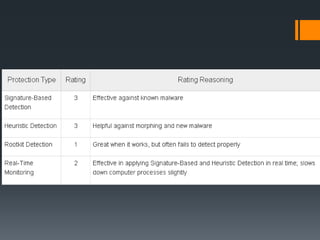
This document discusses malware, antivirus software, and firewalls. It defines malware as malicious software like viruses, worms, trojans, adware and spyware that can damage computers. It describes common types of malware and how they infect devices. It then explains how antivirus software works using techniques like signature-based detection, heuristics, rootkit detection and real-time protection to identify and remove malware. Finally, it defines firewalls as systems that block unauthorized network access and outlines types like hardware/software firewalls as well as how they function using methods such as packet filtering, application inspection and proxy servers.