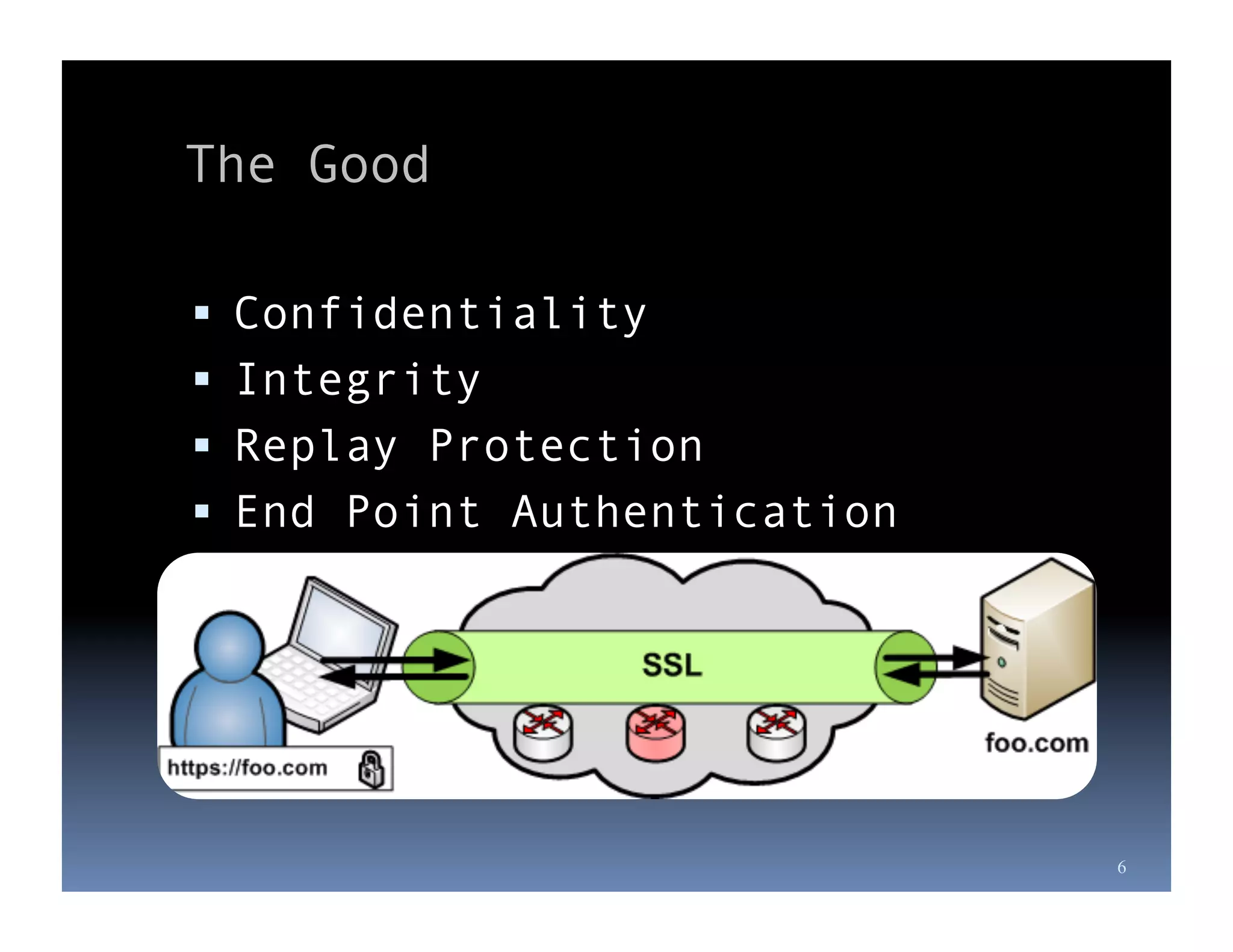
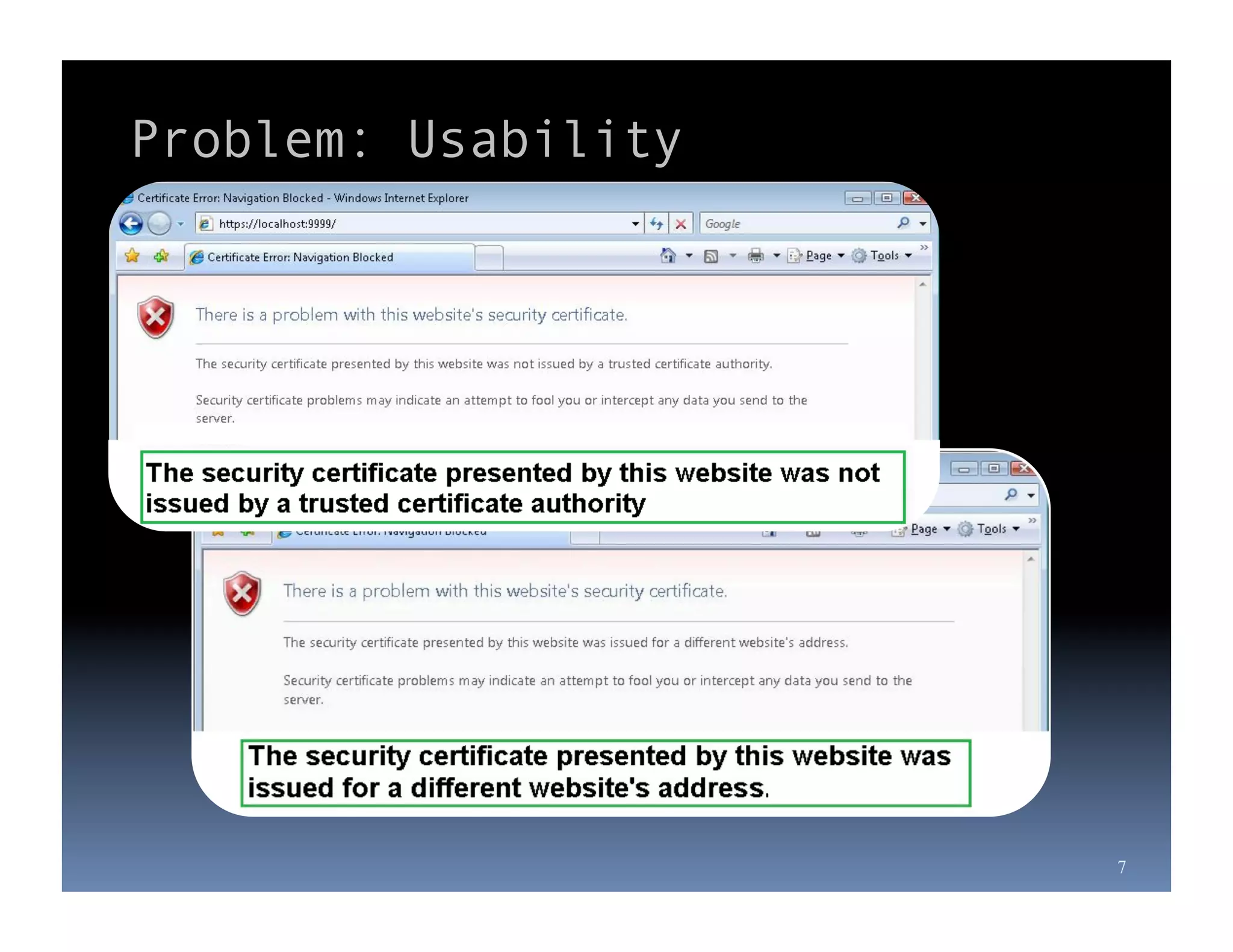
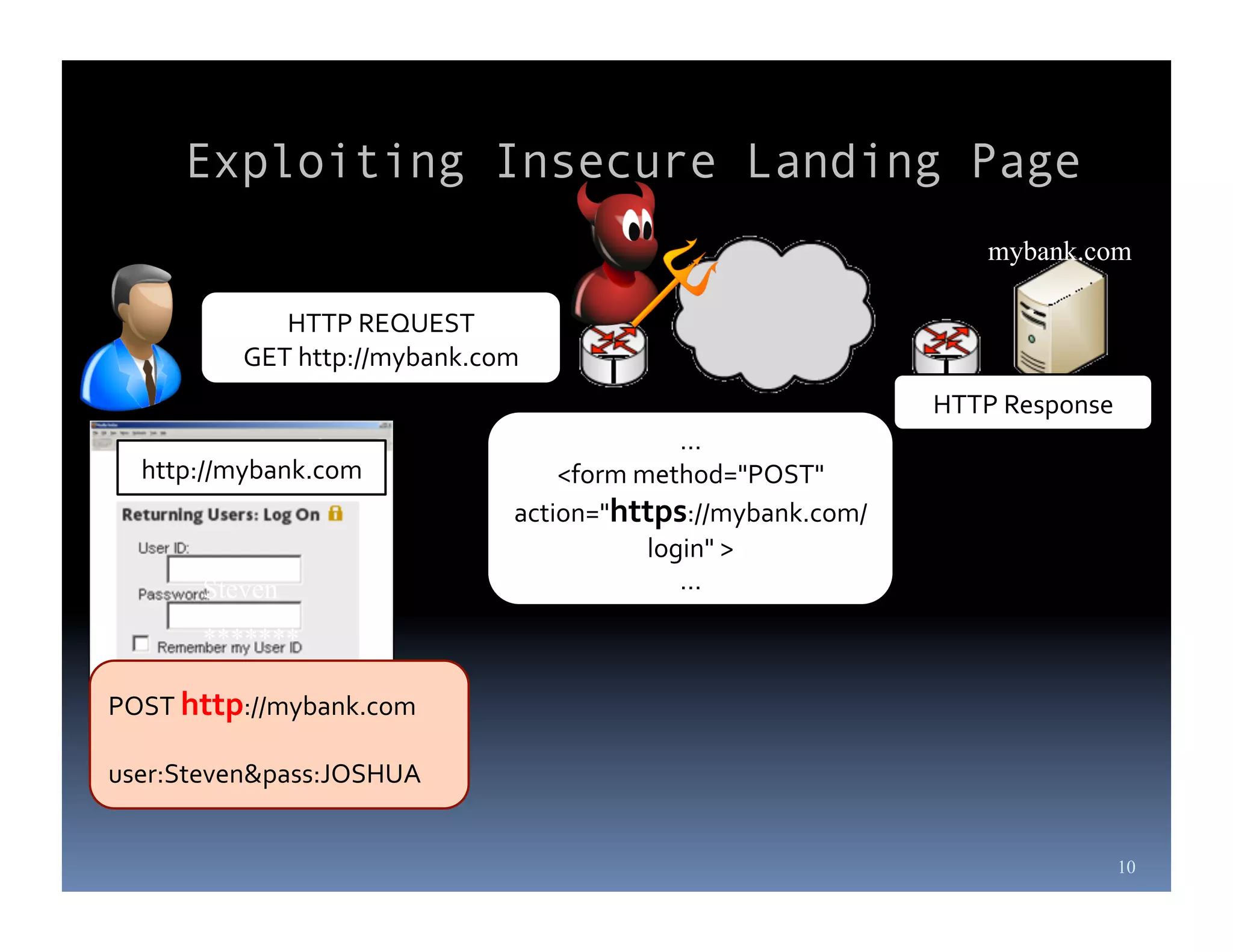
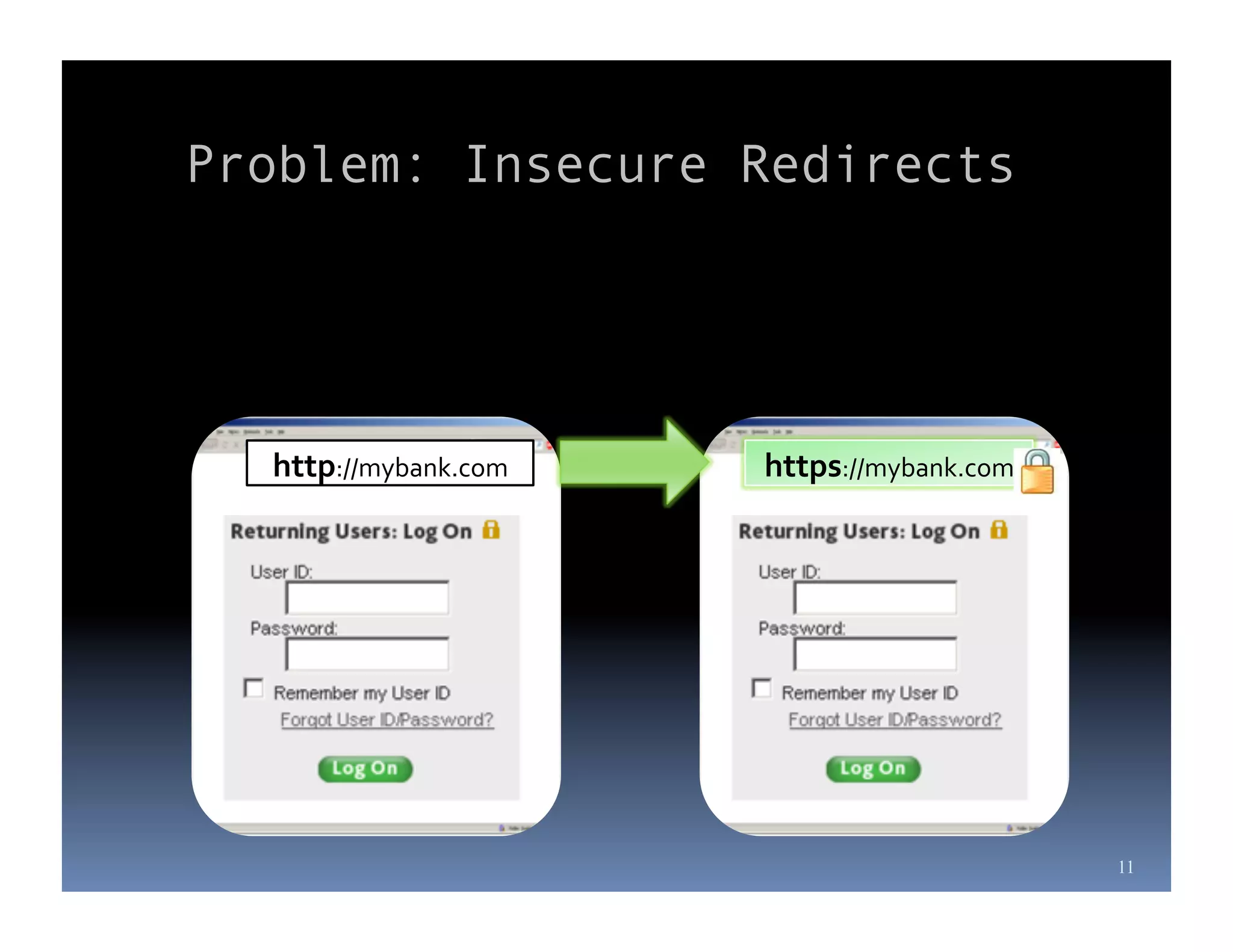
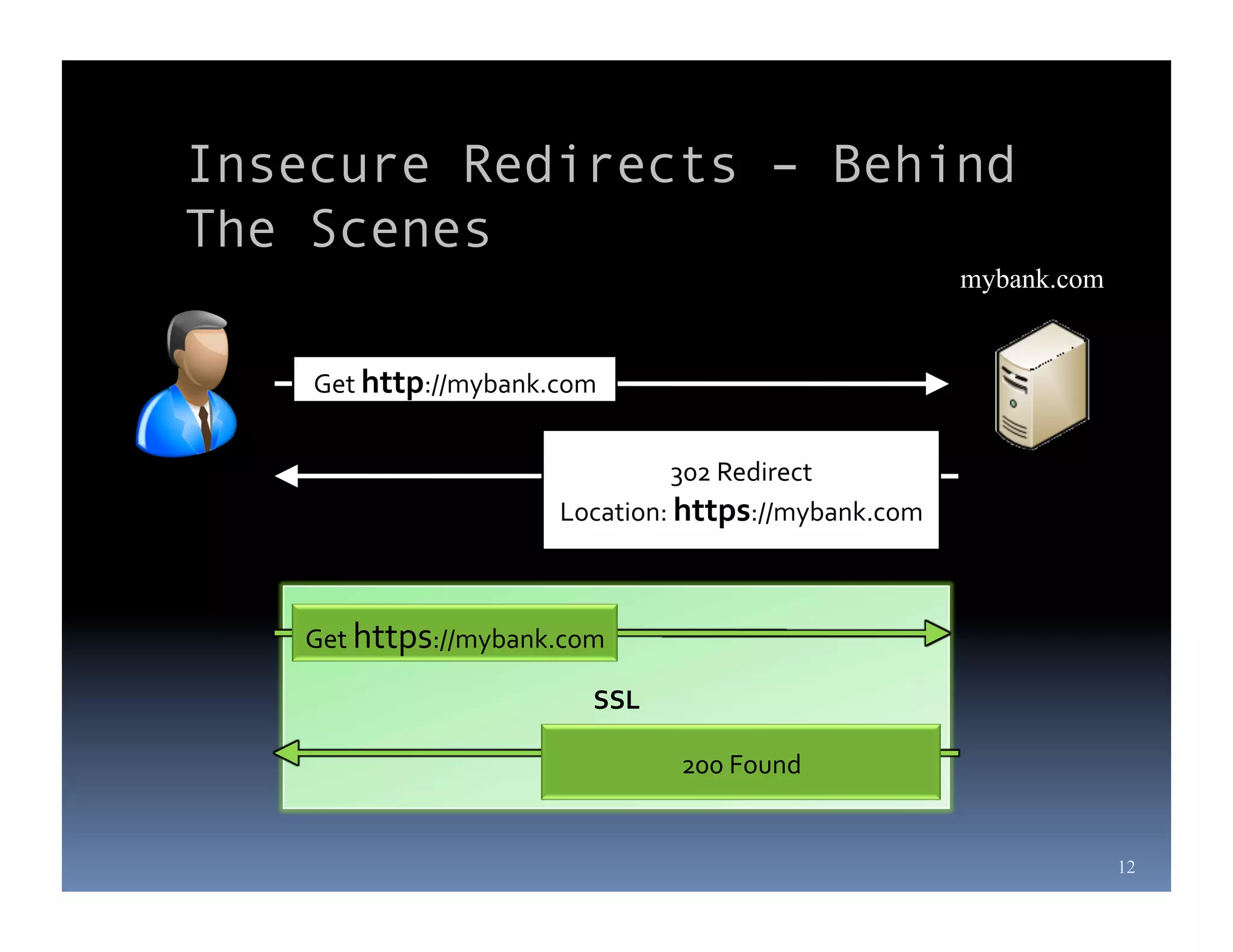
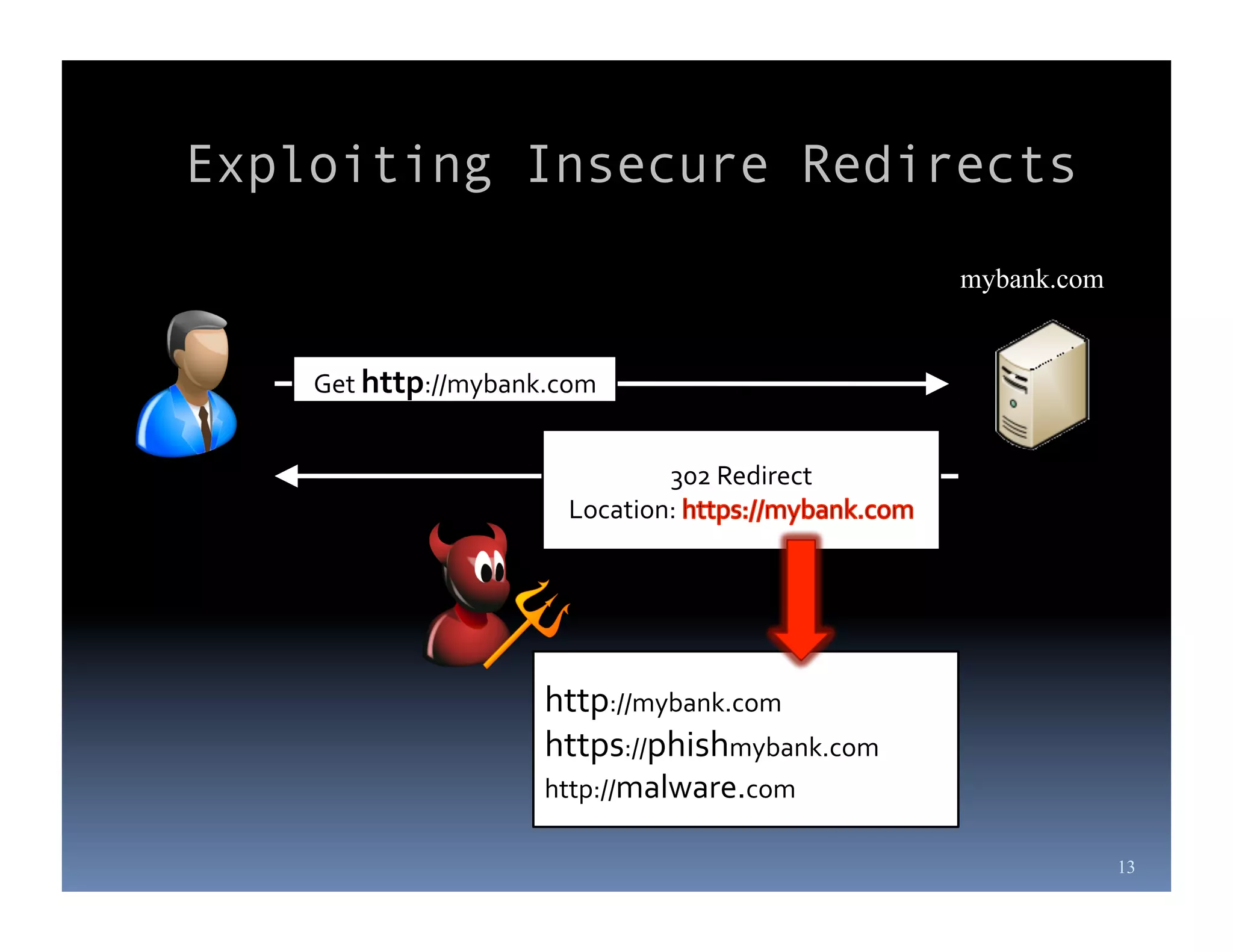
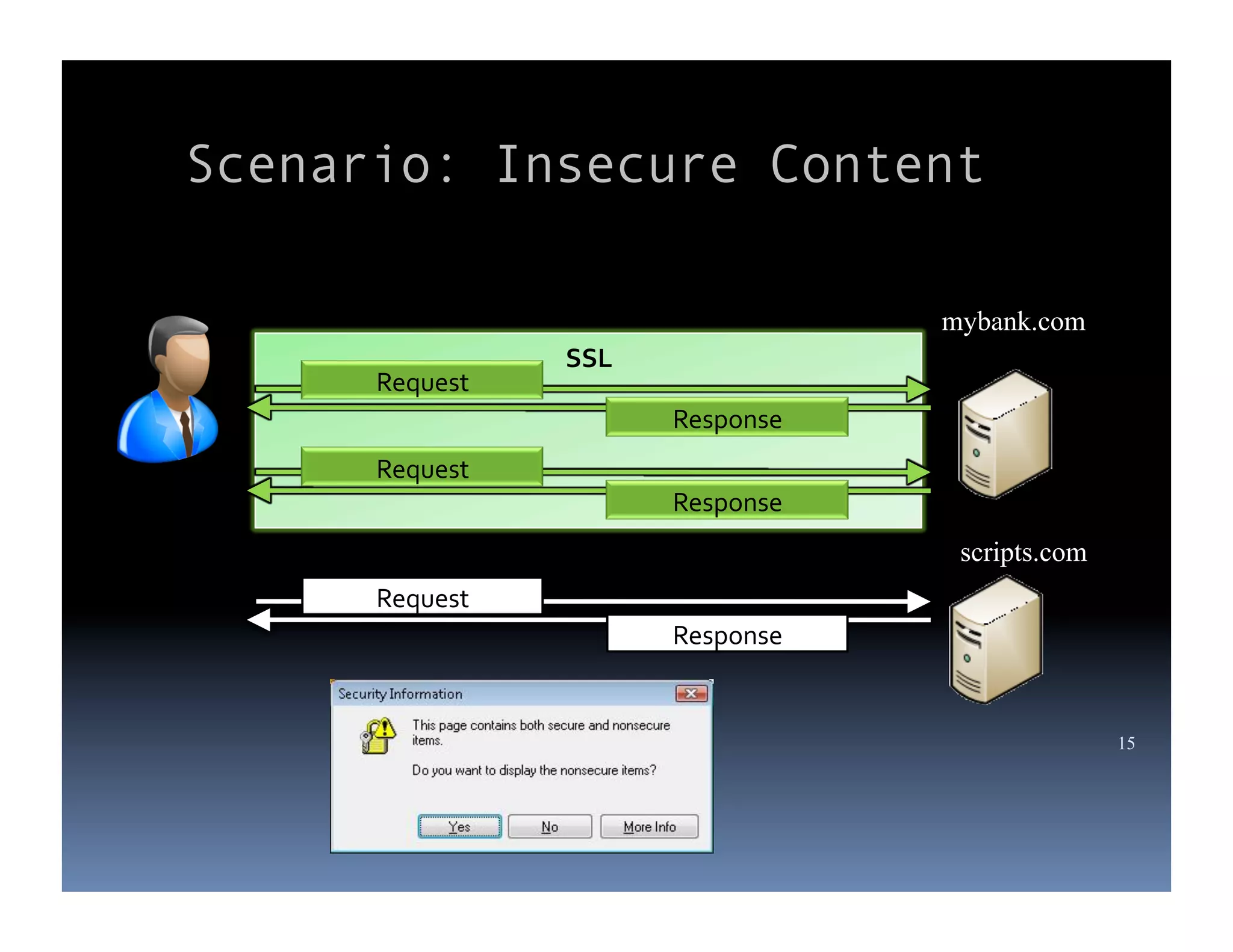
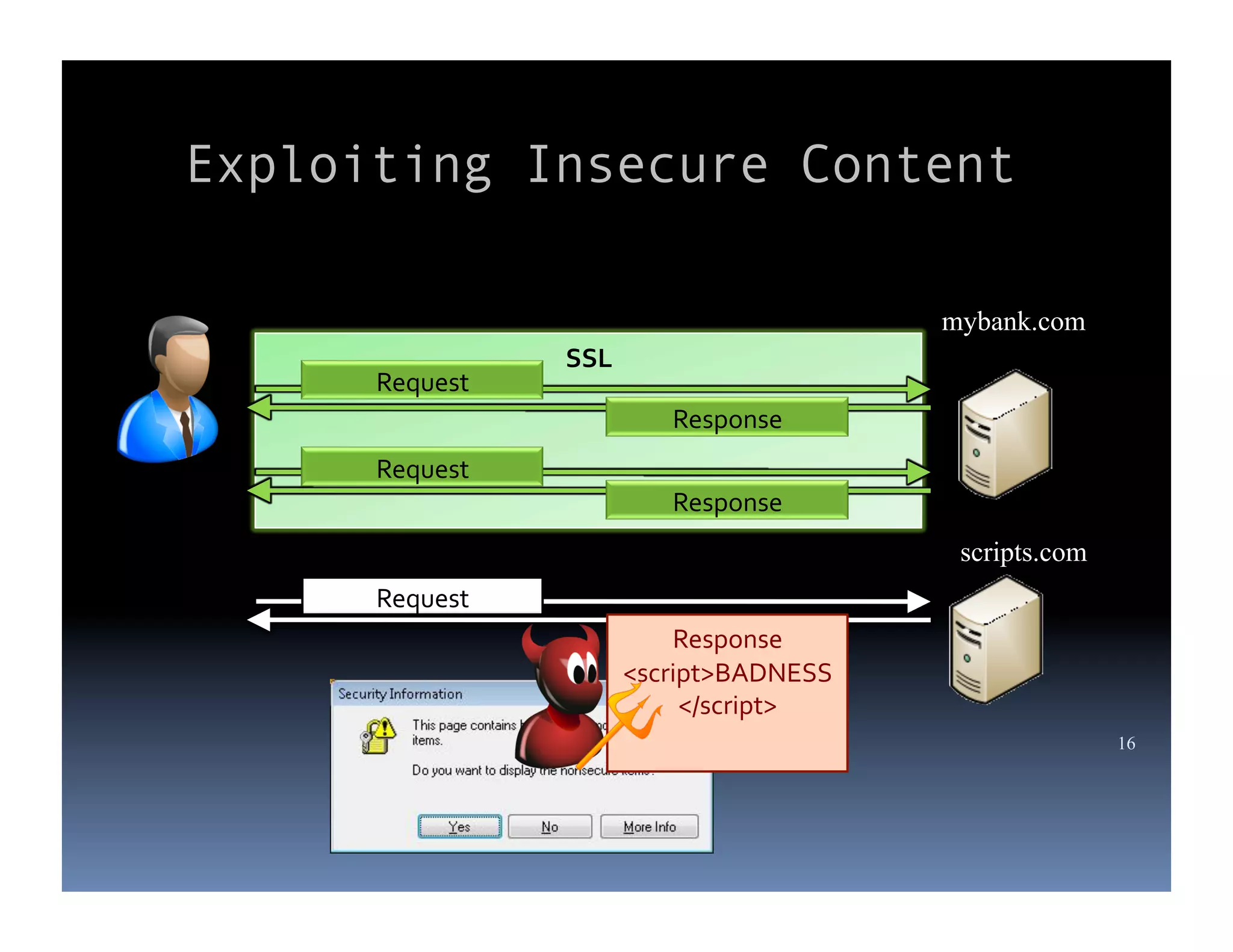
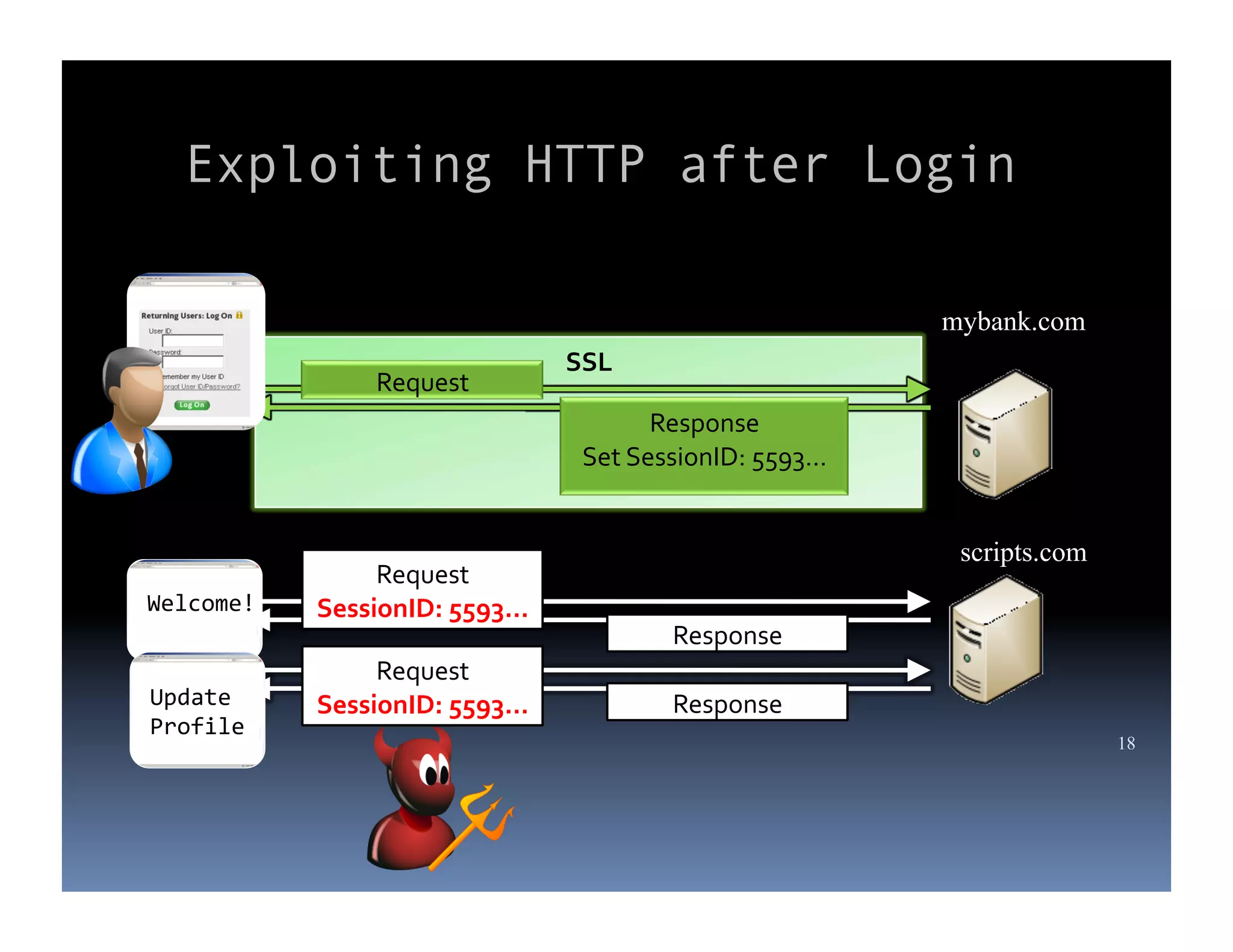
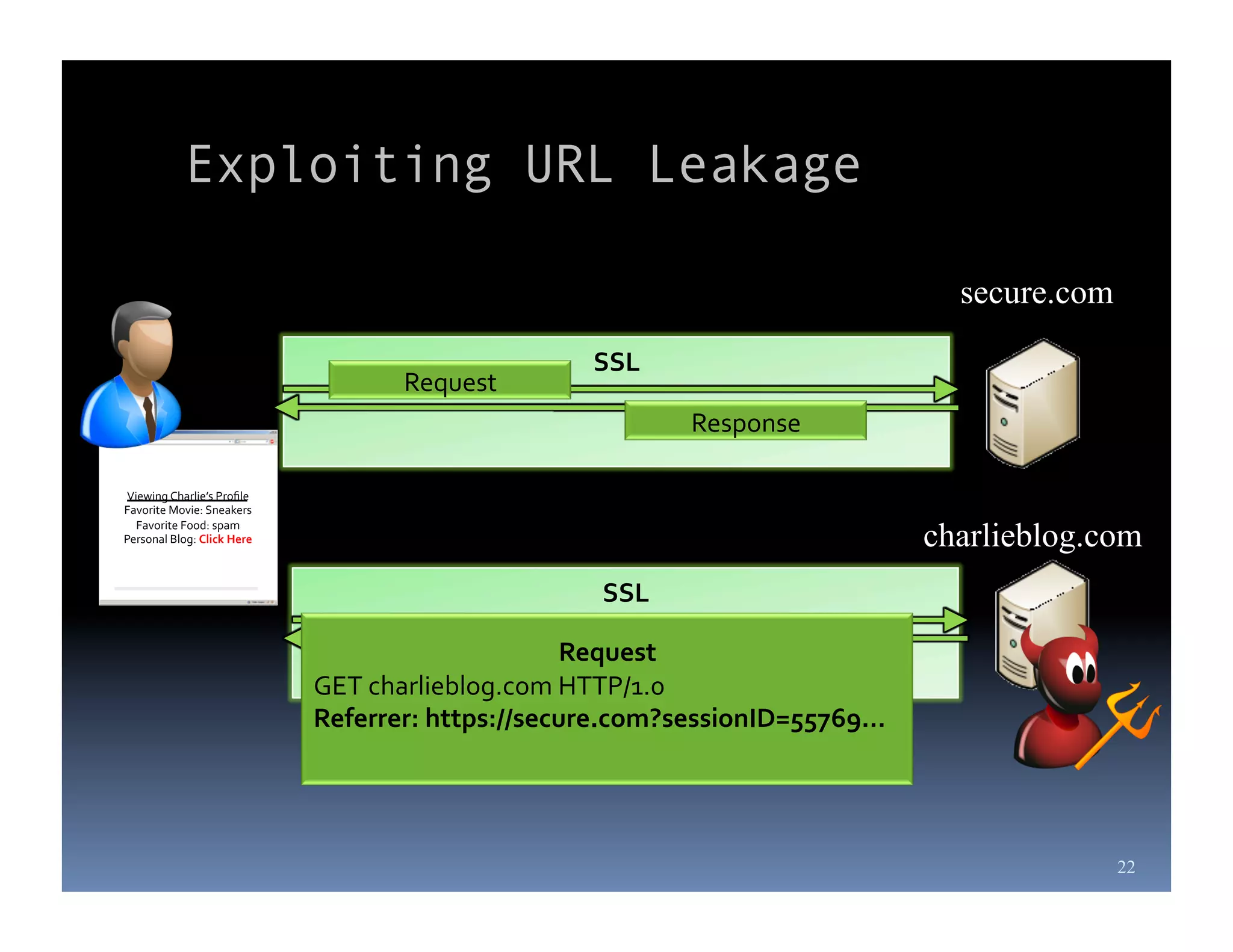
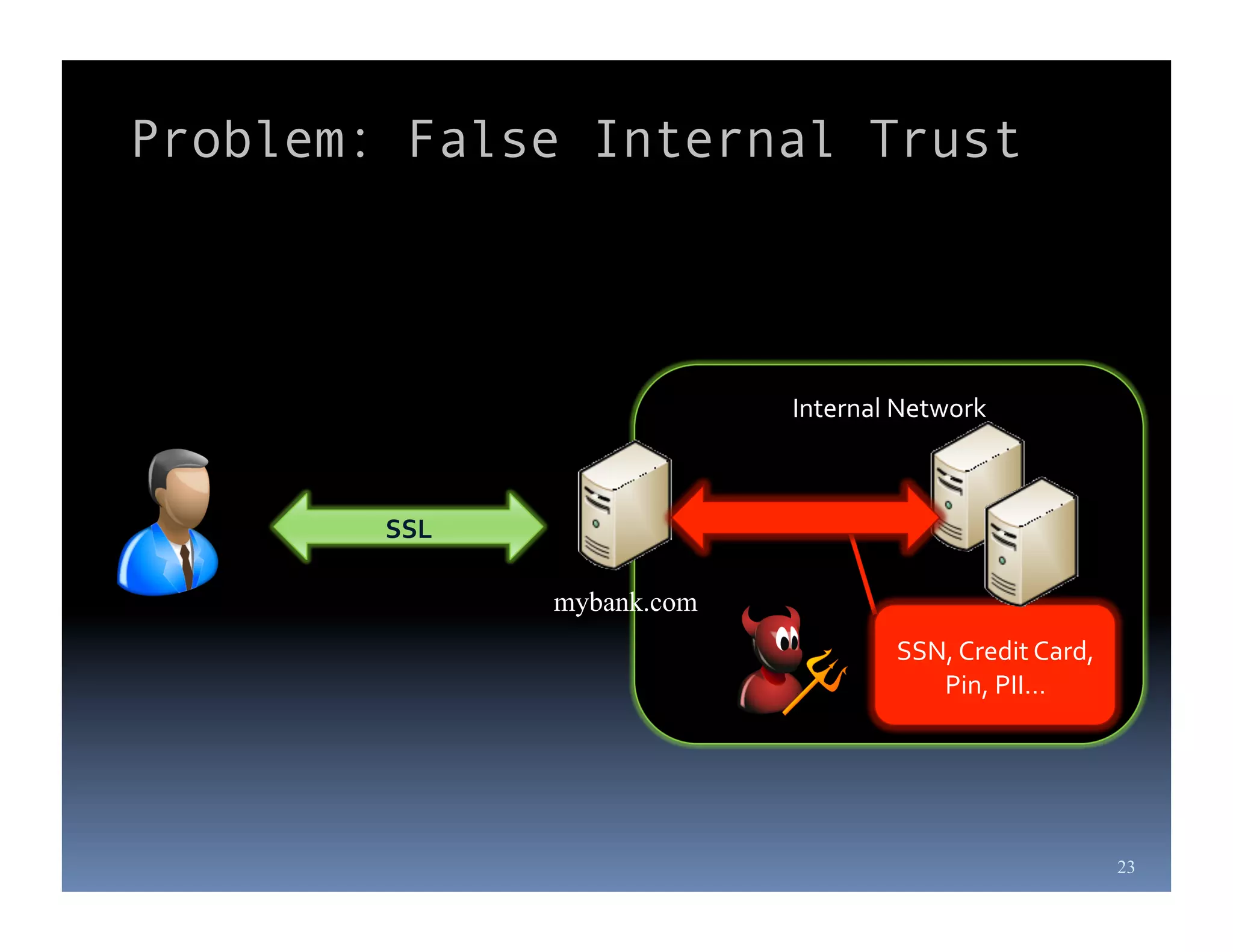
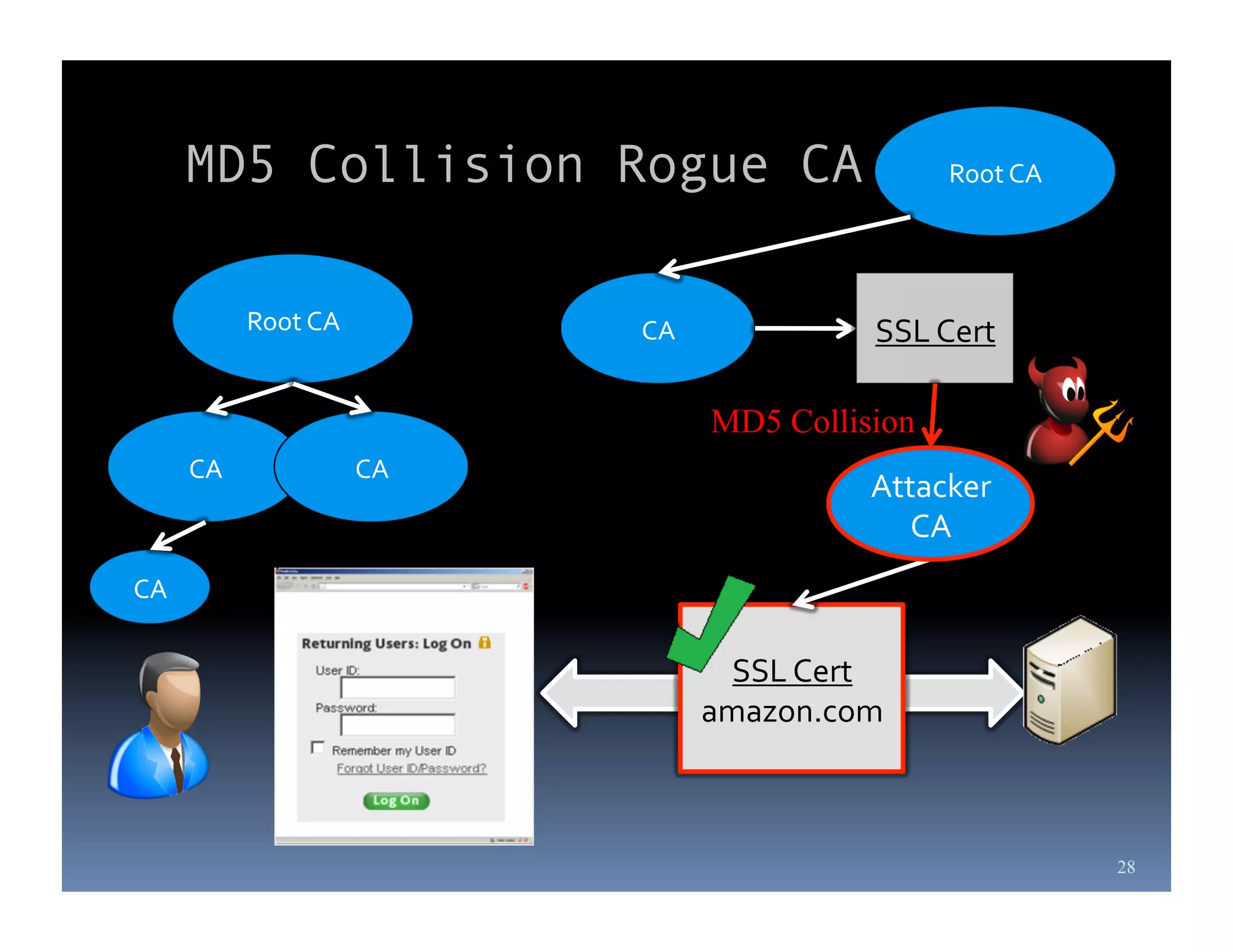
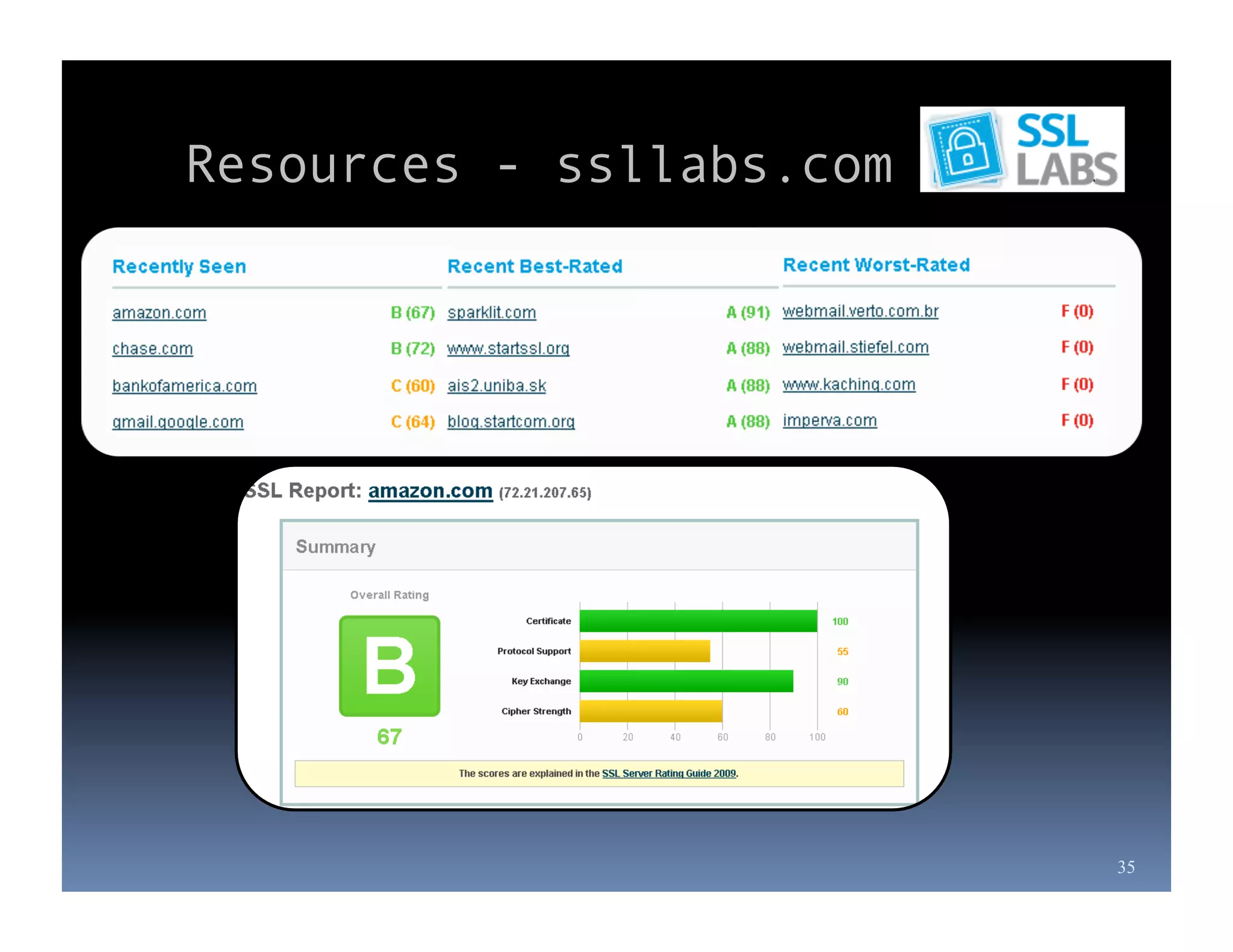
Michael Coates is a web security engineer at Mozilla who has contributed to several security projects. Some of the key problems with SSL/TLS usage that he discusses include usability issues for users in understanding SSL, insecure redirects and content that can allow attackers to exploit user sessions, and false assumptions that all SSL is equally secure.