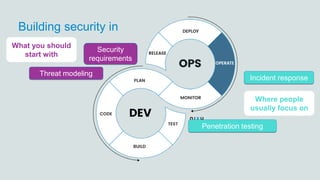
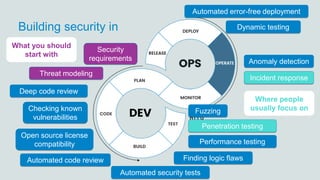
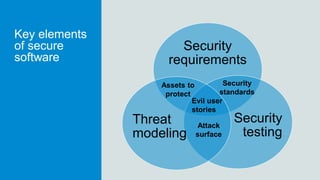
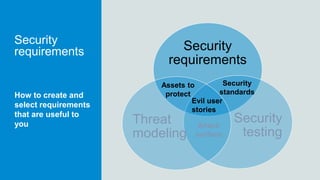
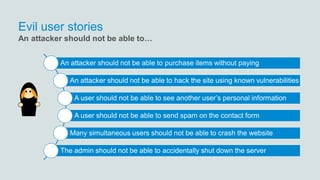
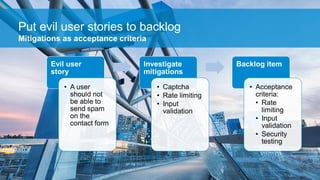
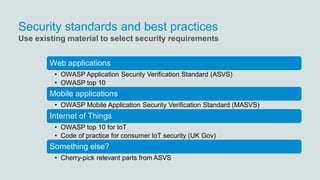
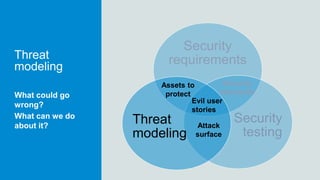
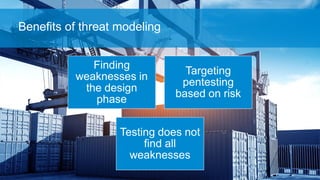
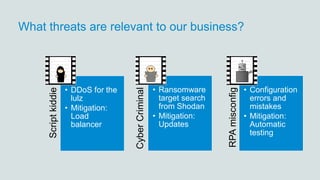
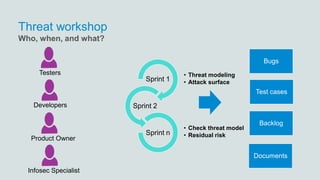
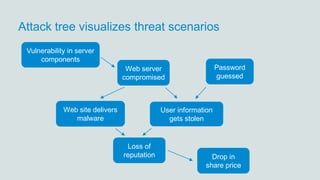
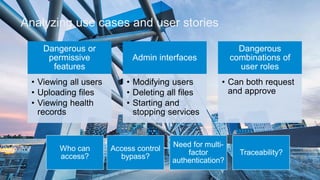
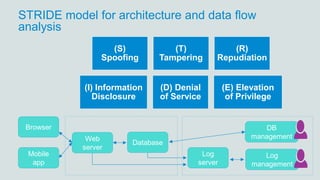
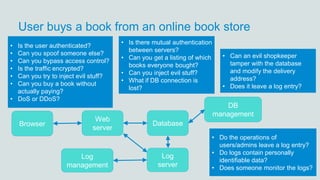
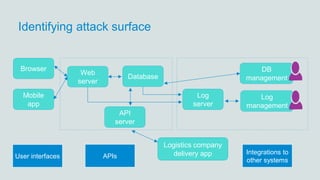
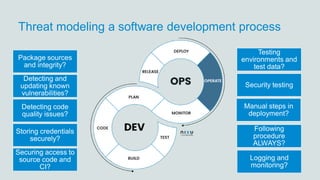
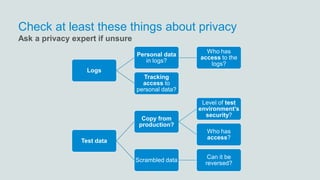
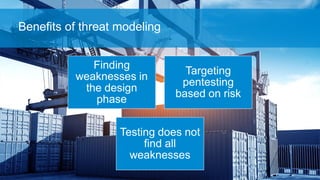
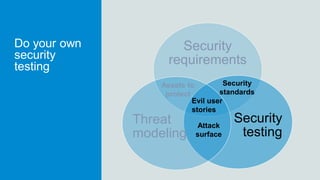
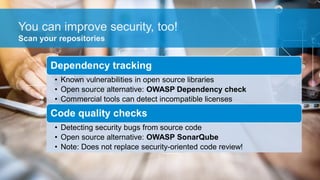
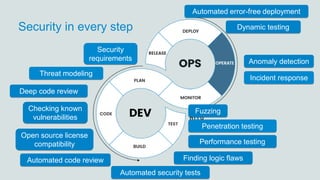
The document discusses what software developers and testers should know about software security. It emphasizes the importance of threat modeling to understand potential threats, creating security requirements, and including security testing in the development process. It provides examples of security best practices like checking for vulnerabilities, conducting code reviews, and penetration testing applications to find issues before attackers. The goal is to integrate security practices into development rather than as an afterthought.