for web data, where
access control is defined on ontological concepts and instances of
these concepts inherit the access control of the concepts they belong
to.
ª Finin et al. [5]: A policy based access control model for RDF data in
an RDF store. Provides control over the different action modes
supported by the RDF store like inserting a set of triples, deleting a
triple, and querying a triple.
ª Dietzold and Auer [6]: An access control model for RDF Triple Wikis.
Their model allows the specification of custom rules that can be used
for securing access to the store.
ª Kaushik et al. [7]: A logic based policy language for securing full or
partial ontologies.](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-34-320.jpg)
![Existing Literature
¯ Semantic Data Integration
36
ª Xiao & Cruz [8]:
² An ontology-based approach for integration of
heterogeneous XML sources.
² Converts XML data sources into a RDF ontology.
Local ontologies are merged to create a global
ontology.
ª Several Engineering based works
² Gloze [9]
² WEESA [10]
² Try to induct semantics in XML based on discovery.](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-36-320.jpg)



![RDF Security Policy
¯ Typical Security Policy Components:
ª (Subject, Object, Privilege/Security label)
ª <s,o,±pri/sl>
¯ RDF security object / pattern [x, y, z]
¯ Security classification ([x, y, z], TS)
¯ Security Objects Subsumption
¯ Association protection
¯ Fine grained – Individual elements/two elements
¯ Policies in RDF format
40](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-40-320.jpg)
![Mapping a Default Policy
44
¯ Default policy
² ([x, y, z], TS)
(Student, rdfs:subClassOf, Person)
(University, rdfs:subClassOf, GovAgency)
(studiesAt, rdfs:domain, Student)
(studiesAt, rdfs:range,University)
(John, studiesAt, USC)](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-44-320.jpg)

![Conflict resolution: Pattern
Mapping
46
¯ Conflict Resolution
ª ([Student, studiesAt, University], P)
ª ([John, studiesAt, USC], S)
P
S
( [John, studiesAt, USC],
S)](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-46-320.jpg)



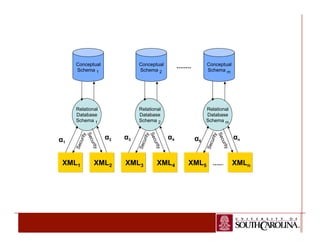


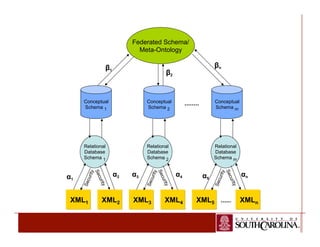
![Mappings
¯ Let X be the XML schema tree and O be the RDF ontology. The XML to
RDF mappings are defined in the following way:
• An XML leaf node vi is mapped to a RDF property p Є P, : p → (c1,
c2) such that the datatype of the leaf node element { Ri.ai }
corresponds to the object datatype RDF Class c2 Є C,
• A non-leaf node vi with sub element nodes is mapped to a RDF class
c Є C.
• A non-leaf node vi with sub element nodes is mapped to a RDF
property p Є P such that μ(vj) = cj , μ(vk) = ck and (p) = (cj , ck). Here
vj and vk are the ancestor and descendant of node vi, respectively.
• A pair of XML nodes (vi, vj) is mapped to an RDF triple [s, p, o] where
ed(vi, vj) is an unlabeled edge in XML tree and (p) = rdf:type,
rdfs:subClassOf, or rdfs:subPropertyOf.
55](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-55-320.jpg)
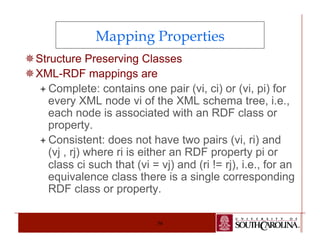
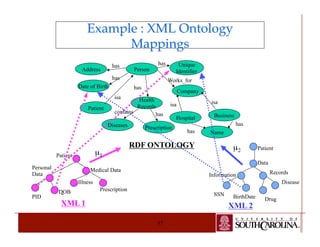

















![RDF - Patterns
¯ An RDF pattern pt, is a triple represented as pt = [r,
p, v], where each component of the pattern is
either
ª A data constant such that r є R, p є PR, and v є
R U L, or
ª The symbol ”-” representing the empty element
of the triple, or
ª A variable represented as a symbol starting
with ?, corresponding to any value for the triple
element
79](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-79-320.jpg)
![RDF Security Policy
¯ The security policy SP is a set of pairs SP =
{sp1, . . . , spn} U {spdef} such that every spi has the
form (pti, sli) and λ(pti) = sli where pti is an RDF
pattern, sli is a security label in SL and λ is the
security labeling function. spdef = (ptdef , sldef )
represents the default policy where ptdef = [?x1, ?
x2, ?x3] is a pattern with all variables and sldef is the
default security label such that sldef !≥ sli & sldef !≤ sli
for any sli in SL.
80](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-80-320.jpg)
![RDF Pattern Mapping
¯ Let pt = [r, p, v] and pt′ = [r′, p′, v′] be two RDF patterns and
R be the set of Resources. Let ST and DT be the RDF
Schema and Instance respectively. For all pattern elements
e and e′ where e is either r,p, or v and e′ is either r’,p’, or v’
respectively, the pattern mapping ν: pt → pt′ is defined as:
ª ν maps a variable e to a resource e′ Є R.
ª ν preserves all constants (i.e., (c) = c), where c is a
constant
ª ν maps an empty element “-” to
81
² an empty element “-”.
² a variable e′
² a constant e′ in ST U DT
ª ν maps a constant e in DT (data instance) to a constant
e’ such that e = e′, i.e., it is an identity mapping](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-81-320.jpg)


![Conflict Policy Mapping
¯ Let pt1, . . . , ptk be the RDF patterns and sl1, . . . ,
slk be their security labels, respectively. Let ν1, . . . ,
vk be the mappings from pt1, . . . , ptk to an RDF
triple t. The security label sl of a triple t is defined as
least upper bound,i.e., sl = LUB[sl1, . . . , slk] and
the corresponding security object is (t, sl).
84](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-84-320.jpg)
![Mapping Rule Set
¯ Let X = (V,E, θ,L) be an XML schema tree, O = (C,
P,δ ,≤) be an RDF ontology schema and μ : X → O
be a mapping function. A mapping rule set Mxo
containing XML to RDF components’
correspondences is defined as Mxo = {(x1, r1) . . .
(xk, rk)} such that xi is either an XML node vi Є V or
a pair of nodes (vi, vj) and ri is either an RDF class
ci Є C, an RDF property pi Є P or an RDF triple ti =
[si, pi, oi].
86](https://image.slidesharecdn.com/semanticsecuritydefensepresentationamitjain-141009021134-conversion-gate02/85/Semantic-Security-Authorization-on-the-Web-with-Ontologies-86-320.jpg)