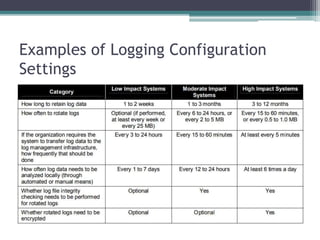
Logs record events within an organization's systems and networks. Log management is important for identifying security incidents, policy violations, and operational problems by routinely analyzing logs. However, log management faces challenges including balancing resources with increasing log data, inconsistent log content and formats, and protecting log confidentiality and integrity. Proper log management requires prioritizing it, establishing policies, maintaining secure infrastructure, and training staff.