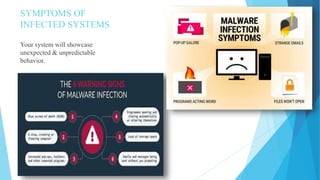
This document discusses malware forensics. It defines malware as malicious software programs and describes what malware can do. The document outlines different types of malware and explains how malware analysis has become a forensic discipline. It describes malware forensics as investigating malware properties to identify culprits and reasons for attacks. This includes analyzing malicious code, entry points, propagation methods, and system impacts. The document contrasts static and dynamic malware analysis approaches.