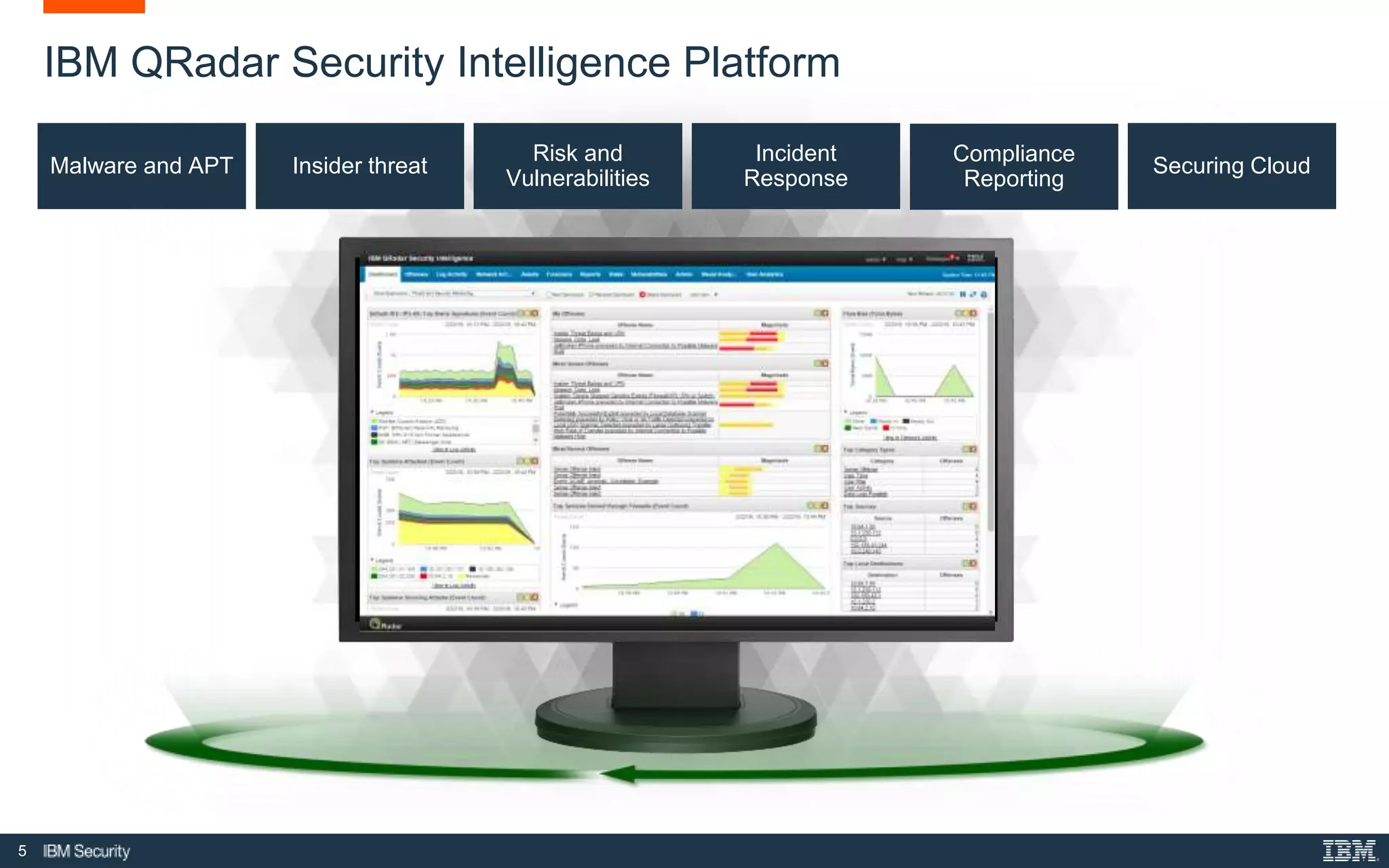
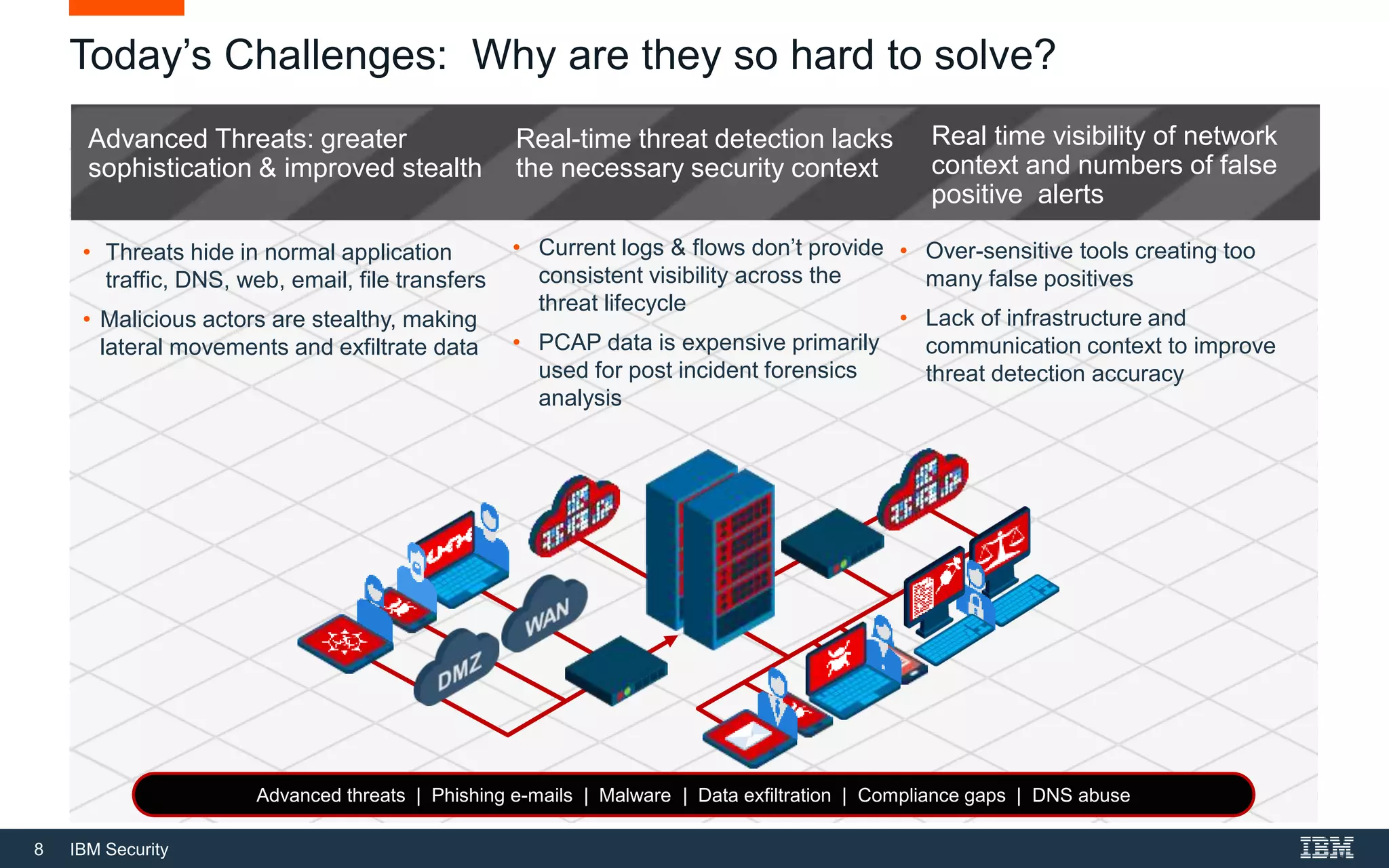
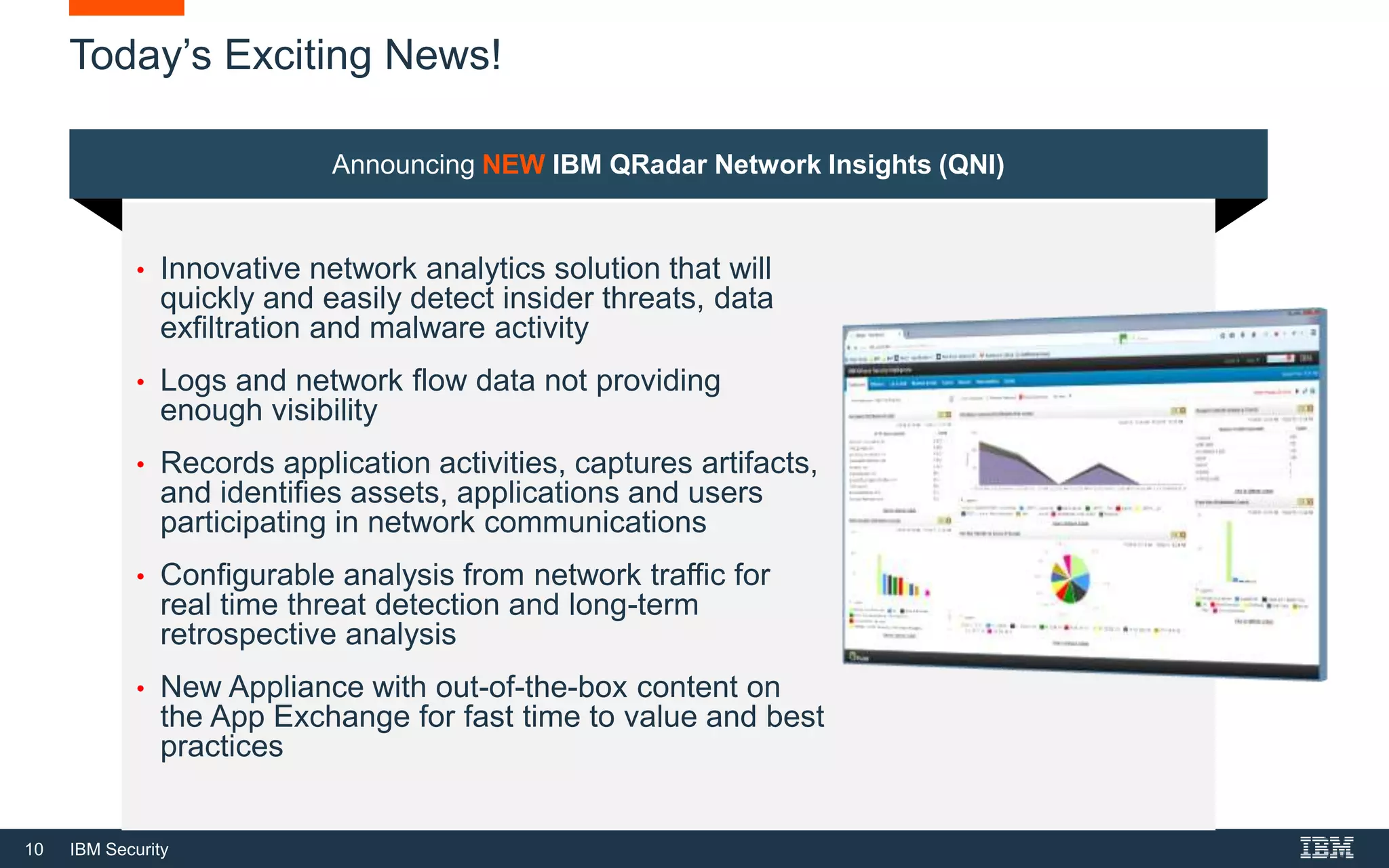
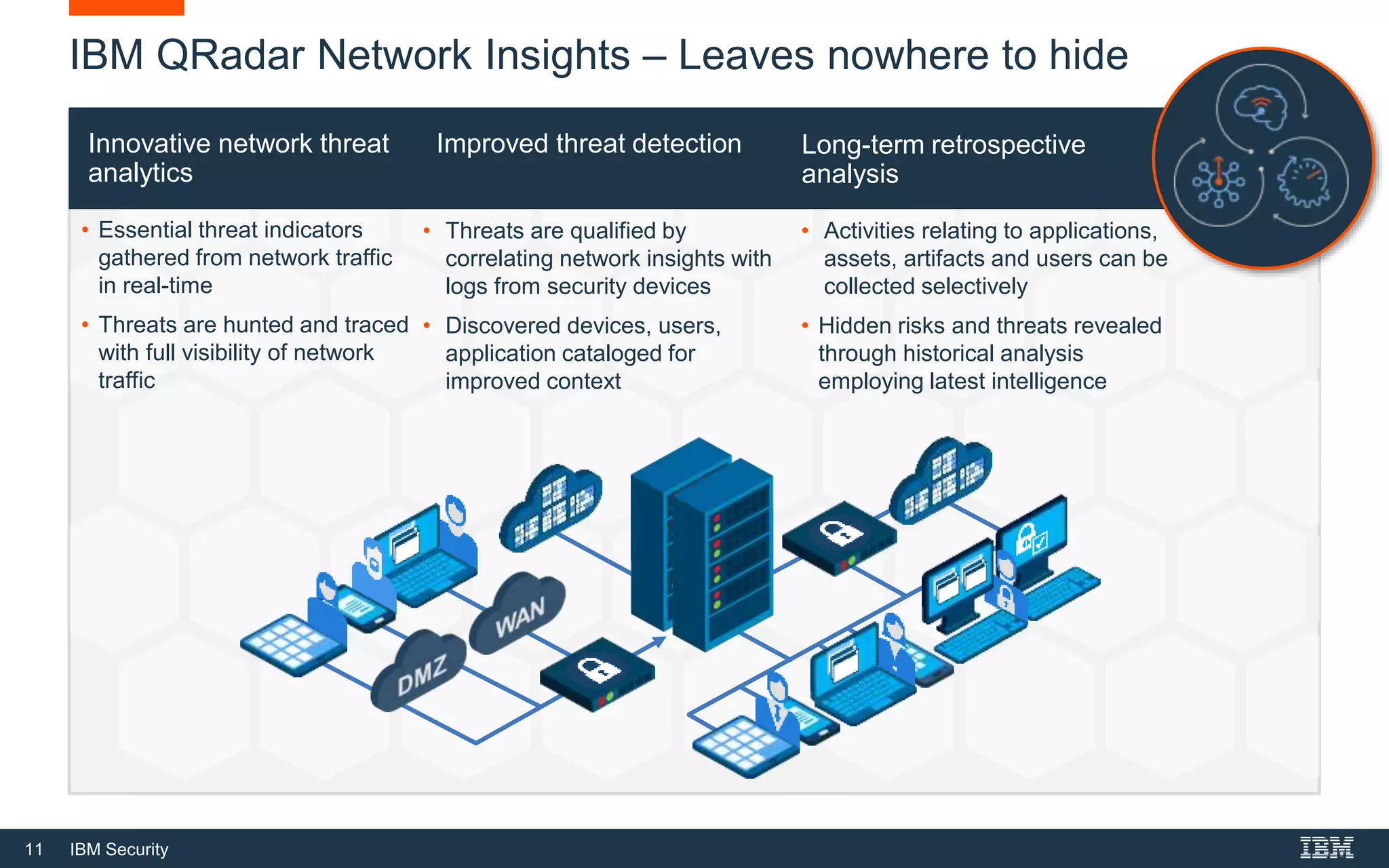
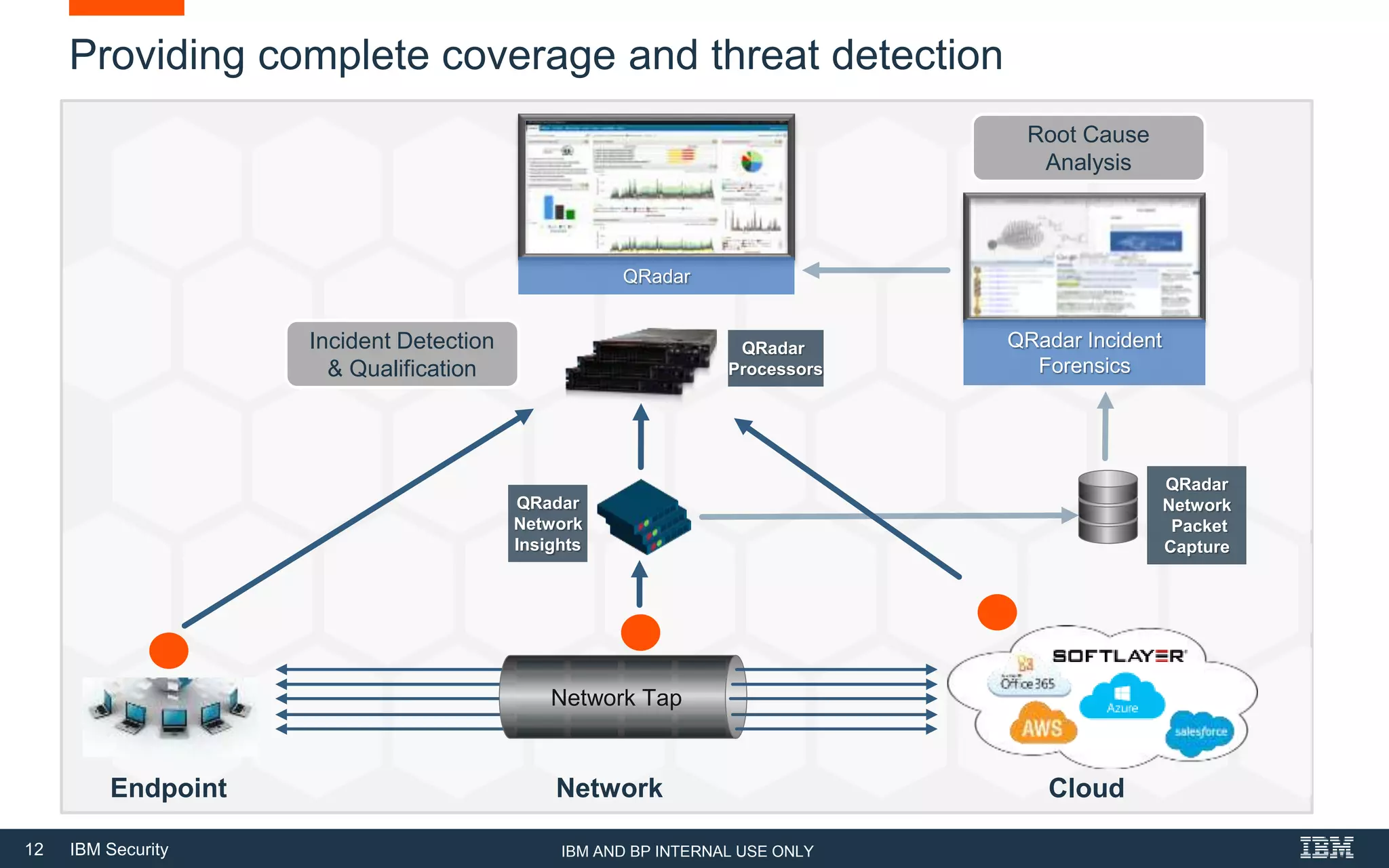
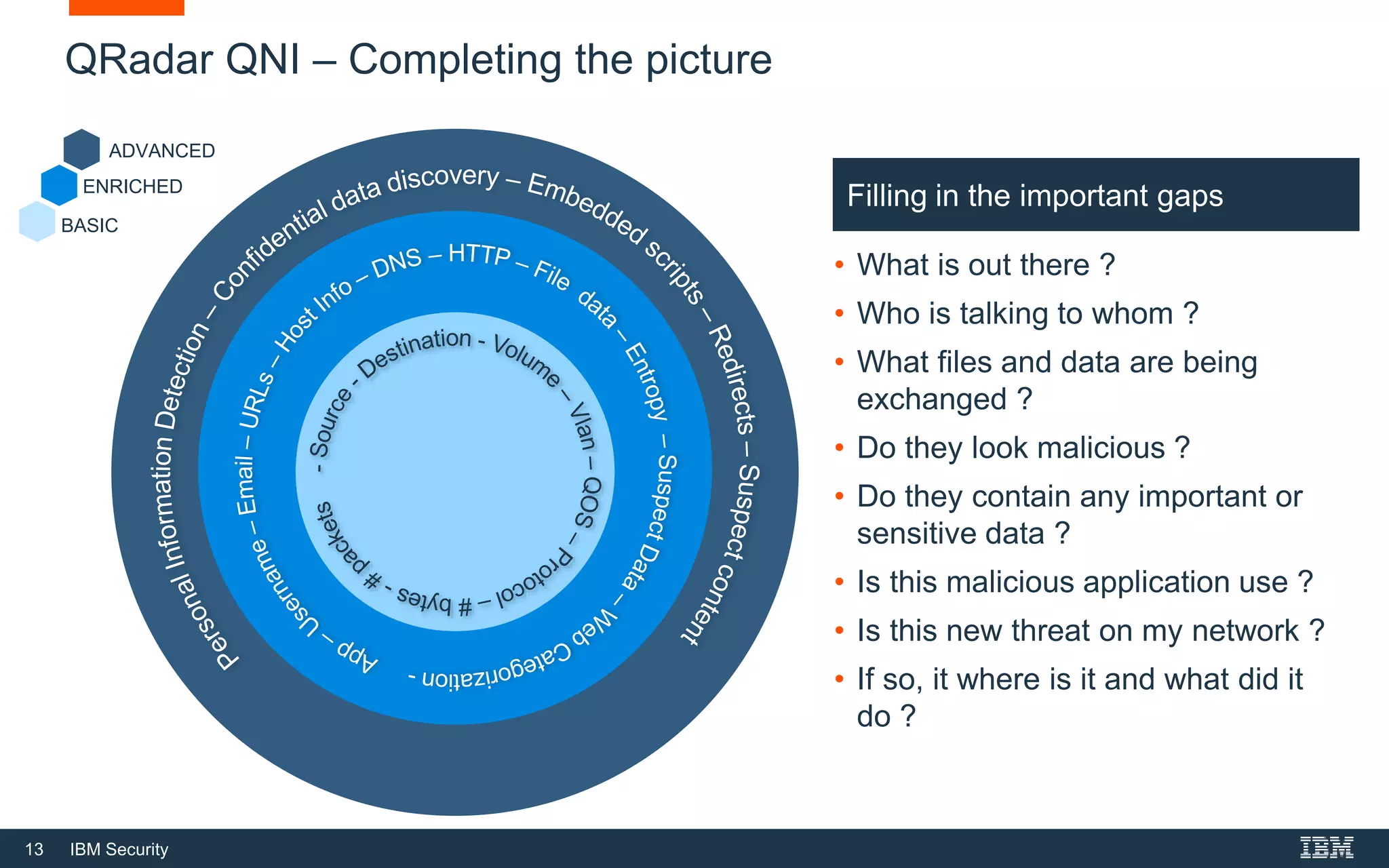
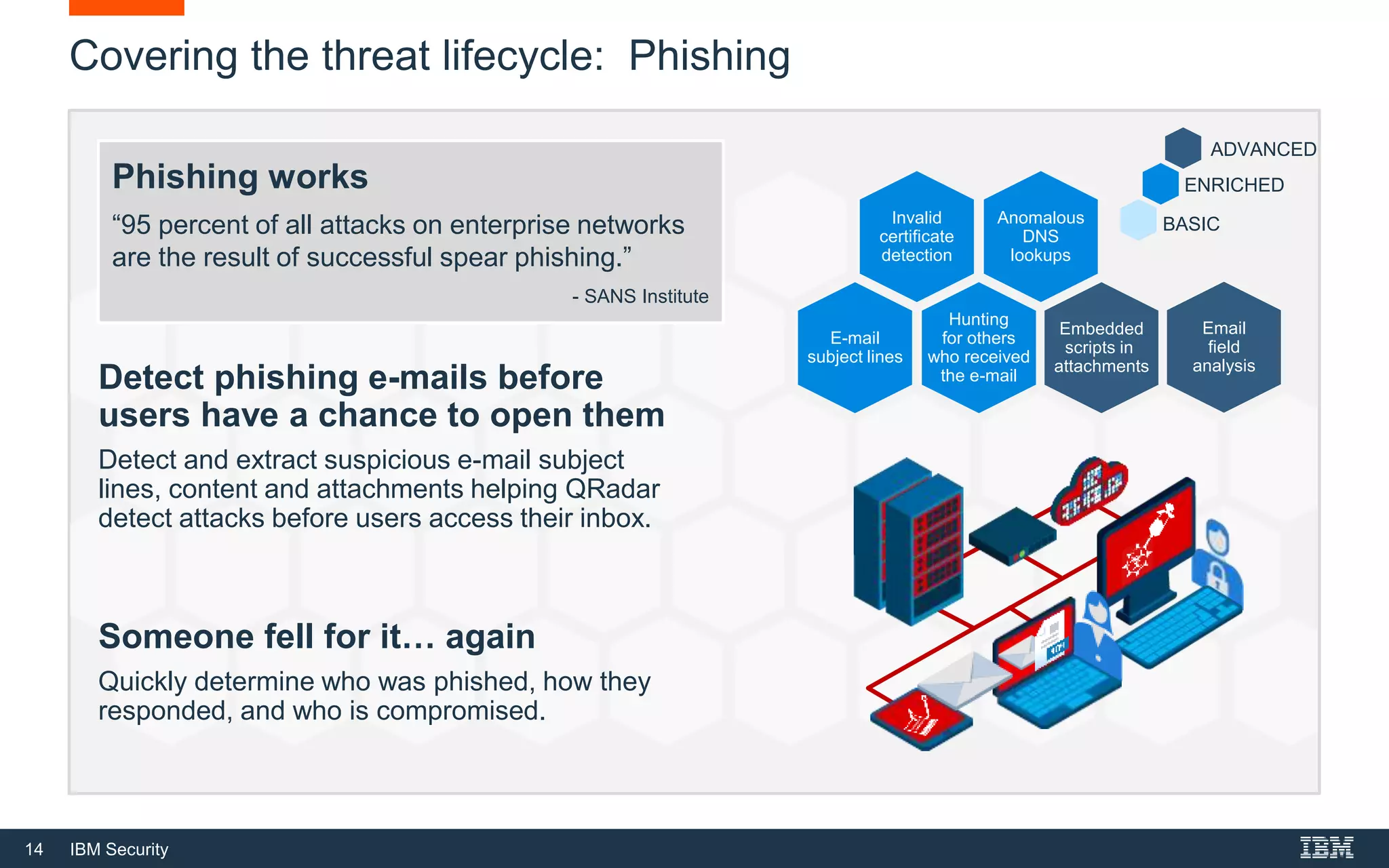
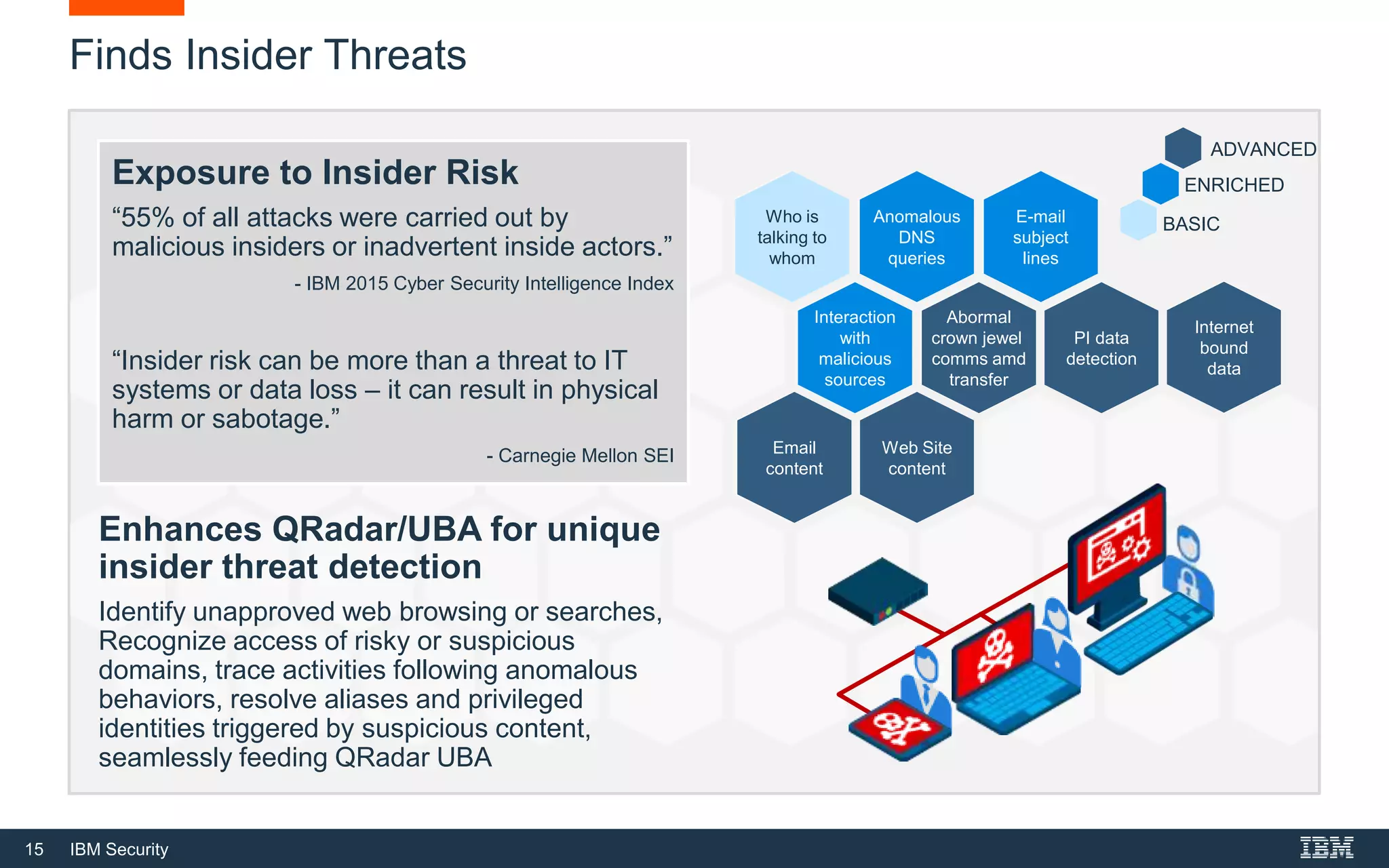
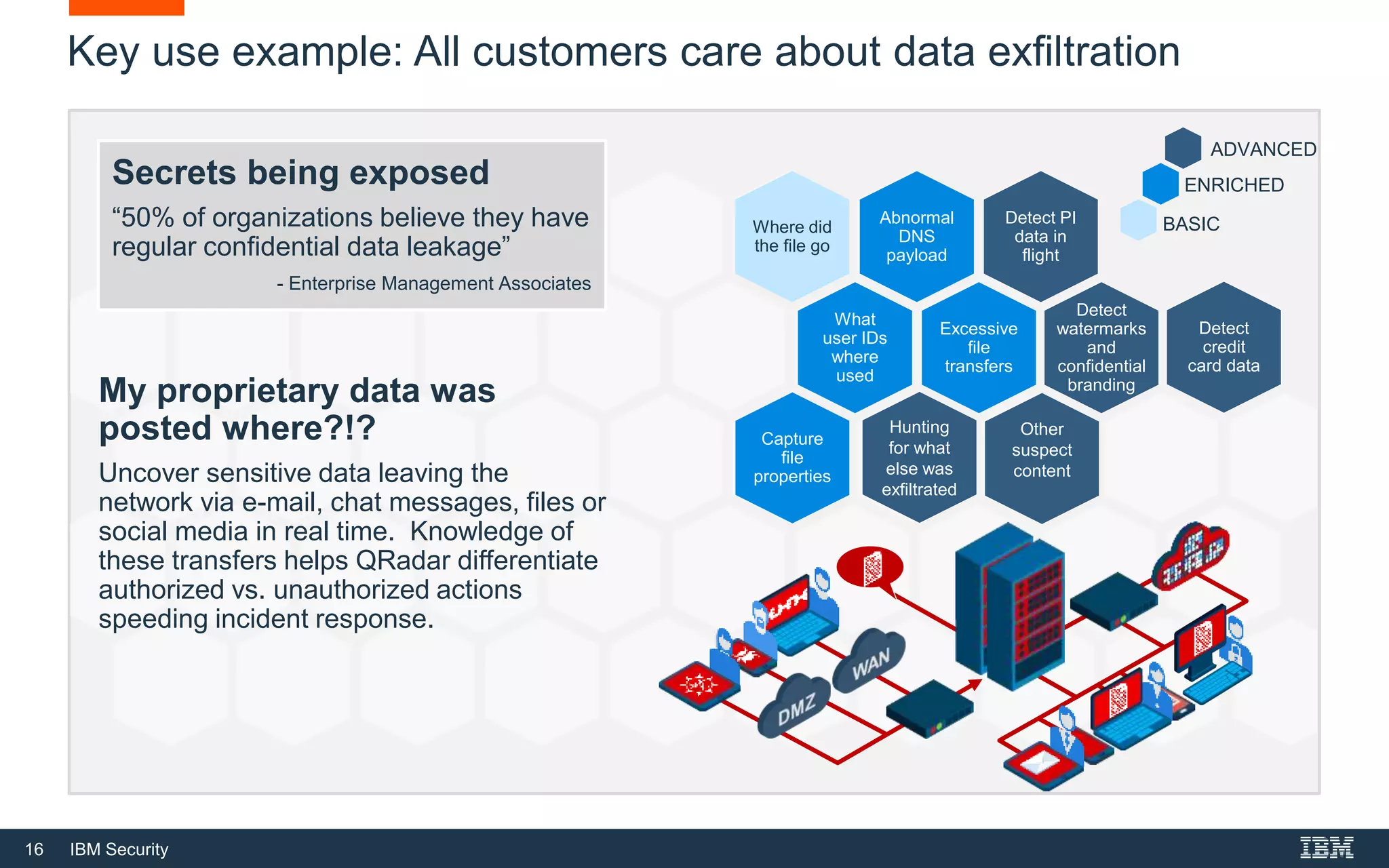
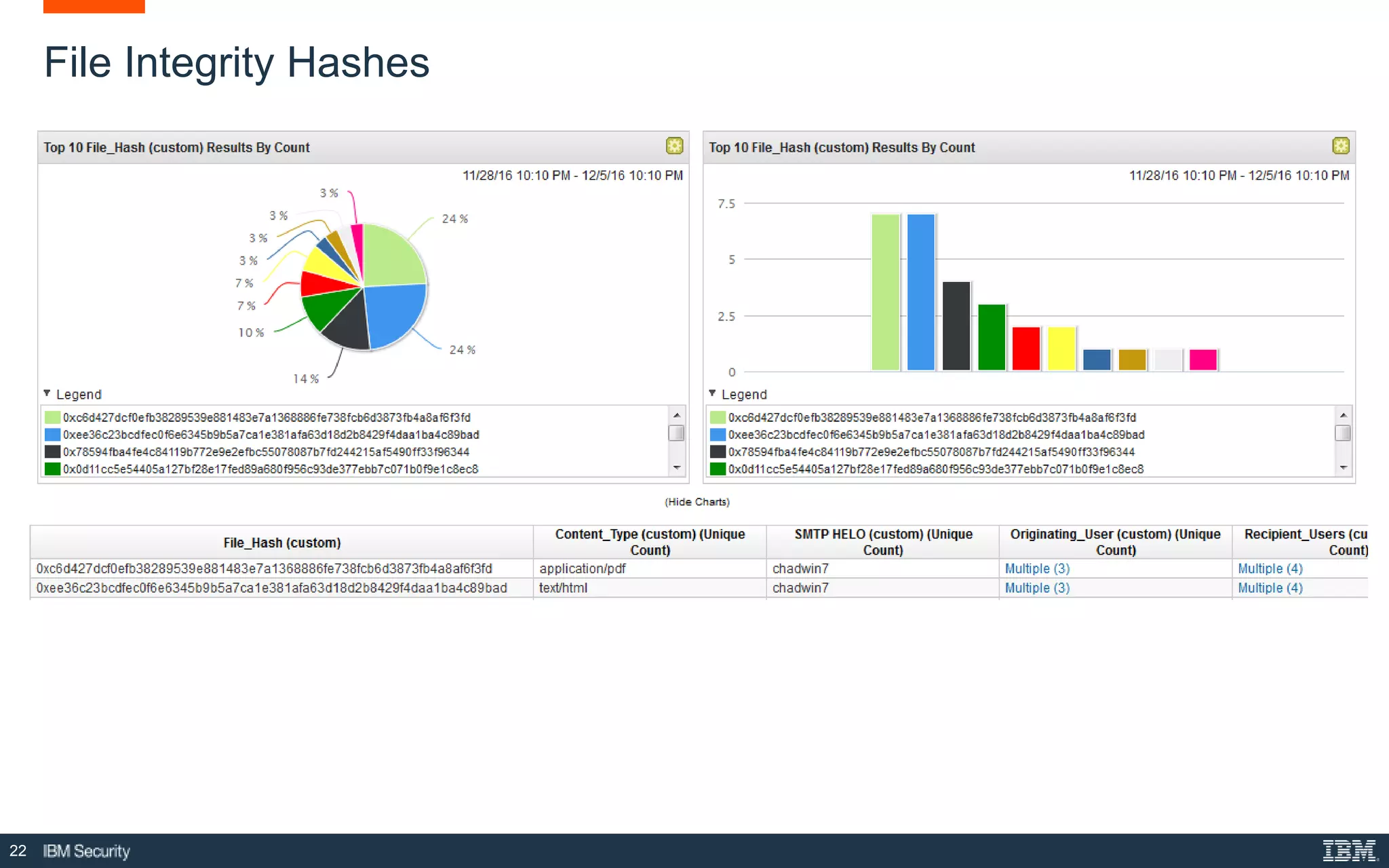
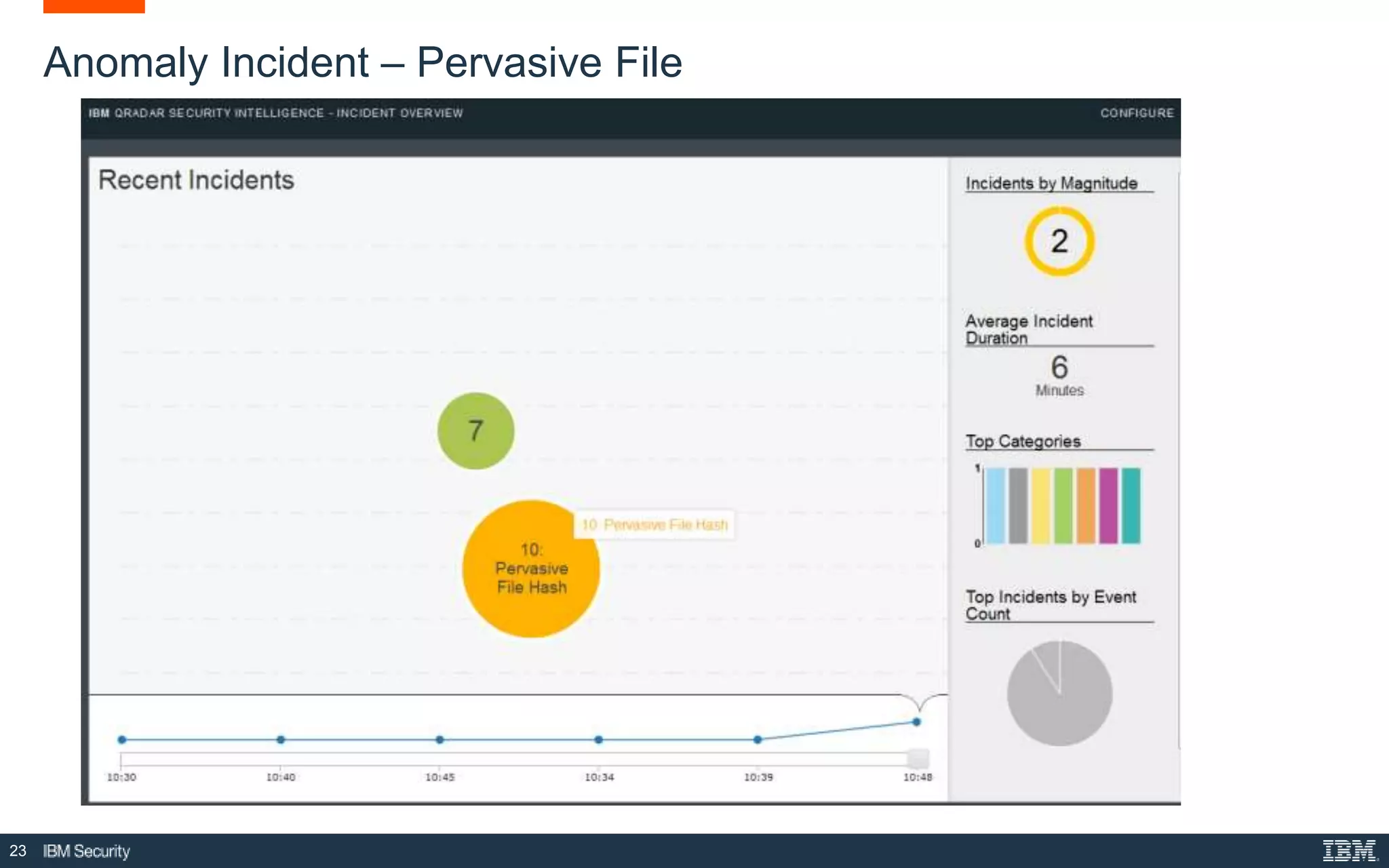
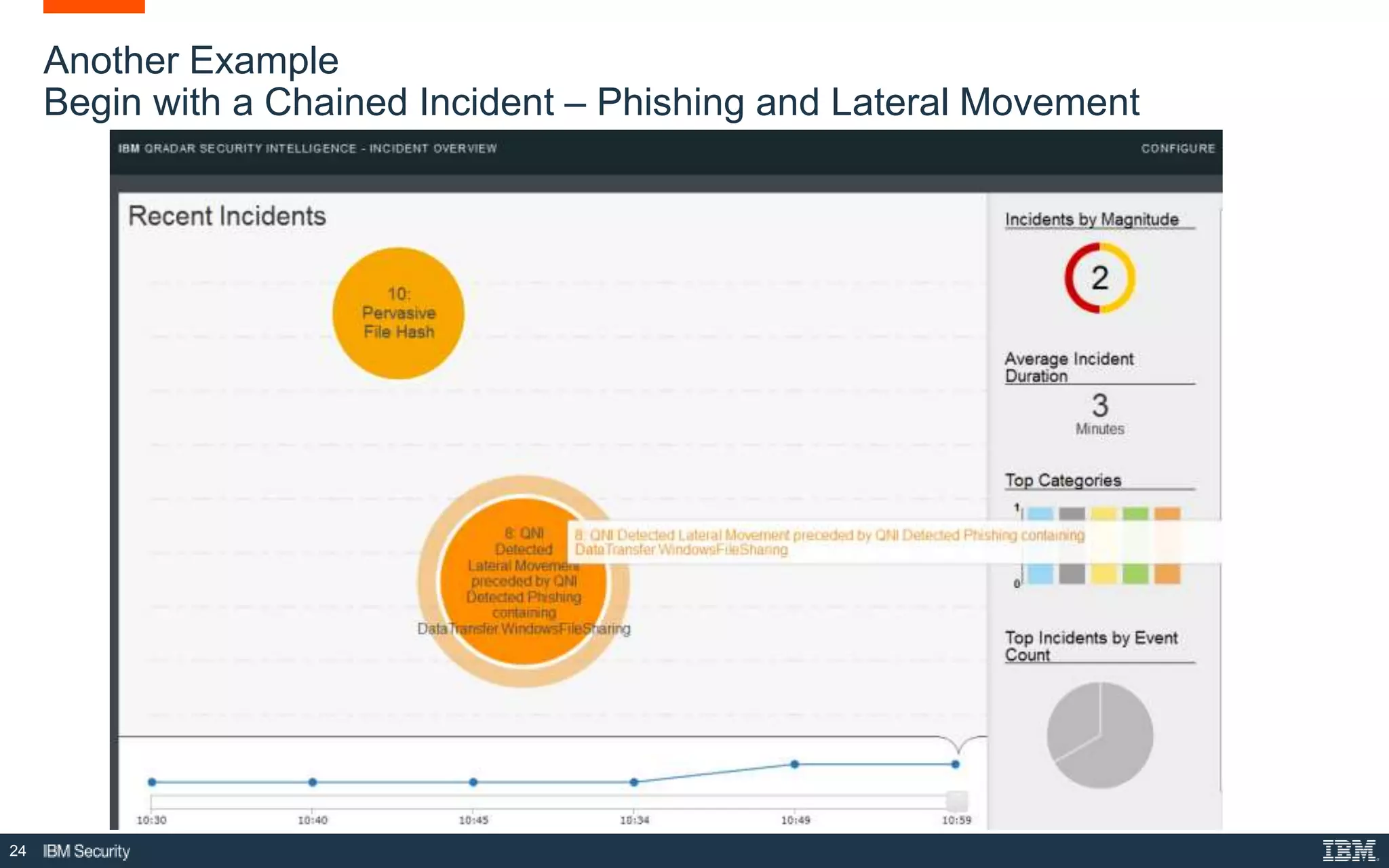
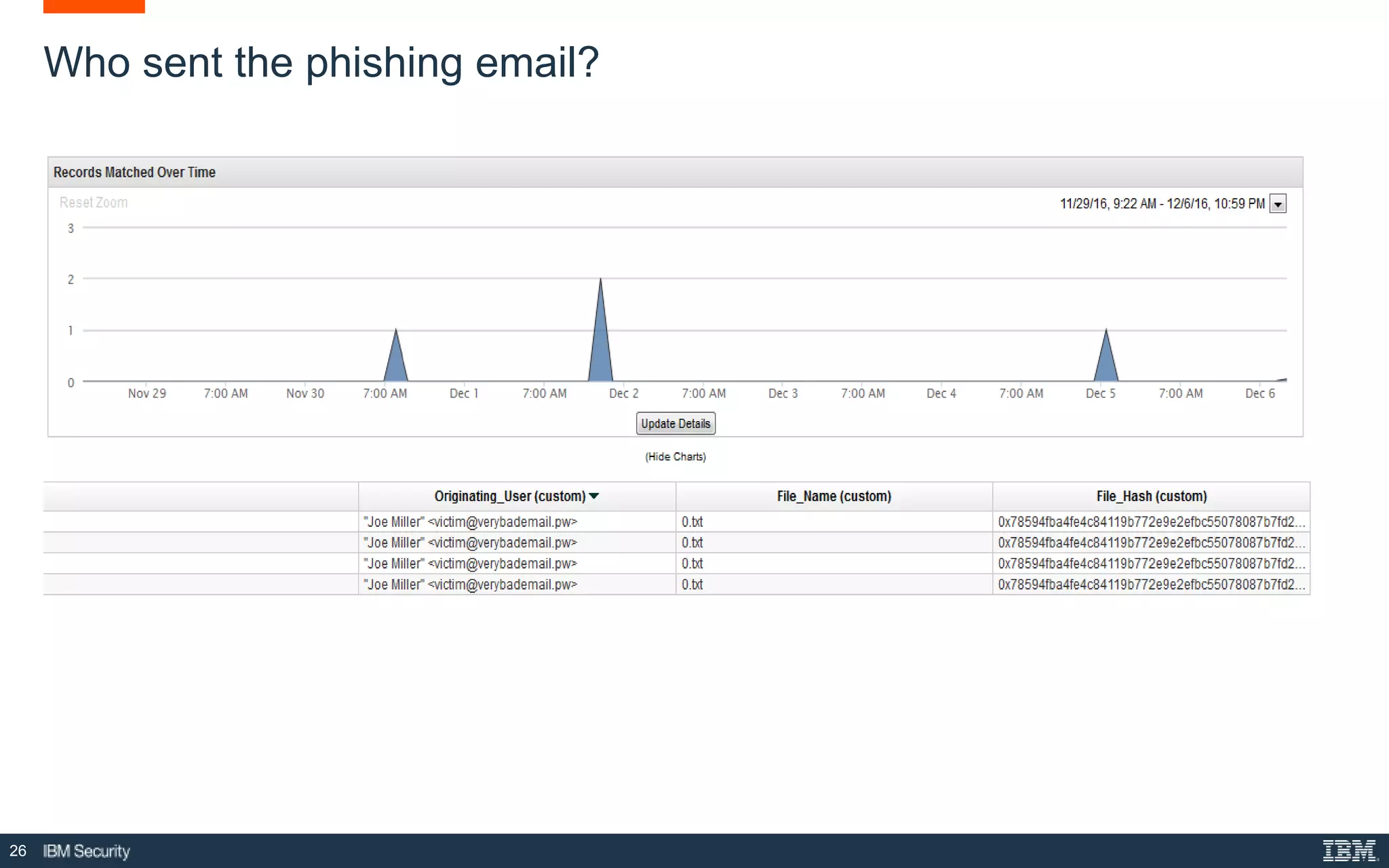
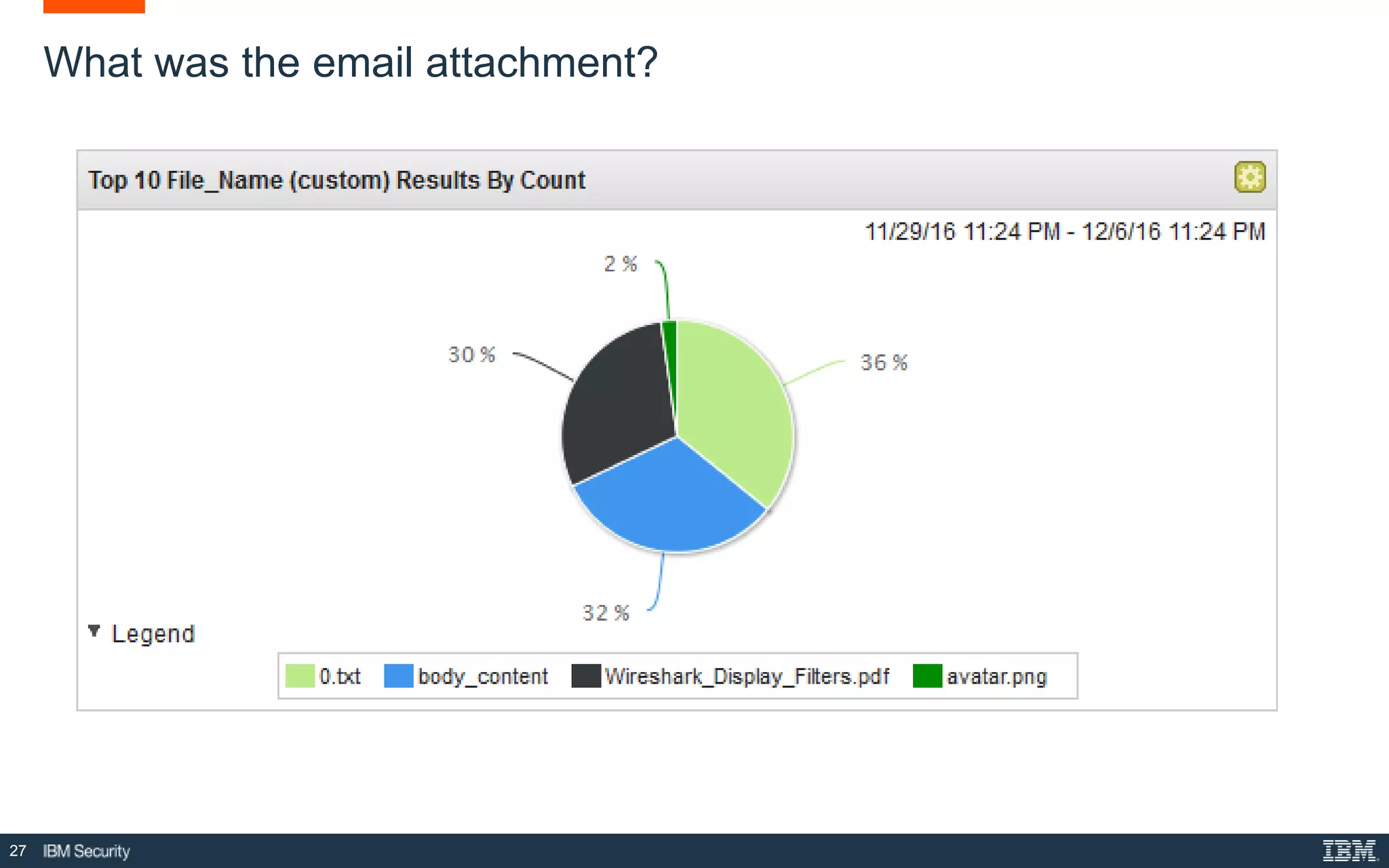
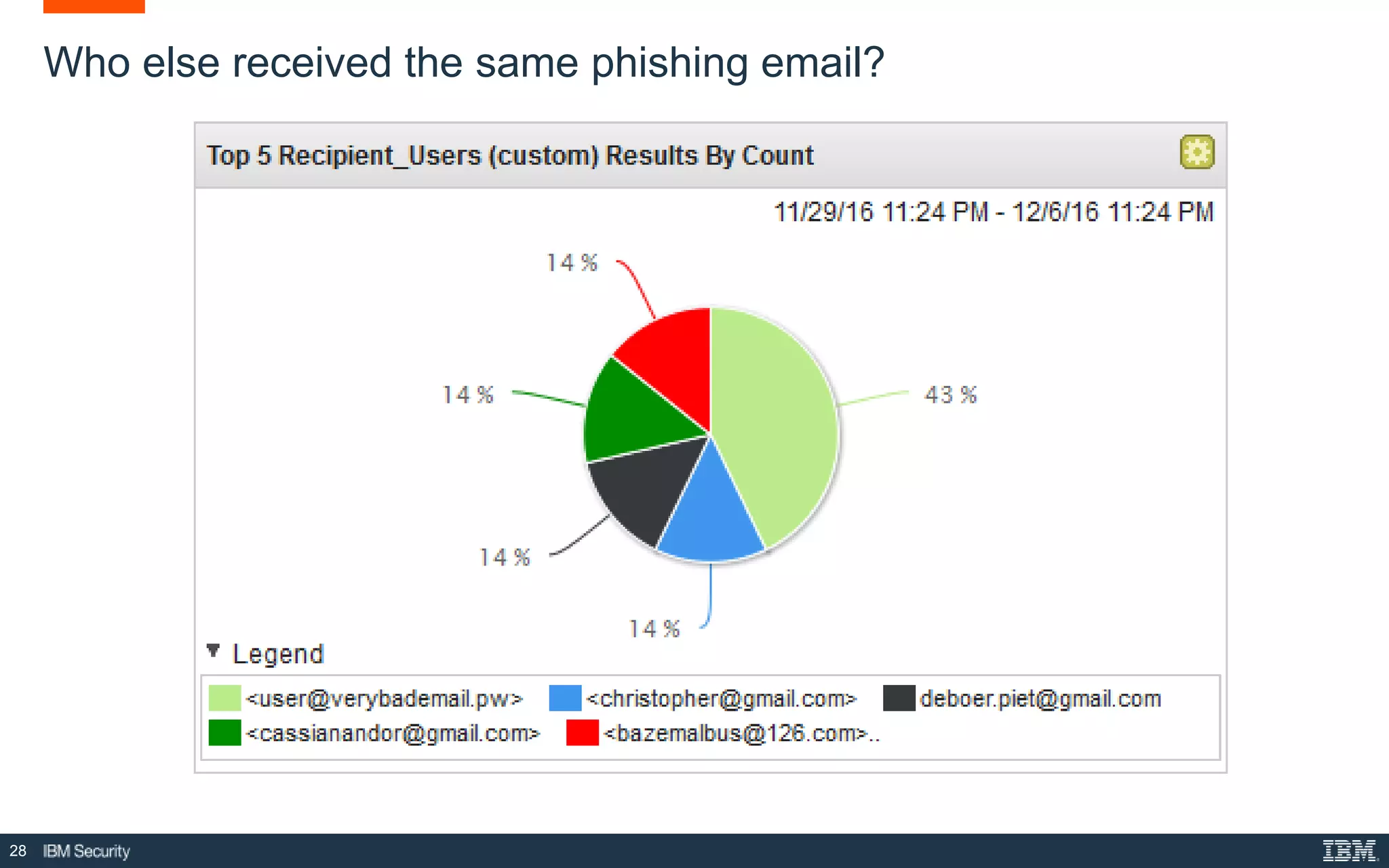
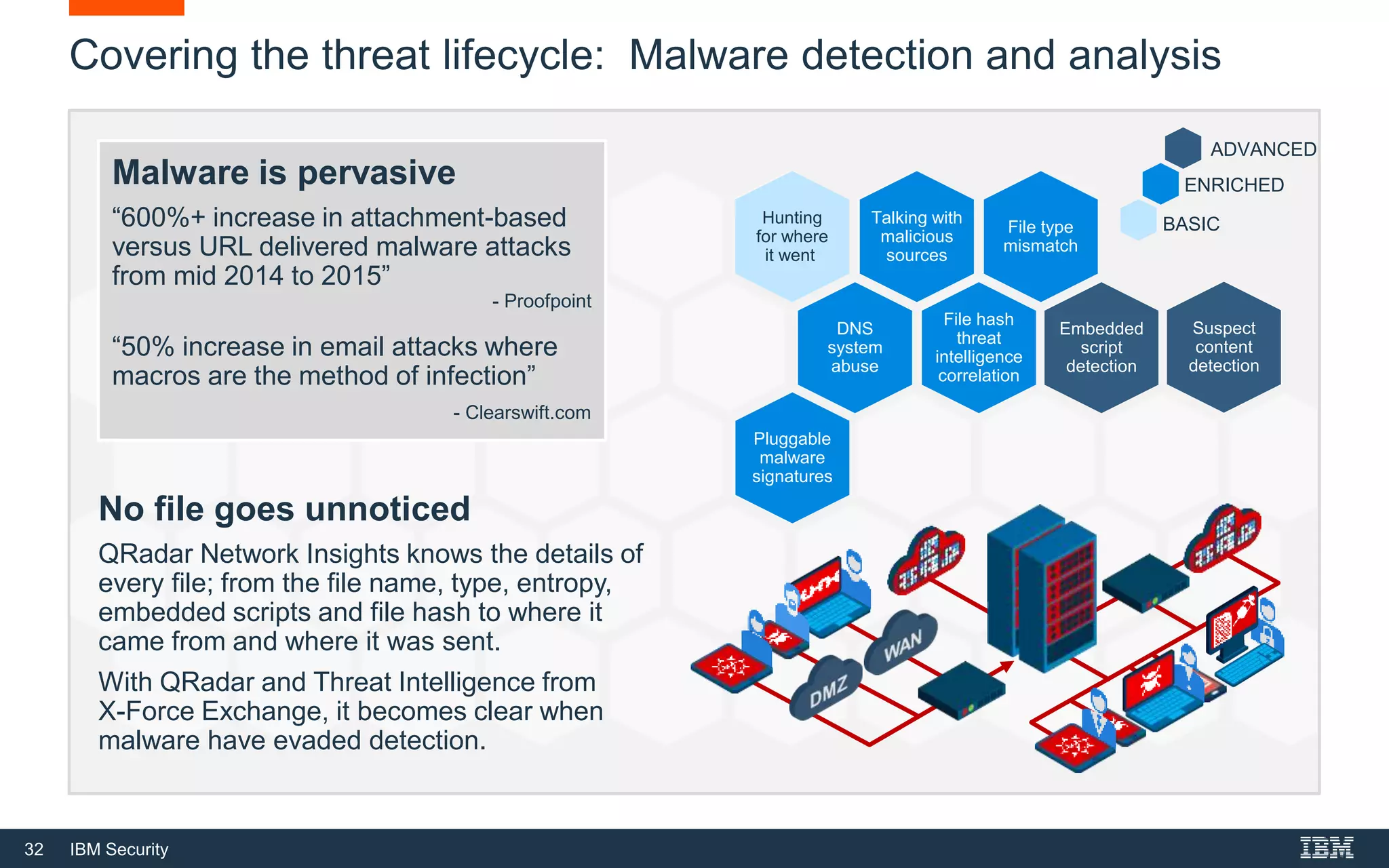
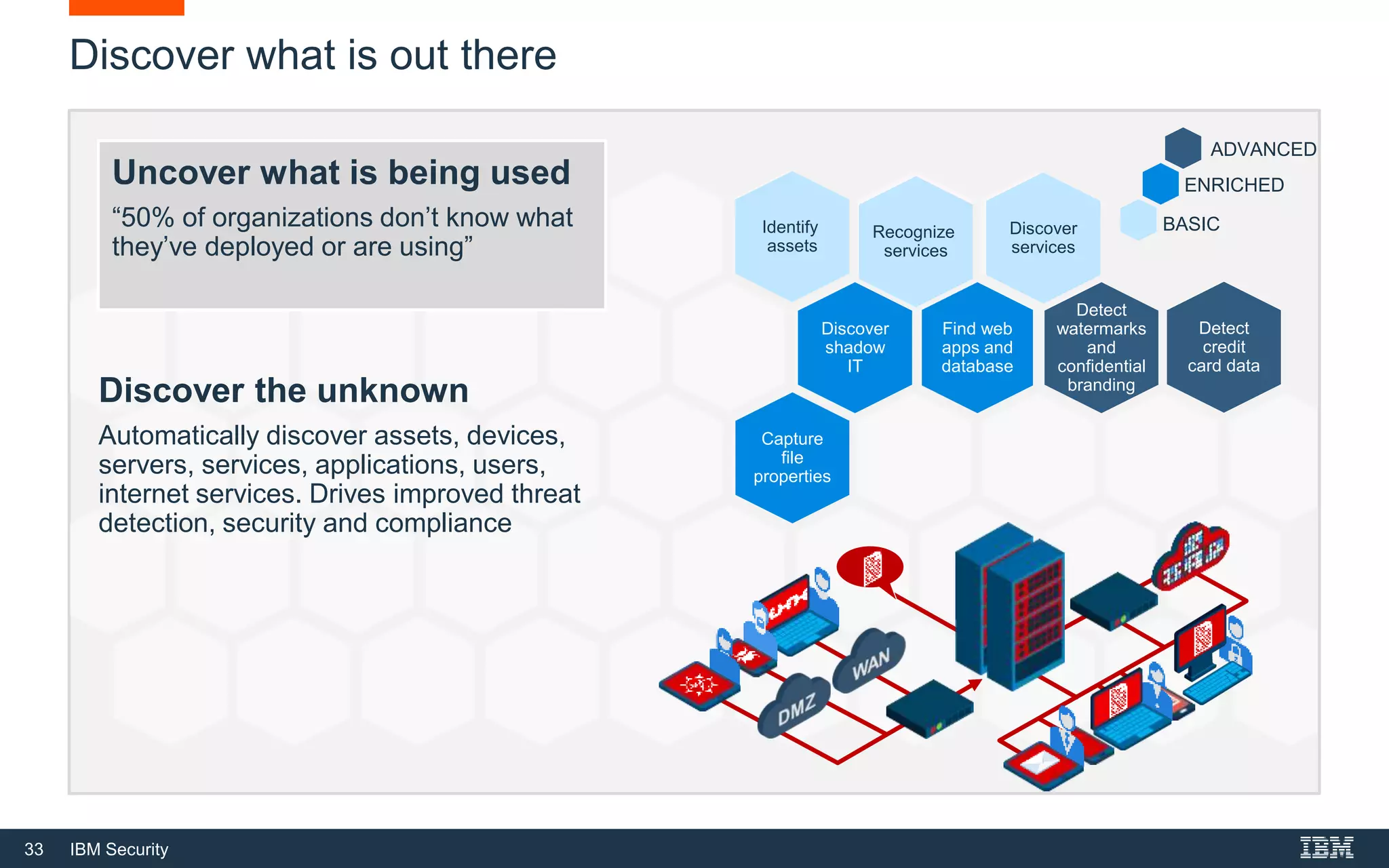
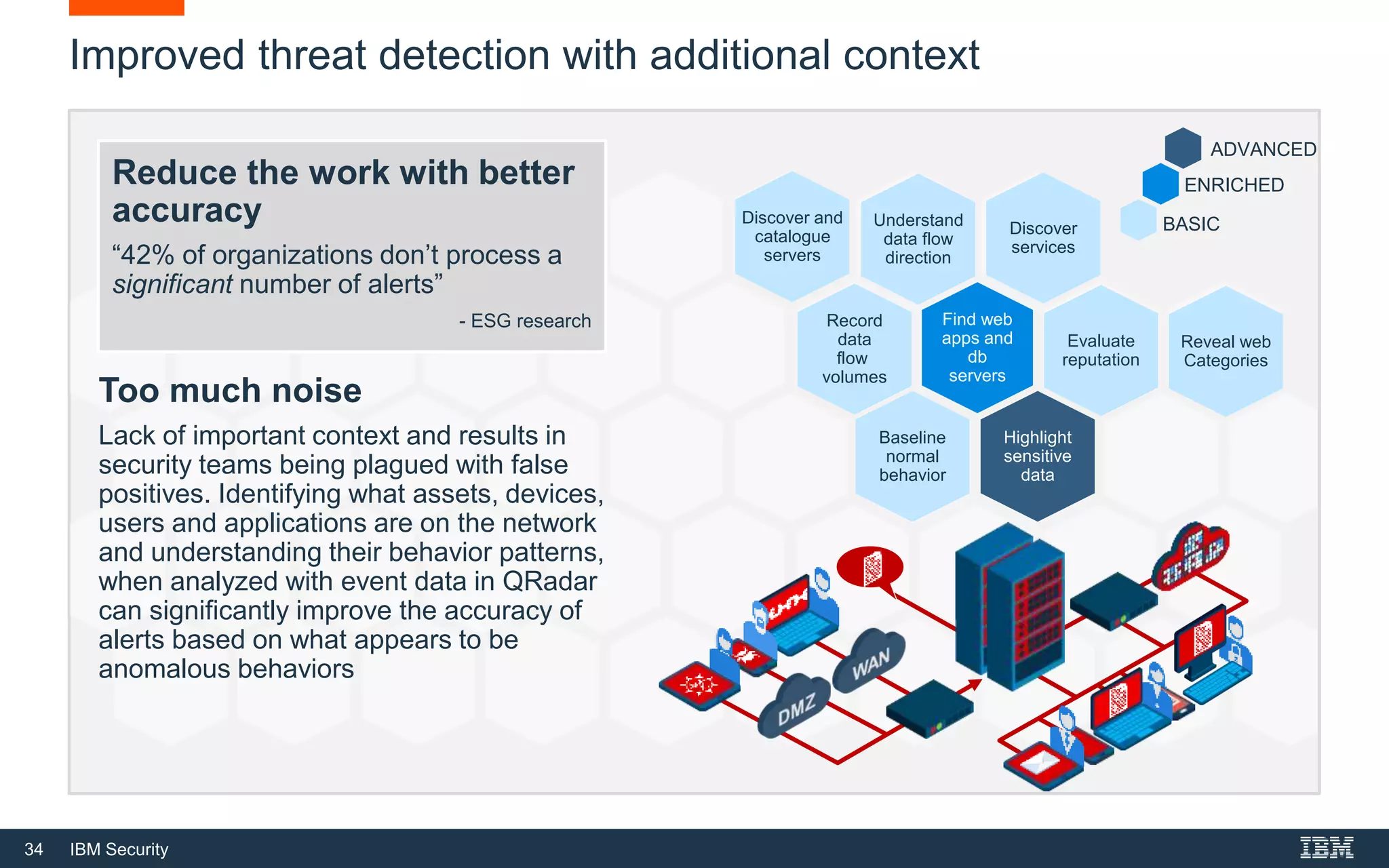
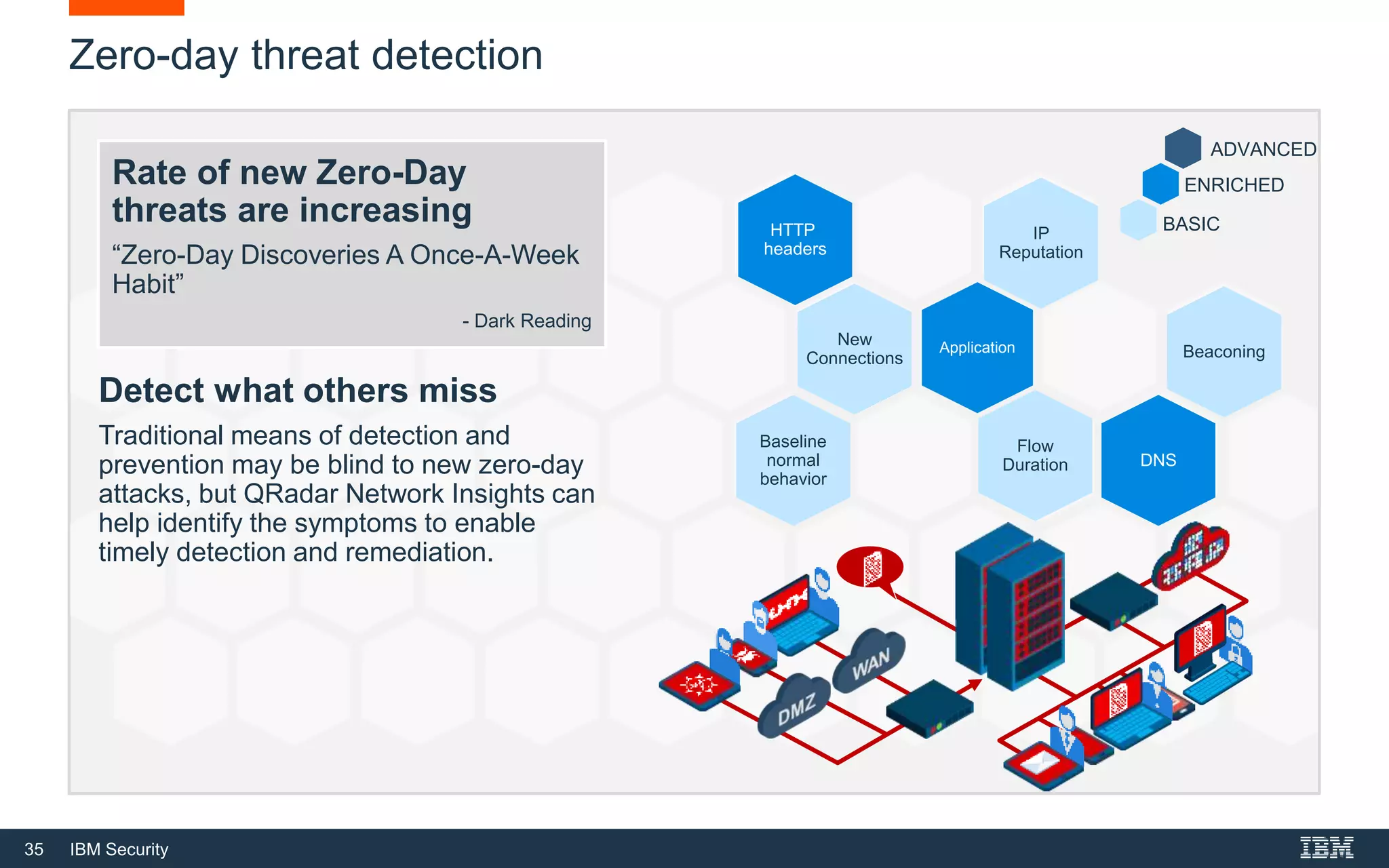
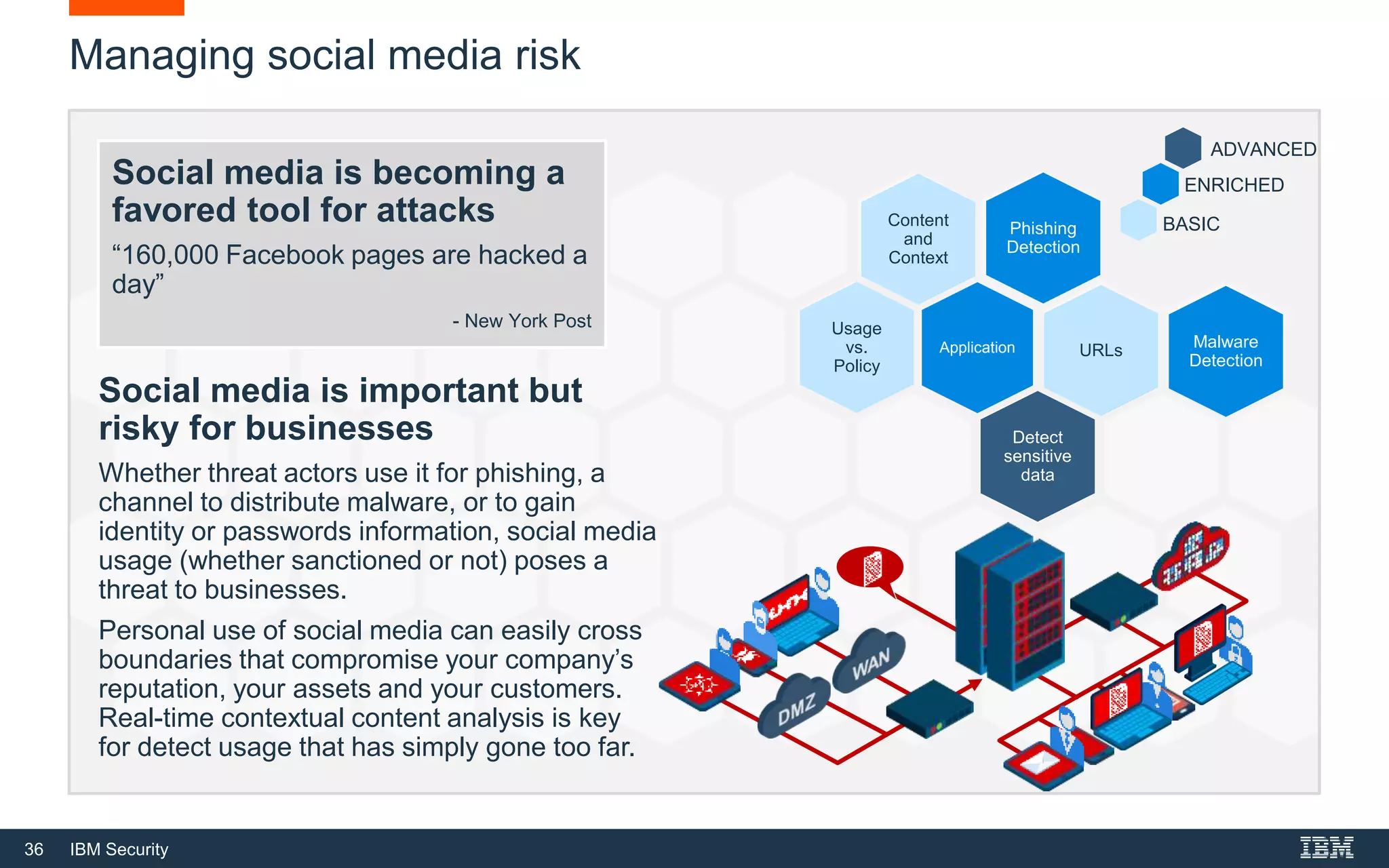
The document presents IBM QRadar Network Insights, a security analytics solution designed to enhance real-time detection of insider threats, malware, and data exfiltration. It addresses contemporary cybersecurity challenges by providing comprehensive visibility and actionable insights into network traffic and user behaviors. The platform combines advanced analytics with automated discovery to improve incident response and threat detection accuracy.