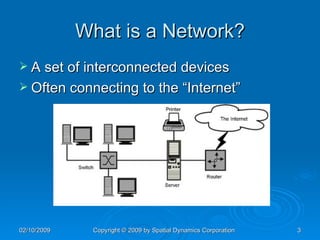
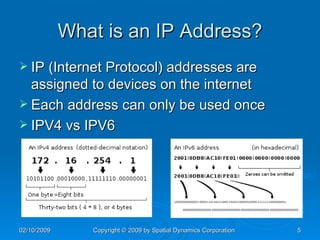
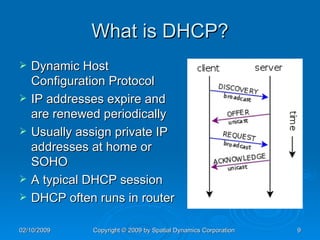
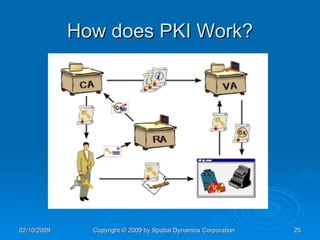
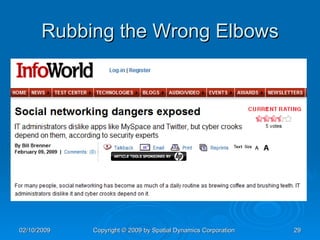
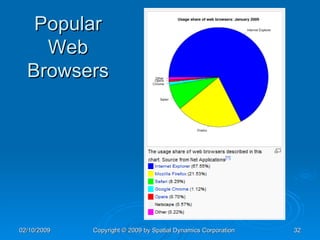
The document provides an overview of safe computing at home and work, covering essential topics such as network definitions, security measures, different types of malware, and protections like firewalls and anti-virus software. It also discusses various communication platforms, risks associated with them, and concepts of digital security, including digital signatures and public key infrastructure. Additionally, it highlights the importance of acceptable use policies and privacy policies in managing electronic communications.









![What was the first Virus? In 1988 an employee at the NASA Ames Research Center in California sent a memo by email to his colleagues[citation needed] that read: “We are currently under attack from an Internet VIRUS! It has hit Berkeley, UC San Diego, Lawrence Livermore, Stanford, and NASA Ames.”](https://image.slidesharecdn.com/SafeComputingatHomeandWork-123429119302-phpapp01/85/Safe-Computing-At-Home-And-Work-13-320.jpg)































![Questions and Answers Contact info: John Steensen [email_address] 925-413-6379](https://image.slidesharecdn.com/SafeComputingatHomeandWork-123429119302-phpapp01/85/Safe-Computing-At-Home-And-Work-55-320.jpg)