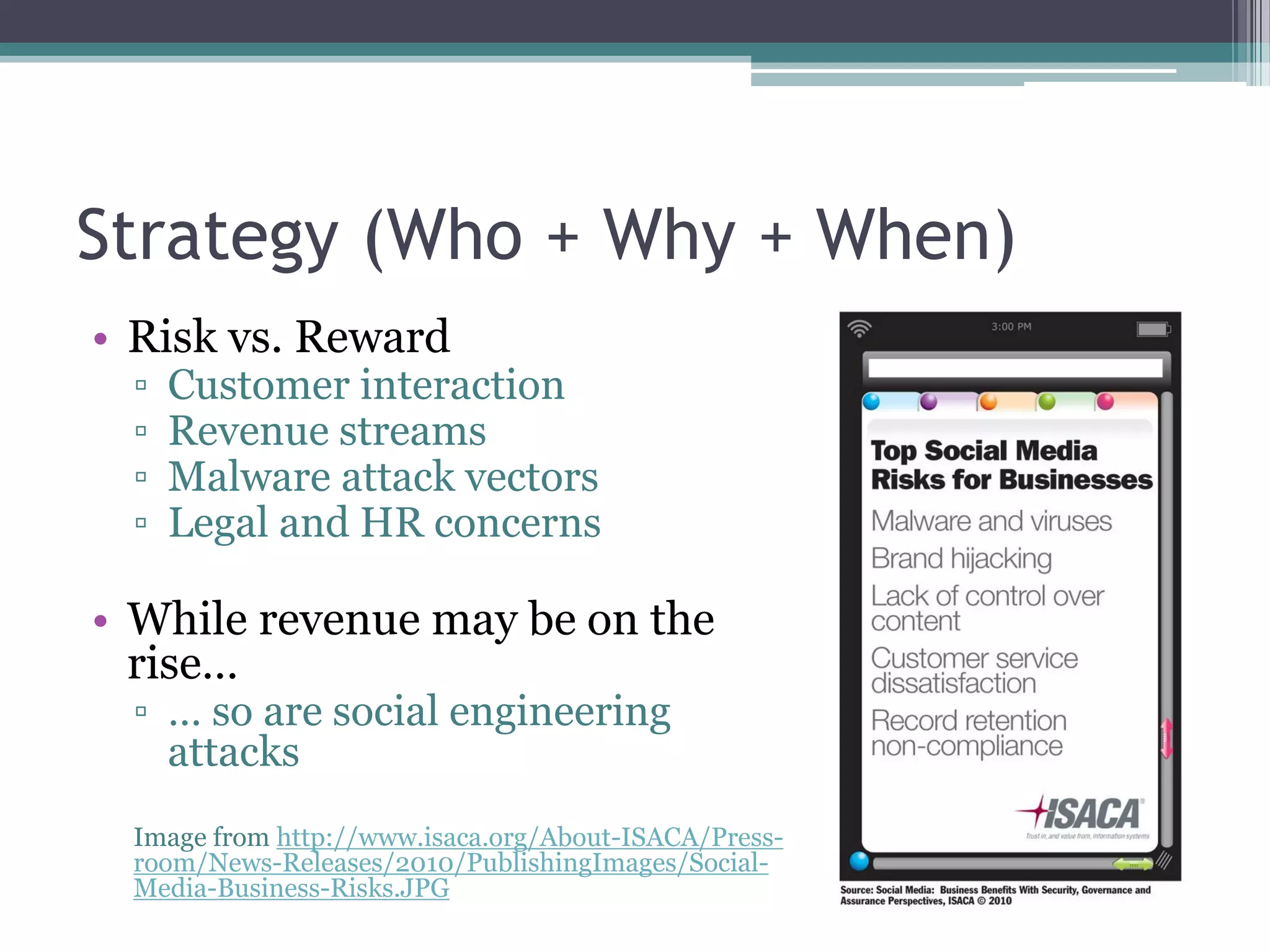
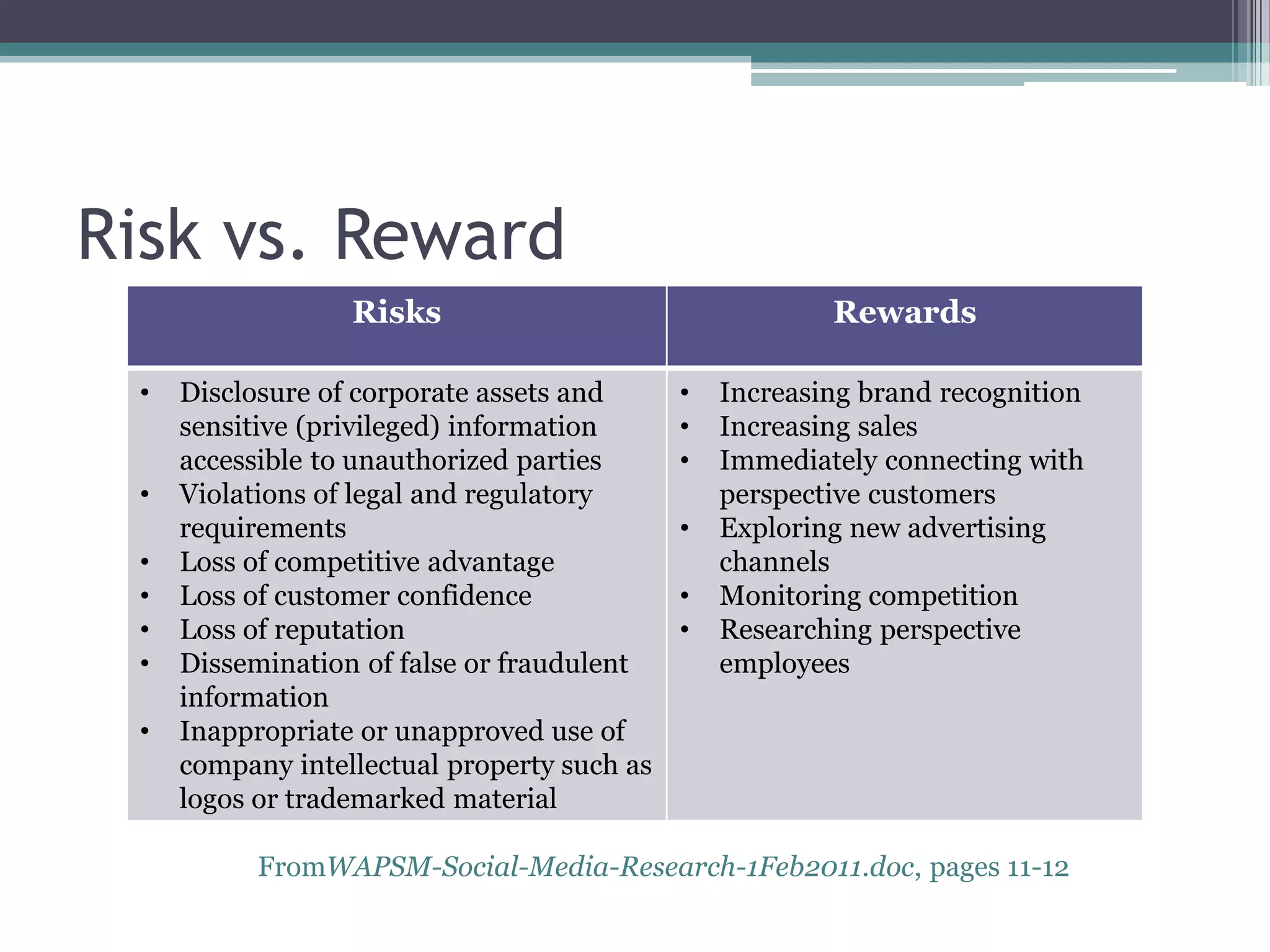
The document discusses the need for a comprehensive approach to social media implementation and auditing, highlighting risks such as unauthorized information access and loss of reputation versus rewards like increased brand recognition. It emphasizes the importance of defining policy, training, and ongoing assessments to mitigate risks while leveraging social media's benefits. Regulatory compliance and strategic alignment with business objectives are also key considerations for effective social media management.


![The Five W’s
•
•
•
•
•
•
Who?
What?
When?
Where?
Why?
How?
[Image courtesy of Master Isolated Images / FreeDigitalPhotos.net]](https://image.slidesharecdn.com/bridgingthesocialmediaimplementation-auditgap-131209092611-phpapp01/75/Bridging-the-Social-Media-Implementation-Audit-Gap-3-2048.jpg)


![Scope, per ISACA
• Current social media tools include:
▫ Blogs (e.g., WordPress, Drupal™, TypePad®)
▫ Microblogs (e.g., Twitter, Tumblr)
▫ Instant messaging (e.g., AOL Instant Messenger [AIM™],
Microsoft® Windows Live Messenger)
▫ Online communication systems (e.g., Skype™)
▫ Image and video sharing sites (e.g., Flickr®, YouTube)
▫ Social networking sites (e.g., Facebook, MySpace)
▫ Professional networking sites (e.g., LinkedIn, Plaxo)
▫ Online communities that may be sponsored by the
company itself (Similac.com, “Open” by American Express)
▫ Online collaboration sites (e.g., Huddle)
FromWAPSM-Social-Media-Research-1Feb2011.doc, page 11](https://image.slidesharecdn.com/bridgingthesocialmediaimplementation-auditgap-131209092611-phpapp01/75/Bridging-the-Social-Media-Implementation-Audit-Gap-8-2048.jpg)