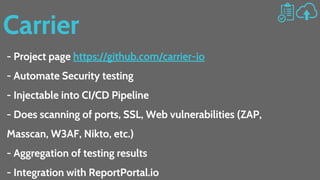
The document discusses web security strategies, emphasizing the importance of a security-aware culture and continuous security practices within organizations. It outlines various techniques and tools for identifying vulnerabilities and enhancing security, such as using secure connections, keeping software updated, and performing thorough audits. Furthermore, it highlights the significant economic impact of cybercrime and provides references for further resources on web security.