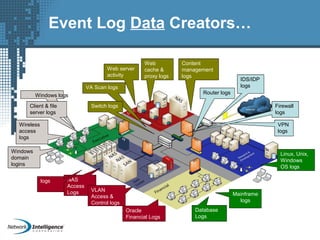
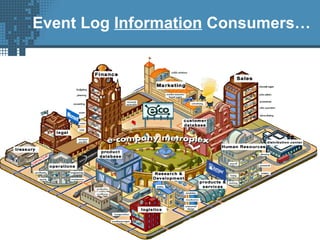
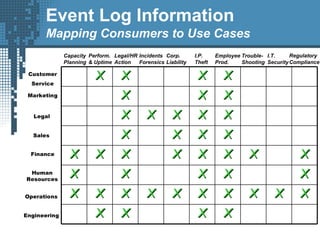
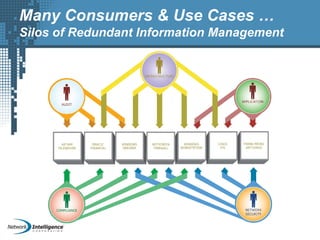
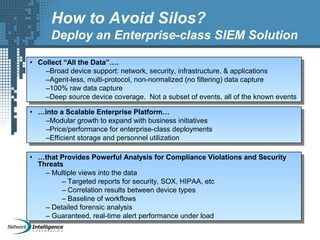
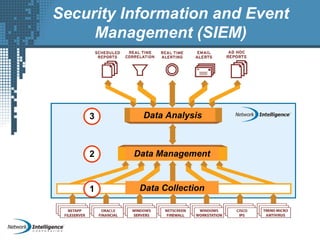
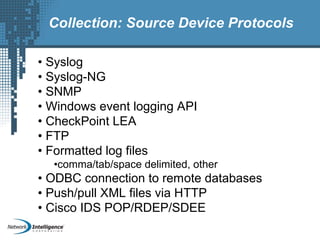
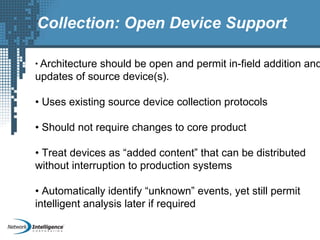
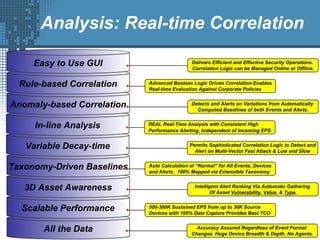
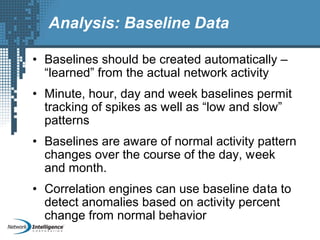
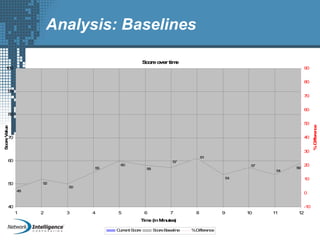
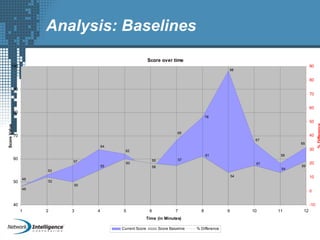
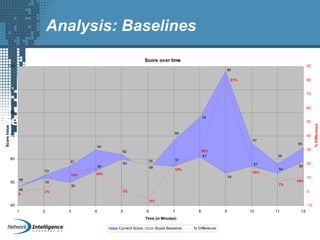
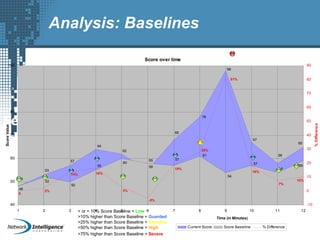
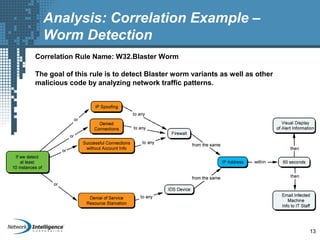
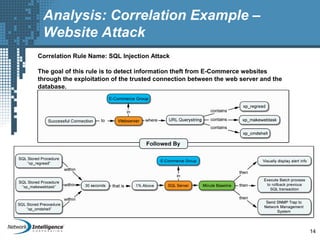
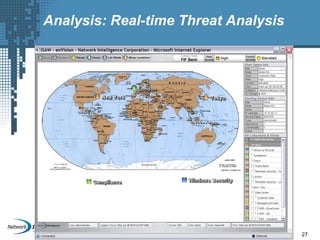
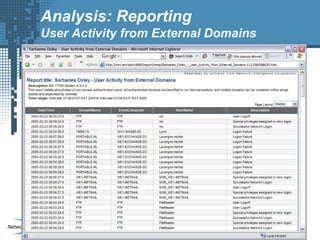
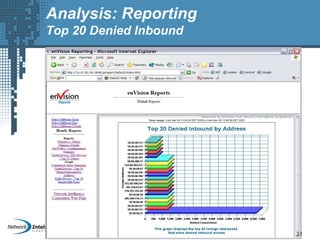
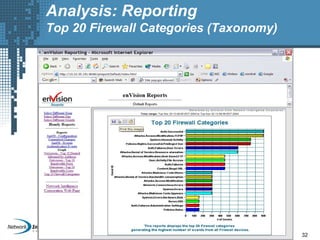
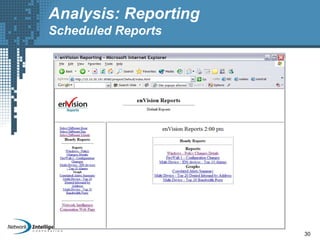
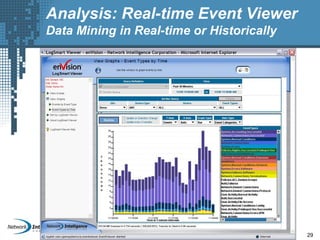
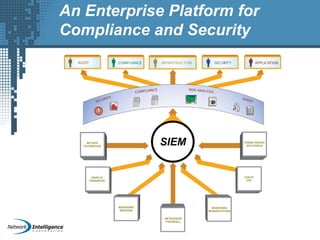
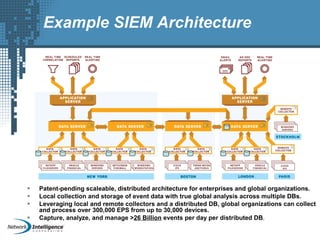
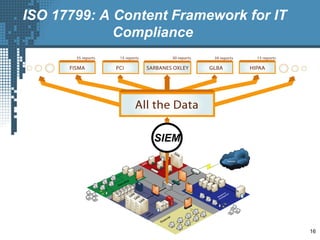
An SIEM solution provides the ability to collect, analyze, and manage log data from across an organization. It can collect data from various sources using different protocols and store large volumes of raw data in a scalable platform. This centralized log management allows organizations to generate insightful reports, detect threats in real-time, investigate incidents, ensure compliance, and more. By automatically learning baselines of normal activity, an SIEM can detect anomalies and prioritize the most critical alerts. Its analytics capabilities like correlation rules and taxonomy-driven classification further enhance threat detection and security operations.