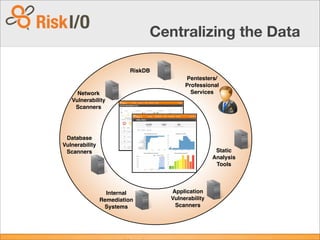
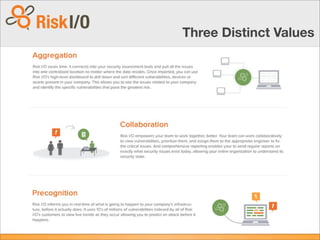
The document discusses the challenges of performing comprehensive vulnerability assessments across hundreds of websites that are constantly changing. It then describes how automated vulnerability scanners were used to try to address this problem, but resulted in dumping large amounts of data without prioritization or context. The document proposes a "Moneyball" or sabermetrics approach to security intelligence by collecting and correlating vulnerability data from multiple sources and using attributes, trends, and outcomes to analyze risk, prioritize issues, and compare organizations. This approach would provide a centralized view of an organization's vulnerability posture and the external threat landscape.